

MS Windows Defender & DeCSS
source link: https://www.arch13.com/ms-windows-defender-decss/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
MS Windows Defender & DeCSS
On 7/20/2021 at 7:42pm, Windows Defender definitions daily update picked up a copy of the famous DeCSS DVD encryption software as a Trojan and performed an immediate quarantine, followed by deletion 60 seconds later. This appears to be a false positive, notable only because the software it is incorrectly targeting is so famous.
It picks up the software as the Glupteba!ml Trojan per the screenshot below, marking it as a Severe threat;
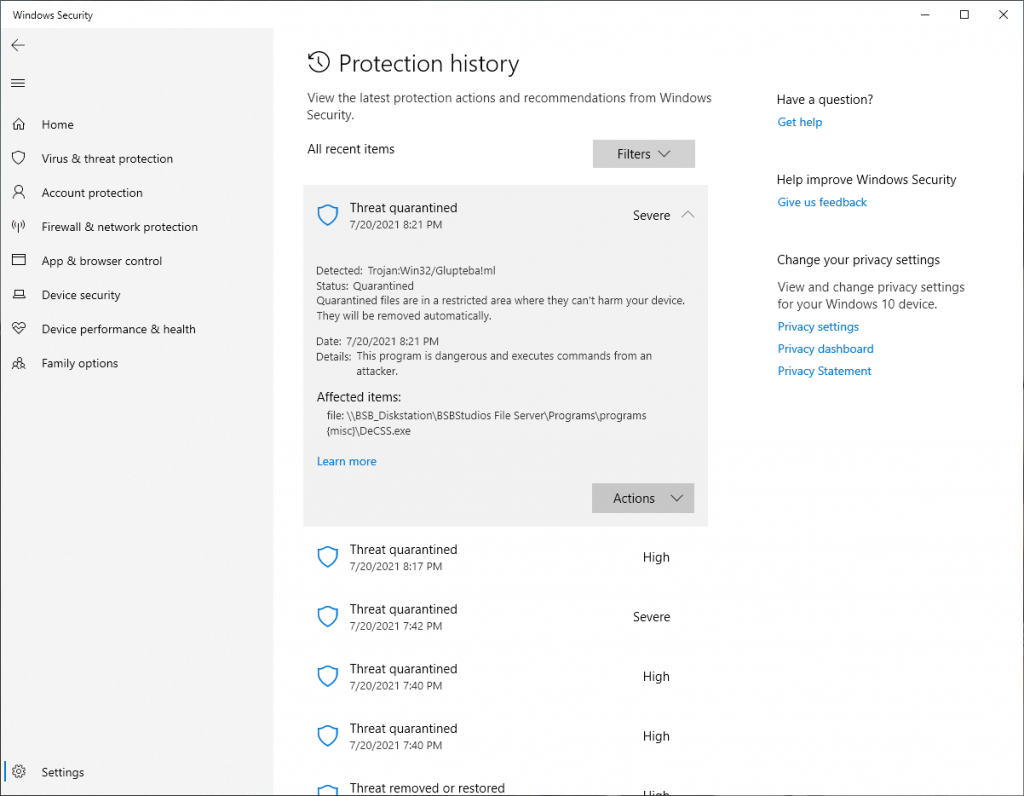
Windows Defender is also misdiagnosing XFX Keygen programs from the mid-2000’s as high threats. Yes they crack software, but that’s a medium to low threat unless the concern is something bigger.
Download the File
If you are feeling brave, here is the file in question: DeCSS.exe <— Warning! Here be dragons. Download this at your own risk. Know the risks.
I vouch for the provence of this file as follows: It was acquired via DirectConnect from a file hub run by 2600 affiliated contributors in 2004. It’s code signature matches the incorrectly used 1999 code signature of David Fawcus that Jon Lech Johansen used to sign the executable.
Here is the metadata:
Separately, here is the XFX Force Keygen being tagged as a false positive High threat
Here is the file: KEYGENXFORCE.exe <— Warning! Here be dragons. Download this at your own risk. Know the risks.
File Analysis & Log Files
Kapersky finds no threat. On VirusTotal, 32 out of 72 engines misidentify this as malicious.
Here is last nights log file
-------------------------------------------------------------------------------------
MpCmdRun: Command Line: mpcmdrun -restore -all
Start Time: Tue Jul 20 2021 20:10:48
MpEnsureProcessMitigationPolicy: hr = 0x1
ERROR: MpQuarantineRequest failed: name: HackTool:Win32/Keygen!MSR, GUID: {8003F52C-0000-0000-33A7-F7F5B974DFEF} (80508014)
ERROR: QuarantineRestore failed (80508014)
ERROR: MpQuarantineRequest failed: name: HackTool:Win32/Keygen!MSR, GUID: {8003F52C-0000-0000-B7CE-870973926357} (80508014)
ERROR: QuarantineRestore failed (80508014)
ERROR: MpQuarantineRequest failed: name: Trojan:Win32/Glupteba!ml, GUID: {80040956-0000-0000-D48C-06A3EB93B95A} (80508014)
ERROR: QuarantineRestore failed (80508014)
MpCmdRun.exe: hr = 0x80508014.
MpCmdRun: End Time: Tue Jul 20 2021 20:10:48
-------------------------------------------------------------------------------------
You dump the log by opening an elevated CMD window in the folder
C:\Program Files\Windows Defenderfolder.
You then execute
mpcmdrun -restore -listall to list all quarantined items. Follow that with mpcmdrun -restore -allto restore all (Danger!)
You’ll notice my log above lists a failed code of 80508014 for each file. So instead I execute
mpcmdrun -restore -all --Path D:\tempto restore it to a different location than the NAS it was deleted from.
The data will then be fine at rest in D:\temp until I try to copy it back to where Defender Deleted it on the NAS. At which point it deletes it again.
Closing and General Info
My OS Build is 19043.1110, version 21H1 installed on 6/10/2020.
The data at rest on the NAS lives on a DS920+ Synology with a 4tb Raid 1 volume in BRTFS format. This NAS volume is shared via SMB as the Z: drive on all machines in the house. The NAS contains other separate volumes servicing an Internet facing Pi running Traefikv2 with multipule services on a separate VLAN.
MS Has pushed out an update that appears to fix the false positive on DeCSS as of 7:42am this morning. As of 8:10pm on 7/21/21 it is still misidentifying XFX Keygens as a threat.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK