Tsunami of junk traffic that broke DDoS records delivered by tiniest of botnets
source link: https://arstechnica.com/information-technology/2022/06/tsunami-of-junk-traffic-that-broke-ddos-records-delivered-by-tiniest-of-botnets/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

ARMS RACE —
Tsunami of junk traffic that broke DDoS records delivered by tiniest of botnets
The DDoS arms race shows no signs of slowing down.
Dan Goodin - 6/15/2022, 9:37 PM

A massive flood of malicious traffic that recently set a new distributed denial-of-service record came from an unlikely source. A botnet of just 5,000 devices was responsible, as extortionists and vandals continue to develop ever more powerful attacks to knock sites offline, security researchers said.
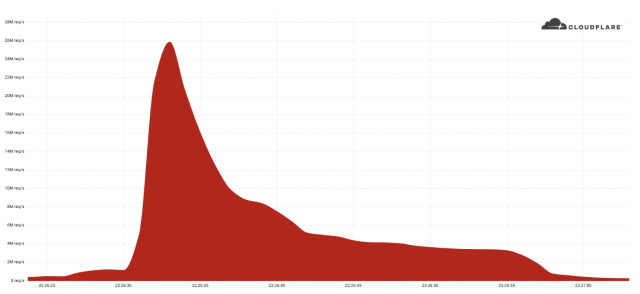
The DDoS delivered 26 million HTTPS requests per second, breaking the previous record of 15.3 million requests for that protocol set only seven weeks ago, Cloudflare Product Manager Omer Yoachimik reported. Unlike more common DDoS payloads such as HTTP, SYN, or SYN-ACK packets, malicious HTTPS requests require considerably more computing resources for the attacker to deliver and for the defender or victim to absorb.4,000 times stronger
"We've seen very large attacks in the past over (unencrypted) HTTP, but this attack stands out because of the resources it required at its scale," Yoachimik wrote.
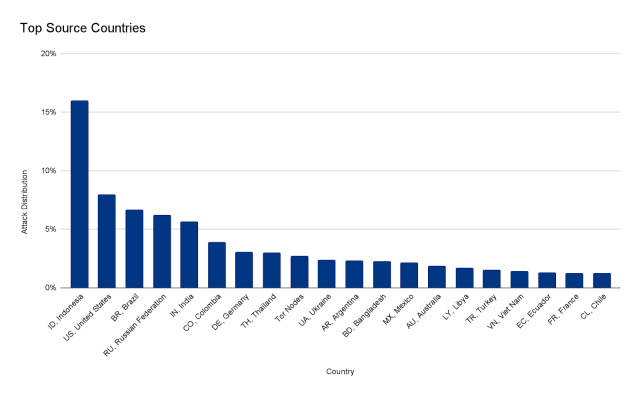
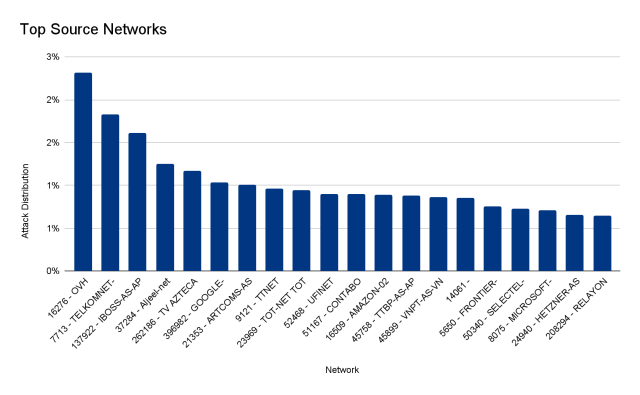
The burst lasted less than 30 seconds and generated more than 212 million HTTPS requests from more than 1,500 networks in 121 countries, with Indonesia, the United States, Brazil, and Russia topping the list. The top networks used included French-based OVH (Autonomous System Number 16276), the Indonesian Telkomnet (ASN 7713), the US-based iboss (ASN 137922), and the Libyan Ajeel (ASN 37284). About 3 percent of the attack came through Tor nodes.
As was the case with the previous 15.3 million-HTTPS-requests-per-second attack, the new one originated mainly on devices from cloud service providers. The servers and virtual machines available from these providers are considerably more powerful than compromised computers and IoT devices connected to residential ISPs, which are the more common source of DDoSes.
AdvertisementYoachimik wrote:
The 26M rps DDoS attack originated from a small but powerful botnet of 5,067 devices. On average, each node generated approximately 5,200 rps at peak. To contrast the size of this botnet, we’ve been tracking another much larger but less powerful botnet of over 730,000 devices. The latter, larger botnet wasn’t able to generate more than one million requests per second, i.e. roughly 1.3 requests per second on average per device. Putting it plainly, this botnet was, on average, 4,000 times stronger due to its use of virtual machines and servers.
In some cases, DDoSers combine their use of cloud-based devices with other techniques to make their attacks more potent. In the 15.3 million-HTTPS-requests-per-second DDoS from earlier this year, for example, Cloudflare uncovered evidence that the threat actors may have exploited a critical vulnerability. This exploit allowed them to bypass authentication in a wide range of Java-based applications used inside the cloud environments running their attack devices.
DDoS attacks can be measured in several ways, including by the volume of data, the number of packets, or the number of requests sent each second. The other current records are 3.4 terabits per second for volumetric DDoSes—which attempt to consume all bandwidth available to the target—and 809 million packets per second. The 26 million HTTPS requests per second break the previous 17.2 million-requests-per-second record set in 2020. Not only did that earlier attack deliver fewer packets than the new record, but it also relied on HTTP, which isn't as potent as HTTPS.
The Cloudflare product manager said that his company automatically detected and mitigated the attack against the customer, which was using Cloudflare's free service.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK