

Why Xen wasn't hit by RETBleed on Intel CPUs
source link: https://xcp-ng.org/blog/2022/08/26/why-xen-wasnt-hit-by-retbleed-on-intel-cpus/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Why Xen wasn't hit by RETBleed on Intel CPUs
You probably heard about RETBleed security issue. Almost all operating systems had to release patches regarding this new hardware vulnerability. See our previous blog post about it:
But why Xen did release a fix only for AMD CPUs while Intel seems to be also hit? The answer is very interesting and another proof that Xen Project is taking security VERY seriously.
Security is hard
For example, on Linux kernel, both Intel and AMD CPUs were impacted, as you can read here: CVE-2022-29900 (AMD) and CVE-2022-29901 (Intel).
In the Xen security bulletin, only CVE-2022-29900 was fixed. What about CVE-2022-29901 on Intel side?
RETBleed on Intel isn't in fact a new hardware issue. It's a consequence of choices made by some OSes 4 years ago (including Linux), when Spectre-like speculation issues started to be known. To understand a bit more about it, we need first to talk about the first mitigation to those speculation issues: reptolines. They were introduced in 2018, as one possible mitigation against Spectre v2 speculative execution attacks.

Retpoline concept
To mitigate speculation/side-channel issues, there's mainly 2 options:
- direct manipulation on the hardware level (requiring CPU microcode updates)
- rewriite software such that it doesn't use the problematic predictor.
So in the end, retpoline is primarily a software construct where specific knowledge on the hardware is needed to mitigate branch target injection.
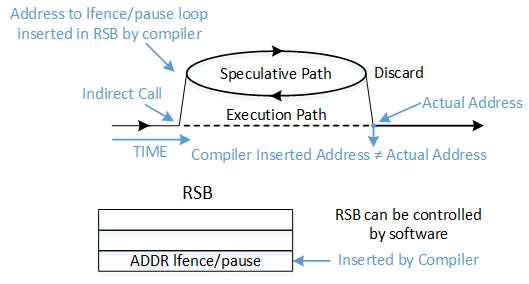
Are retpolines enough to stop speculative executions attack? Well, it's not, and RETBleed is the living proof of it. Despite some public warning inside the Linux project (4 years ago) about the insufficient capability of retpolines to protect against those attacks in some configurations, and even suggesting other solutions to fix it (see below), it was decided to left it "as is".
Mostly because people didn't believe that it was possible to exploit the retpoline limitations. As we seen, it was more a belief than a true statement.
So is there other solutions to protect against these attacks? Yes, using IBRS!
IBRS to the rescue
So when retpolines aren't safe, there is indeed another possibility to protect yourself from speculation attacks: using IBRS. Another acronym, yay! IBRS means "Indirect Branch Restricted Speculation". This is an Intel CPU specific feature, restricting speculation of indirect branches, and therefore protecting indirect branch predictions.
So why not using it for everything? Well, there's multiple reasons:
- it's a kind of "retrofit" added in the microcode, not originally a native/hardware mitigation (in Skylake CPUs): it is very SLOW compared to retpoline 🐌
- it's harder to implement than just doing retpolines from the hypervisor or operating system perspective 👷
That's likely why other projects/OSes decided to not use it… until RETBleed!
If you want to read more about IBRS and eIBRS, you can directly read the Intel official documentation.
Xen Project and security
However, security (and not leaking your data to anyone), is more important than those previous considerations. That's why Xen project didn't left the hypervisor with incomplete mitigations for 4 years, and decided to use IBRS when it was crucial, despite the performance hit when used by the virtual machine on top of it.
The approach in Xen was to virtualize and expose MSR_SPEC_CTRL to the guest operating system. This way, even Windows system could rely on their own code to call IBRS when needed (which is the case). That's why IBRS was exposed to guests back in 2018 (XSA 263).
All of this explains why the latest Xen Security Advisory (XSA) 407 was only about AMD:
On Intel CPUs, Retbleed is not a new vulnerability; it is only applicable to software which did not follow Intel's original Spectre-v2 guidance.
This is a great demonstration that Xen Project is taking security very seriously, as we also do here for XCP-ng. By the way, if you are still not convinced, you can have a read on https://xenproject.org/users/security.
Frankly, Xen is probably the best Open Source project I know in terms of taking security seriously. If you are interested to learn more about how Xen Project is working on deep security issues, let us know, we'll be happy to go deeper and even get some Xen core developers interviews!
Recommend
-
 12
12
Xen Modes: What Color Is Your Xen? 07 May 2014 What's faster: PV, HVM, HVM with PV drivers, PVHVM, or PVH? Cloud computing providers using...
-
 13
13
Getting started with Xen Virtualization On CentOS 7.xSearch ComputingForGeeksWelcome to Getting started with...
-
 42
42
Install Xen Orchestra on Ubuntu 20.04|Debian 10 to Manage Xen/XCP-ngXen Orchestra (XO) is a web interface tool for Xen and XCP-ng Administrators to visualize and administer the complete Virtualization stack. The Xen Orchestra doesn’t require...
-
 7
7
Virtualization Performance: Zones, KVM, Xen 11 Jan 2013 I originally posted this at http://dtrace.org/blogs/brendan/2013/01/11/virtualization-performance-zones-kvm-xen. Update 2017: Virtualization has s...
-
 4
4
No, Intel wasn't granted a patent for AMD Zen architecture More of a case of stealing AMD's homework By Adrian Potoroaca April 6, 2...
-
 3
3
Xen 学习笔记 2009-02-10 Wed, Feb 11, 2009 • Computer System x86_64上不支持...
-
 4
4
Xen DomainU 自动测试脚本 Tue, Apr 7, 2009 • Computer System 写完代码测试时重复的...
-
 14
14
The "Retbleed" speculative execution vulnerabilities [Posted July 12, 2022 by corbet] Some researchers at ETH Zurich have
-
 4
4
New ‘Retbleed’ Attack Can Swipe Key Data From Intel and AMD CPUsThe exploit can leak password information and other sensitive material, but the chipmakers are rolling out mitigations.
-
 4
4
Testing shows AMD Zen 4 handling Spectre, Retbleed mitigations like a real champ...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK
 XCP-ng newsOlivier Lambert
XCP-ng newsOlivier Lambert