nmap脚本详解 - 春告鳥
source link: https://www.cnblogs.com/Cl0ud/p/17052752.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

nmap脚本详解 - 春告鳥 - 博客园
nmap --script
我们通过nmap script来大幅扩展nmap的功能,nmap具有强大的脚本引擎NSE(Nmap Scripting Engine),它允许用户编写(和共享)简单的脚本(使用lua编程语言)自动化各种网络任务
NSEDoc Reference Portal — Nmap Scripting Engine documentation
目前nmap官方有604个NSE脚本,安装nmap后存储在script文件夹下,这些都是Nmap特有的,是基于lua语言编写的
nmap脚本分类
nmap脚本主要分为以下几类,在扫描时可根据需要设置--script=类别这种方式进行比较笼统的扫描:
- 指定运行脚本
当我们使用Nmap并添加参数-sC或者--script时,Nmap会执行NSE脚本
例如,在script目录下有http-title.nse、http-trace.nse脚本,执行如下命令:
- 从文件中读取参数
- 显示全部发送和收到的数据
- 更新数据库
在Nmap的scripts目录里有一个script.db,该文件中保存了当前Nmap可用的脚本,类似于一个小型数据库,如果我们开启nmap并且调用了此参数,则nmap会自行扫描scripts目录中的扩展脚本,进行数据库更新
指定对应的脚本信息,Nmap会输出该脚本名称对应的脚本使用参数,以及详细介绍信息。
nmap脚本简介
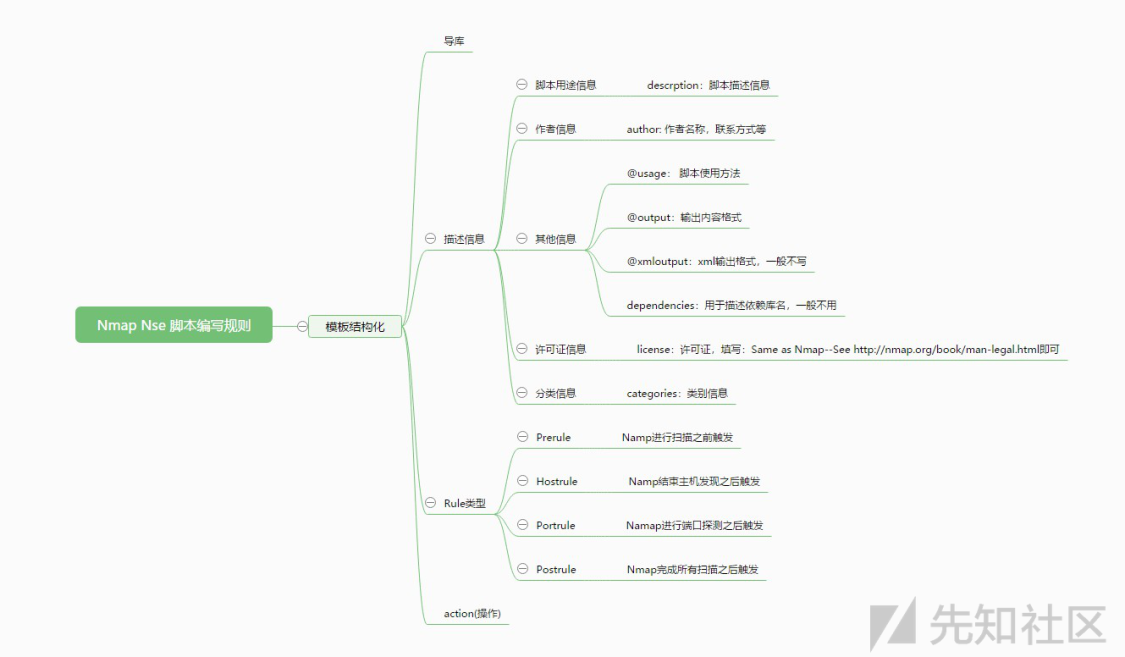
一个NSE脚本的书写一般分为四步:
- 导入脚本编写所需库
- 编写脚本描述信息
- 确定Rule类型
- 编写Action
Nmap nse脚本模板结构图
其中Rule存在四种类型:
- Prerule 在Nmap没有扫描之前进行触发
- Hostrule 在Nmap执行主机发现或探测时进行触发
- Protrule 在Nmap执行端口扫描的时候触发
- Postrule 在Nmap结束的时候触发脚本,通常用于扫描结果的数据提取和整理
用于描述脚本的触发规则,返回值只有true和false两种。返回值决定了后面的action对应的函数是否执行
- true - 执行
- false - 不执行
Rule描述脚本的触发规则,定义了脚本在nmap生命周期的啥时候来执行
我们选择 http-php-version.nse脚本来跟进分析一下,这个脚本的主要作用是检测PHP服务器的版本
查看API手册 https://nmap.org/nsedoc/lib/ 来导入你要导入的lua脚本 - nmap内置模块
local http = require "http" local nmap = require "nmap" local shortport = require "shortport" local stdnse = require "stdnse" local string = require "string" local table = require "table"
local openssl = stdnse.silent_require "openssl"
description对脚本进行概述
description = [[ Attempts to retrieve the PHP version from a web server. PHP has a number of magic queries that return images or text that can vary with the PHP version. This script uses the following queries: * <code>/?=PHPE9568F36-D428-11d2-A769-00AA001ACF42</code>: gets a GIF logo, which changes on April Fool's Day. * <code>/?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000</code>: gets an HTML credits page.
A list of magic queries is at http://www.0php.com/php_easter_egg.php. The script also checks if any header field value starts with <code>"PHP"</code> and reports that value if found.
PHP versions after 5.5.0 do not respond to these queries.
Link: * http://phpsadness.com/sad/11 ]]
作者和脚本分类
在端口扫描的时候运行判断函数,这里直接调用了shortport提供的判断
然后定义了访问的接口和PHP对应关系
-- These are the magic queries that return fingerprintable data. local LOGO_QUERY = "/?=PHPE9568F36-D428-11d2-A769-00AA001ACF42" local CREDITS_QUERY = "/?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000"
-- For PHP 5.x hashes up to 5.2.14 and 5.3.3 see: -- http://seclists.org/nmap-dev/2010/q4/518
local LOGO_HASHES = { -- Bunny (Carmella) ["37e194b799d4aaff10e39c4e3b2679a2"] = {"5.0.0 - 5.0.3"}, -- Black Scottish Terrier (Scotch) ["4b2c92409cf0bcf465d199e93a15ac3f"] = {"4.3.11", "4.4.0 - 4.4.9", "5.0.4 - 5.0.5", "5.1.0 - 5.1.2"}, -- Colored ["50caaf268b4f3d260d720a1a29c5fe21"] = {"5.1.3 - 5.1.6", "5.2.0 - 5.2.17"}, -- PHP Code Guy With Breadsticks (Thies C. Arntzen) ["85be3b4be7bfe839cbb3b4f2d30ff983"] = {"4.0.0 - 4.2.3"}, -- Brown Dog In Grass (Nadia) ["a57bd73e27be03a62dd6b3e1b537a72c"] = {"4.3.0 - 4.3.11"}, -- Elephant ["fb3bbd9ccc4b3d9e0b3be89c5ff98a14"] = {"5.3.0 - 5.3.29", "5.4.0 - 5.4.45"}, }
local CREDITS_HASHES = { ["744aecef04f9ed1bc39ae773c40017d1"] = {"4.0.1pl2", "4.1.0 - 4.1.2", "4.2.2"}, ["4ba58b973ecde12dafbbd40b54afac43"] = {"4.1.1 OpenVMS"}, ["8bc001f58bf6c17a67e1ca288cb459cc"] = {"4.2.0 - 4.2.2"}, ["3422eded2fcceb3c89cabb5156b5d4e2"] = {"4.2.3"}, ["1e04761e912831dd29b7a98785e7ac61"] = {"4.3.0"}, ["1e04761e912831dd29b7a98785e7ac61"] = {"4.3.1"}, ["65eaaaa6c5fdc950e820f9addd514b8b"] = {"4.3.1 Mandrake Linux"}, ["8a8b4a419103078d82707cf68226a482"] = {"4.3.2"}, ["22d03c3c0a9cff6d760a4ba63909faea"] = {"4.3.2"}, -- entity encoded "'" ["8a4a61f60025b43f11a7c998f02b1902"] = {"4.3.3 - 4.3.5"}, ["39eda6dfead77a33cc6c63b5eaeda244"] = {"4.3.3 - 4.3.5"}, -- entity encoded "'" ["913ec921cf487109084a518f91e70859"] = {"4.3.6 - 4.3.8"}, ["884ba1f11e0e956c7c3ba64e5e33ee9f"] = {"4.3.6 - 4.3.8"}, -- entity encoded ["c5fa6aec2cf0172a5a1df7082335cf9e"] = {"4.3.8 Mandrake Linux"}, ["8fbf48d5a2a64065fc26db3e890b9871"] = {"4.3.9 - 4.3.11"}, ["f9b56b361fafd28b668cc3498425a23b"] = {"4.3.9 - 4.3.11"}, -- entity encoded "'" ["ddf16ec67e070ec6247ec1908c52377e"] = {"4.4.0"}, ["3d7612c9927b4c5cfff43efd27b44124"] = {"4.4.0"}, -- entity encoded "'" ["55bc081f2d460b8e6eb326a953c0e71e"] = {"4.4.1"}, ["bed7ceff09e9666d96fdf3518af78e0e"] = {"4.4.2 - 4.4.4"}, ["692a87ca2c51523c17f597253653c777"] = {"4.4.5 - 4.4.7"}, ["50ac182f03fc56a719a41fc1786d937d"] = {"4.4.8 - 4.4.9"}, ["3c31e4674f42a49108b5300f8e73be26"] = {"5.0.0 - 5.0.5"}, ["e54dbf41d985bfbfa316dba207ad6bce"] = {"5.0.0"}, ["6be3565cdd38e717e4eb96868d9be141"] = {"5.0.5"}, ["b7cf53972b35b5d57f12c9d857b6b507"] = {"5.0.5 ActiveScript"}, ["5518a02af41478cfc492c930ace45ae5"] = {"5.1.0 - 5.1.1"}, ["6cb0a5ba2d88f9d6c5c9e144dd5941a6"] = {"5.1.2"}, ["82fa2d6aa15f971f7dadefe4f2ac20e3"] = {"5.1.3 - 5.1.6"}, ["6a1c211f27330f1ab602c7c574f3a279"] = {"5.2.0"}, ["d3894e19233d979db07d623f608b6ece"] = {"5.2.1"}, ["56f9383587ebcc94558e11ec08584f05"] = {"5.2.2"}, ["c37c96e8728dc959c55219d47f2d543f"] = {"5.2.3 - 5.2.5", "5.2.6RC3"}, ["1776a7c1b3255b07c6b9f43b9f50f05e"] = {"5.2.6"}, ["1ffc970c5eae684bebc0e0133c4e1f01"] = {"5.2.7 - 5.2.8"}, ["54f426521bf61f2d95c8bfaa13857c51"] = {"5.2.9 - 5.2.14"}, ["adb361b9255c1e5275e5bd6e2907c5fb"] = {"5.2.15 - 5.2.17"}, ["db23b07a9b426d0d033565b878b1e384"] = {"5.3.0"}, ["a4c057b11fa0fba98c8e26cd7bb762a8"] = {"5.3.1 - 5.3.2"}, ["b34501471d51cebafacdd45bf2cd545d"] = {"5.3.3"}, ["e3b18899d0ffdf8322ed18d7bce3c9a0"] = {"5.3.4 - 5.3.5"}, ["2e7f5372931a7f6f86786e95871ac947"] = {"5.3.6"}, ["f1f1f60ac0dcd700a1ad30aa81175d34"] = {"5.3.7 - 5.3.8"}, ["23f183b78eb4e3ba8b3df13f0a15e5de"] = {"5.3.9 - 5.3.29"}, ["85da0a620fabe694dab1d55cbf1e24c3"] = {"5.4.0 - 5.4.14"}, ["ebf6d0333d67af5f80077438c45c8eaa"] = {"5.4.15 - 5.4.45"}, }
最后就是判定的主要逻辑了,虽然我们不懂Lua,但是我们还是能大概看懂这里做的事情
action = function(host, port) local response local logo_versions, credits_versions local logo_hash, credits_hash local header_name, header_value local lines
-- 1st pass : the "special" PHP-logo test response = http.get(host, port, LOGO_QUERY) if response.body and response.status == 200 then logo_hash = stdnse.tohex(openssl.md5(response.body)) logo_versions = LOGO_HASHES[logo_hash] end
-- 2nd pass : the PHP-credits test response = http.get(host, port, CREDITS_QUERY) if response.body and response.status == 200 then credits_hash = stdnse.tohex(openssl.md5(response.body)) credits_versions = CREDITS_HASHES[credits_hash] end
for name, value in pairs(response.header) do if string.match(value, "^PHP/") then header_name = name header_value = value break end end
lines = {} if logo_versions then lines[#lines + 1] = "Versions from logo query (less accurate): " .. table.concat(logo_versions, ", ") elseif logo_hash and nmap.verbosity() >= 2 then lines[#lines + 1] = "Logo query returned unknown hash " .. logo_hash end if credits_versions then lines[#lines + 1] = "Versions from credits query (more accurate): " .. table.concat(credits_versions, ", ") elseif credits_hash and nmap.verbosity() >= 2 then lines[#lines + 1] = "Credits query returned unknown hash " .. credits_hash end if header_name and header_value then lines[#lines + 1] = "Version from header " .. header_name .. ": " .. header_value end
if #lines > 0 then return table.concat(lines, "\n") end end
访问可能存在泄露PHP版本的接口,并将返回值进行md5计算,检查字典里是否有对应值,如果有的话就说明存在PHP的版本泄露,最后返回结果。
事实上只是实现的语言不一样,核心的检测原理都是一致的
按照应用服务扫描
nmap脚本的完整文档可以看官方文档 https://nmap.org/nsedoc/scripts/
下面是常用的一些应用扫描
VNC扫描
VNC (Virtual Network Console)是虚拟网络控制台的缩写。它 是一款优秀的远程控制工具软件
- 检查vnc bypass
- 检查vnc认证方式
- 获取vnc信息
smb扫描
SMB(全称是Server Message Block)是一个网络协议名,它能被用于Web连接和客户端与服务器之间的信息沟通
- smb破解
- smb字典破解
- smb漏洞检测
Mssql扫描
- 暴力破解用户名密码
- 有密码后
xp_cmdshell执行命令
- 有密码后dymphash
Mysql扫描
- 扫描root空口令
- 列举所有mysql用户
- 扫描mysql相关的脚本
Oracle扫描
- oracle sid 扫描
- oracle弱口令破解
如果想要了解更多的脚本内容,移步官方文档 -> https://nmap.org/nsedoc/scripts/
建了一个微信的安全交流群,欢迎添加我微信备注进群,一起来聊天吹水哇,以及一个会发布安全相关内容的公众号,欢迎关注 😃
__EOF__
Recommend
-
 18
18
nmap脚本使用总结 clzzy ·...
-
 45
45
在这篇文章中,我们将研究最著名的渗透工具之一 Nmap 一款标志性的跨平台扫描器。它的原意为Network Mapper(网络映射器),具有相当强大的扫描...
-
 7
7
安全岗春招面经总结 五一过后,春招就差不多结束了,今年...
-
 4
4
对Github指定类目的内容进行监控和推送 - 春告鳥 - 博客园 很久之前看到HACK学习呀有一个Github 安全搬运工的系列文章,个...
-
 8
8
如果想要对针对WiFi的攻击进行监测,就需要定期获取WiFi的运行状态,例如WiFi的SSID,WiFi强度,是否开放,加密方式等信息,在Android中通过WiFiManager来实现 WiFiManager简介 WiFiManager这个类是Android暴露给开发者使用的...
-
 4
4
PowerUsageSummary.java源码分析 - 春告鳥 - 博客园 在在线网站http://androidxref.com/上对Android版本6.0.1_r10源码进行分析 官方手机的应用...
-
 7
7
在分析PowerUsageSummary的时候,其实可以发现主要获取应用和服务电量使用情况的实现是在BatteryStatsHelper.java中 还是在线网站http://androidxref.com/上对Android版本6.0.1_r10源码进行分析 具体位置在 /frameworks/bas...
-
 6
6
极客大赛的碎碎念 - 春告鳥 - 博客园 公司的应届生都会参加极客大赛,简单来说就是会给出各个部门根据自身业务而出的题目,参赛者从题...
-
 11
11
[安全开发] SQL注入扫描(一股子GPT味~) 实际上大部分都是它写的,它真我哭 SQL注入扫描就是一种...
-
 5
5
xpoc漏洞使用与编写 浅尝 下载地址 https://github.com/chaiti...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK