

TPM Module Too Expensive? DIY Your Own Easily!
source link: https://hackaday.com/2022/05/04/tpm-module-too-expensive-diy-your-own-easily/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
TPM Module Too Expensive? DIY Your Own Easily!
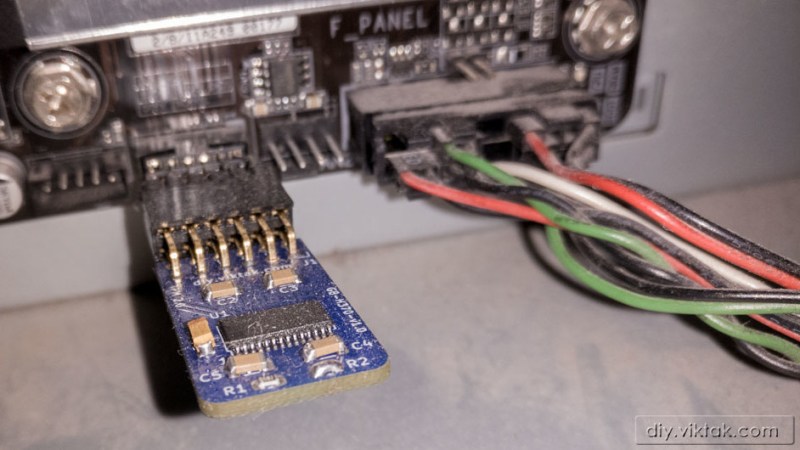
Since Windows 11 has announced its TPM module requirement, the prices for previously abundant and underappreciated TPM add-on boards for PC motherboards have skyrocketed. We’ve been getting chips and soldering them onto boards of our own design, instead – and [viktor]’s project is one more example of that. [Viktor] has checked online marketplace listings for a TPM module for his Gigabyte AORUS GAMING 3 motherboard, and found out they started at around 150EUR – which is almost as much as the motherboard itself costs. So, as any self-respecting hacker, he went the DIY way, and it went with hardly a hitch.
Following the schematic from the datasheet, he quickly made a simple KiCad layout, matching it to the pinout from his motherboard’s user manual, then ordered the boards from PCBWay and SLB9665 chips from eBay. After both arrived, [viktor] assembled the boards, and found one small mistake – he designed a module for 2.54mm pin headers, but his motherboard had 2.0mm headers. He wired up a small adapter to make his assembled V1.0 boards work, and Windows 11 installed without any TPM complaints. He shows that he’s designed a new, V1.1 version with an updated connector, too, and published its (untested but should work) design files for us on GitHub. These modules can vary, by manufacturer and motherboard series, but with each module published, a bunch of hackers can save money – and get a weekend project virtually guaranteed to work out.
Regardless of whether the goal of running Windows 11 is ultimately worthwhile, it has been achieved. With scalpers preying on people who just want to use their hardware with a new OS, rolling your own TPM PCB is a very attractive solution! Last time we covered a DIY TPM module for ASrock server motherboards, we had a vivid discussion in the comments, and if you’re looking to create your own TPM board, you could do worse than checking them out for advice and insights!
Posted in computer hacks, Security HacksTagged Gigabyte, SLB9665, TPM, Trusted Platform Module
Post navigation
68 thoughts on “TPM Module Too Expensive? DIY Your Own Easily!”
-
Mojoe says:
Since the article doesn’t mention it… TPM stands for Trusted Platform Module and according to wikipedia: “Trusted Platform Module (TPM, also known as ISO/IEC 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. The term can also refer to a chip conforming to the standard.
TPM is used for digital rights management (DRM), Windows Defender, Windows Domain logon, protection and enforcement of software licenses, and prevention of cheating in online games.
One of Windows 11’s system requirements is TPM 2.0. Microsoft has stated that this is to help increase security against firmware and ransomware attacks.”
-
RW ver 0.0.1 says:
Yay, clipper chip 2.0.
Really it’s so considerate to concentrate all the security tech into a single point of failure high value target, saves wasted resources.
-
jarfil says:
Secure hardware, as in protected against physical attacks, is much harder and expensive to design and produce. That’s why most hardware is not even remotely secured against physical attacks, and why it makes sense to have a specific chip dedicated to the task.
The actual problem is, the final user should be the owner of the keys… but since most average users are incredibly inept at safekeeping their keys, that would lead to a ton of bricked systems, so someone decided that it’s better if some external centralized organization kept the keys… which undermines the whole security concept.
-
Mike says:
Defence against physically present attackers is always futile. In any scenario with a physically present attacker they could plant a spycam in the room to see your password or threaten it out of you. By not having something like a TPM though atleast one reduces the risk of remote attacks and backdoors. One suspects this TPM requirement in Win 11 might be about making motherboard manufacturers all start putting them in, so in a few years time M$ can then insist they are used to block the booting of linux or other better competitors to windows.
-
-
-
Ostracus says:
Something to read.
https://trustedcomputinggroup.org/resource/a-practical-guide-to-tpm-2-0/
-
Ostracus says:
“TPM based attestation – how can we use it for good?” – Matthew Garrett (LCA 2020)
-
-
1235Testing says:
Note to article author: Please spell out full acronym when first using it: Trusted Platform Module [TMP]. There is of course some acronyms like USB that are ingrained by now. But on a tech site like Hackaday there will be hundreds of acronyms and nobody know all of them
-
Winston says:
“Since the article doesn’t mention it…”
Thank you! First rule of technical writing, spell out an acronym upon first use.
-
John says:
I see that rule broken regularly in white papers. Very annoying when trying to understand something new.
-
-
Steven Clark says:
I’m not really sure about it adding any practical protections to DRM (other than just generally making an uncopyable key ). PCRs for policy get pretty useless pretty fast once you’re past the nice predicatble land of bootloaders.
-
George says:
Thanks, I was wondering why I needed a Tire Pressure Monitor on my motherboard….
-
-
scott.tx says:
before you buy/build one check your bios settings to see if you already have one that just needs enabled.
-
Miles says:
Exactly, IIRC firmware TPM from 7th gen Intel, or if you are running corporate grade equipment (like Dell or Lenovo mobile workstations) you may have a hardware TPM chip that can be upgraded from 1.2 to version 2.0.
I’m sticking with 10 until there is a reason. I did a test install of 11, just shift f10 and killed the TPM requirement and made a local account, then ran ThisIsWin11 (sp?), Fixed the taskbar and a lot of stuff.
-
-
Paul says:
I hear the argument to have such a thing, but I have visceral reservations about having one in my computer. Basically, the TPM is the literal keys to my hardware, but the OS vendor essentially has those keys: Somebody far away can change the operation of my hardware at will, lock out anybody else, and can deny me access to my own hardware any time they want.
Heck, with Windows 11 I can’t even log into my own computer without asking Microsoft permission to let me log in. It’s humiliating. For that reason I don’t have a Microsoft ID. Never have. And so, until the place freezes over, I won’t be running Windows 11 on any machines I control.
-
justsayin says:
Well put. Essentially, sticking a ‘TPM’ in your machine is abdication of ownership. There’s nothing I need *that* badly.
-
Truth says:
Preaching to the choir. TPM modules come with factory hardcoded “EPS” (Endorsement Primary Seed) which typically can never be changed. The reason it is to be cheaper to manufacture, avoids corruption as a point of failure, and it help you fully outsource all your TRUST to the factory where they were created – They would never keep a backup copy of the EPS (unless they were given a FISA court order with gagging).
TPM is a fully open standard which was created by the Trusted Computing Group (Very strange bedfellows, for non-native English speakers the idiom means “Unlikely allies”, – Intel, AMD, IBM, Microsoft, and Cisco), and before they were known as the TCG they were, prior to 2003, the Trusted Computing Platform Alliance which was formed in 1999 (Compaq, Hewlett-Packard, IBM, Intel, and Microsoft). You should always TRUST any organisation that keeps “trust” in their name, “trust” is is exactly like “confidence”, “belief”, “faith” or possibly “conviction”. I tip my hat to them, brilliant marketing picking “Trust” as part of their name, it is absolutely perfect social engineering.
-
Dave says:
I have to answer this misinformation. There are 3 hierarchies in the TPM. Each has a primary seed. The Endorsement hierarchy, which is used to create the endorsement key (EK) is seldom used, even for that. if you use the EPS to recreate the EK, then you get a special key which has a certificate created by the mfger. This key can be used by the OWNER OF THE TPM (NOT the mfger) together with a trusted third party, to create a certificate for a user generated key stating that the key was created by some TPM (and is in some sense more secure). Keys that a user makes on the TPM are created under the storage hierarchy. THe Storage primary seed is created using a random number generator. So basically the EPS has no security relevance for anything you would care about. So just stop.
-
lmnhgtrbhbyhf says:
“trusted” organisations, just the way a “people’s republic” is always run according to the welfare of the population.
-
-
Miles says:
I made a local account on my Win11 test system
Also turn off the TPM. Already ran into a situation where bitlocker encryption is holding hostage a hard drive and never backed up the keys. If I don’t log in and don’t TPM then it can’t encrypt my data.
Just stick with 10 til support is dropped and then either 11 will be declawed by the community or Linux here I come. Ubuntu LTS pls.
Win 10 LTSC is amazing BTW, sadly I have 1 Metro app I want to run.
ChromeOS has android apps, Linux subsystem, and soon . . . Steam. Maybe I’ll make a ‘Brunch’-book out of a Thinkpad for my main system at that point. If they get support for my nVidia card.
-
RÖB says:
This is why I removed the TPM module from my motherboard. Now it wont upgrade to 11.
TPM is a resource available anything running on the system including browser pages and it is open to abuse.
Physical possession will alway be better than this.
-
-
Paul says:
Had to chuckle at the number they picked for the standard: 11889. My apologies to native Chinese speakers, but it loosely can be interpreted to mean “me me rich rich emperor”.
-
lol says:
Use Rufus to burn installation media and there is no TPM requirement.
-
Gareth says:
Can you elaborate?
-
lol says:
There’s an option in Rufus to eliminate the hardware checks:
https://www.thewindowsclub.com/bypass-tpm-and-secure-boot-indows-11-rufus -
Topgeard says:
Rufus is a bootable drive maker that have an easy option to create a win11 install without any requirement I certify I have used it on 7 very old computers like a quad core, a dual core, a 3770 I7 and 4 other including laptops and have no trouble till this day.
-
-
-
UT says:
TPM = Treacherous Platform Module. It’s DRM in its most cynical form, and lets media corporations control and own your computer instead of you.
-
Loxmyth says:
Remember that TPM isn’t the only Win11 stumbling block. You also need a relatively recent CPU. I could upgrade my TPM to Microsquish’s requirements, but my mackine is just one generation too old to have some of the security features they insist on.
At one level, I approve of someone pushing people to be more aware of hardware security. But sprining it on us without a deprecation cycle was somewhat rude. Oh well, for my purposes Win10 is adequate and I’m still looking at whether I can migrate to Linux cometely without losing too much of my DAW investment
-
Shannon says:
How is this not a ‘deprecation cycle’? You don’t have to upgrade to Win11, you have advance notice that your older hardware won’t be supported.
-
-
Mhajicek says:
What happens if you swap or remove the TPM after installing Windows 11?
-
RÖB says:
Or if the TPM fails – well I guess you end up with the totally encrypted system that they’re trying to prevent with TPM – encryption ransom-ware – except there’s no amount of money you can pay to anyone to get your data back.
-
Slartibartfast says:
You can add recovery keys which you can save to a USB key or file. Either can then be used to unlock your system even if the TPM modules is removed or fails. The problem is that Microsoft doesn’t care to make users aware of the need to do this. Add to that the recent changes to Windows which automatically BitLock your system drive using only the TPM key if your system supports Modern Sleep and you use a Microsoft account to log in and you have a recipe for bad outcomes if your mainboard or TPM module fails.
-
-
AKA the A says:
if you did what you were told and backed up the recovery key – you just type it in
If you did not, then you deserve the data loss.
-
-
CREEA says:
Déjà vu. I could swear this article was posted not that long ago.
-
Alexander says:
Me too, along with a discussion about the bad grounding scheme around the IC (which unfortunately seem to remain in the new PCB revision).
-
Arsenijs Picugins says:
That article was about a different module! It is even linked in the last paragraph.
https://hackaday.com/2022/04/06/build-a-tpm-module-for-your-server/
And this picture, showing the first revision PCBs, does seem to have a bottom layer groundplane with plenty of vias, at the very least:
https://i0.wp.com/diy.viktak.com/wp-content/uploads/2021/12/tpm-pcb.jpg
-
-
-
CRJEEA says:
-
Darry says:
I am a bit confused. I thought H370 based platform had integrated TPM 2.0 functionality via PTT. Why is all this necessary ? Am I missing something here ?
-
Joshua says:
Cool! I love hacks like this. Kudos.
Personally, though, I think I would just have had used a vero board and some fine copper wire.
I mean, there are merely 12pins on the header, so that seems feasible.
With a bit of patience, the result would have had been the same. Just more hacky, perhaps. -
ian 42 says:
I got bought a few motherboards recently and high on the list was no tpm so it wouldn’t auto upgrade to win11.. I think win 10 is the end of the the road for windows for a lot of users…
-
LordNothing says:
on my new mobo it was off by default, and its going to stay that way. as far as i know the os still is not able to change bios settings.
-
-
LordNothing says:
ive spent a few weeks evaluating windows 11 and so far i am not impressed with any of it. the number of registry hacks ive needed to use in the first few days is absurd. i did notice that it did not immediately encrypt my drives or break any of my stuff. but the os is barely usable and it throws a lot of extra clicks into my workflow. if it commits any deadly sins against my data (which is actually an old copy so i wont lose anything if it did) or forces me to have a microsoft account (it hasnt, yet), its gone.
i still have to run a lot of stuff in virtual machines, so i might mosey on over to the linux side to see if theirs are better. gpu passthrough is something that doesnt seem to work as good as vm developers claim. i recently did an xp32 install on a vm and noticed how lean the os is. it has barely any clutter, but not like 11 does. even 7 has a lot of clutter and people seem to love that one for some reason. but im not liking eleven, its too phone.
tpm might have some useful abilities, but i dont trust any os that forces you to use it.
-
JvandeWerken says:
The XP-sp3 image i use on qemu (ls -l shows: -rw-r–r– 1 jan users 252575744 Apr 25 2008 VirtualXP3.iso).
I did run that in ReadOnly mode on the company network “without” any anti-virus software and is “allowed” by top managment. When something happens you just kill that vm, start new vm in just a few seconds. Works great.
-
-
Sjaak says:
How hard would it be to write a firmware for an STM32 or Pico to ’emulate’ a TPM?
-
Dodo says:
The standard is open. A compliant but not very secure implemenntation would not be difficult but a lot of work to make. Note your TPM will need to provide an attestation certificate, I don’t know if win 11 checks if you are a trusted TPM manufacturer or just accept any.
-
anszom says:
That was my thought as well. Make a TPM that you really can trust.
-
Joshua says:
Wouldn’t an PIC16C84 from ca. 1993 do just as well ? ;)
-
LordNothing says:
i would certainly want an easy way to back up my keys. like put them on an sd card or something.
-
-
greenbit says:
You know what hardware protection module I trusted? Still do, when I encounter it? The lowly write-protect jumper.
Maybe there’s a bug in my firmware and it needs an update. Fine, I can manage that. That jumper comes off when I decide it’s time, and goes back on when it’s done. “But how do you know what you flashed is what you think it is” someone says. I trust myself to research what it is and verify the source and the image.
Or, you know, you can put your trust in a chunk of crypto hardware that supposedly only lets the “right” mysterious entities decide what to do to your computer and when to do so. Because the Baddies would never ever figure it out would they. And the people you trust, errr, the people that little module trusts, whoever they are, would never ever use their power unwisely, would they.
-
rick says:
Please, please, make this a thing again. Write protection jumpers are the way to go, utterly unhackable remotely, utterly under the control of any skilled user locally, just the way it ought to be.
-
-
RÖB says:
I guess building your own TPM might be a bonus.
I remember when I was younger and kept loosing my house keys. I would buy blanks and cut spares but eventually I would run out of spares and be locked out again.
I re-cut the the lock tumblers so that only an uncut blank key would unlock the door. No-one was any the wiser and I could just buy a new key without having access to an older one at any time.
-
borgy says:
security through absurdity!
-
RW ver 0.0.3 says:
Ah yes, the level of security provided by setting your password to “password” because nobody would think anyone would use something so simple.
Or are you really serious when you think “only” a blank key could open that lock? … and not say, any random piece of metal you could get into the hole?
-
denis says:
I’ve done this on fords ( old bangers that were worth nothing) remove the bar from the wafer lock and any ford key works.. classic security by obscurity.
-
The Commenter Formerly Known As Ren says:
Until the absent minded person in the parking lot sticks their key into your cars door….
Sometimes, I’ve deliberately parked the vehicle I was driving, next to an identical one,
(same year, model, color) just wondering if the other car’s owner will get confused.
B^)-
RW ver 0.0.3 says:
Really? Oh I thought one felt the urge to do that because it let it catch up with it’s factory sibling.
-
Elliot Williams says:
I opened up someone else’s Toyota Camry once. It was parked near mine, and I was lost in thought.
What are the chances that the key codes are close enough, the car parked next to me, and that one day I was randomly distracted enough to get in someone else’s car?
I still wonder if maybe it was unlocked at the time, but I _do_ remember the lock actually turning.
Probably should have bought a lottery ticket or taken up a life of crime. Oh well.
-
-
-
-
Justin A says:
“Regardless of whether the goal of running Windows 11 is ultimately worthwhile”…LOL!
-
some guy says:
Building a “trusted” something with IC from a random ebay seller… Yeah…
Anyway, i don’t need neither want this.
-
paulvdh says:
I think what we need is an Open Source implementation of TPM firmware for a generic microcontroller.
-
AKA the A says:
the whole point of a TPM is that it’s hard to get the keys out of it without authorization, you need hardware specifically designed for that…a generic MCU is not resistant to extracting data from it, so that would be kinda pointless…
-
paulvdh says:
The whole point of a TPM module for the vast majority of people is to get their damn computer to boot.
They really don’t give a hoot about the rest.
And with the chip scarcity and the ridiculous prices of these things at the moment this seems a quite useful project.I bought a new Mobo / Processor / Memory / SSD in December 2021, and checking whether the thing had a TPM module or even a connector for it was not on my list. I switched to Linux quite some years ago and have no intention to run another os. I did put it in a box that has a shiny “Designed for Windows XP” sticker but that is about as far as I will go regarding that brand.
-
paulvdh says:
For the vast majority of people the only purpose of the TPM module is to get their PC to boot and they do not care about the rest.
(Hackaday ate my previous post)
-
-
-
abe says:
or just use the registry hack, during start of install to disable the requirements. I was able to get win11 to run on a 3rd gen i5. mobo has no tpm and cpu is not supposed to be compatible, but win11 runs just fine and is actually faster than win7 it was running before.
Leave a Reply Cancel reply
Please be kind and respectful to help make the comments section excellent. (Comment Policy)
This site uses Akismet to reduce spam. Learn how your comment data is processed.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK


