

How to Protect Hackers From Your Privacy
source link: https://hackernoon.com/how-to-protect-hackers-from-your-privacy
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Security is important!
For the average human, your daily internet habits might not matter. But for hackers, well, your data is money. Data big or small is valuable.
In this blog, I’m going to discuss how we can secure our web accounts, web servers, mobiles, Windows systems & Linux systems.
Blog Agenda:
Web accounts.
Web servers.
Windows systems.
Linux systems.
Key points.
Web Accounts:

Web accounts are really easy to hack. All that the process really needs is patience.
General Advice:
Keeping a strong password with a minimum of 12 characters, containing numbers, small letters, capital letters, symbols, spaces, etc.
Enabling 2-factor authentication using your phone number, email, or a third-party application.
You can also follow these special steps to be aware of database leaks or breaches:
Check password leak websites regularly for your email or username. If you find your information on these sites, then you can immediately change your credentials and also verify how much the hacker knows about you.
Use tools such as Dashlane which provides password protection and dark web breach intel to you whenever it detects such an incident.
Tips and Tricks:
There are certain tricks you may want to follow in case you don’t want your account to be hijacked by some random hacker with the right password.
You can secure your accounts by using the regular password combinations everyone follows which are symbols & numbers. But that’s a minimal level.
You can do more to outsmart hackers by using ALT symbols. With each increase in characters, it may take 1 million years to crack your password.
I will be dead by that time, don’t know about the hacker. The hacker or anyone, in that case, cannot access your accounts without the right password.
Sure, there are other ways such as phishing, keylogging, etc. we will look into those in a while.
These are the ALT symbols and their ALT keys:
™ Alt+0153 Trademark
© Alt+0169 Copyright
® Alt+0174 Registered
‰ Alt+0137 Per mille (per thousand)
± Alt+241 Plus or Minus
¼ Alt+0188 Quarter
½ Alt+0189 Half
¾ Alt+0190 Three quarters
≡ Alt+240 Exactly Identical
≈ Alt+247 Approximately equal
≥ Alt+242 Greater than or equal
≤ Alt+243 Less than or equal
√ Alt+251 Square Root
ⁿ Alt+252 Power n
¹ Alt+0185 To the power of 1
² Alt+0178 Squared
³ Alt+0179 Cubed
π Alt+227 Pi
° Alt+248 Degree
∞ Alt+2368 Infinity
µ Alt+230 Micro
Σ Alt+228 Sum
☺ Alt+1 White Smiley
☻ Alt+2 Black Smiley
• Alt+7 Bullet 1
○ Alt+9 Bullet 2
♂ Alt+11 Male Sign
♀ Alt+12 Female Sign
↨ Alt+23 Up/Down Arrow
↑ Alt+24 Up Arrow
↓ Alt+25 Down Arrow
→ Alt+26 Right Arrow
← Alt+27 Left Arrow
↔ Alt+29 Right/Left Arrow
£ Alt+156 Pound
€ Alt+0128 Euro
$ Alt+36 Dollar Sign
¢ Alt+155 Cent
¥ Alt+157 Yen
ƒ Alt+159 Frank
₧ Alt+158 Peseta
α Alt+224 Alpha
ß Alt+225 Beta
δ Alt+235 Delta
Ω Alt+234 Omega
► Alt+16 Point Right
◄ Alt+17 Point Left
■ Alt+254 Stop
▲ Alt+30 Point Up
▼ Alt+31 Point Down
§ Alt+21 Section
¶ Alt+20 Paragraph
“ Alt+0147 curly double open quote
” Alt+0148 curly double close quote
« Alt+174 Quotation Mark
» Alt+175 Quotation Mark
♥ Alt+3 Heart
º Alt+0176 Degree symbol
œ Alt+0156 Latin small ligature oe
• Alt+0149 Bullet
↻ Alt+8635 Clockwise Open Circle Arrow
↺ Alt+8634 Counterclockwise Open Circle Arrow
Ø Alt+0216 Diameter
Ñ Alt+0209 EnyeThis ALT code list was compiled by postpresentation.com
You can also choose 2-factor or multi-factor protection which also reduces the risk exponentially.
Ultimately, those are all the processes one needs to practice in order to protect your social media accounts or any accounts in general.
Web-Servers

Web servers are machines accessible by anyone with the correct IP.
Why do Web Servers Need Protection?
Because they collect user data. This includes data not just from the admin but everyone else who is using the platform.
This can be achieved by implementing firewalls, port number changes, and having regular software updates.
Here is what is needed to be secured in a server:
Server firewall.
Database.
Scan source codes to a certain level for vulnerabilities.
Launch Bug bounty programs.
Server firewall:
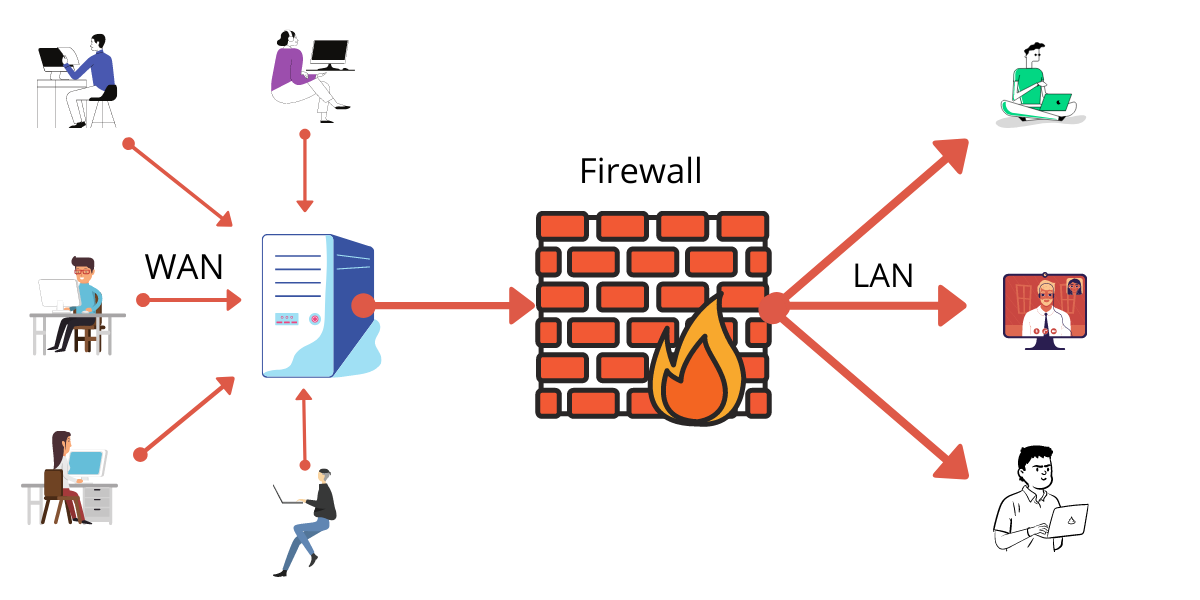
The first thing to do in firewall protection is to change all of the default passwords and default users with a safe and secure password.
Secondly, we need to limit the access of the firewall to as few people as possible. Ether by using blocks to other admins or even eliminate other admins’ permissions on the config files.
Thirdly, disable simple network management protocol (SNMP) or configure it to use a secure community string.
After the above is done we need to architect zones that we need to forbid or allow access to anyone other than the admin.
The best thing to do is other than the default HTTPS service which runs on PORT:443 we need to block all unnecessary ports and change the port numbers of all the other necessary services for example: change SSH port default: 22 to port:1000 or anything else and set up a forward of all the specific traffic from the service which is SSH from port 1000 to port 22 using the firewall. This reduces the chance of any possible port scanners taking a delay in searching the specific port in the web IP.
After the above is completed we need to concentrate on the ACL or access control list that contains all the rules required to provide access to a specific service in the server.
To put this into context the normal person in max may have access to the web page and the admin will have access to the ssh connection (if the admin is in the same network or via an authentication portal) other than this, no one can access the various services provided by the website.
ACL has a list of rules to also manage port monitoring and logging of firewall activity.
After the ACL has done its job it’s recommended that an expert checks the work. If this is an industrial environment, there are network professionals who will look into the various firewall rules. They tend to modify them if they are of any threat.
Database:
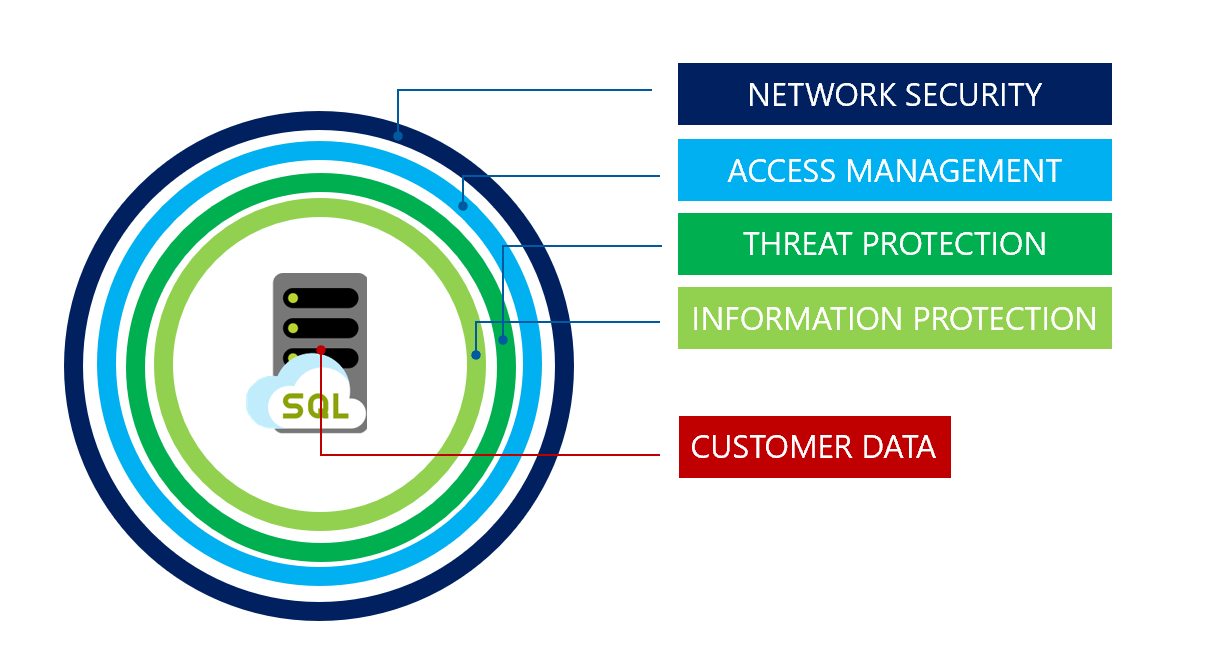
Database security is a key element in data stability and safety.
If there is a data breach the hackers can get their hands on juicy information, for example: Credit card information, phone numbers, names, address, IP, etc.
This may not look like much but in the wrong hands, this information can also be used in fraud.
Firstly, we will look into the basic stuff things such as audits and updates which should be done regularly.
Secondly, we will look into encryption.
A company should hire a cryptographer or an expert in that manner to create a unique rainbow table that can be used to store data in a much safer way. In case you are using a database such as MySQL then it comes with its encryption but it is good that you add a layer of protection upon it.
Thirdly, backups are really important if by any means your data is blocked by malware or it is lost due to an error then backups are really handy now.
Fourthly, use a separate server from the main server to store the database that has its firewall and secure environment that only the system administrator and a certain application combined can access to better ensure the protection of the database from potential malware and ransomware.
Scan source codes to a certain level for vulnerabilities.
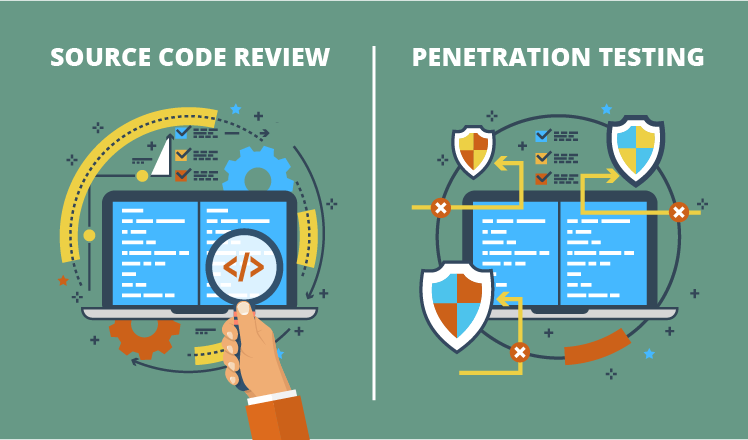
If you are a developer then you will be familiar with Github.
You can upload the source code of your application not entirely but as snippets and scan them using SYNK.
Synk uses a scanner to scan the code to locate potential endpoints or libraries that can be vulnerable and gives the option to manually patch or automatically patch the code.
This is particularly useful to check for developer errors before publishing.
You can hire a Professional analyzer also who is internal to the organization and also conduct the code review.
Launch Bug Bounty Programs

Sometimes you will need external views or creative views to get to the issue.
These individual hackers all over the world participate and try to hack the vulnerability which might be fatal to the company depending on the risk factor and priority of the company.
If they find a potential vulnerability or a bug they are rewarded on the basis of the intensity of the bug.
Where does it stand in the priority and what is it affecting? These factors play a vital role in the end payout.
This is a win-win situation for both the company and the hacker. Both have profited via this program.
These are the ways you can protect a web server on the backend. There are also many things to be done on the front end. I have explained various exploits done on the front end you can check out my article on that topic on that ‘self-publicity‘ link to the article.
Windows Systems
Windows is a commercially highly used Operating System that in all cases is important to protect.
Being a Proprietary Software it does not have any kind of open-source community such as Linux to patch potential bugs for them instead they hire white hat hackers for the work.
Things to be careful of in windows:
Virus & Anti Virus.
Phishing.
unwanted services.
Be far away from pirated software.
Virus & Anti Virus
Virus, malware, or ransomware are really common for windows systems.
The best practice is to keep updating Windows Defender, and never turn off the real-time protection of the system.
The virus protection from Windows or Windows Defender has an adequate amount of security to protect you from unsafe downloads.
Phishing

Phishing or Social Engineering is a powerful technique. It is a tool used for convincing the target to do what you intend by manipulating his thoughts. It is tough but effective.
Usually, hackers pose as legit people with the same interest as you and convince you to click on links, or tell you to download certain malware on the system to gain system access to your files.
Or else use the biggest weakness of a person -- his curiosity --to make him install software or connect a USB stick to his system to gain unauthorized access.
Unwanted Services
Services that are not in much use and are simply running in the background of the system can also lead to a lot of problems if maybe they are vulnerable and a hacker can hack them.
You can use the task manager to go to their services section and disable such services from running in the background and problems solved.
Beware of Pirate Software
Stay away from pirated software. Remember Piracy can sometimes lead to Bankruptcy.
Follow the above things and you are safe to go and use windows.
Linux Systems
Linux systems are open source and are constantly checked by millions of users for vulnerabilities.
They are constantly patched, making it less easy to hack. Even though it is hackable.
Reduce SUID File Privileges
SUID privileges are Superuser privileges in Linux and using these the hacker can gain root access into the server.
This is not good news for the server because by reducing the number of SUID files and keeping the rest in isolation we can reduce the chance of privilege escalation.
A huge database of SUID and privilege escalation enumeration tool is Linpeas and winpeas used in Linux and windows respectively.
Links to Github are used to enumerate the entire system to find SUID files and password files left by the dev team for later use.
It can be used also for priv-esc.
You can refer GTFOBins link to check for all the codes for priv-esc.
For example, nano has SUID permissions.
nano
^R^X
reset; sh 1>&0 2>&0I can enter this and get a Root shell using nano.
Key Notes
If you follow the above things there is a good chance that you might not get hacked.
But it really depends on your self-safety and interest to protect your privacy.
I have explained all I know on how I can help you be safe from Black hat hackers out there in the cyber world.
The goal is not to scare my readers but to warn you all that if your data falls into the wrong hands you can end up in a bad situation.
For example, your photos can be DeepFaked, your phone number used to mask another crime, and many more things.
So be careful and be safe.
If you want to know what all crazy stuff happens over on the dark web check out my other article completely covering the dark web and how to start a website in the dark web ‘self-publicity link to the article.
Sources
Contact me.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK