

Lo, Rowhammer!
source link: https://slate.com/technology/2015/07/rowhammer-security-exploit-why-a-new-security-attack-is-truly-terrifying.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Lo, Rowhammer!
Security researchers just revealed a computer vulnerability that’s frightening, amazing, and unlike anything else.
July 28, 201511:25 AM
Photo illustration by Lisa Larson-Walker. Photos by Hellen Sergeyeva/Shutterstock and Photodisc/Thinkstock.
The now-ubiquitous Heartbleed, the devastating Sony Pictures hack, the $1 billion Russian bank hack, the theft of sensitive government personnel files—one hole in a cybersecurity edifice can cause the whole thing to crash down. New reports of an Android text message vulnerability, so far unrevealed yet affecting almost a billion devices, underscore how every new computer technology seems to open up even more possibilities for hackers. Security fixes, from Chrome patches to Windows hotfixes, hold the walls in place. But what if you had a security hole you couldn’t patch?
Rowhammer.js, a new security attack revealed in a paper by security researchers Daniel Gruss, Clémentine Maurice, and Stefan Mangard, brings a truly new wrinkle to our understanding of computer vulnerabilities. “But I keep my system patched and up to date!” you might say. Rowhammer is here to tell you that’s not enough. Though the tech industry has known about the bug that Rowhammer exploits for several years, it was only this March that researchers at Google’s Project Zero revealed how it could be used by attackers.
Why is Rowhammer so scary? Because it doesn’t afflict your software but finds a weakness in your hardware, a physical problem with how current memory chips are constructed. So it doesn’t matter whether you’re using Linux, Windows, or iOS: If an Intel chip (or an AMD one, or possibly others) is inside, so is Rowhammer. Incredibly, Gruss, Maurice, and Mangard’s paper reveals how to exploit it from a simple webpage.
Chipmakers have known about Rowhammer since at least 2012. The problem affects Intel processors going back as far as 2009. Describing a remote Javascript attack using Rowhammer, Gruss, Maurice, and Mangard’s paper is a wake-up call. Previously, taking advantage of Rowhammer required local program execution on a computer—in other words, the computer already needed to be partly compromised. But now, any webpage can potentially exploit Rowhammer to arbitrarily access your data, perhaps even by gaining full control over the computer. And again, it doesn’t matter what operating system you’re using, since the problem is in the physical circuits of your memory chips. As the security researchers explain, it is “the first remote software-induced hardware-fault attack.”
The basis of many exploits, including Rowhammer, is a program getting access to places it shouldn’t. In the abstract, computers distinguish between programs (the code that runs) and data (the information that the code runs on), when in actuality a program is just a particular kind of data that a computer treats in a special way. Many exploits that take control of a computer, from buffer overruns to Microsoft Office hijacks, revolve around contriving a particular stream of data that worms through an accidental hole between where the data is supposed to be and where the program is. Part of the attacker’s “data” is the attacker’s own program, which then overwrites the user’s program to give the attacker control over the user’s computer that he shouldn’t have.
Here’s a classic example from xkcd:
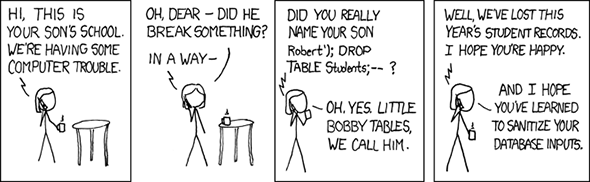
Cartoon by xkcd.com (https://xkcd.com/327/)
The gag is that Robert’s name actually contains a bit of executable database code. Because the school’s computers failed to treat Robert’s name merely as data but mistakenly took part of it (the “DROP TABLE Students;” part) as an actual program instruction, Robert’s name instructed the computer to delete the whole database. (Oops.)
Rowhammer, as the authors write, can cause data to be executed as code: As they put it, “Bit flips caused by row hammering breach the CPU’s memory protection.” What’s new with Rowhammer is how that border is made porous. Rowhammer is not a code bug but a hardware bug, a weakness in a particular set of memory chips. Software, whether it’s Windows or Linux or Firefox or Chrome, can only try to work around the problem to prevent it from being exploited; it can’t fix it. But here, there can’t even be a software hotfix. Which makes Rowhammer an amazing and frightening phenomenon.
Rowhammer takes advantage of a design defect in dynamic random-access memory, or DRAM, chips, which provide the high-speed data storage for a computer’s CPU. The most common DRAM standard today is called DDR3, ubiquitous on laptops, workstations, servers, phones, and tablets. A single DRAM chip contains billions of electrical capacitors, each of which stores a single bit. The sheer density of capacitors on these memory chips, however, causes a problem. By “hammering” a row of bits repeatedly, constantly changing their values, an attacker can sometimes induce an electrical interference in which capacitors in a different, adjacent row are mistakenly flipped. If the attacker can sufficiently control what’s in that adjacent row, then the attacker can manipulate your computer without authorization. Researchers at Google’s Project Zero were able to gain kernel privileges via Rowhammer and thus full read-write access to a computer’s memory.
Rowhammer wouldn’t be so scary, however, if it could be exploited only locally, by downloading malware. But the authors of this new paper found a way to trigger Rowhammer simply through Javascript on a webpage—the scripting language used by almost every site today. Yet browsers can’t patch the bug because there’s nothing they can patch. It would take a BIOS firmware update, beyond most users’ capacity to install, to fix the problem on vulnerable systems. Otherwise, the best one can do is mitigate the issue by turning off Javascript on untrusted sites. The paper mentions the possibility of slowing down Javascript in the browser to reduce vulnerability to Rowhammer, but Gruss told me he considers browsers unlikely to take such a performance hit.
There is some good news: Rowhammer is difficult to control. While it’s comparatively easy to use Rowhammer to flip unauthorized bits, it’s considerably harder to flip the right bits in order to take control of a computer. It’s been done, but only locally so far; the Rowhammer.js paper doesn’t provide a full exploit to take control of a computer. Rowhammer.js’s bitflips could crash your computer or give a hacker a peek at unauthorized data, but full remote access might prove more of a challenge. Consequently, as Gruss told me, the likelihood of being attacked via Rowhammer right now is low; there are easier avenues of attack currently available. The paper’s attack would work best, Gruss said, if you “attacked thousands of machines and succeeded on a few of them.” This doesn’t rule out the possibility of more advanced exploits, however. The significance is not in the ease of the vulnerability, but in its pervasiveness and the difficulty of fixing it—as well as the conceptual scariness of random webpages making your physical hardware malfunction.
One message this should send concerns the secrecy of hardware-makers when it comes to security bugs. Gruss told me that chipmakers like Intel filed patents back in 2012 to mitigate Rowhammer, but participated little in security discussions, which is why it took several years before the authors of “Rowhammer.js” created their remote attack. The scope of Rowhammer is still unknown due to the need to test it on every combination of CPU and physical memory—there have been reports of it also affecting newer DDR4 memory—though chances are chipmakers know a lot more than the rest of us. Hardware-makers need to become more involved in security. Hardware bugs like Rowhammer may be comparatively rare next to software holes, but we certainly haven’t seen the last of them.
This article is part of Future Tense, a collaboration among Arizona State University, New America, and Slate. Future Tense explores the ways emerging technologies affect society, policy, and culture. To read more, visit the Future Tense blog and the Future Tense home page. You can also follow us on Twitter.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK