Phishers who breached Twilio and fooled Cloudflare could easily get you, too
source link: https://arstechnica.com/information-technology/2022/08/phishers-breach-twilio-and-target-cloudflare-using-workers-home-numbers/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

PHISHERS OF MEN —
Phishers who breached Twilio and fooled Cloudflare could easily get you, too
Unusually resourced threat actor has targeted multiple companies in recent days.
Dan Goodin - 8/9/2022, 11:33 PM

At least two security-sensitive companies—Twilio and Cloudflare—were targeted in a phishing attack by an advanced threat actor who had possession of home phone numbers of not just employees but employees' family members as well.
In the case of Twilio, a San Francisco-based provider of two-factor authentication and communication services, the unknown hackers succeeded in phishing the credentials of an undisclosed number of employees and, from there, gained unauthorized access to the company's internal systems, the company said. The threat actor then used that access to data in an undisclosed number of customer accounts.
Two days after Twilio's disclosure, content delivery network Cloudflare, also headquartered in San Francisco, revealed it had also been targeted in a similar manner. Cloudflare said that three of its employees fell for the phishing scam, but that the company's use of hardware-based MFA keys prevented the would-be intruders from accessing its internal network.
Well-organized, sophisticated, methodical
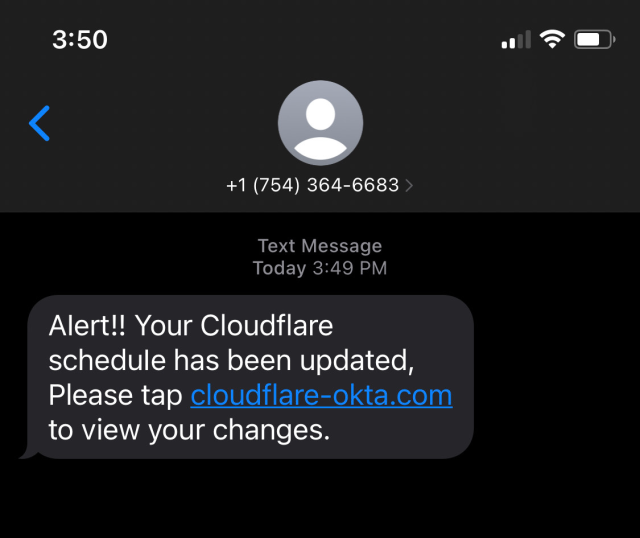
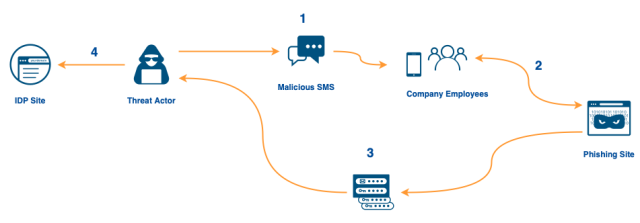
In both cases, the attackers somehow obtained the home and work phone numbers of both employees and, in some cases, their family members. The attackers then sent text messages that were disguised to appear as official company communications. The messages made false claims such as a change in an employee's schedule, or the password they used to log in to their work account had changed. Once an employee entered credentials into the fake site, it initiated the download of a phishing payload that, when clicked, installed remote desktop software from AnyDesk.
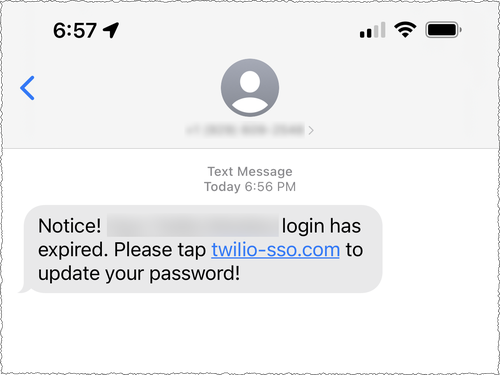
The threat actor carried out its attack with almost surgical precision. When the attacks on Cloudflare, at least 76 employees received a message in the first minute. The messages came from a variety of phone numbers belonging to T-Mobile. The domain used in the attack had been registered only 40 minutes prior, thwarting the domain protection Cloudflare uses to ferret out impostor sites.
Advertisement"Based on these factors, we have reason to believe the threat actors are well-organized, sophisticated, and methodical in their actions," Twilio wrote. "We have not yet identified the specific threat actors at work here, but have liaised with law enforcement in our efforts. Socially engineered attacks are—by their very nature—complex, advanced, and built to challenge even the most advanced defenses."
Matthew Prince, Daniel Stinson-Diess, Sourov Zaman—Cloudflare's CEO, senior security engineer and incident response leader respectively—had a similar take.
"This was a sophisticated attack targeting employees and systems in such a way that we believe most organizations would be likely to be breached," they wrote. "Given that the attacker is targeting multiple organizations, we wanted to share here a rundown of exactly what we saw in order to help other companies recognize and mitigate this attack."
Twilio and Cloudflare said they don't know how the phishers obtained employee numbers.
It's impressive that despite three of its employees falling for the scam, Cloudflare kept its systems from being breached. The company's use of hardware-based security keys that comply with the FIDO2 standard for MFA was a critical reason. Had the company relied on one-time passwords from sent text messages or even generated by an authentication app, it likely would have been a different story.
The Cloudflare officials explained:
When the phishing page was completed by a victim, the credentials were immediately relayed to the attacker via the messaging service Telegram. This real-time relay was important because the phishing page would also prompt for a Time-based One Time Password (TOTP) code.
Presumably, the attacker would receive the credentials in real-time, enter them in a victim company’s actual login page, and, for many organizations that would generate a code sent to the employee via SMS or displayed on a password generator. The employee would then enter the TOTP code on the phishing site, and it too would be relayed to the attacker. The attacker could then, before the TOTP code expired, use it to access the company’s actual login page — defeating most two-factor authentication implementations.
CloudflareWe confirmed that three Cloudflare employees fell for the phishing message and entered their credentials. However, Cloudflare does not use TOTP codes. Instead, every employee at the company is issued a FIDO2-compliant security key from a vendor like YubiKey. Since the hard keys are tied to users and implement origin binding, even a sophisticated, real-time phishing operation like this cannot gather the information necessary to log in to any of our systems. While the attacker attempted to log in to our systems with the compromised username and password credentials, they could not get past the hard key requirement.
Cloudflare went on to say it wasn't disciplining the employees who fell for the scam and explained why.
Advertisement"Having a paranoid but blame-free culture is critical for security," the officials wrote. "The three employees who fell for the phishing scam were not reprimanded. We're all human and we make mistakes. It's critically important that when we do, we report them and don't cover them up."
Promoted Comments
-
Ragashingo wrote:If I was to get a hardware key... is there anywhere that really uses it? Twitter? Discord? Telegram? That kind of thing? Or are they mostly for large corporations?All kinds of public facing services let you provision your account to require these keys. Github. Amazon. GMail or whatever it's called this week, not many banks, but some. Everybody EXCEPT AMAZON / AWS lets you set up multiple keys so you have a backup. NO BACKUP KEY FOR AMAZON. Ask me how I know this sometime.
It's a reliable and workable tech. My yubi key has been riding around in my pocket with my house key etc since 2016 and still works perfectly. Dropped in winter slush, still good. Haven't tried baking it in a heat wave though.
My Ars key is my backup.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK