

Authentication using Azure Databricks personal access tokens
source link: https://docs.microsoft.com/en-gb/azure/databricks/dev-tools/api/latest/authentication?toc=https%3A%2F%2Fdocs.microsoft.com%2Fen-gb%2Fazure%2Fazure-databricks%2FTOC.json&bc=https%3A%2F%2Fdocs.microsoft.com%2Fen-gb%2Fazure%2Fbread%2Ftoc.json
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Authentication using Azure Databricks personal access tokens
- 24/11/2020
- 2 minutes to read
In this article
To authenticate to and access Databricks REST APIs, you can use Azure Databricks personal access tokens or Azure Active Directory (Azure AD) tokens.
This article discusses how to use Azure Databricks personal access tokens. For Azure AD tokens, see Authenticate using Azure Active Directory tokens.
Important
Tokens take the place of passwords in an authentication flow, and like passwords, they should always be treated with care. To protect tokens, Databricks recommends that you store tokens in:
- Secret management and retrieve tokens in notebooks using the Secrets utilities.
- A local key store and use the Python keyring package to retrieve tokens at runtime.
Requirements
Token-based authentication is enabled by default for all Azure Databricks accounts launched after January 2018. If it is disabled, your administrator must enable it before you can perform the tasks described in this article. See Manage personal access tokens.
Generate a personal access token
This section describes how to generate a personal access token in the Azure Databricks UI. You can also generate and revoke tokens using the Token API.
Click the user profile icon
 in the upper right corner of your Azure Databricks workspace.
in the upper right corner of your Azure Databricks workspace.Click User Settings.
Go to the Access Tokens tab.
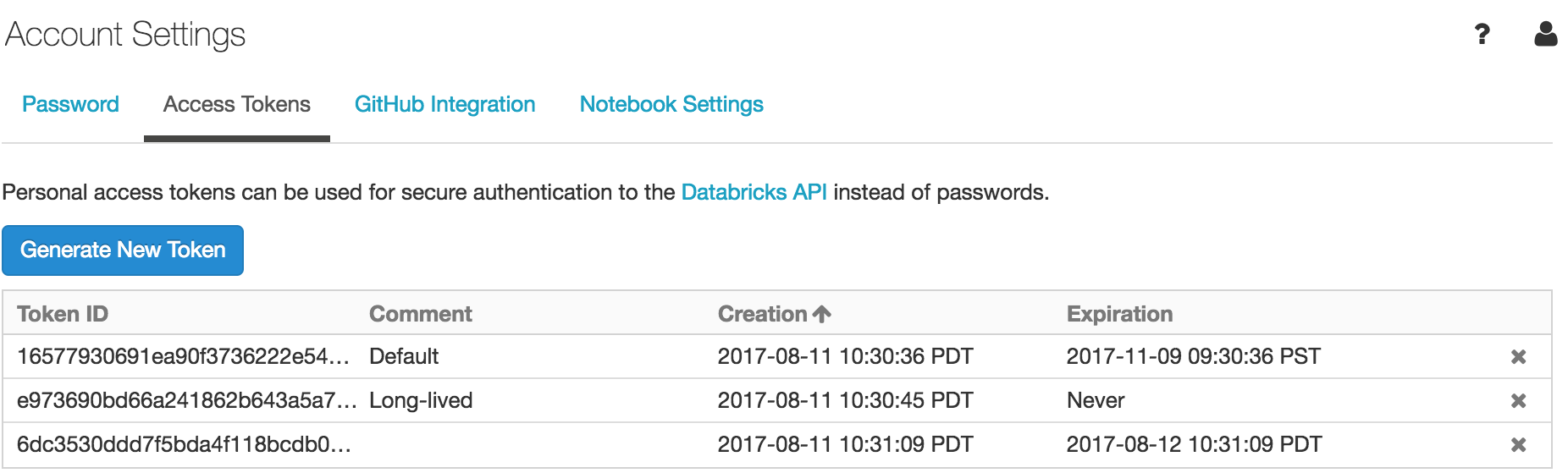
Click the Generate New Token button.
Optionally enter a description (comment) and expiration period.
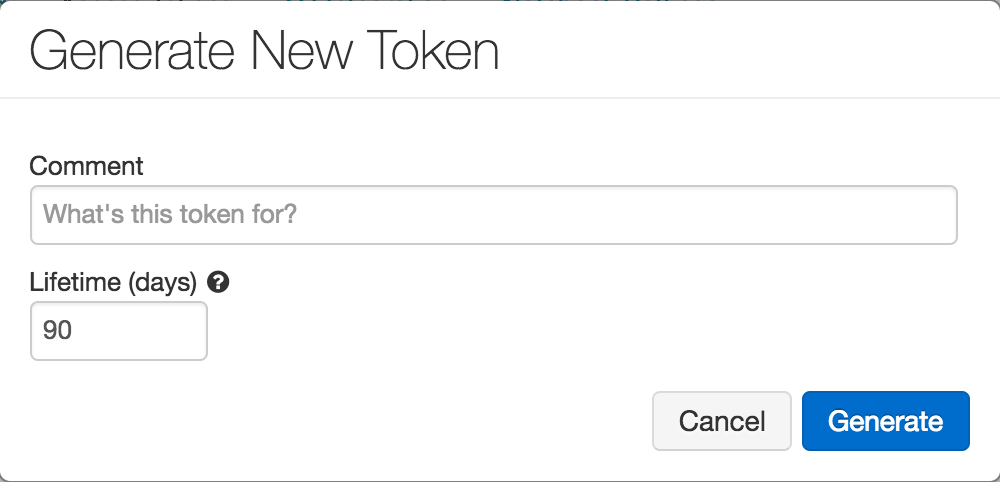
Click the Generate button.
Copy the generated token and store in a secure location.
Revoke a personal access token
This section describes how to revoke personal access tokens using the Azure Databricks UI. You can also generate and revoke access tokens using the Token API.
- Click the user profile icon
 in the upper right corner of your Azure Databricks workspace.
in the upper right corner of your Azure Databricks workspace. - Click User Settings.
- Go to the Access Tokens tab.
- Click x for the token you want to revoke.
- On the Revoke Token dialog, click the Revoke Token button.
Use a personal access token to access the Databricks REST API
You can store a personal access token in .netrc and use in curl or pass it to the Authorization: Bearer header.
Store token in .netrc file and use in curl
Create a .netrc file with machine, login, and password properties:
machine <databricks-instance>
login token
password <personal-access-token>
where:
<databricks-instance>is the workspace URL of your Azure Databricks deployment.tokenis the literal stringtoken<personal-access-token>is the value of your personal access token.
To invoke the .netrc file, use -n in your curl command:
curl -n -X GET https://<databricks-instance>/api/2.0/clusters/list
Pass token to Bearer authentication
You can include the token in the header using Bearer authentication. You can use this approach with curl or any client that you build. For the latter, see Upload a big file into DBFS.
curl -X GET -H 'Authorization: Bearer <personal-access-token>' https://<databricks-instance>/api/2.0/clusters/list
Is this page helpful?
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK