Enforcing SmartScreen with Policy
source link: https://textslashplain.com/2023/08/14/enforcing-smartscreen-with-policy/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Enforcing SmartScreen with Policy
Microsoft Defender SmartScreen provides protection against the most common forms of attack: phishing and malware. SmartScreen support is built-in to Microsoft Edge and the Windows 8+ shell. The SmartScreen web service also powers the Microsoft Defender Browser Protection extension for Chromium-derived browsers.
While SmartScreen provides powerful controls to block attacks, the user remains in full control. SmartScreen will block Edge browsers from visiting a known-phishing site, but there’s a “Continue to this unsafe site (not recommended)” link available to override the decision:
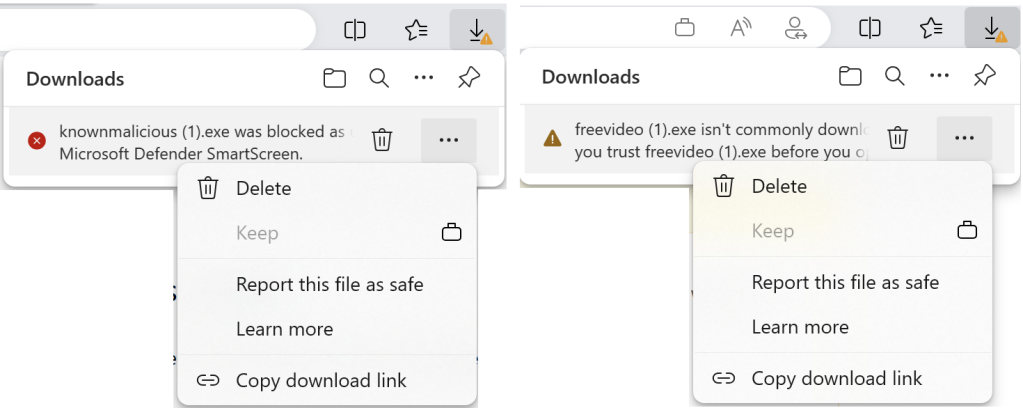
Similarly, if a known malicious file is blocked from download in Edge, the user may use the Keep menu command to override the blocking decision:
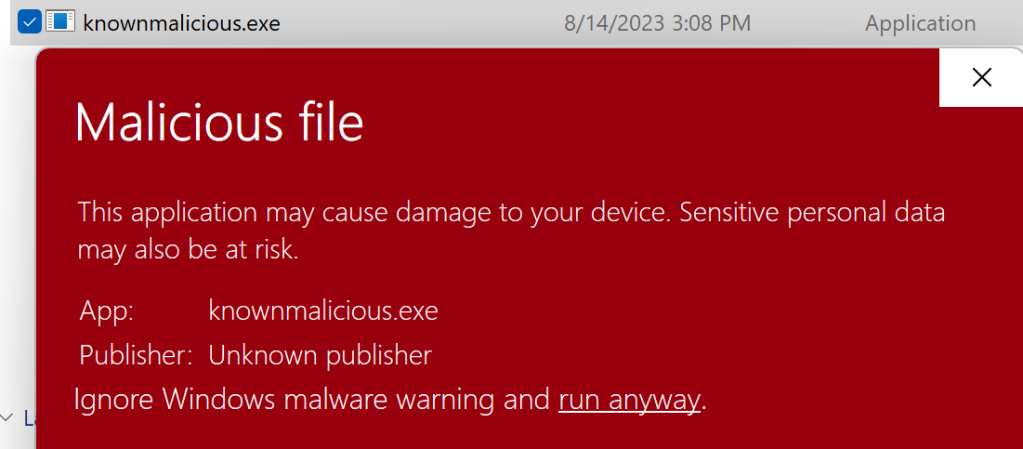
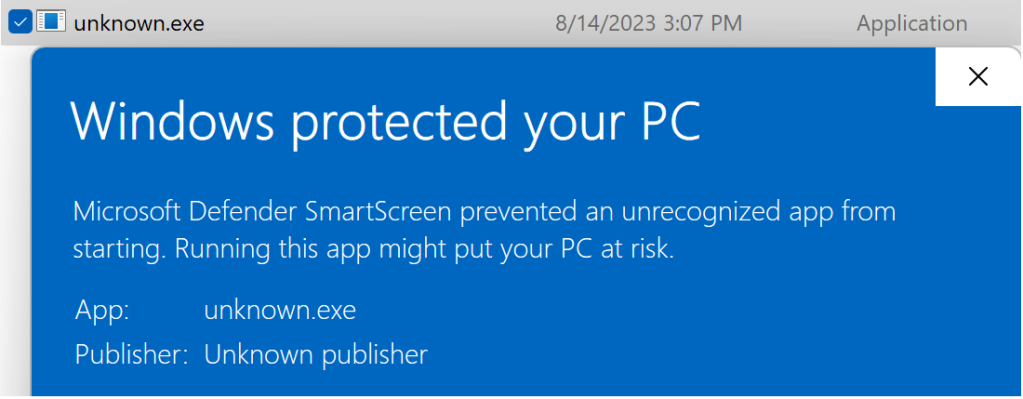
When a known bad file is downloaded using another browser without SmartScreen built-in (e.g. Chrome), attempting to run the file via Windows Explorer will trigger a prompt that also includes a hidden option to run anyway:
Controls
But what if you’re a tech-savvy parent, child, or IT administrator who doesn’t want a less-savvy user you’re responsible for protecting to override the security protections of SmartScreen?
Here’s where Group Policy comes in. SmartScreen allows you remove these dangerous override options.
Policies can be set using various administrative tools, but these ultimately flow through to a handful of registry settings:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"EnableSmartScreen"=dword:00000001
"ShellSmartScreenLevel"="Block"
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"SmartScreenPuaEnabled"=dword:00000001
"SmartScreenEnabled"=dword:00000001
"PreventSmartScreenPromptOverrideForFiles"=dword:00000001
"PreventSmartScreenPromptOverride"=dword:00000001
After these policies are set, the software’s dangerous “do it anyway” commands are removed entirely.
The Edge block page loses the “Continue” link:
When downloading malicious or unrecognized programs, the “Keep” command is disabled:
Within the Windows Shell, the “Run anyway” link or button is removed from the dialog when invoking malicious or unrecognized files downloaded via other browsers:
Pairing the powerful protections of SmartScreen with policies that ensure that only experts are in control helps you keep everyone safe.
-Eric
Posted byericlaw2023-08-14Posted insecurity, webTags:malware, phishing, policy, security, SmartScreen
Published by ericlaw
Impatient optimist. Dad. Author/speaker. Created Fiddler & SlickRun. PM @ Microsoft 2001-2012, and 2018-, working on Office, IE, and Edge. Now a GPM for Microsoft Defender. My words are my own, I do not speak for any other entity. View more posts
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK