Cyber Apocalypse 2021 五道硬件小题:总线电路信号分析
source link: https://xuanxuanblingbling.github.io/iot/2022/10/24/logic2/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Cyber Apocalypse 2021 五道硬件小题:总线电路信号分析
五道使用logic2逻辑分析仪进行总线电路信号分析的小题,主要涉及UART、I2C与SPI总线协议。
参考WP:
Serial Logs
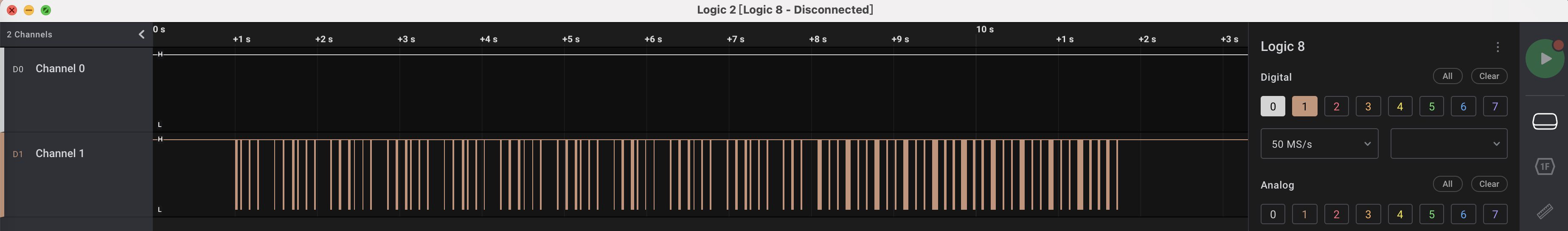
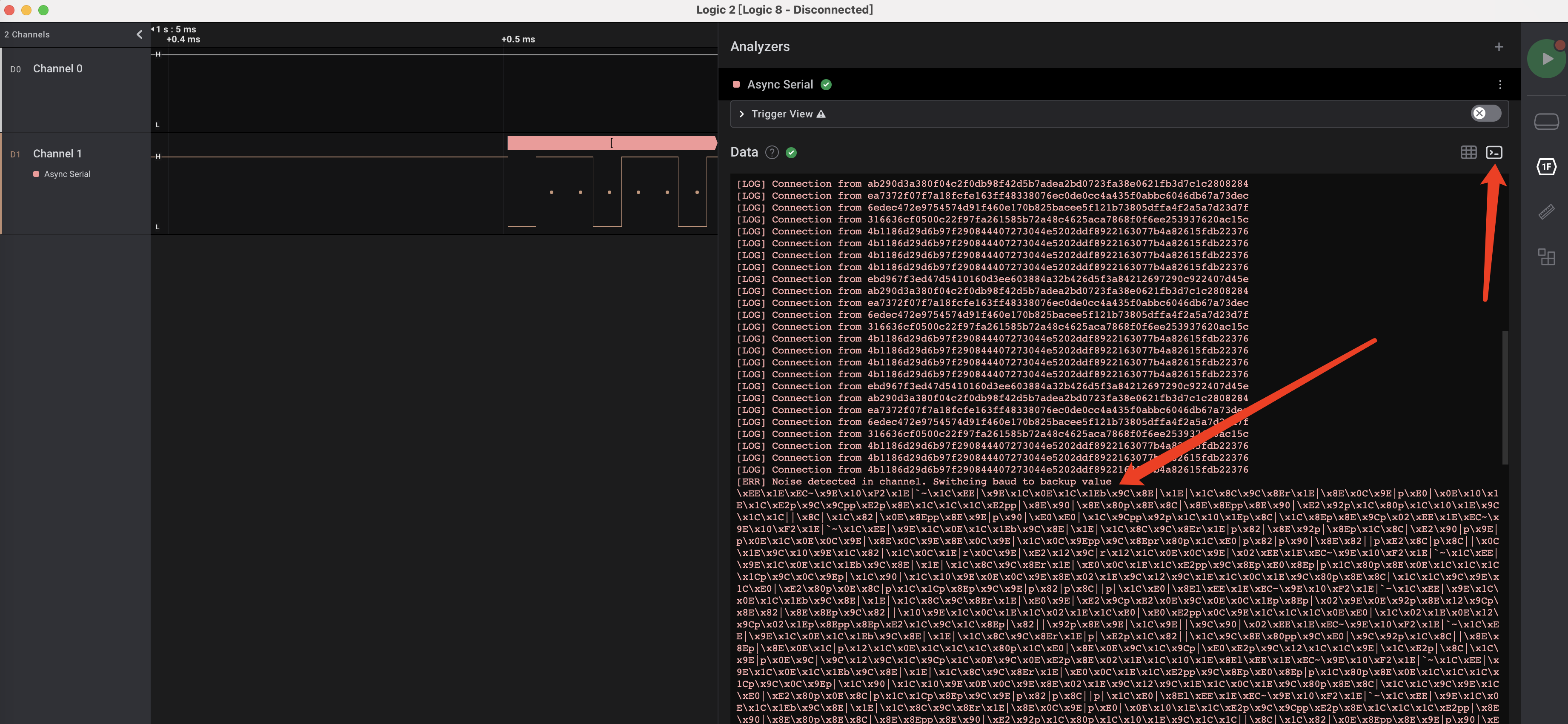
使用logic2打开发现只有一路信号,通过题目名称交叉验证应为UART串口信号:
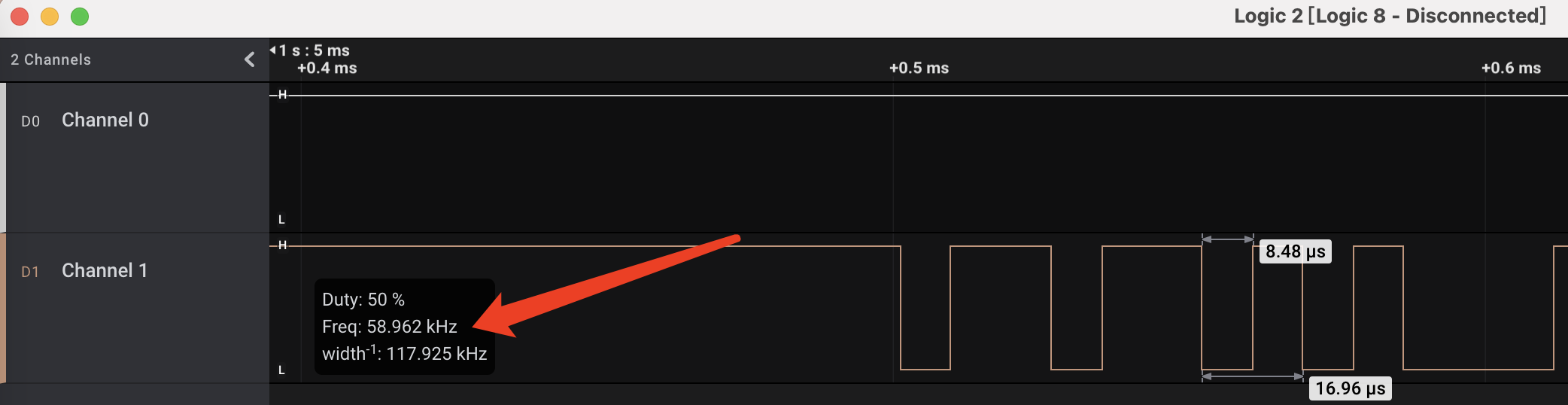
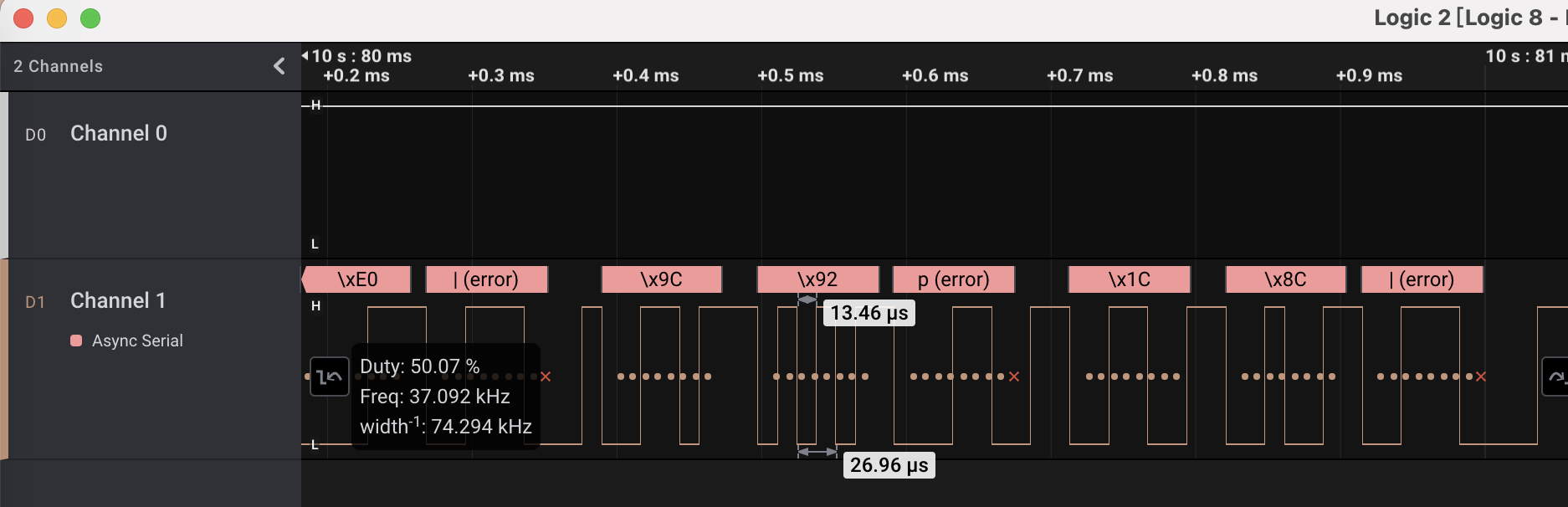
通过查看开始部分最紧凑的波形猜测波特率,这里显示的频率为58.962kHz,由于这里是通过两个高低电平为一个周期计算的频率,所以对应的比特率应为58962*2=117924,接近于常用比特率115200:
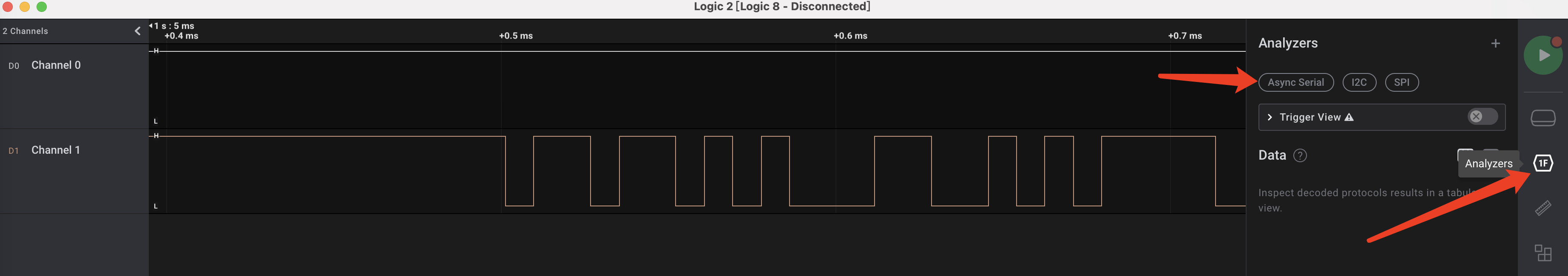
使用Analyzers功能识别信号为Async Serial:
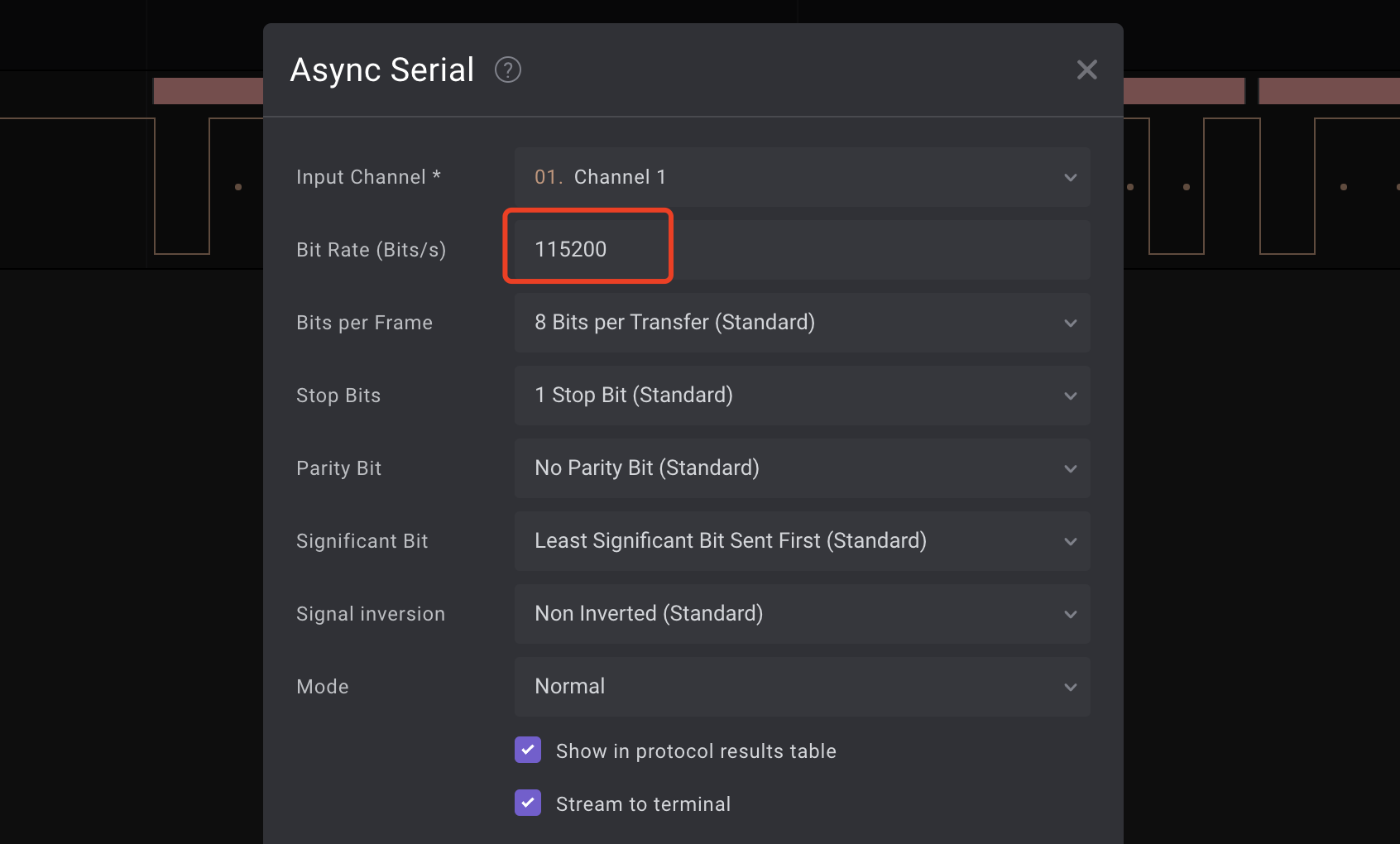
设置波特率为115200:
然后即可在解析功能中看到通信字符串,不过发现并没有解出flag,并且在提示更换波特率后无法继续识别字符串,因此猜测flag在更换波特率后传输的数据中:
定位到无法解析的数据,仍然是找到最紧凑的波形,计算波特率应为 37000*2 = 74000 左右:
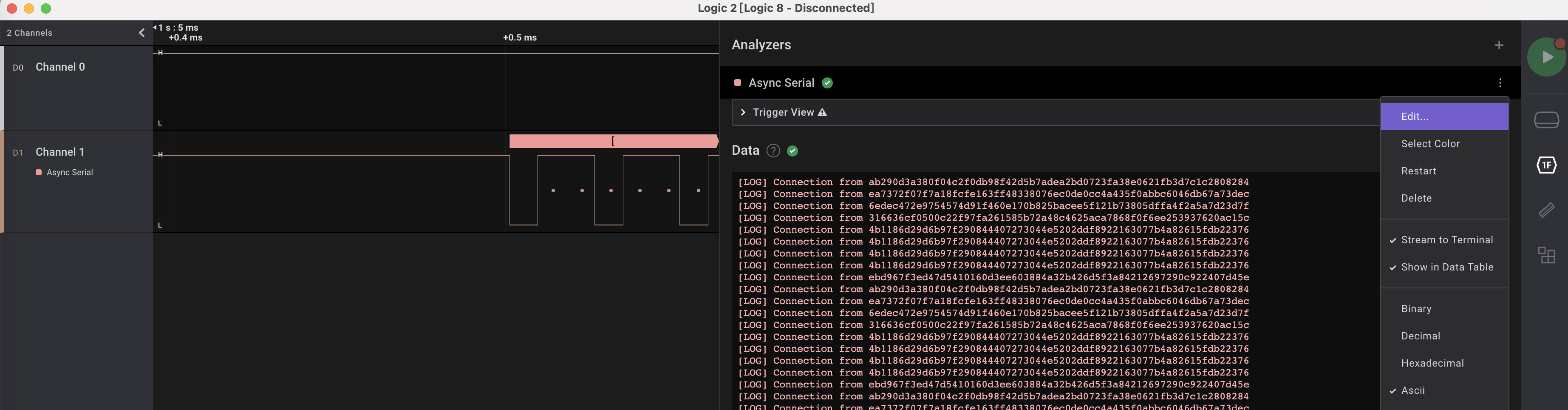
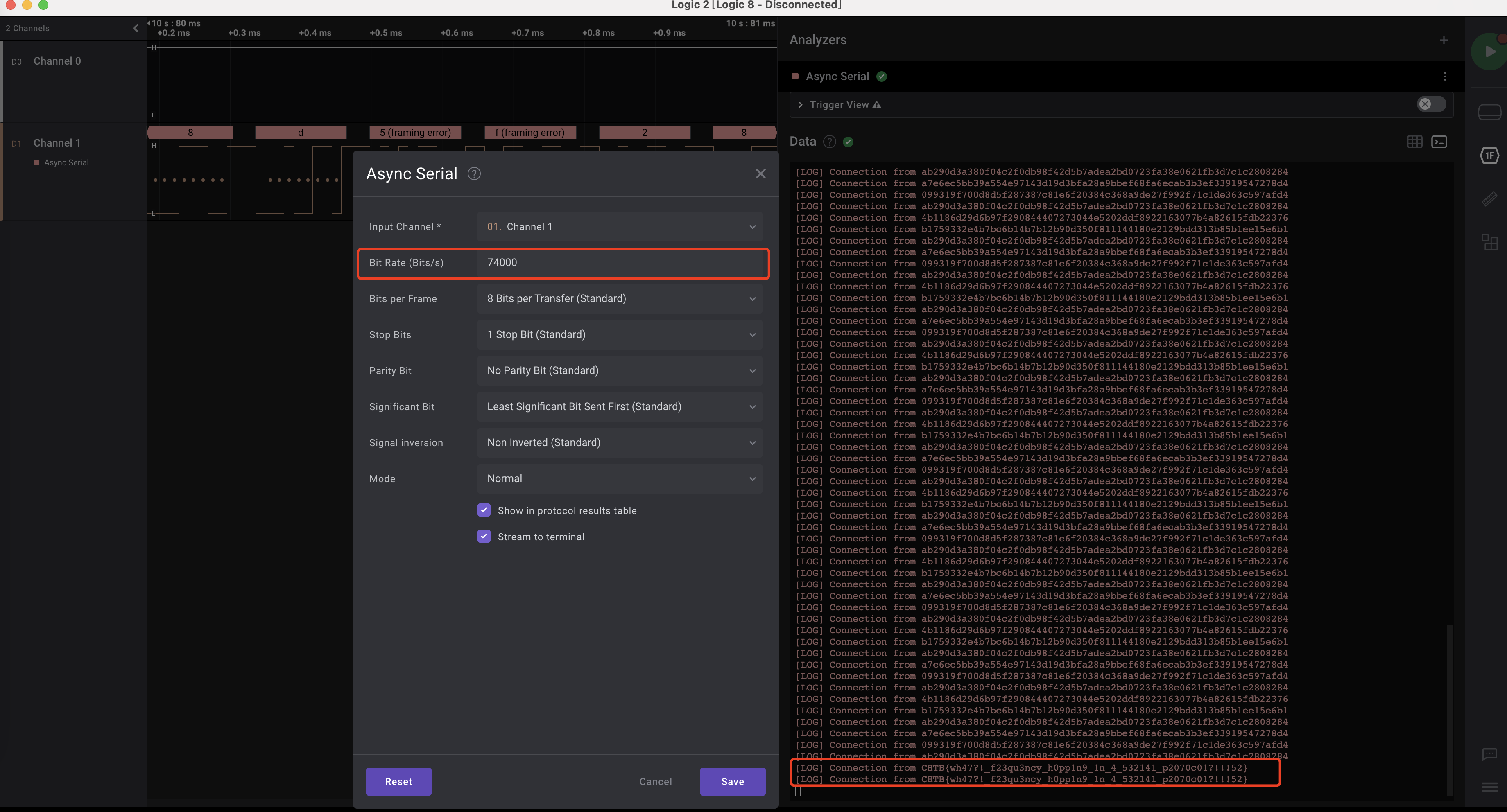
在Analyzers功能中使用edit更换波特率:
设置波特率为74000,即可在数据窗口中看到flag:
flag为:
CHTB{wh47?!_f23qu3ncy_h0pp1n9_1n_4_532141_p2070c01?!!!52}
Compromised
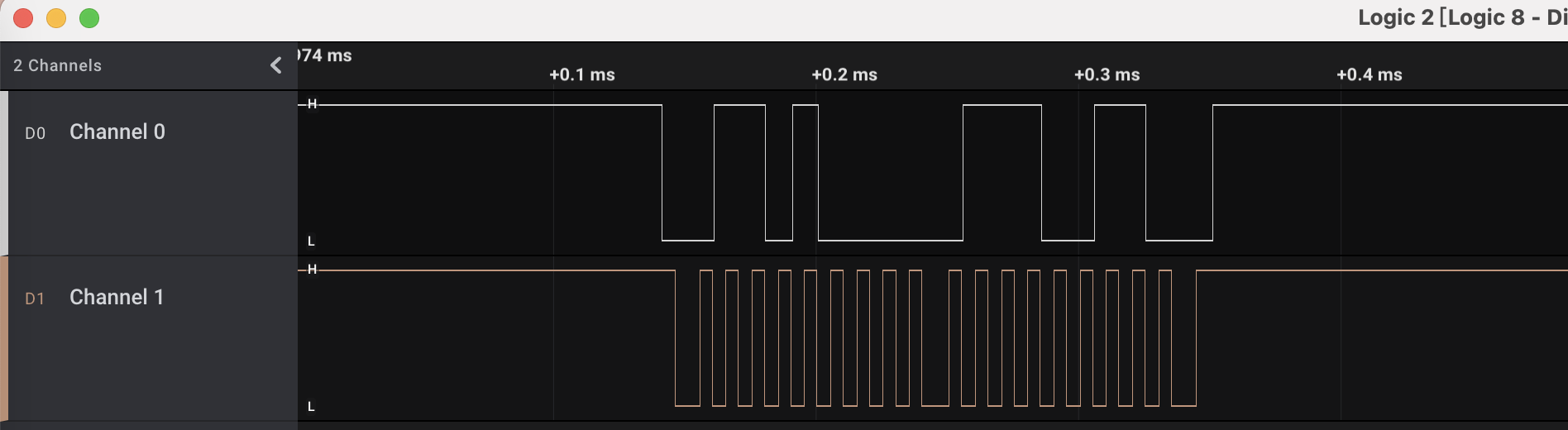
使用logic2打开发现有两路信号,并且channel1显然为时钟信号,所以推测为i2c信号:
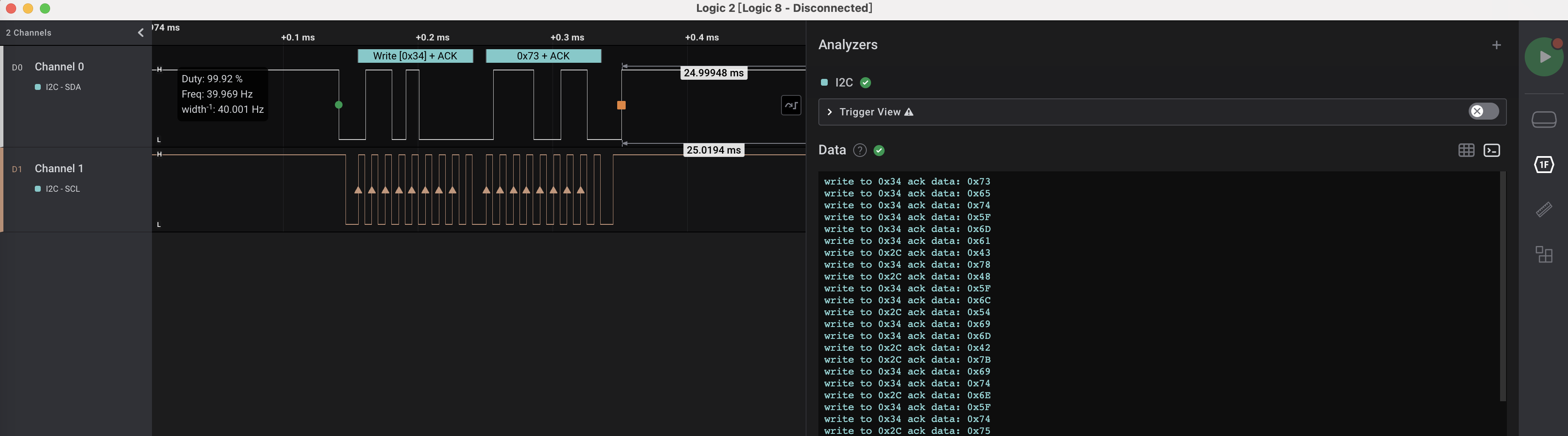
使用Analyzers功能识别信号为i2c,channel0为数据,channel1为时钟,然后即可在数据解析窗口中看到只有写动作:
经过分析,主要是向0x2C、0x34两个地址进行写操作,将数据按目标地址进行区分并hex解码,即可发现按时间顺序提取所有向0x2c的写的数据,即为flag:
write to 0x2C ack data: 0x43
write to 0x2C ack data: 0x48
write to 0x2C ack data: 0x54
write to 0x2C ack data: 0x42
write to 0x2C ack data: 0x7B
write to 0x2C ack data: 0x6E
write to 0x2C ack data: 0x75
write to 0x2C ack data: 0x31
write to 0x2C ack data: 0x31
write to 0x2C ack data: 0x5F
write to 0x2C ack data: 0x37
write to 0x2C ack data: 0x33
write to 0x2C ack data: 0x32
write to 0x2C ack data: 0x6D
write to 0x2C ack data: 0x31
write to 0x2C ack data: 0x6E
write to 0x2C ack data: 0x34
write to 0x2C ack data: 0x37
write to 0x2C ack data: 0x30
write to 0x2C ack data: 0x32
write to 0x2C ack data: 0x35
write to 0x2C ack data: 0x5F
write to 0x2C ack data: 0x63
write to 0x2C ack data: 0x34
write to 0x2C ack data: 0x6E
write to 0x2C ack data: 0x5F
write to 0x2C ack data: 0x38
write to 0x2C ack data: 0x32
write to 0x2C ack data: 0x33
write to 0x2C ack data: 0x34
write to 0x2C ack data: 0x6B
write to 0x2C ack data: 0x5F
write to 0x2C ack data: 0x34
write to 0x2C ack data: 0x5F
write to 0x2C ack data: 0x35
write to 0x2C ack data: 0x33
write to 0x2C ack data: 0x32
write to 0x2C ack data: 0x31
write to 0x2C ack data: 0x34
write to 0x2C ack data: 0x31
write to 0x2C ack data: 0x5F
write to 0x2C ack data: 0x35
write to 0x2C ack data: 0x79
write to 0x2C ack data: 0x35
write to 0x2C ack data: 0x37
write to 0x2C ack data: 0x33
write to 0x2C ack data: 0x6D
write to 0x2C ack data: 0x21
write to 0x2C ack data: 0x40
write to 0x2C ack data: 0x35
write to 0x2C ack data: 0x32
write to 0x2C ack data: 0x29
write to 0x2C ack data: 0x23
write to 0x2C ack data: 0x40
write to 0x2C ack data: 0x25
write to 0x2C ack data: 0x7D
hex解码即为flag:
➜ python3
>>> bytes.fromhex('434854427B6E7531315F3733326D316E34373032355F63346E5F383233346B5F345F3533323134315F35793537336D21403532292340257D')
b'CHTB{nu11_732m1n47025_c4n_8234k_4_532141_5y573m!@52)#@%}'
Secure
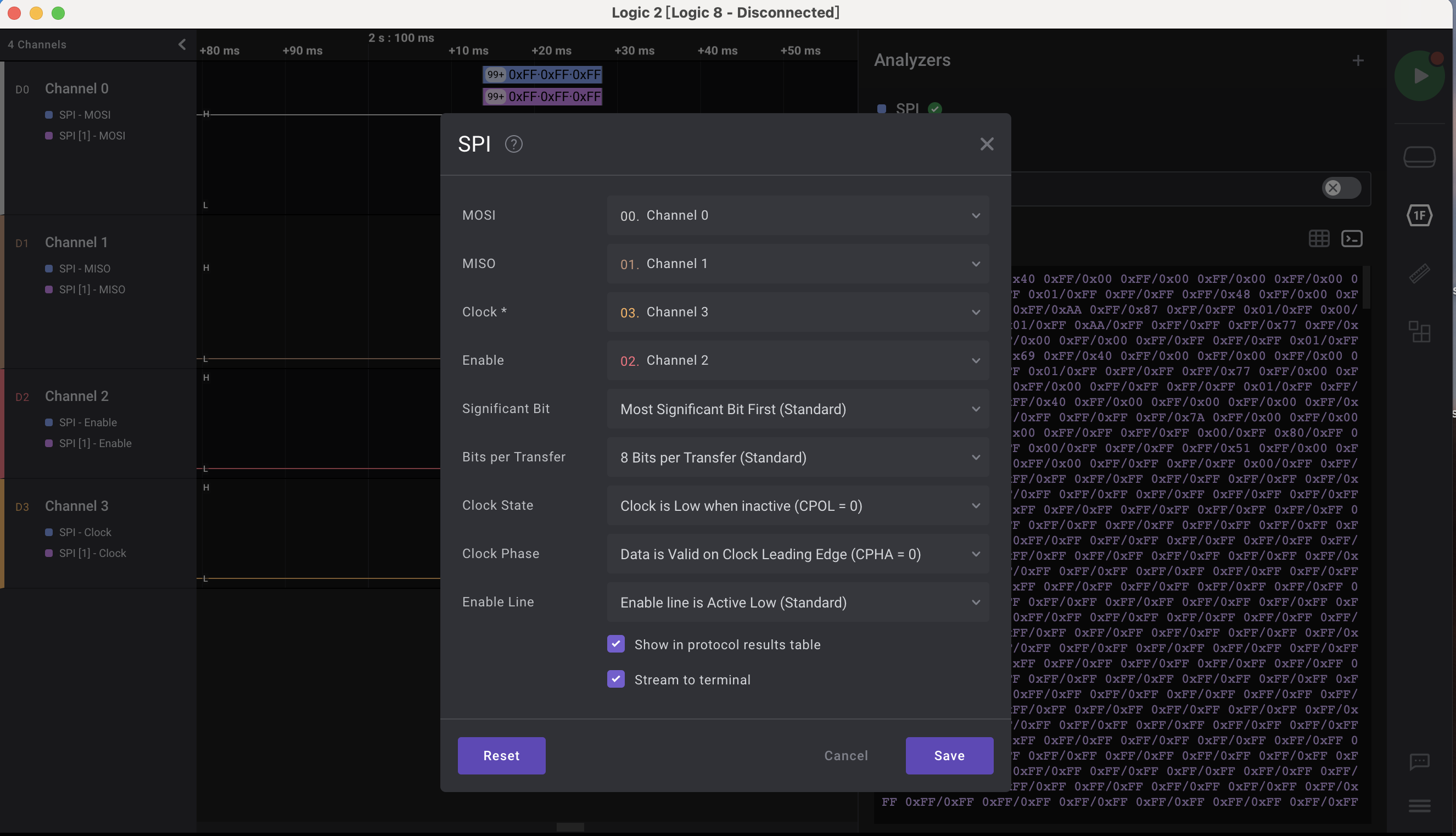
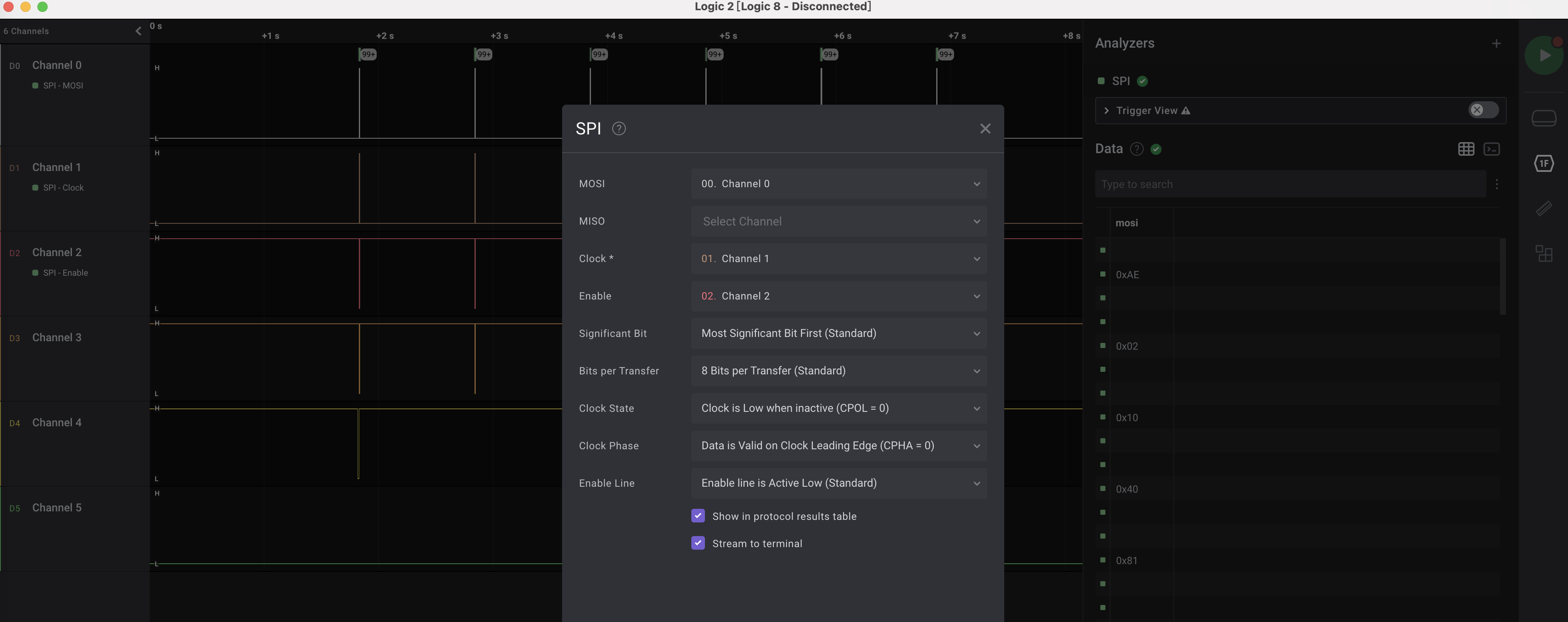
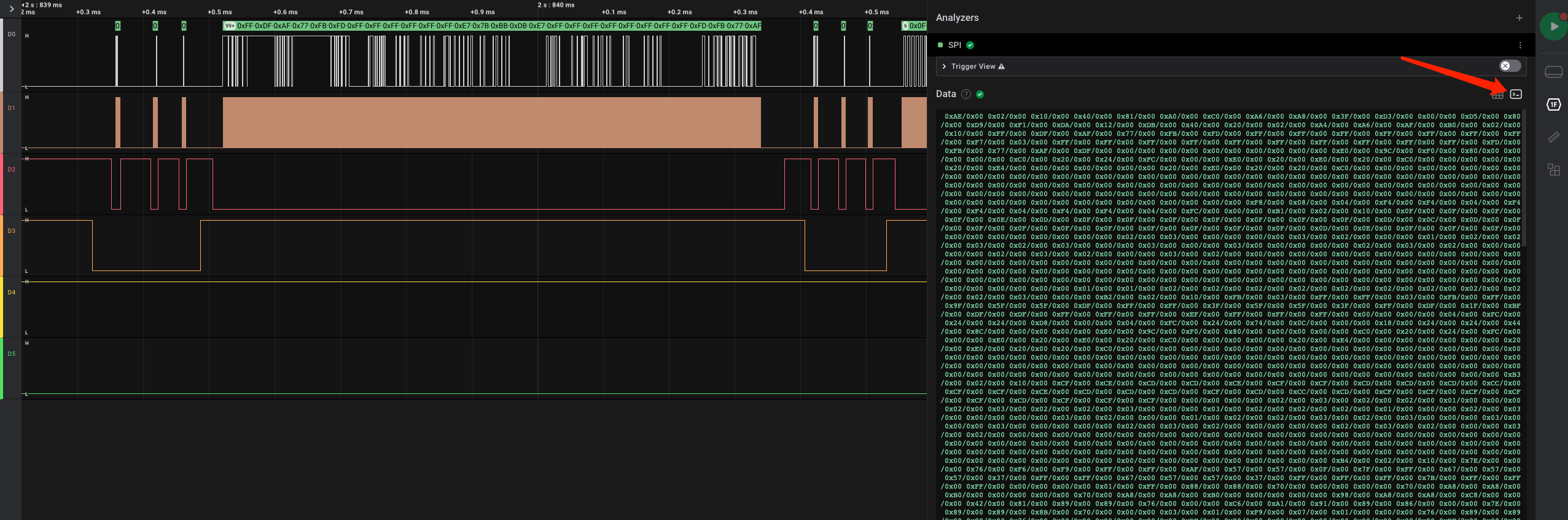
四路信号,题目信息说是SD卡,SD卡一般支持SDIO、SPI两种接口,但logic2里没有SDIO的解析器,因此尝试按SPI解析:
按SPI解析后,将0x??/0xff的相关数据筛出,然后hex解码即可筛出flag:
➜ python3
>>> bytes.fromhex('FFFF01FFFF01000001AAFFFFFF01FFFFFF01FFFFFF01FFFFFF00FFFFFF0080FF8000FFFFFF00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFE000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000020400060ACACA810000007FAF3B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000055AA5CD8FFFFFF00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEEB3C904D53444F53352E3000024002000200020000F8EF003F00FF00810000007FAF3B008000294A04D0064E4F204E414D4520202020464154313620202033C98ED1BCF07B8ED9B800208EC0FCBD007C384E247D248BC199E83C01721C83EB3A66A11C7C26663B07268A57FC750680CA0288560280C31073EB33C98A461098F7661603461C13561E03460E13D18B7611608946FC8956FEB82000F7E68B5E0B03C348F7F30146FC114EFE61BF0000E8E600723926382D741760B10BBEA17DF3A66174324E740983C7203BFB72E6EBDCA0FB7DB47D8BF0AC9840740C487413B40EBB0700CD10EBEFA0FD7DEBE6A0FC7DEBE1CD16CD19268B551A52B001BB0000E83B0072E85B8A5624BE0B7C8BFCC746F03D7DC746F4297D8CD9894EF2894EF6C606967DCBEA030000200FB6C8668B46F86603461C668BD066C1EA10EB5E0FB6C84A4A8A460D32E4F7E20346FC1356FEEB4A525006536A016A10918B4618969233D2F7F691F7F64287CAF7761A8AF28AE8C0CC020ACCB80102807E020E7504B4428BF48A5624CD136161720B40750142035E0B497506F8C341BB000060666A00EBB0424F4F544D4752202020200D0A52656D6F7665206469736B73206F72206F74686572206D656469612EFF0D0A4469736B206572726F72FF0D0A507265737320616E79206B657920746F20726573746172740D0A00000000000000ACCBD855AA1602FFFFFF00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFE3031202020202020545854201043F59273507850000002977750250073000000444154414C4F4720545854000000000821282128000000082128070064190000544553542020202054585400000000082128212800000008212808005E0000004B455920202020205458540000000008212821280000000821280900B6000000534B4559202020205458540000000008212821280000000821280A006A00000053454352455420204B45590000000008212821280000000821280B00560000004D415354455220204B45590000000008212821280000000821280C0058000000412E005F00300031002E000F00687400780074000000FFFFFFFF0000FFFFFFFF5F307E31202020205458542200460697775078500000069777501F0000100000E56D0073000000FFFFFFFF0F009AFFFFFFFFFFFFFFFFFFFFFFFF0000FFFFFFFFE52E00540065006D0070000F009A6F0072006100720079004900000074006500E5454D504F527E312020201200890FA87250725000000FA87250160000800000E52E0066007300650076000F00DA65006E0074007300640000000000FFFFFFFFE5534556454E7E31202020120064A676785078500000A6767850050000800000E5302020202020205458542010C2F59273503652000038AE7350000000000000412E005F00310030002E000F00ED7400780074000000FFFFFFFF0000FFFFFFFF3299FFFFFF00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFE434854427B3550315F31355F63306D6D306E5F306E5F6D336D3032795F643376316333355F214035327D0D0A434854427B3550315F31355F63306D6D306E5F306E5F6D336D3032795F643376316333355F214035327D0D0A000000000000000000000000000000000000000000000000000000000000FFFF0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFF000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004160')
CHTB{5P1_15_c0mm0n_0n_m3m02y_d3v1c35_!@52}
Off the grid
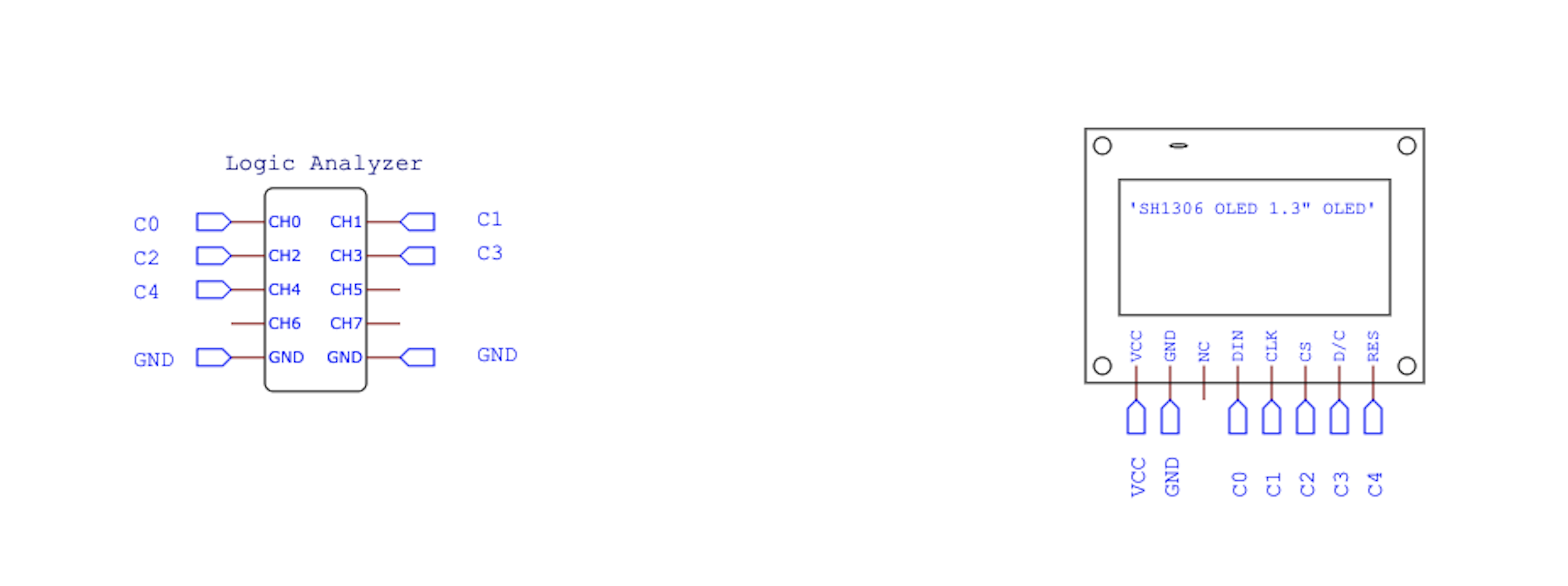
题目给出了电路图,为SPI接口的OLED屏幕,所以推测flag画在了屏幕上:
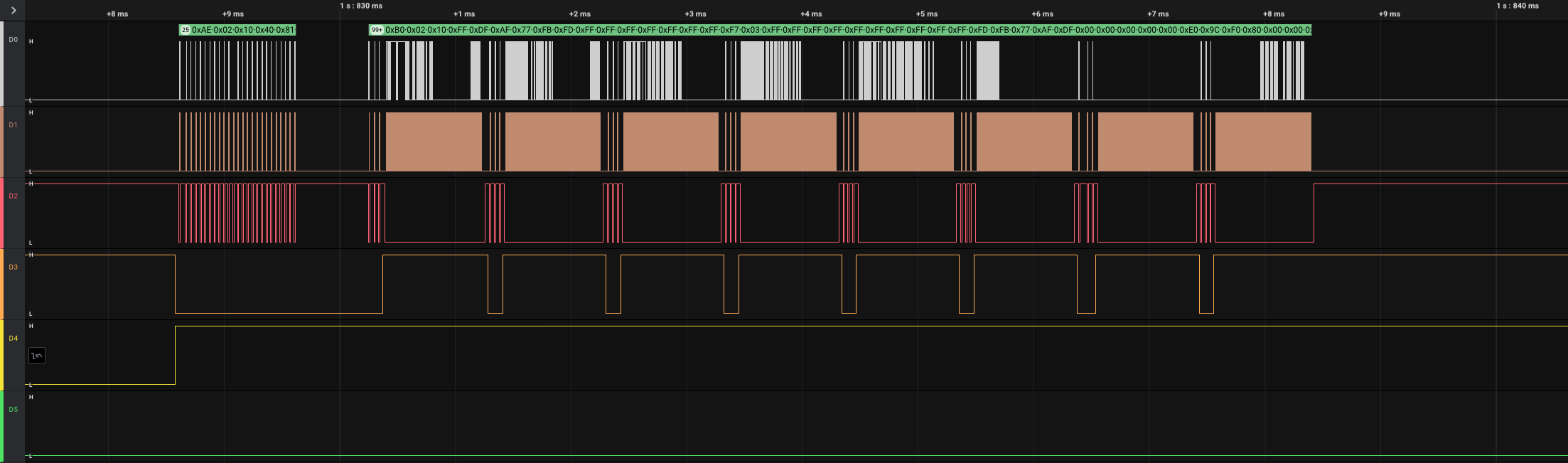
使用logic2打开,对应设置0,1,2三个通道即可,3通道为OLED屏幕自身D/C功能的信号,不为SPI标准信号。4通道为reset,没有更多数据,因此3,4通道不用设置,解析后总览发现总共有6大段:
放大后6大段中只有第大1段里有9小段,其余均有8小段,根据3通道在第1大段第1小段中的低电平可以推测这为OLED的初始命令配置:
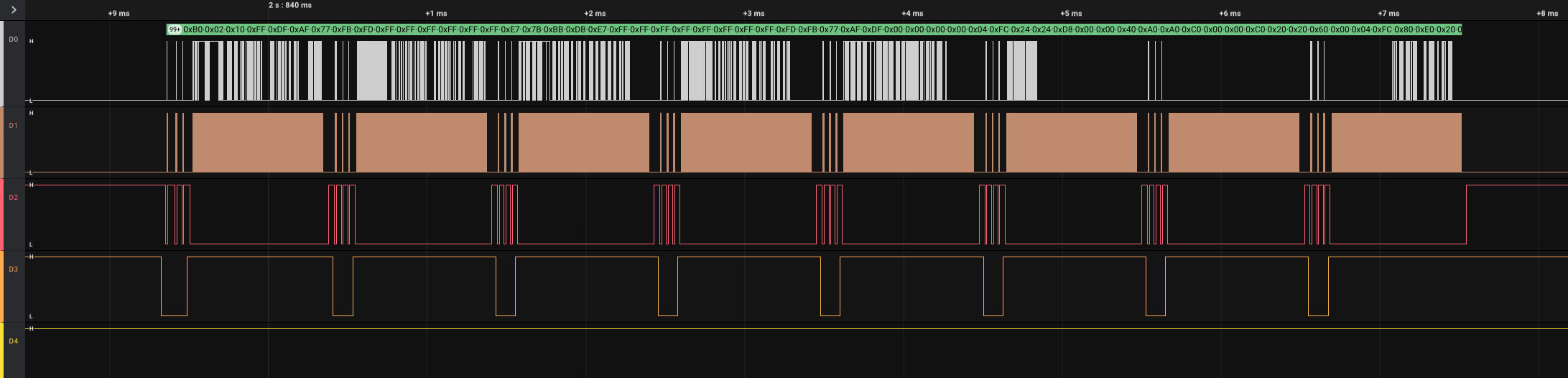
例如第4大段放大后,可以看到其中只有8小段:
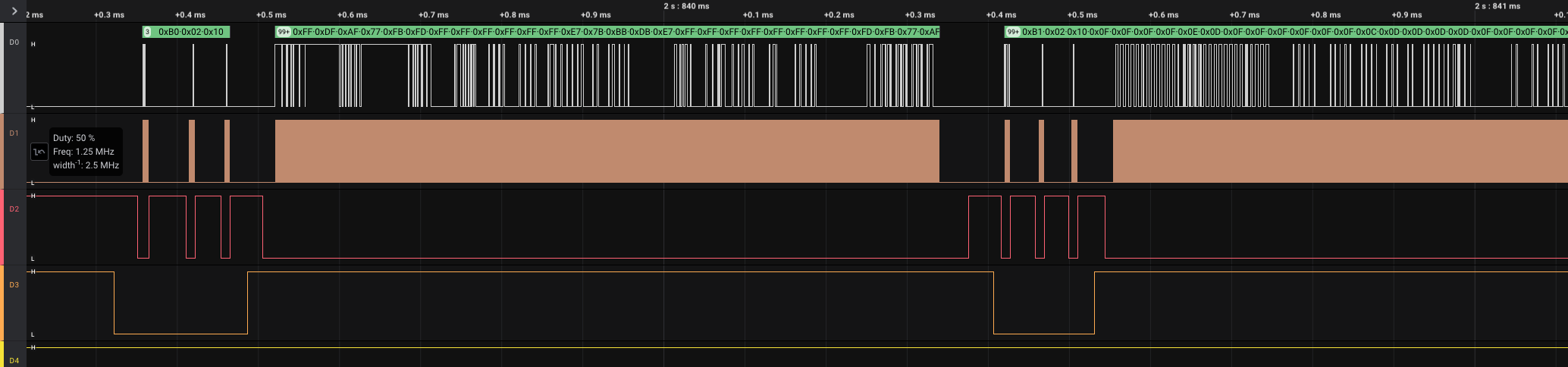
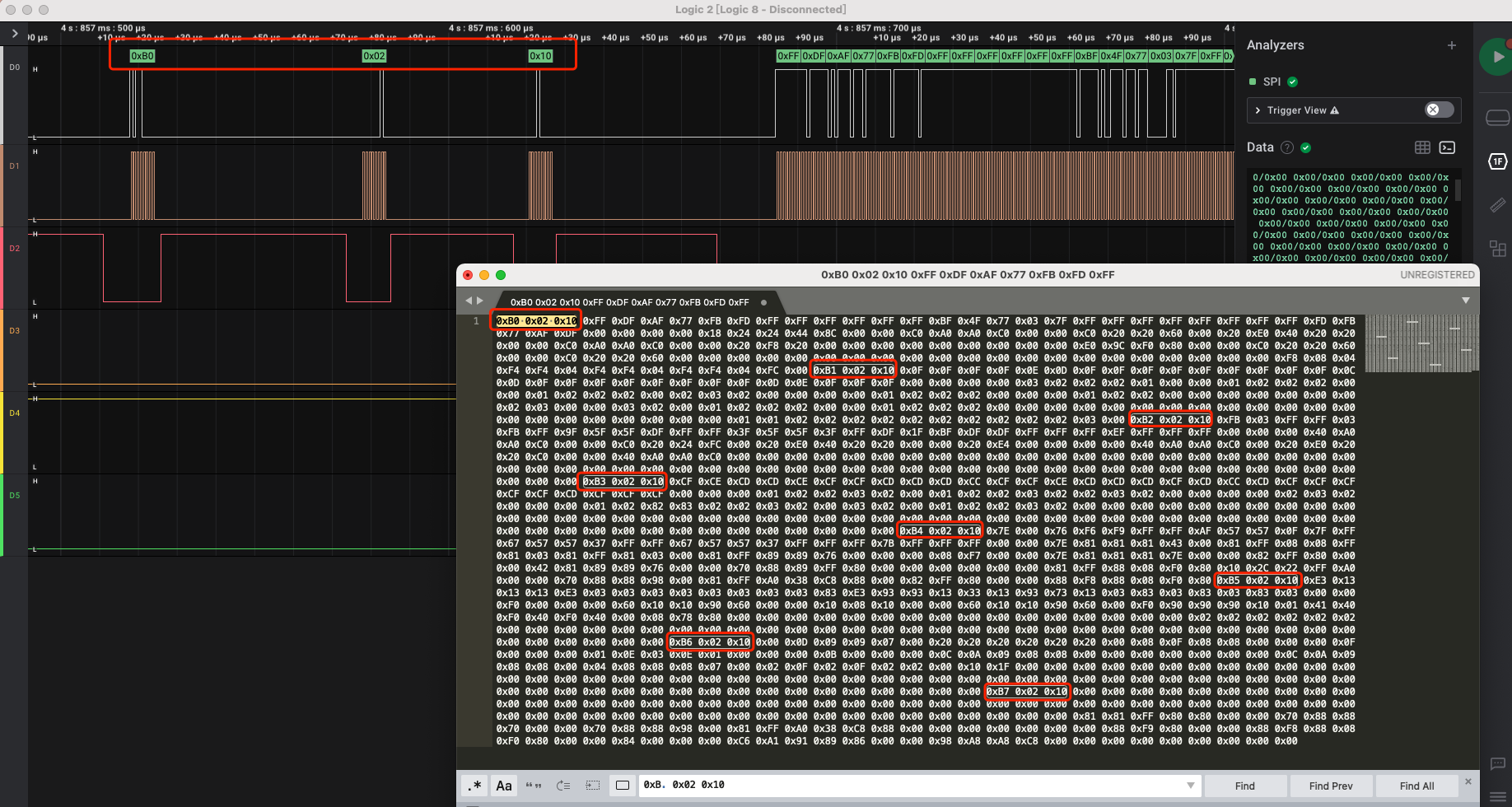
重点关注数据信号,即0通道,放大第4大段的前2个小段发现在大量数据前有3个字节疑似前导字节:
可以在数据解析窗口中把解析数据复制出来:
以第4大段数据为例,其中的8小段每段都有3个字节前导,其中主要信息变化为第1字节的0xb0-0xb7的递增,所以应该没有关键的显示数据本身,删掉:
然后以十六进制整理好数据发现正好2048字节,所以hex解码后正好为1024字节(第4大段的全部数据):
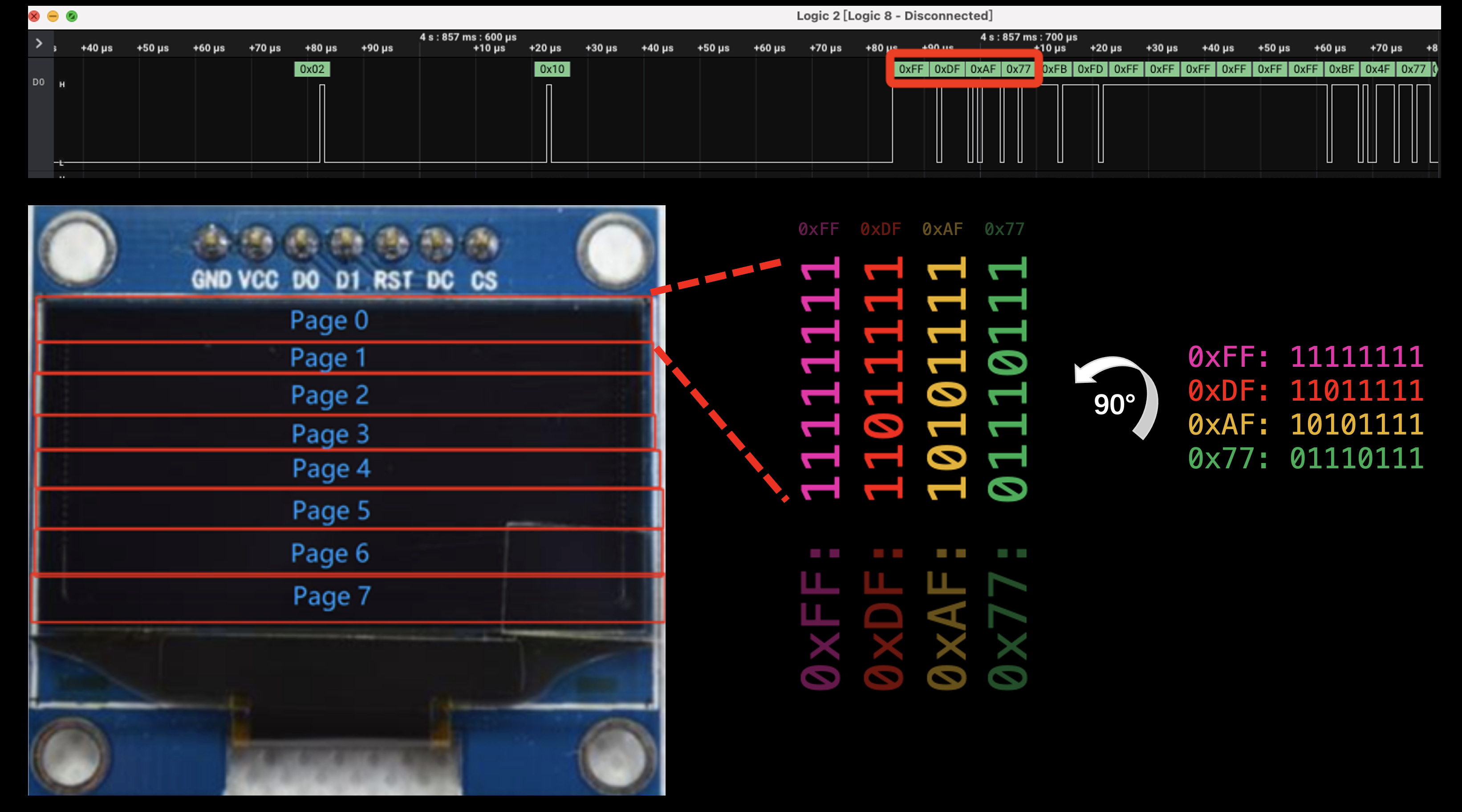
OLED为64行*128列,显示点阵总数为8192,点阵每点无颜色,无深浅,只有亮灭,所以显示数据应为二进制。而第4大段数据总共1024字节,以二进制角度考虑,每个字节8bit,1024 * 8正好为8192,可以填满屏幕。所以,6大段为应6个不同的屏幕画面。不过直接按64行或128列顺序解析这1024字节是错误的,因为他这玩意是按照8个页来显示的,每小段是先横着把每页填完(8行 * 128列),然后在竖着填下一个页,总共8页。例如第4大段第1小段的前4个字节,每个字节拆成二进制单独一列(8行):
操作图像比较费劲,所以把先把数据转为0、1字符,然把0用空格替代,1用井号替代,直接在shell窗口中显示:
a = bytes.fromhex('FFDFAF77FBFDFFFFFFFFFFFFBF4F77037FFFFFFFFFFFFFFFFFFDFB77AFDF00000000182424448C0000C0A0A0C00000C02020600020E04020200000C0A0A0C0000020F820000000000000000000E09CF0800000C02020600000C0202060000000000000000000000000000000000000000000F80804F4F404F4F404F4F404FC000F0F0F0F0E0D0F0F0F0F0F0F0F0F0F0C0D0F0F0F0F0F0F0F0F0D0E0F0F0F0000000003020202010000010202020000010202020002030200000000010202020000000102020000000000000002030000030200010202020000010202020000000000000000000000000000000000000000000101020202020202020202020300FB03FFFF03FBFF9F5F5FDFFFFF3F5F5F3FFFDF1FBFDFDFFFFFFFEFFFFFFF00000040A0A0C00000C02024FC0020E0402020000020E40000000040A0A0C00020E02020C0000040A0A0C000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000CFCECDCDCECFCFCDCDCDCCCFCFCECDCDCDCFCDCCCDCFCFCFCFCFCDCFCFCF00000001020203020001020203020203020000000002030200000001028283020203020003020001020203020000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007E0076F6F9FFFFAF57570F7FFF67575737FFFF67575737FFFFFF7BFFFFFF00007E818181430081FF0808FF810381FF81030081FF89897600000008F700007E8181817E000082FF80000042818989760000708889FF8000000000000081FF8808F080102C22FFA00000708888980081FFA038C8880082FF80000088F88808F080E3131313E3030303030303030383E39393133313937313038303830383030000F0000000601010906000001008100000601010906000F090909010014140F040F0400008788000000000000000000000000000000000020202020202000000000000000000000000000000000000000000000000000000000000000000000000000D0909070020202020202000080F08080000000F000000010E030E010000000B0000000C0A090808000000000000000C0A09080800040808080700020F020F020200101F00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000008181FF80800000708888700000708888980081FFA038C8880000000000000088F980000088F88808F080000084000000C6A1918986000098A8A8C8000000000000000000')
for k in range(8):
tmp = ''
for i in a[k*128:128*(k+1)]:
b = bin(i)[2:].zfill(8).replace('0',' ').replace('1',"#")
tmp += b
tmp2 = ''
for j in range(8):
for i in range(len(tmp)//8):
tmp2 += tmp[(7-j)+8*(i)]
tmp2 +='\n'
print(tmp2[:-1])
flag就在第四大段中,结果如下:
##############################
############################## ##
########################## #### ## ####### #### # ### # ### ## ## # ## #
# ## ######################### # # # # # # # # # # # # ## # # # # ## # ##
# ## ##################### ### # # # # # # # # # # # # # # # # #
# #### ### ## ####### # #### # ### # # # # ## ### ### # # ### # ### # ####
# ##### ## ## ##### ########## # # # # # # # # # # # # # # # # # # # # # # # #
# ###### ### #### ######## # # # # # # # # # # # # # # # #### # ### # # #
# ##### ## ##### ##### ####### # # # # # # # # # # # # # # # # # # # # # # # #
##### # ## ### ### ### ## ## ### #### # ### ### ### #### ### ## ## ### ### ## ### ### ##
############################## ##
############################## ######
# ##
### ######## # ### # # ### ##### # # #
# # # # # # # # # # # # # #
# # # # # # # # # # ###### #
# # #### # # # # # # # #### # # #
#### # # # # # # # # # # # #
# # # ### # # # # ###### #
# # # # # # # # # # # # #
### #### # # # # ##### ##### ### # # #
##
######
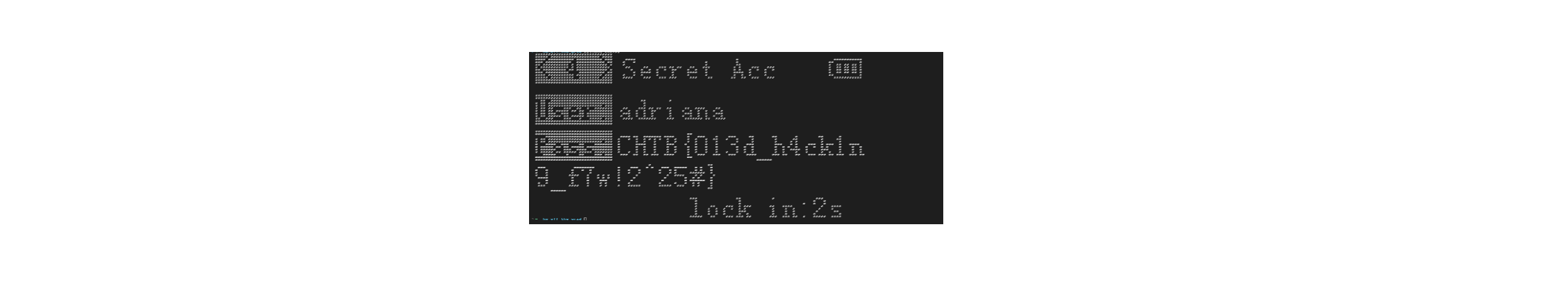
截图也可看清:
如果觉得不精致可以自由变换一下,压扁再缩小:
flag为:
CHTB{013d_h4ck1n9_f7w!2^25#}
hidden
这题信号比较诡异,虽然就一路信号,但不是默认标准的UART,解析过程纯misc,自行探索…
</article
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK