

Hackers target unsecured Amex and SnapChat sites to steal user data | TechSpot
source link: https://www.techspot.com/news/95546-hackers-target-unsecured-amex-snapchat-sites-steal-user.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Hackers target unsecured Amex and SnapChat sites to steal user data
The new attack uses a not-so-new vulnerability that redirects users to fraudulent sites
By Jimmy Pezzone Today 12:37 PM
Why it matters: An email-focused security firm released a blog post detailing a phishing attack targeting unsecured American Express and Snapchat sites. The identified exploit uses a known open redirect vulnerability that allows threat actors to specify a redirect URL, driving traffic to fraudulent sites designed to steal user information.
Maryland-based security firm INKY Security tracked attack activity related to the vulnerability from mid-May through mid-July. The phishing attack relies on a known open redirect vulnerability (CWE-601) and popular brand recognition to deceive and harvest credentials from unsuspecting Google Workspace and Microsoft 365 users.
The attacks targeted unsecured sites from Snapchat and American Express. Snapchat-based attacks resulted in more than 6,800 attacks over a two-and-a-half-month period. The American Express-based attacks were much more effective, affecting over 2,000 users in just two days.
Malicious actors have taken advantage of open-redirect vulnerabilities affecting AMEX & Snapchat domains to send #phishing emails targeting Google Workspace and Microsoft 365 users." https://t.co/bTG2b7dLWY
— INKY (@InkyPhishFence) August 4, 2022
The Snapchat-based emails drove users to fraudulent DocuSign, FedEx, and Microsoft sites to harvest user credentials. Snapchat's open redirect vulnerability was initially identified by openbugbounty more than a year ago. Unfortunately, the exploit still appears to be unaddressed.
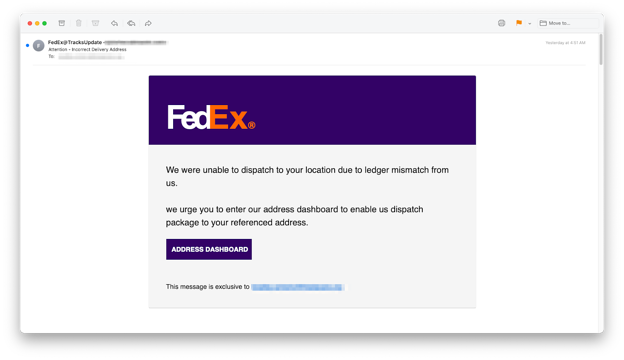
American Express appears to have remediated the vulnerability, which redirected users to an O365 login page similar to the one that the Snapchat-based attacks used.
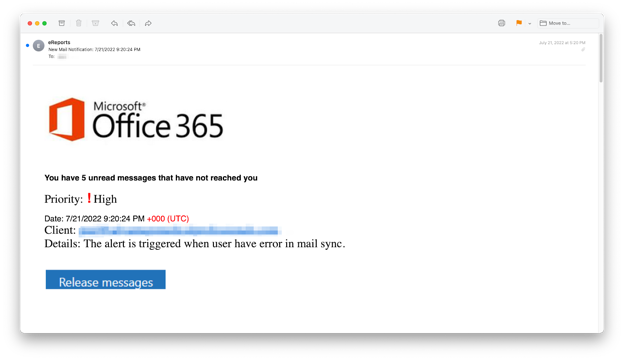
This specific phishing attack uses three primary techniques: brand impersonation, credential harvesting, and hijacked accounts. Brand recognition relies on recognizable logos and trademarks to create a sense of trust with the potential victim leading to the user's credentials being entered into and harvested from the fraudulent site. Once harvested, hackers can sell the stolen information to other criminals for profit or use the information to access and obtain the victim's personal and financial information.
Open redirect vulnerabilities don't tend to get the same level of care and attention as other identified exploits. Additionally, most risk exposure is on the user rather than the site owner. The blog post provides additional background and guidance to help users stay safe and keep their data out of the wrong hands. These tips help users identify key terms and characters that may indicate if a redirect is occurring from a trusted domain.
Image credit: INKY Security
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK