

Elasticsearch use cases in cybersecurity
source link: https://dzlab.github.io/2023/04/02/elastic-cybersecurity/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Elasticsearch use cases in cybersecurity
02 Apr 2023 by dzlab

Elasticsearch core capability is indexing and retrieving textual data, which makes it a solid foundation for many use cases. In the context of cybersecurity, Elasticsearch can be used for a variety of applications, such as:
- Log analysis: Elasticsearch can be used to store and search through large amounts of log data from different sources, such as network devices, servers, and applications. This can help identify anomalies, detect attacks, and analyze patterns that could indicate potential threats.
- Security incident response: When responding to security incidents, such as breaches or malware outbreaks, Elasticsearch can be used to quickly search through logs and other relevant data to gather evidence and track down the source of the attack.
- Intrusion Detection/Prevention Systems (IDS/IPS): IDS/IPS systems generate a lot of alerts which need to be investigated by security analysts. Elasticsearch can act as a central repository for these alerts, allowing security teams to easily search and filter them based on multiple criteria such as IP addresses, user agents etc., and automate certain actions like blocking IPs etc.
- Security Information and Event Management (SIEM): SIEM solutions aggregate data from various security tools including firewalls ,IPS/IDS etc and uses machine learning algorithms to create correlation rules .Elasticsearch can act as a powerful back end database to store this correlated data and provide real time query capabilities to detect new kinds of advanced persistent threat .It provides ability to perform complex queries on structured ,semi structured and unstructured data at very low latency which makes it extremely scalable compared to traditional relational databases
- Fraud detection: Elasticsearch can be used to build models for fraud detection by analyzing transactional data, browsing behavior, and device metadata.
- Insider Threat Detection: By collecting and indexing data related to employee activity within company networks and infrastructure, Elasticsearch can be leveraged to flag any unusual activities and raise red flags for further investigation
As you can see there are too many applications, in the rest of this article we will focus on the Vulnerability management use case and how Elasticsearch can be leveraged.
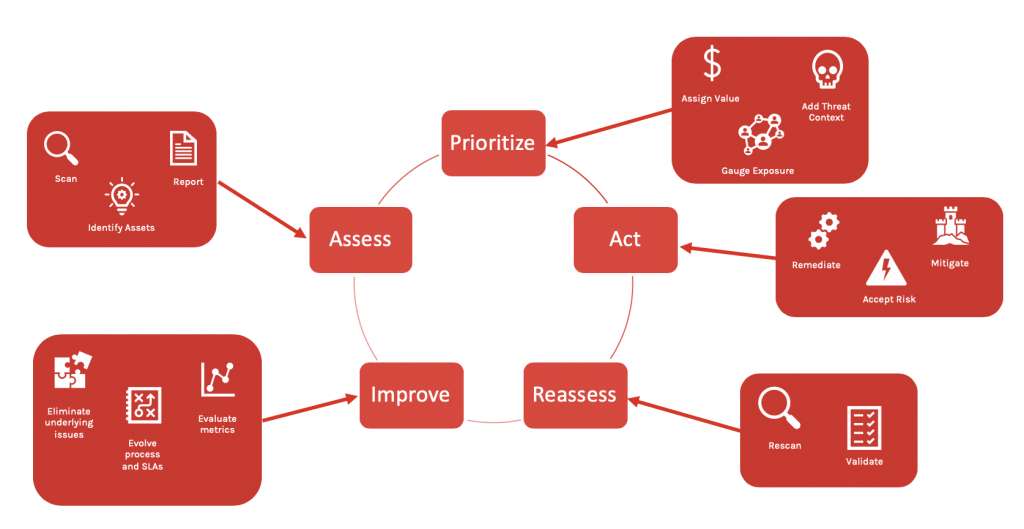
Vulnerability management can be defined as the process of identifying, analyzing, and addressing weaknesses and vulnerabilities present in software products, networks, or systems. It involves continuous discovery, tracking, reporting, and mitigation of known vulnerabilities to prevent potential threats from being exploited. Thus making it an important practice for any organization as it helps maintaining a secure environment, meeting regulatory compliance obligations, and reducing risks from cybersecurity threats.
Elasticsearch offers numerous benefits when applied to vulnerability management processes, providing both automation and scalability to address the increasing volume and complexity of incoming vulnerabilities. Here are some specific use cases where Elasticsearch might play a vital role in vulnerability management:
- Vulnerability Correlation: Elasticsearch allows security teams to correlate vulnerabilities across their entire environment by storing and searching through large volumes of scan results from various sources. This helps prioritize remediation efforts and ensure critical assets receive the most attention.
- Patch Management: Elasticsearch can help organizations efficiently manage patches and updates for known vulnerabilities. With accurate tracking of installed software versions, IT administrators can proactively apply necessary patches before vulnerabilities become exploitable.
- Asset Discovery & Tracking: Organizations often struggle with asset discovery and tracking, especially in dynamic environments with rapidly changing infrastructures. Elasticsearch can aid in identifying all connected devices on a network, providing contextual information around each asset, and associating detected vulnerabilities accordingly.
- Compliance Monitoring: To meet industry regulations such as PCI DSS, HIPAA, GDPR, etc., organizations must continuously monitor for compliance gaps and ensure effective risk mitigation measures are in place. Elasticsearch enables faster scanning, reporting, and auditing processes, making it easier to maintain regulatory compliance.
- False Positive Filtering: Security professionals spend significant time manually reviewing vast amounts of scan results to distinguish actual issues from false positives. Leveraging Elasticsearch’s full text search functionality, security teams can automatically reduce noise levels by weeding out unlikely matches.
- Contextual Intelligence Sharing: With open APIs, integration into numerous third-party systems is achievable, enabling collaboration and sharing of data insights among stakeholders. By consuming external feeds such as threat intelligence reports, incident notifications, and CVE advisories.
We went through a veriety of cybersecurity related use cases for Elasticsearch and then focused on the vulnerability management use case. In a next article, we will implement a vulnerability tracking system based on Elasticsearch. Stay tuned!
That’s all folks
I hope you enjoyed this article, feel free to leave a comment or reach out on twitter @bachiirc.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK