

Radware thwarts tsunami-size DDoS attack, spans seven days and 20 attack waves
source link: https://itwire.com/guest-articles/guest-opinion/radware-thwarts-tsunami-size-ddos-attack,-spans-seven-days-and-20-attack-waves.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Monday, 26 June 2023 12:23
Radware thwarts tsunami-size DDoS attack, spans seven days and 20 attack waves
By Shira Sagiv, vice president of products portfolio, RadwareGUEST OPINION: The cyber security world is in turmoil. A new generation of aggressive, layer 7 (L7), HTTPS Flood attacks, also known as Web DDoS Tsunami attacks, is disrupting the market by bypassing organisations’ traditional DDoS protection and web application firewall (WAF) solutions.
The destructive attacks, which roll out in multiple waves, last for days, hit with ultra-high volumes, and are aimed at wearing down an organisation’s security team. They also masquerade as legitimate traffic, making them very difficult to detect and mitigate.
Recently, my company took on one of these attacks to defend a customer and major global business. The attack started with a ransom demand and evolved daily with more attacks and demands.
This is what we encountered:
• Ultra-high volumes: Some attack waves peaked at nearly two million requests per second (RPS).
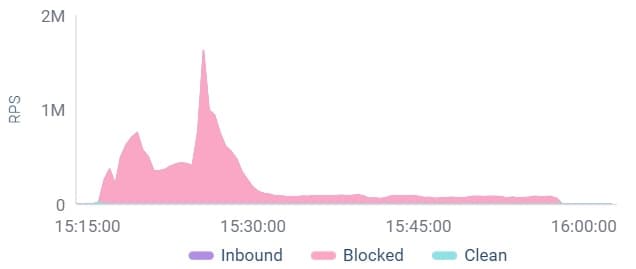
Web DDoS Tsunami attack wave peaking at nearly 2 million RPS
• Persistent and long attacks: Over the course of seven days, we observed nearly 20 different waves. Some lasted several hours, reaching over 10 billion requests in aggregate.
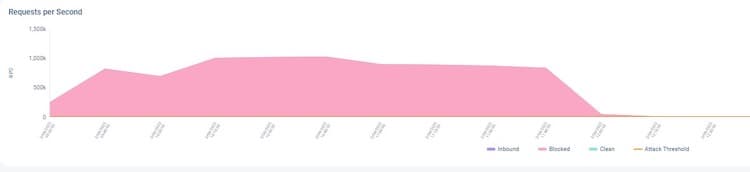
Persistent Web DDoS Tsunami attack wave of over 1 million RPS for almost 3 hours
• Complex attacks: They were encrypted and crafted as HTTPS GET requests, posing as legitimate web requests.
In the news, we often see attacks making headlines over huge RPS numbers. What makes this new breed of attack and recent attack campaign unique is the dangerous combination of volume, plus duration and complexity.
As part of their latest campaigns, hackers are combining network and application layer attacks and using new tools to create these giant L7 DDoS Tsunamis. To elude detection, the attacks leverage multiple evasion techniques, such as randomising HTTP headers, cookies, spoofing IPs, and more.
Defending against this combination during a prolonged period of attack calls for more than traditional rate-limiting solutions. The reality is traditional mitigation tools based on pre-existing signatures or rate-based detections are not built to protect against these attacks.
Network-based DDoS protection cannot detect and mitigate L7 DDoS attacks. Standard on-prem or cloud-based WAFs fail to keep up with the scale and randomisation. And rate-limiting techniques have a major negative impact on legitimate traffic.
As a result, companies are being caught off guard. Without a behavioural-based approach and automated real-time signatures, standard protections are simply overwhelmed and outmanoeuvred, and businesses are left vulnerable.
To defend against this emerging generation of DDoS attacks, companies need to start thinking differently about mitigation solutions. To mitigate automated offensive cybersecurity activity, organisations must deploy defensive automation capabilities.
This includes behavioural-based algorithms that can automatically detect and quickly generate new signatures for unknown malicious requests at a high scale, on the fly, and in real-time without generating false positives and blocking legitimate traffic.
The level of service and support that back the solution is also important, especially now when so many security teams are running lean.
The evolution of the DDoS attack might not be new, but the debut of the Web DDoS Tsunami represents a whole new level of sophisticated attacks and emboldened actors.
Read 471 times
Please join our community here and become a VIP.
Subscribe to ITWIRE UPDATE Newsletter here
JOIN our iTWireTV our YouTube Community here
BACK TO LATEST NEWS here
GARTNER MARKET GUIDE FOR NDR 2022
You probably know that we are big believers in Network Detection and Response (NDR).Did you realise that Gartner also recommends that security teams prioritise NDR solutions to enhance their detection and response?
Picking the right NDR for your team and process can sometimes be the biggest challenge.
If you want to try out a Network Detection and Response tool, why not start with the best?
Vectra Network Detection and Response is the industry's most advanced AI-driven attack defence for identifying and stopping malicious tactics in your network without noise or the need for decryption.
Download the 2022 Gartner Market Guide for Network Detection and Response (NDR) for recommendations on how Network Detection and Response solutions can expand deeper into existing on-premises networks, and new cloud environments.
PROMOTE YOUR WEBINAR ON ITWIRE
It's all about Webinars.Marketing budgets are now focused on Webinars combined with Lead Generation.
If you wish to promote a Webinar we recommend at least a 3 to 4 week campaign prior to your event.
The iTWire campaign will include extensive adverts on our News Site itwire.com and prominent Newsletter promotion https://itwire.com/itwire-update.html and Promotional News & Editorial. Plus a video interview of the key speaker on iTWire TV https://www.youtube.com/c/iTWireTV/videos which will be used in Promotional Posts on the iTWire Home Page.
Now we are coming out of Lockdown iTWire will be focussed to assisting with your webinars and campaigns and assistance via part payments and extended terms, a Webinar Business Booster Pack and other supportive programs. We can also create your adverts and written content plus coordinate your video interview.
We look forward to discussing your campaign goals with you. Please click the button below.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK
