

Using Azure AD Device Extension Attributes in Microsoft Endpoint Manager
source link: https://medium.com/learning-mem/using-azure-ad-device-extension-attributes-in-microsoft-endpoint-manager-19a3b4c30172
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Using Azure AD Device Extension Attributes in Microsoft Endpoint Manager
In case you missed it, Azure AD recently released 15 new attributes on Azure AD devices for you to populate and use as you please.
The two main reasons you’ll want to consider using them are:
- Using as a device filter on Conditional Access Policy. For example, you could add an attribute for “Super secure developer devices” and then make sure developers can only use those devices to access some cloud app, for example Azure DevOps.
- Using in Dynamic Device groups. You could bundle up all of those “Super secure developer devices” into an Azure AD group. Once they’re in the group you can use that group for delegating administration and/or policy targeting in Microsoft Endpoint Manager (Intune).
Which devices in AAD can have Extension Attributes?
All Azure AD device objects have extension Attributes. This includes all platforms (Windows, iOS, Android) and Join Types (Registered, AAD Joined and Hybrid AAD Joined). You can apply extension attributes to both Intune managed and unmanaged devices.
You might also find it useful to add extension attributes to pre-registered Autopilot device objects, so that they can be placed into a group and be targeted with Policies and Applications before they enroll in Intune.
How do you populate AAD device extension attributes?
Right now, there is a read-only UI experience in the portal for extension attributes. Similarly, the Azure AD Powershell module does not yet have this capability.
If you want to edit them, you will need to do it manually using Graph API. Here I’ll show you how to use using Microsoft Graph Explorer:
- Go to Graph Explorer
- Sign in with AAD credentials
- View all 15 Extension Attribute values for one of your devices by performing a GET on the AAD device ObjectID.
https://graph.microsoft.com/v1.0/devices/{ObjectID}/extensionAttributes
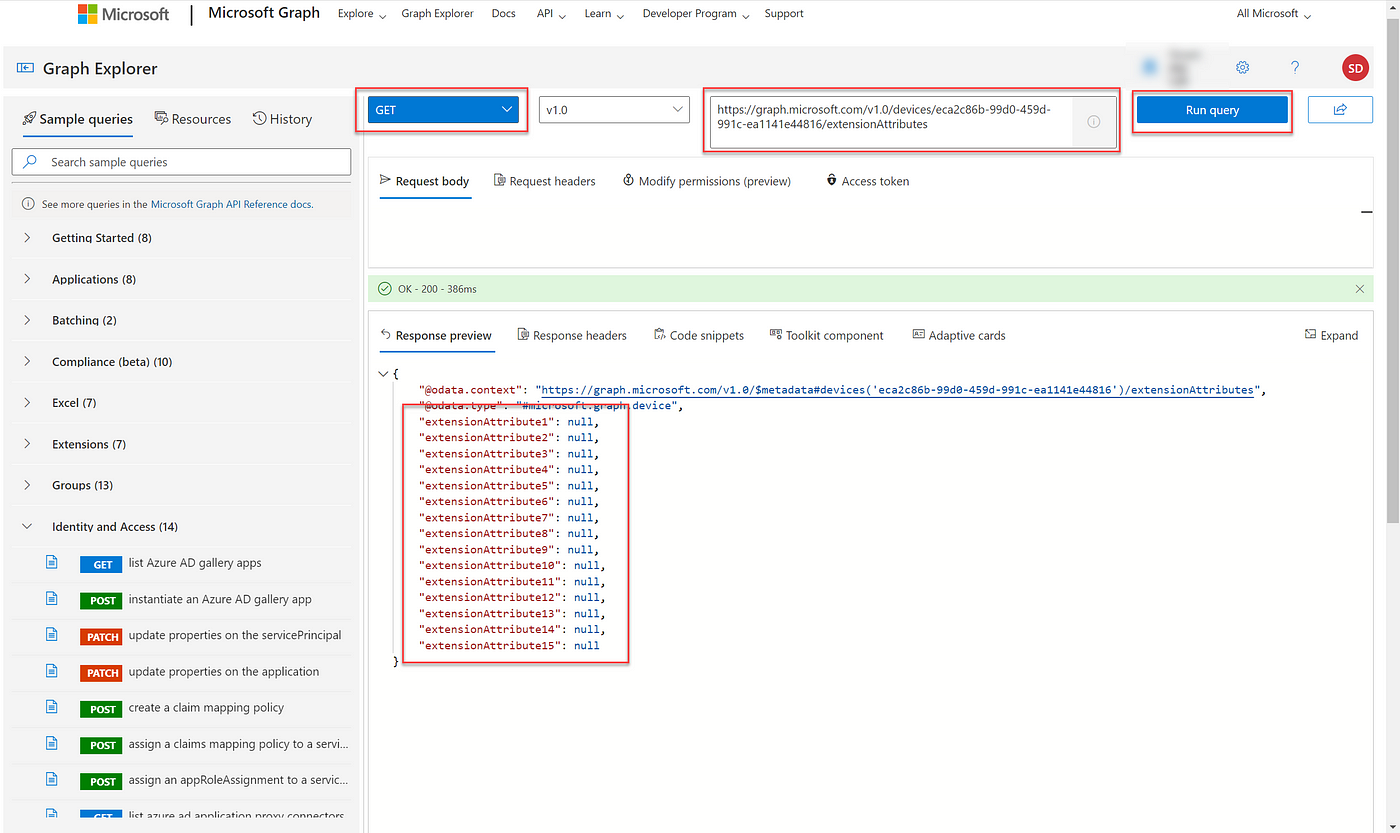
Use Graph Explorer to view extension attributes on AAD registered devices
Tip: You‘ll find the ObjectID in the AAD Portal. Devices > All Devices > {Device} > ObjectID
4. Now Patch the desired values. In this example I’m going to use Extension Attribute 15 to stamp my “Super secure developer devices” tag.
The request body will look something like this:
{“extensionAttribute15”: “Super secure developer devices”}
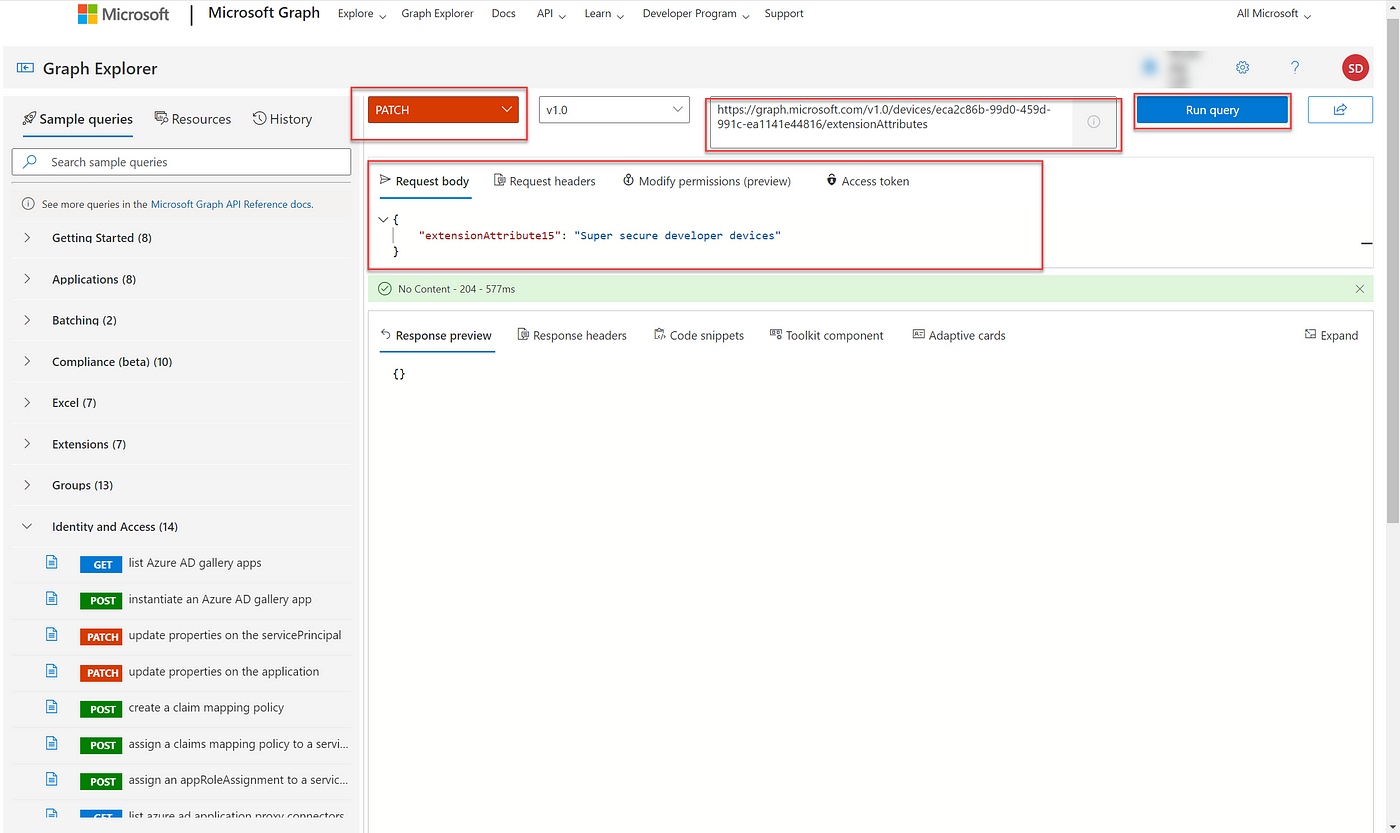
Use graph explorer to update extension attributes on AAD registered devices
5. Verify that the value was written by performing another GET.
https://graph.microsoft.com/v1.0/devices/{ObjectID}/extensionAttributes
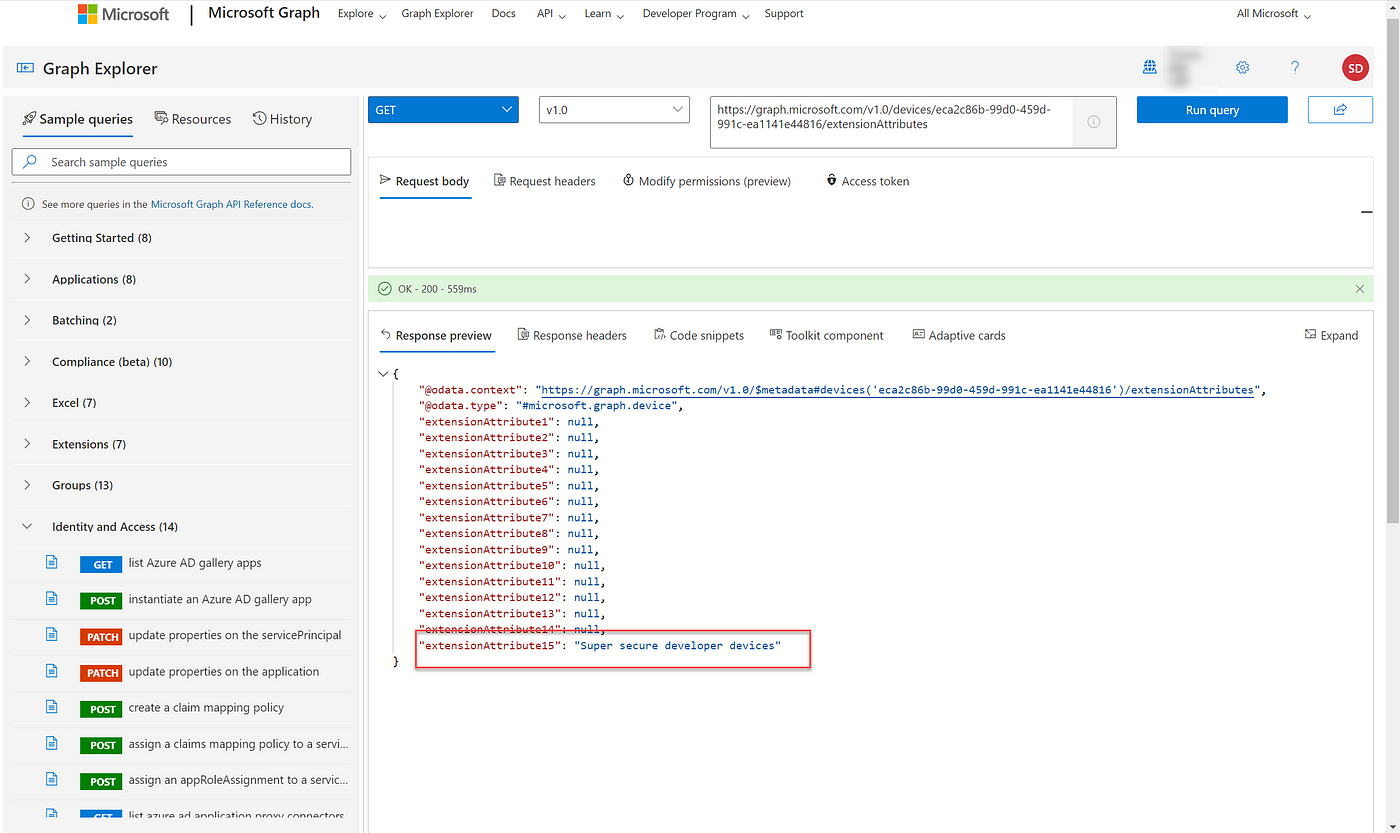
Use graph explorer to view the new extension attribute value
How do you create a dynamic device group using Extension Attributes?
Go to Microsoft Endpoint Manager > Groups > New group and create a new dynamic device group. Use the extension attributes as the basis for group membership.
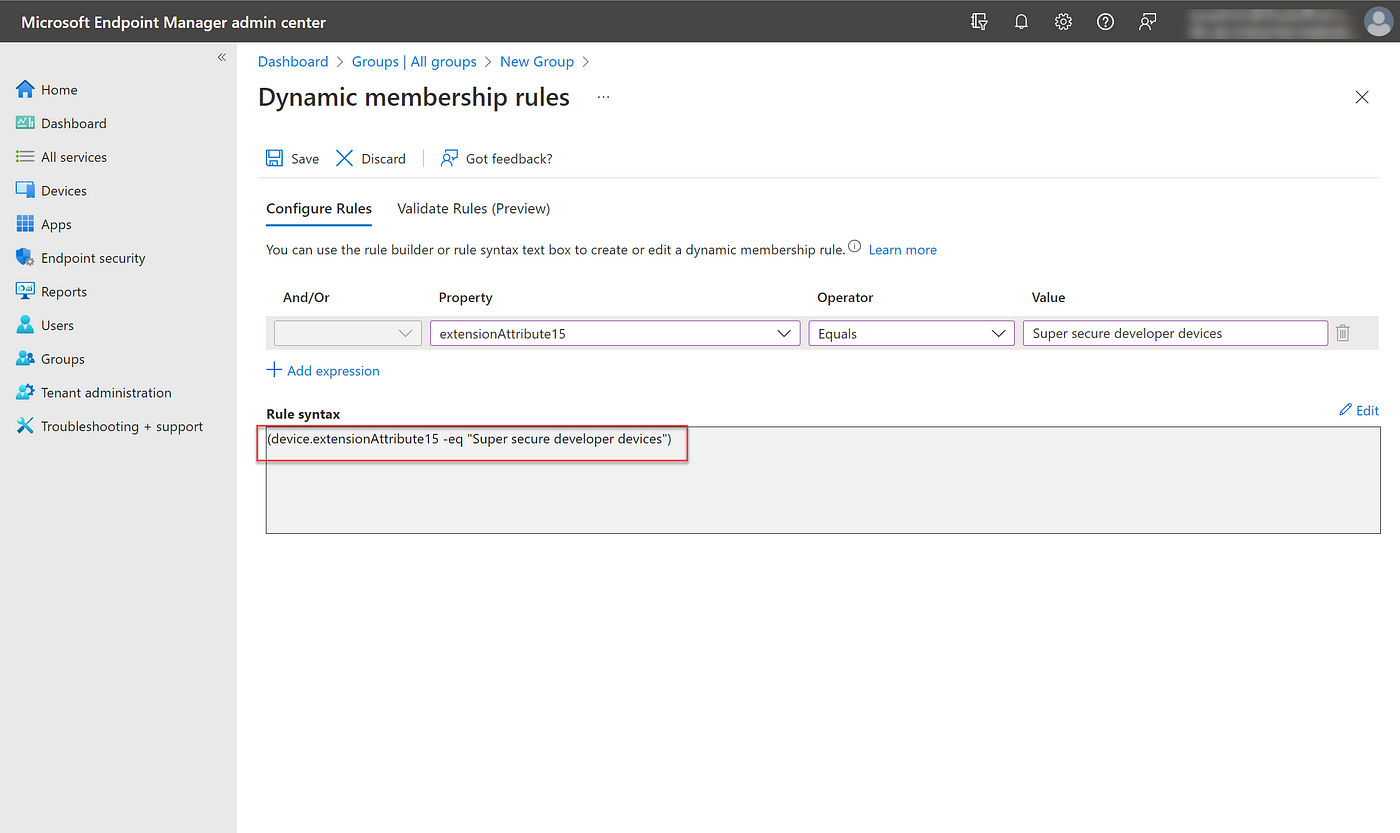
Create a dynamic device group based on Extension Attributes
How do you create a conditional access policy using Extension Attributes?
Go to Microsoft Endpoint Manager > Endpoint Security > Conditional Access and create a new Conditional Access policy. Under Conditions, Filters for Devices you can select the extension attributes as the basis for including or excluding specific devices.

Create an Azure AD Conditional Access policy with a filter for devices
How do you view Device Extension Attributes in the console?
You can see an AAD registered device’s extension attributes in the Azure AD Portal or the new Microsoft Entra portal. These attributes are not currently exposed in the Microsoft Endpoint Manager portal.
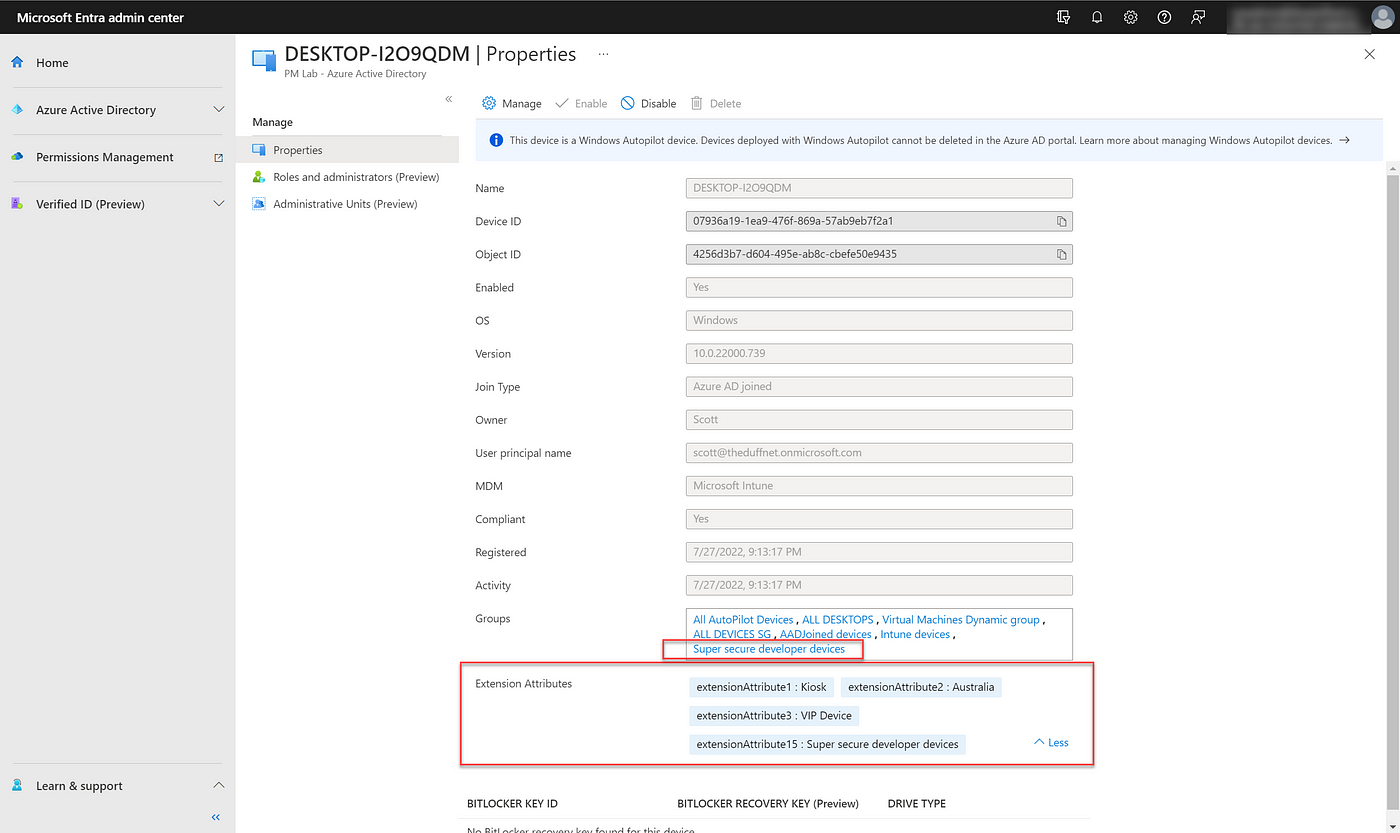
View Extension Attributes in Microsoft Entra admin center
Where can you learn more?
Check out the official Microsoft documentation to learn more about Extension Attributes:
Extension Attributes:
Azure AD cmdlets to work with extension attributes
Extension attributes offer a convenient way to extend your Azure AD directory with new attributes that you can use to…
Dynamic Device Groups:
Rules for dynamically populated groups membership - Azure AD - Microsoft Entra
You can create attribute-based rules to enable dynamic membership for a group in Azure Active Directory (Azure AD)…
Conditional Access Filter for Devices
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK