
1

Building an Intrusion Detection System: A Triumph at the SANReN Cyber Security C...
source link: https://blogs.mathworks.com/student-lounge/2024/03/18/building-an-intrusion-detection-system-a-triumph-at-the-sanren-cyber-security-challenge/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Inspiration
Meet the champions: Shani Nezar, Uhone Teffo, Carlo Barnardo, and Heinrich E. Guided, this team trained the most accurate machine learning model among the all 10 teams at the SANReN Cyber Security Challenge! The exploited the ease-to-use capabilities of the MathWorks platform and trained machine learning model via MATLAB Classification Learner App for cyber threat detection. Their proficiency was significantly enhanced by complimentary courses like MATLAB Onramp and Machine Learning Onramp, which equipped them with the latest knowledge in AI swiftly and extra points for the competition. Let’s hear their journey:

Inspiration
In the dynamic realm of cybersecurity, staying one step ahead of potential threats is paramount. The SANReN Cyber Security Challenge provided a platform for teams to showcase their prowess, and our journey through the challenge was marked by a standout achievement in the MATLAB Classification Challenge: a remarkable 98% accuracy score on a machine learning model designed for intrusion detection. The crux of our success lay in the utilization of the open dataset UNSW-NB15, a goldmine of real-time network traffic data with rich features specifically curated for anomaly-based intrusion detection. The data set can be download at the following link.
Breaking Down the Problem
The UNSW-NB15 dataset, with its meticulous labelling of attacks (1) and non-attacks (0), served as the foundation for our challenge. The primary goal was to leverage the features within the dataset to predict whether a given data point belongs to the attack or non-attack category. This, essentially, was the task at hand – developing a robust Intrusion Detection System (IDS) capable of discerning malicious activities from normal network behaviour.
How Did We Implement It?
Dataset Exploration
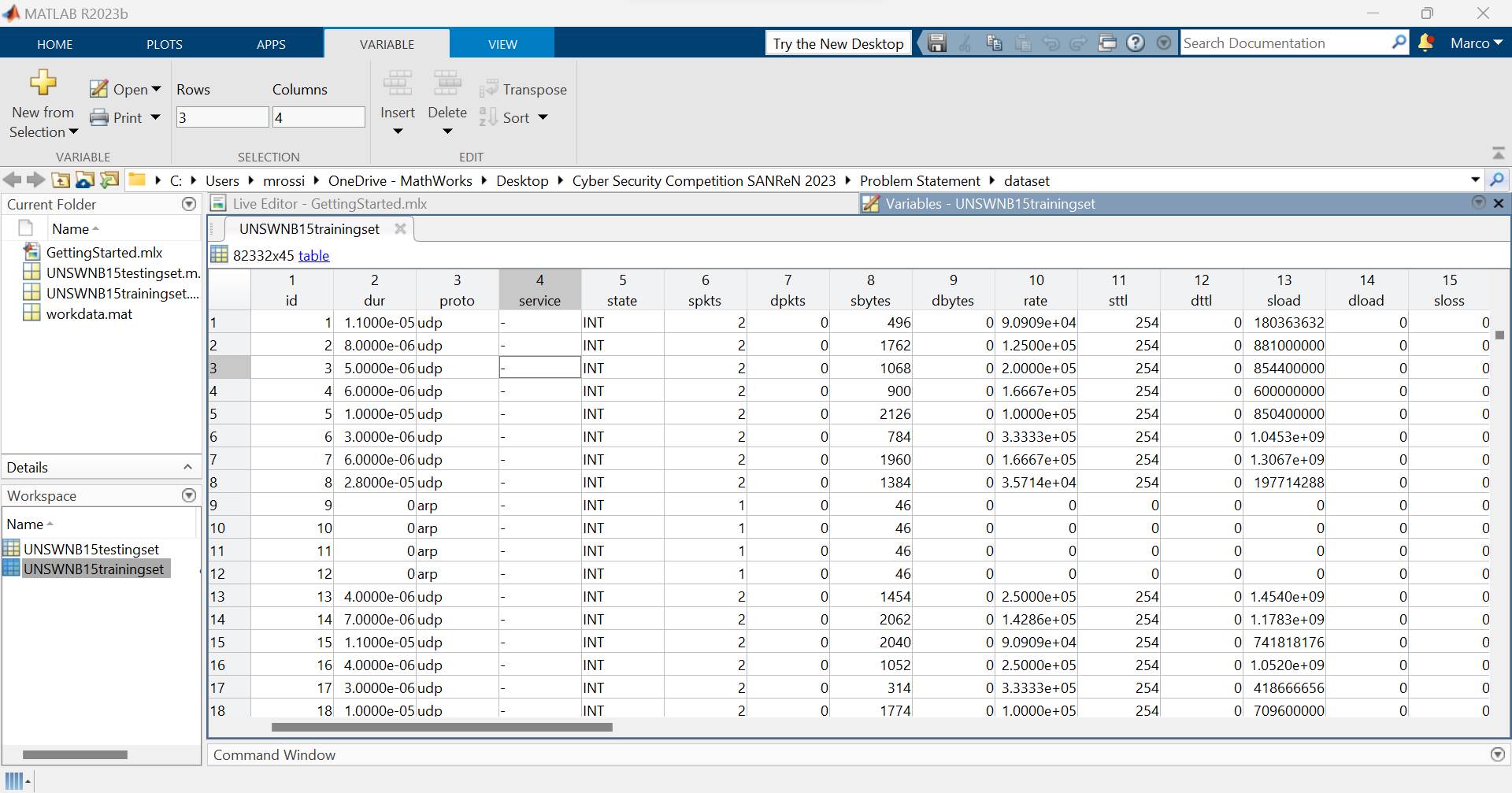
Before diving into the development of the machine learning model, we meticulously explored the UNSW-NB15 dataset. Understanding the intricacies of the features, the distribution of data, and the characteristics of attacks proved crucial in designing an effective solution.
Model Selection
Given the nature of the problem, we opted for a machine learning approach. Our model of choice was carefully selected based on its suitability for intrusion detection tasks. After thorough evaluation, we settled on a model that showcased promising results during initial experimentation.
Online Trainings with MATLAB Onramp and Machine Learning Onramp
Our journey to success is significantly enriched by the invaluable skills and insights gained through MATLAB Onramp and Machine Learning Onramp in honing our skills. The online trainings provided by MATLAB Academy equipped our team with essential knowledge, allowing us to navigate the intricacies of data exploration and model development seamlessly. These onramps acted as catalysts in our problem-solving journey, bridging the gap between theoretical understanding and practical application.
Low-code AI with MATLAB
MATLAB’s intuitive environment facilitated a smooth exploration of the dataset. With its user-friendly interface and powerful functionalities, we delved into the data, gaining insights that shaped our approach. MATLAB’s capabilities not only simplified the process but also enhanced our efficiency in handling complex data structures. A noteworthy aspect of our methodology was the utilization of low-code AI with MATLAB. Leveraging an App coupled with a concise 10 lines of code, we navigated what might have seemed like a daunting coding challenge. This approach not only streamlined our implementation but also highlighted the accessibility of AI, even for those not deeply versed in coding intricacies.
Ready-to-Train Models in Classification Learner App
The Classification Learner App merged as a game-changer, providing us with ready-to-train models that significantly expedited our development process. This feature allowed us to focus on the application of AI rather than its intricate development especially with having the correct model hyperparameters. Theavailability of pre-built models within the app played a pivotal role in achieving success without the need for extensive AI expertise.
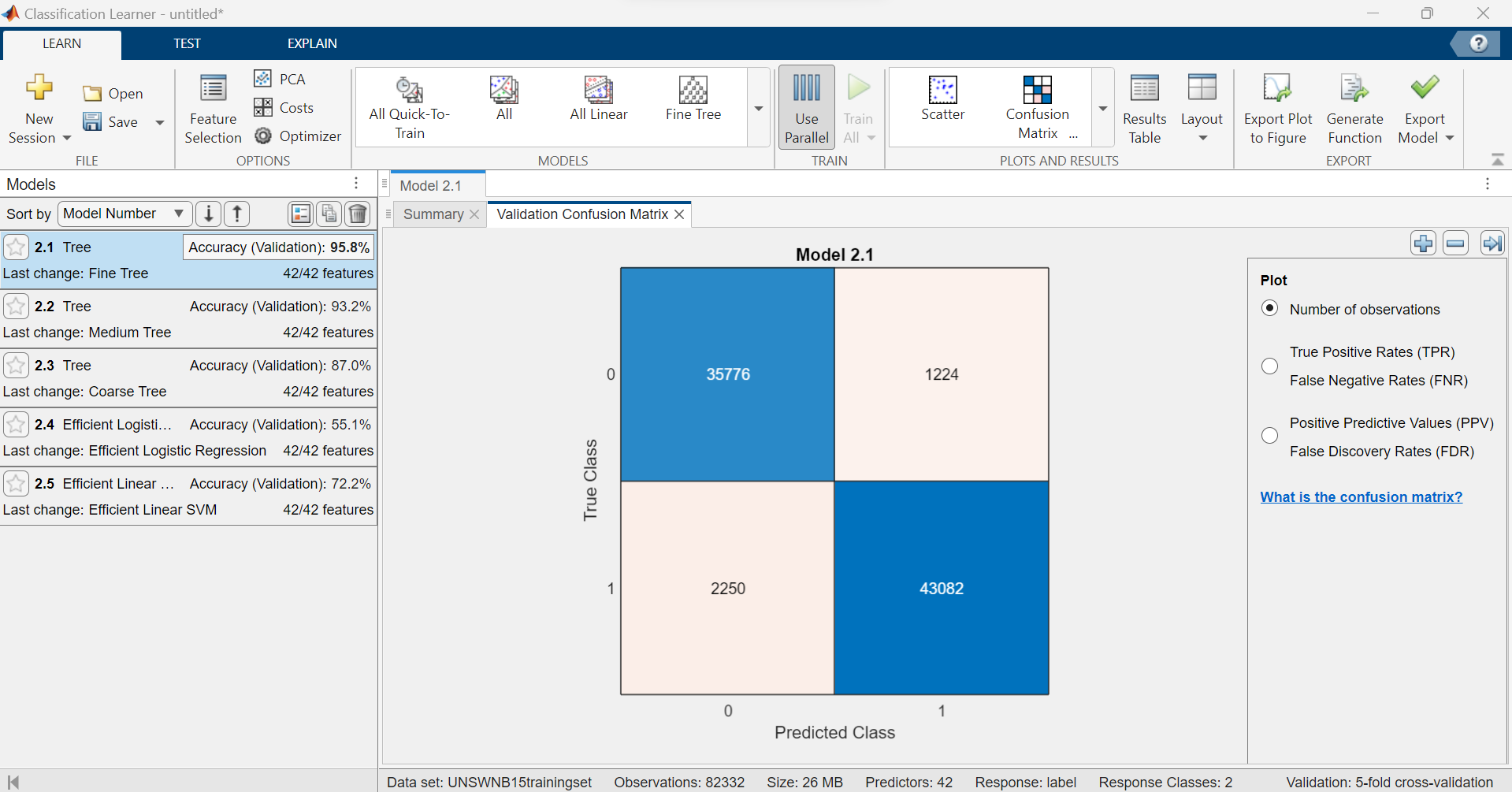
Results
The culmination of our efforts resulted in an impressive 95.8% accuracy score. Our machine learning model successfully identified and classified attacks with remarkable precision, showcasing the potential of data-driven approaches in cybersecurity. The ability to predict malicious activities with such accuracy reflects not only the efficiency of our chosen model but also the robustness of our methodology.
Key Takeaways
1. Dataset Understanding is Key
Thoroughly understanding the dataset is foundational. MATLAB enables easy features exploration, pattern identification, and a comprehension of the nature of attacks. Such ease to explore data greatly influenced the success of the intrusion detection system.
2. Model Selection Matters
Selecting the optimal machine learning model for intrusion detection is crucial. MATLAB Apps offers a variety of pre-built models, enabling users to concentrate on enhancing the precision required to detect nuanced irregularities in network traffic, which directly influences the system’s efficiency.
3. Real-world Simulation
The inclusion of fresh, unlabelled data for prediction mirrors the challenges faced in real-world cybersecurity. A model’s ability to adapt and identify novel threats is a testament to its practicality.
4. Continuous Improvement
The landscape of cybersecurity is ever-evolving. Regular updates to the model and continuous monitoring ensure that the IDS remains effective in identifying new and emerging threats.
In conclusion, our success at the SANReN Cyber Security Challenge stands as a testament to the power of machine learning in bolstering cybersecurity defences. The journey from dataset exploration to model deployment underscored the importance of meticulous planning, adaptability, and a deep understanding of the intricacies of network traffic. As we celebrate our triumph, we also acknowledge the ongoing commitment required to stay at the forefront of cybersecurity innovation. The path to a secure digital landscape is paved with continuous learning, resilience, and a proactive approach to emerging threats.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK