

STRIDE Threat Modeling: What You Need to Know
source link: https://dzone.com/articles/stride-threat-modeling-what-you-need-to-know
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Threat modeling is the ultimate shift left approach. It can be used to identify and eliminate potential vulnerabilities before a single line of code is written. Employing threat modeling methodologies should be your first step toward building networks, systems, and applications that will be secure by design. STRIDE is a model of threats that can be used as a framework in ensuring secure application design.
STRIDE - Threat Modeling Methodology
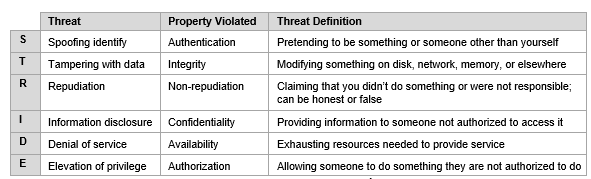
STRIDE was developed in the late 1990s by two engineers working at Microsoft, Koren Kohnfelder and Praerit Garg. STRIDE’s threat model accounts for six different threat categories:
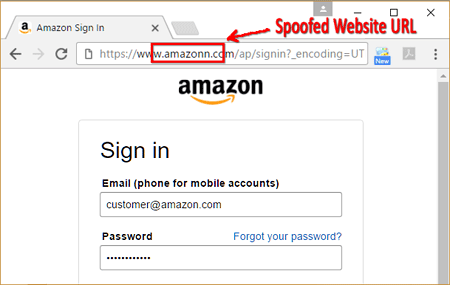
Spoofing Identity
Identify spoofing occurs when the hacker pretends to be another person, assuming the identity and information in that identity to commit fraud. A very common example of this threat is when an email is sent from a false email address, appearing to be someone else. Typically, these emails request sensitive data. A vulnerable or unaware recipient provides the requested data and the hacker is then easily able to assume the new identity.
Identities that are faked can include both human and technical identities. Through spoofing, the hacker can gain access through just one vulnerable identity to then execute a much larger cyber attack.
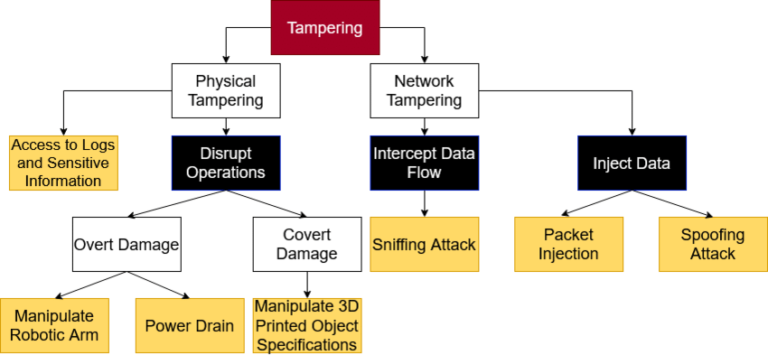
Tampering With Data
Data tampering occurs when data or information is changed without authorization. Ways that a bad actor can execute tampering could be through changing a configuration file to gain system control, inserting a malicious file, or deleting/modifying a log file.
Change monitoring, also known as file integrity monitoring (FIM) is essential to integrate into your business to identify if and when data tampering occurs. This process critically examines files with a baseline of what a ‘good’ file looks like. Proper logging and storage are critical to support file monitoring.
Repudiation Threats
Repudiation threats happen when a bad actor performs an illegal or malicious operation in a system and then denies their involvement with the attack. In these attacks, the system lacks the ability to actually trace the malicious activity to identify a hacker.
Repudiation attacks are relatively easy to execute on e-mail systems, as very few systems check outbound mail for validity. Most of these attacks begin as access attacks.
Information Disclosure
Information disclosure is also known as information leakage. It happens when an application or website unintentionally reveals data to unauthorized users. This type of threat can affect the process, data flow, and data storage in an application. Some examples of information disclosure include unintentional access to source code files via temporary backups, unnecessary exposure of sensitive information such as credit card numbers, and revealing database information in error messages.
These issues are common and can arise from internal content that is shared publicly, insecure application configurations, or flawed error responses in the design of the application.
Denial of Service
Denial of Service (DoS) attacks restrict an authorized user from accessing resources that they should be able to access. This affects the process, data flow, and data storage in an application. DoS attacks are getting bigger and more frequent, with an estimated 12.5 million DDoS weapons detected in 2020.
One of the most famous attacks was on Google in 2017. According to Google, “The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us. This demonstrates the volumes a well-resourced attacker can achieve: This was four times larger than the record-breaking 623 Gbps attack from the Mirai botnet a year earlier.”
Elevation of Privileges
Through the elevation of privileges, an authorized or unauthorized user in the system can gain access to other information that they are not authorized to see. An example of this attack could be as simple as a missed authorization check, or even elevation through data tampering where the attacker modifies the disk or memory to execute non-authorized commands.
Identifying a Threat Modeling Methodology
One reason that threat modeling is performed as a first step is to obtain an objective viewpoint of the big picture for the project. It will also help define the locations of potential security vulnerabilities. This process can be done once the design has been defined conceptually.
Though STRIDE is a highly popular and effective methodology, several others are also available including PASTA, VAST, Trike, OCTAVE, and NIST. Some are more appropriate for different IT disciplines or have different focuses, such as applications instead of networks, for example.
No threat modeling technique is perfectly tailored to a specific use. You should choose the one that most closely aligns with your goals. However, your DevOps team should be encouraged to adapt or customize threat modeling techniques to better fit their specific use case.
Going forward, remember that your threat model is a living document and needs to be constantly reviewed and updated. After a system-wide threat model has been performed it can be valuable to perform mini threat models as a secure engineering design requirement.
Regarding Frequency
- Full initial threat modeling should be performed and repeated annually.
- Delta threat modeling should be performed on any newly proposed feature or significant change at the design phase.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK