

What's New with Splunk Enterprise Security 6.6?
source link: https://www.splunk.com/en_us/blog/security/what-s-new-with-splunk-enterprise-security-6-6.html
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

We are super excited to announce updates to Splunk Enterprise Security (ES) with our latest 6.6 release. Get ready for the latest and greatest that Splunk Enterprise Security has to offer. Let's dive right into it.
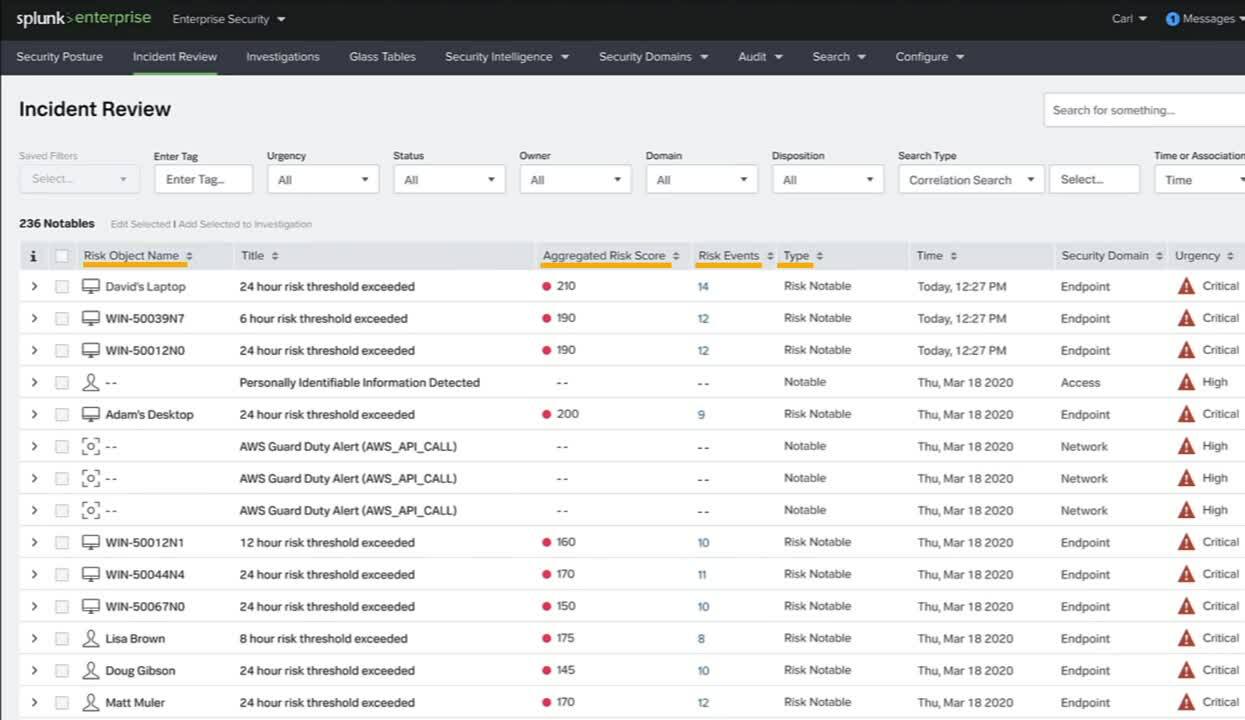
Incident Review Dashboard Enhancements
As you would expect with any Splunk release, the Splunk Enterprise Security 6.6 update is here to make your job easier. The first thing that jumps off the page with this Splunk Enterprise Security update is a new and improved Incident Review Dashboard. It allows for a refreshingly easy and modern way to filter Notable Events so that you see the most relevant information. This release is packed with new visualizations that allow you to display the number of Notable Events by urgency, status, owner, and security domain.
Incident Review Dashboard
When closing a Notable Event, you now have the ability to classify the disposition of a Notable Event as a True Positive, Benign Positive, and more. This classification allows Security Operations Centers (SOCs) to do accurate reporting on how well their detections work and is fundamental to the detection review lifecycle. The best part about this dashboard is that you can now save your filters and recall them at your convenience to quickly jump back into what you were working on, and set a saved filter as your personal default when you load Incident Review. We are confident that you and your teams will be wowed by the enhanced workflow.
More Screen Real Estate
Who doesn’t love more screen space? Based on customer feedback, we went to work on improving visibility so that you can do more with fewer context switches. You can now hide filters and visualizations so that your screen is focused on the Notable Events of interest. With a nuanced, focused screen, your SOC will become even more efficient by displaying exactly what you need.
RBA Event Timeline Visualizations
The Splunk team is all in on Risk Based Alerting. The reason behind this? Customers LOVE RBA. Taking investigations from days to minutes. Fewer false positives, higher true-positive rates and threat detections that traditional correlation simply misses. The new RBA Event Timeline in Splunk Enterprise Security will be a difference maker for you and your team.
RBA Event Timeline Visualization
In Enterprise Security 6.6 we have added enhanced capabilities for Risk-Based Alerting within the Incident Review dashboard. The new RBA Event Timeline visualizations allow your team to quickly identify timelines around contributing Risk events and provide a comprehensive view of the threat activity. You now have improved visibility between risk objects, risk attributions, threat objects, and the timeline of detection. With just a single click, you’ll see a new RBA event timeline visualization that gives you a bird’s eye view of all the contributing Risk Events for your Risk Notable Event.
Additionally, the Notable Events queue has been updated to give you at-a-glance RBA context, including new columns for Risk Object, Risk Score, Count of Risk Events, and Risk Notable Type. Most importantly, this will reduce Mean-Time-To-Detection (MTTD) and shorten Mean-Time-To-Resolution (MTTR) SOC metrics to get your team working even more efficiently by giving you instant situational awareness when a Risk Notable appears.
At Splunk, we believe that seeing is believing so check out this overview of how RBA can help you deliver results.
Be on the lookout for future updates with RBA as we work to make them more prominent in Splunk Enterprise Security moving forward.
Cloud Security Monitoring
It would not be a Splunk update if we didn’t mention Cloud Security. Included in Splunk Enterprise Security 6.6 is a new Common Information Model “Data Access” data model for cloud shared storage services such as Box, Google Drive, SharePoint, and OneDrive for all your cloud storage security monitoring needs. This is just the next step in our multi-release initiative to provide out-of-the-box Cloud Security Monitoring content that makes it even easier for you to monitor, investigate, analyze, and detect threats across multi-cloud environments such as AWS, GCP, and Microsoft Azure. This will enable you to build and strengthen a unified cloud security posture. Be on the lookout for more content that leverages the new “Data Access” shared storage data model in Splunk Supported Add-Ons and security detections from Splunk’s Security Research Team.
Get Started or Upgrade Today!
To make your life as easy as possible, Splunk Enterprise Security 6.6 updates are available in both Cloud and On-Prem environments. So no matter how you Splunk, you now have access to Splunk Enterprise Security 6.6.
Let us know what you think about the new and enhanced capabilities of Splunk Enterprise Security 6.6. Join a conversation or start a new one in the Splunk Community.
Happy Splunking!
Recommend
-
 27
27
README.md Syntax highlighting for Splunk's .conf files This project is public domain. Feel free to create your own branch and submit a pull request via Github or email me: colbyw at gmail dot c...
-
 41
41
Splunk conference is just around the corner, and we’ve got your back with the top news and sessions you won’t want to miss out on. ...
-
 56
56
Splunk Enterprise为其他组织提供数据搜索、分析及可视化功能,这些数据采集自网站、应用软件、传感器(注:通常指安全设备)及其他设备。Splunk Light小型IT网的日志检索与日志分析自动化、服务器与互联网监控的解决方案。
-
 15
15
``` docker pull splunk/k8s-metrics ```
-
 11
11
``` docker pull splunk/universalforwarder ``` ## Splunk Universal Forwarder in Docker! Splunk Enterprise is a platform for operational intelligence. Our software lets you collect, analyze, and act upon the untapped value of big data that you...
-
 9
9
Whiteblock X Splunk at ETHDenver
-
 9
9
PLATFORM What's New: Splunk Enterprise 8.2
-
 11
11
Welcome New Nutanix App for Splunk! 03/31/2016 This week Nutanix is made available...
-
 6
6
PLATFORM A New Way to Look Like Splunk ...
-
 12
12
Splunk adds new security and observability features New security and observability features will be added to Splunk Mission Control and its Observabili...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK