

Use the Azure Arc Managed Identity with Azure PowerShell
source link: https://www.thomasmaurer.ch/2022/10/use-the-azure-arc-managed-identity-with-azure-powershell/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Use the Azure Arc Managed Identity with Azure PowerShell
In this blog post we are going to have a look at how you can use the Azure Arc provided Azure Active Directory (Azure AD) managed identity (MSI) to authenticate in Azure PowerShell on your on-premises Linux and Windows Server machines.
The moment you want to run some automation directly on your servers, you often end up in a scenario where you need some credentials to run your PowerShell script. Now the issue with that is that you need to store or get your credentials from somewhere and that can be an issue. Luckly, Azure Arc provides you with an Azure Active Directory Managed Identity which can be used for that.
Azure PowerShell allows you an uncomplicated way to login using that managed identity.
Prerequisites
- On Windows, you must be a member of the local Administrators group or the Hybrid Agent Extension Applications group.
- On Linux, you must be a member of the himds group.
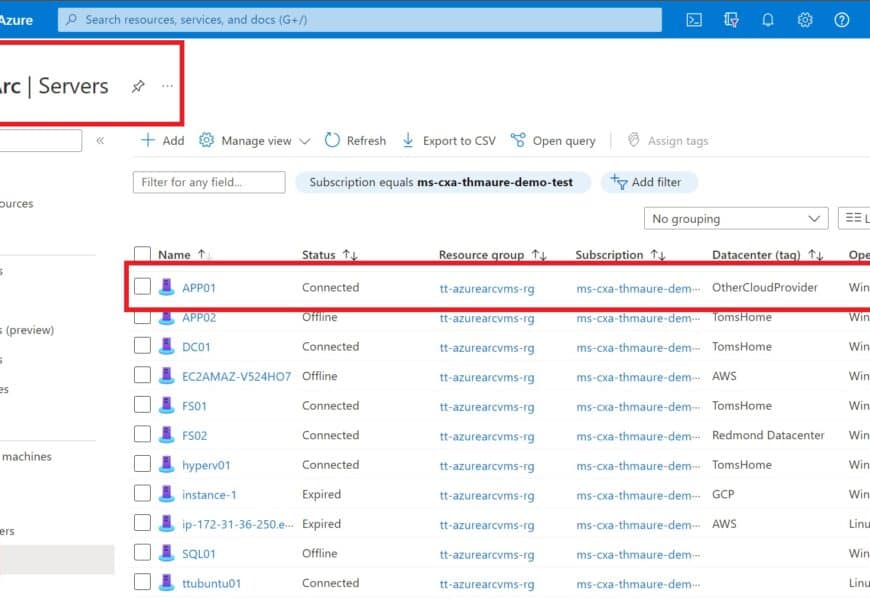
- I connected my servers to Azure using Azure Arc enabled servers and installed the Azure connected machine agent.
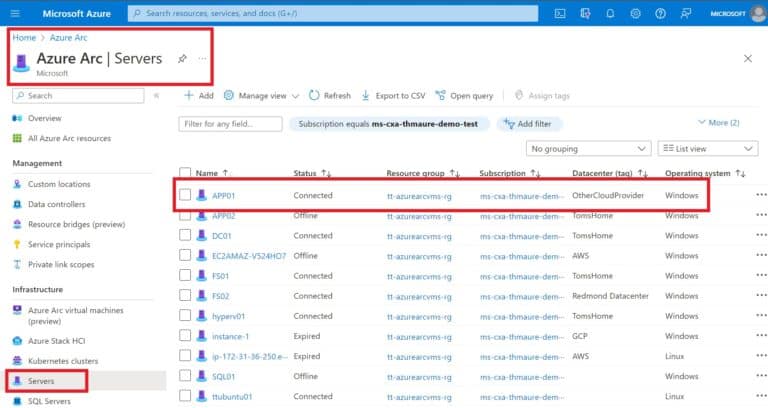
Azure Arc-enabled Server APP01
- You are a member of the Owner group in the subscription or resource group, in order to perform required resource creation and role management steps.
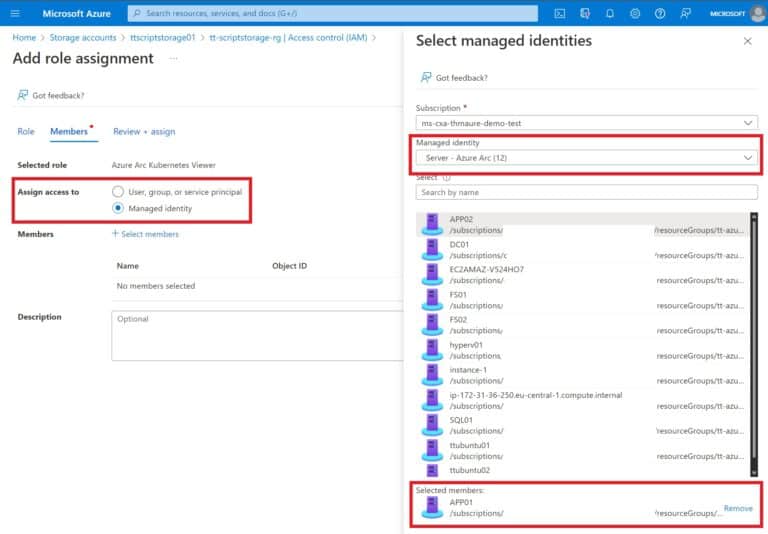
Add Role Assignment to resource or resource group for Azure Arc-enabled Server APP01
- Have Azure PowerShell installed, depending on what you are planning to use.
Get an access token using REST API
For an Azure Arc-enabled Windows server, using PowerShell, you invoke the web request to get the token from the local host in the specific port. Specify the request using the IP address or the environmental variable IDENTITY_ENDPOINT.
$apiVersion = "2020-06-01"
$resource = "https://management.azure.com/"
$endpoint = "{0}?resource={1}&api-version={2}" -f $env:IDENTITY_ENDPOINT,$resource,$apiVersion
$secretFile = ""
try
{
Invoke-WebRequest -Method GET -Uri $endpoint -Headers @{Metadata='True'} -UseBasicParsing
}
catch
{
$wwwAuthHeader = $_.Exception.Response.Headers["WWW-Authenticate"]
if ($wwwAuthHeader -match "Basic realm=.+")
{
$secretFile = ($wwwAuthHeader -split "Basic realm=")[1]
}
}
Write-Host "Secret file path: " $secretFile`n
$secret = cat -Raw $secretFile
$response = Invoke-WebRequest -Method GET -Uri $endpoint -Headers @{Metadata='True'; Authorization="Basic $secret"} -UseBasicParsing
if ($response)
{
$token = (ConvertFrom-Json -InputObject $response.Content).access_token
Write-Host "Access token: " $token
}For an Azure Arc-enabled Linux server, using Bash, you invoke the web request to get the token from the local host in the specific port. Specify the following request using the IP address or the environmental variable IDENTITY_ENDPOINT. To complete this step, you need an SSH client.
ChallengeTokenPath=$(curl -s -D - -H Metadata:true "http://127.0.0.1:40342/metadata/identity/oauth2/token?api-version=2019-11-01&resource=https%3A%2F%2Fmanagement.azure.com" | grep Www-Authenticate | cut -d "=" -f 2 | tr -d "[:cntrl:]")
ChallengeToken=$(cat $ChallengeTokenPath)
if [ $? -ne 0 ]; then
echo "Could not retrieve challenge token, double check that this command is run with root privileges."
else
curl -s -H Metadata:true -H "Authorization: Basic $ChallengeToken" "http://127.0.0.1:40342/metadata/identity/oauth2/token?api-version=2019-11-01&resource=https%3A%2F%2Fmanagement.azure.com"
fiYou can learn more about this on Microsoft Learn.
Login with Azure PowerShell on Azure Arc enabled server using Managed Identity
To login with your managed identity using Azure PowerShell, run the following command:
Connect-AzAccount -IdentityNow you have access to the resources your Azure AD managed identity (MSI) on your Azure Arc-enabled server has permissions to.
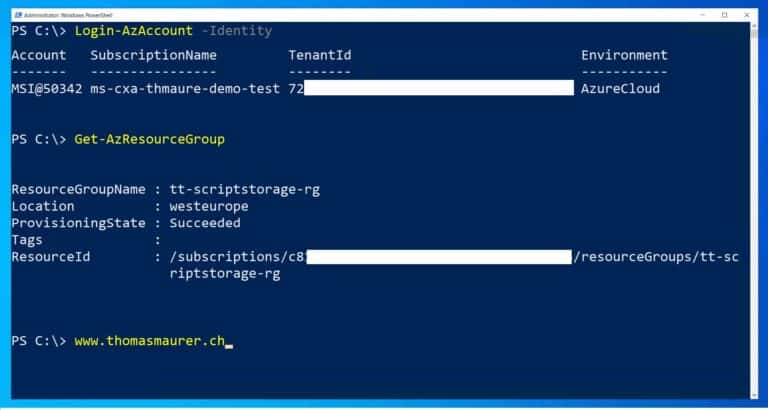
Azure PowerShell on Azure Arc enabled server using Managed Identity
Conclusion
I hope this post is helpful to build some automation with Azure PowerShell on your on-premises or multi-cloud servers with Azure Arc. Let me know if you have any questions in the comments below.
Email address:
Leave this field empty if you're human:
Tags: Azure, Azure AD, Cloud, Hybrid, Hybrid Cloud, Linux, Managed Identity, Microsoft, Microsoft Azure, PowerShell, Virtualization, Windows, Windows Server
Recommend
-
 15
15
Article Image Azure's Managed Identity in Test Kitchen Annie Hedgpeth on...
-
 11
11
Using Managed Identity With Azure KeyVault Leave a reply One of the things that’s always irked...
-
 5
5
【Azure 应用服务】Azure Function 启用 Managed Identity后, Powershell Funciton出现 ERROR: ManagedIdentityCredential authentication failed ...
-
 9
9
Ever since Managed Service Identity was introduced last year, we have been thrilled about it. No more credentials stored in config files. Since it received a bunch of updates now, we thought we'd summarize them a bit and offer our thou...
-
 7
7
Calling your APIs with Azure AD Managed Service Identity using application permissions Posted on: 24-04-2018
-
 10
10
Azure AD Managed Service Identity Posted on: 13-10-2017
-
 7
7
Azure AD Authentication with Azure Storage + Managed Service Identity Posted on: 24-05-2018
-
 12
12
Using Managed Identity and Bicep to pull images with Azure Container Apps 8 minute read | By Anthony Salemo ...
-
 4
4
Home B...
-
 5
5
Connect to Azure Cosmos DB using Managed Identity from Logic App Connect to Azure Cosmos DB using Managed Identity from Logic App ...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK