

Protect Against Log4j Data Exfiltration
source link: https://dzone.com/articles/do-you-know-if-you-are-a-victim-of-the-log4j-vulne
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Protect Against Log4j Data Exfiltration
Is the log4j vulnerability already exploited in your enterprise? Do you know what data is being exfiltrated? Protect your data assets with ease.
Join the DZone community and get the full member experience.
Join For Free We are following developments on the Log4Shell security vulnerability in Apache “Log4j 2" utility (CVE-2021-44228, CVE-2021-45046).
We are following developments on the Log4Shell security vulnerability in Apache “Log4j 2" utility (CVE-2021-44228, CVE-2021-45046).
We, at Theom, are actively helping multiple enterprises expose the impact of the log4j vulnerability and understand what data has been exfiltrated. We are sharing this post to help the defenders.
Establish if the log4j RCE vulnerability has been exploited.
Note: Vulnerability assessment products can only say if the software is vulnerable. Theom tells you if the vulnerability is exploited.
If the vulnerability was exploited, you need answers for questions like:
What data was exposed?
What data entities were exfiltrated?
What is the business criticality of the exfiltrated data?
What other data is at risk?
Further uncover other latent zero-days when exploited, by fingerprinting user and application data access behavior.
Background
The latest vulnerability in the popular Apache Log4j has taken the security world by storm. The log4j vulnerability is so widespread, it may take many weeks to patch and fix. Log4j is a logging library used in almost every Java application. It is very popular as it makes it easy to create a log4j class and pass the suitable parameters for logging within an application. Alibaba cloud security team discovered the vulnerability, and a patch has been made available since then. Refer to the CISA site to track the latest information on this vulnerability. Now that the remote code execution vulnerability in log4j is available with open-sourced proof of exploits, the race is between low-skilled attackers and defenders.
How Are We Helping Against Exploits and Other Zero-days?
Theom is a data security product that protects your data in the cloud (AWS), SaaS data warehouses (Snowflake..), Message Queues(Kafka..), and APIs (Nginx, Envoy). It computes “API drift” and does automatic vendor recognition, which helps track down zero days like log4j.
The First Line of Defense: Unknown Vendor or Malware C2
Theom automatically detects the vendors with whom data is shared. Any new vendor or unrecognized vendor data access is flagged.
In our internal sandbox, the screenshot below shows the type of data sent over to “Tsunami botnet”, a known C2 of the log4jshell exploit. Theom automatically stitches together the API calls originating from various sources and more importantly tracks the data shared with the C2. It triggers an alert automatically, drawing the security practitioners’ attention to the attack in progress. Additionally, Theom identifies malicious botnets (IOCs, indicators of compromise) known to be actively exploiting the log4j vulnerability.

In some cases, really sophisticated attackers can pivot data through a known vendor. So using the identities of vendors is not be sufficient, this is where behavior analysis comes in handy as a second line of defense.
The Second Line of Defense: API Behavioral Fingerprinting (JNDI Abuse)
Theom fingerprints the “normal” of API request/response and identifies drifts in API usage and parameters. Suppose the payload of traffic from an infected host has a different request or response from past transactions. In that case, Theom will identify and flag such access and bring it to the attention of the security practitioner. At Theom, we deployed a proof of concept Log4Shell attack in our environment to demonstrate the result.
The screenshot below shows that if a JNDI reference resolves to a new RMI or uses a new protocol, Theom will identify such an API call as a data risk. Guided remediations, including patching details or changes needed to make data secure, are indicated along with such data security risks on the Theom dashboard.
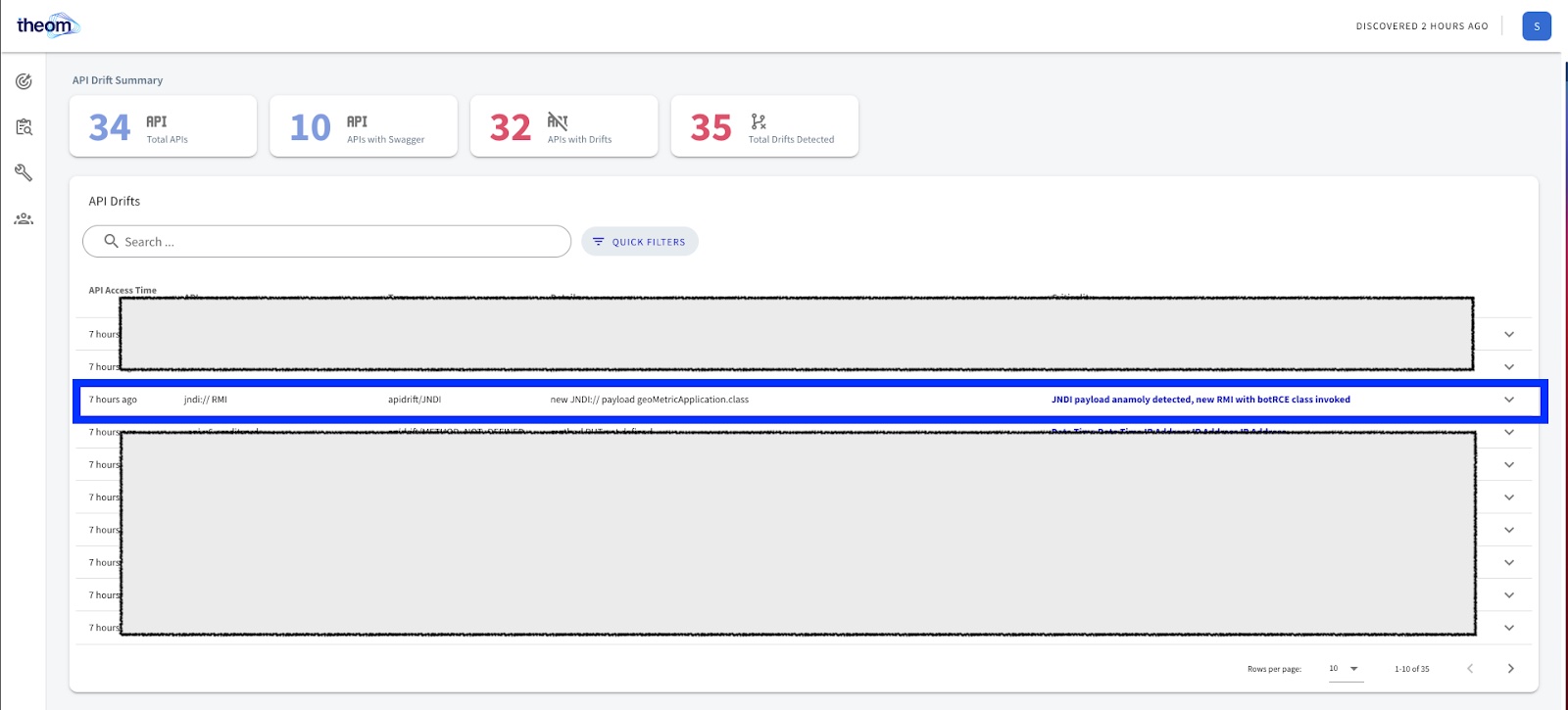
The above behavior analysis works against any zero-days that trigger a behavior change in the way data is accessed over APIs. Theom does not use any hardcoded patterns to detect behavior changes which is why it caught the use of JNDI with ease.
Automated Business Criticality
With the severity and critical nature of such vulnerabilities, a layered defense security strategy is the need of the hour. A security plan that builds on a foundational understanding of data, including finding anomalous access, putting perimeter filters (like WAFs) is essential to protect against zero-days like the log4j RCE.
While some tools can provide runtime application insights and tracing, Theom is the only security product to provide details on what data entities were transacted through the APIs and associate business criticality to those transactions. Enterprises using Theom can find the existence of the log4j zero-day and correlate it with any exfiltrated data. Additionally, they are protected against a similar situation in the future when such vulnerabilities are exposed.
Conclusion
Having a low-touch, holistic visibility of transactions happening for your cloud data at rest (AWS..), or API, message queue assets, and SaaS data warehouses (Snowflake), is essential to help you track and proactively remediate data security risks in your organization.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK