

Snyk @ Snyk: Enabling Kubernetes RBAC for Snyk’s Developers
source link: https://snyk.io/blog/snyk-at-snyk-enabling-kubernetes-rbac-for-snyks-developers/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.

Snyk @ Snyk: Enabling Kubernetes RBAC for Snyk’s Developers
Omer Levi Hevroni
April 14, 2021
As Uncle Ben once said, “With great power comes great responsibility.” This is also true of the Kubernetes API. It is very powerful, and you can build amazing things on top of it, but it comes with a price—a malicious user can also use the API to do bad things.
Enter Kubernetes RBAC (role based access control), which enables you to use the API in a controlled manner by granting only required privileges needed, following least privilege principle.
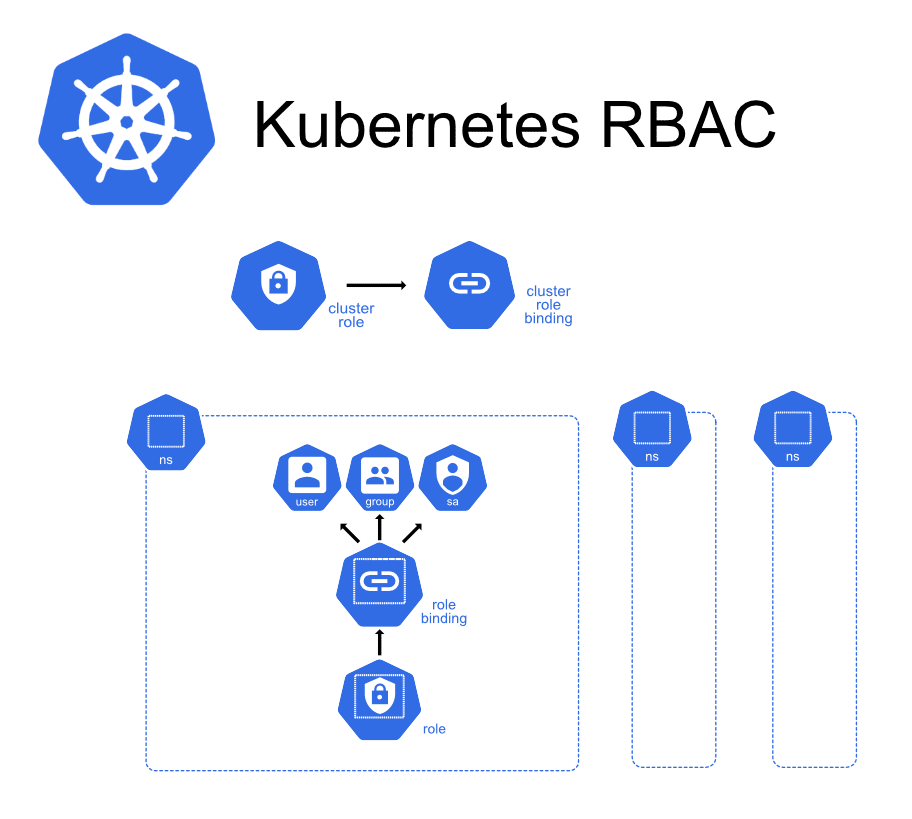 Kubernetes allows users to define roles inside namespaces and cluster roles outside namespaces.
Kubernetes allows users to define roles inside namespaces and cluster roles outside namespaces.But this just moves the problem somewhere else: now we need to have good processes around RBAC resources or a simple RBAC mistake could have a serious security impact. Take the example of a developer ‘accidentally’ granting the cluster admin role to the default service account in the default namespace. Oh, the horror!
Photo by https://unsplash.com/@arnykoor
The paved road approach to Kubernetes security
Ideally, we would like to allow every developer to create RBAC permissions as they desire, while still having guardrails in place for protection and to block things that are insecure. One way to achieve that is by enforcing a code review by AppSec for any change that includes RBAC resources. While this might work, it has some downsides:
- AppSec becomes a blocker, slowing down developers.
- Security becomes “magic” that only AppSec knows, as there are no published guidelines to what AppSec is looking for when reviewing such changes.
- We end up deepening silos, and preventing developers from owning security responsibilities, which further compounds the problem of AppSec being a bottleneck and slowing down developers.
The Kubernetes RBAC security checklist
At Snyk, we faced similar issues. We wanted to empower our developers and let them use the Kubernetes API without slowing them down. We started by compiling a list of security requirements for RBAC rules. The rules list is pretty short and based mainly on the CIS Kubernetes benchmarks:
- No wildcard resources or verbs
- No usage of built-in rules, as they grant too many permissions
- No bindings to service accounts in default namespace (which should be empty) or kube-system namespace (which runs sensitive workloads)
- No binding to default service account
- No usage of dangerous permissions, like create pods or read secrets
With our list compiled, we can do a few things with it:
- Publish it as our internal guidelines and require that all RBAC objects adhere to this list. Now the criteria are not “magic”.
- Ask our developers and security engineers to document any violation of this list as a security risk, and inform AppSec of such violations.
- Solicit feedback and invite all the developers to contribute and update the list so we break down the silos.
- AUTOMATION. After all, once we have a list, we want to make it ridiculously easy to test. 🙂
Automating Kubernetes configuration checks with Snyk IaC
In late 2020, Snyk announced a new product: Snyk Infrastructure as Code (Snyk IaC). Snyk IaC has a built-in set of rules we can use to test our IaC code, including Kubernetes manifests (Terraform, too, but that’s for another blog). One of the perks of working for Snyk is early access to any feature, and, even better, the ability to contribute back to the product. (By the way, if that kind of perk excites you, we are hiring, and looking for AppSec folks!)
So, after compiling our list, we reached out to the Snyk IaC team, discussing our Kubernetes RBAC checklist with them, and voila! We have five new checks in Snyk IaC to help us automate our security checks and make sure AppSec isn’t a bottleneck!
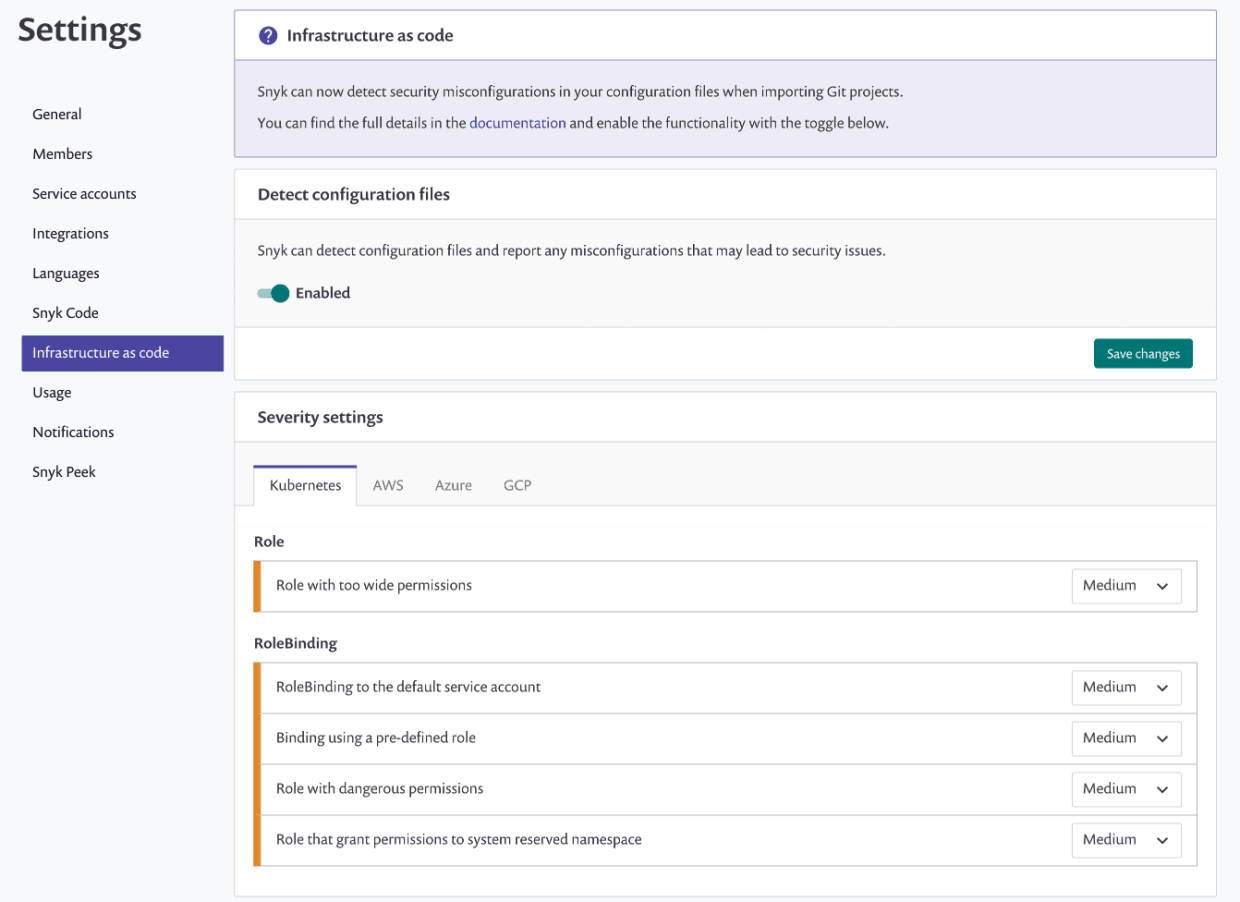
Making IaC security ridiculously easy for Snyk’s developers
Snyk IaC has the ability to scan via GitHub Actions and output results in Sarif format, which could be integrated with GitHub Security. But we wanted to take it a step further and show violations directly in our PRs, which Snyk IaC doesn’t do (yet). Our AppSec group did this by writing our own GitHub integration so that any change to our Kubernetes manifest files are automatically scanned with Snyk when committed, and if there is a violation, the developer will get a nice warning on the PR:
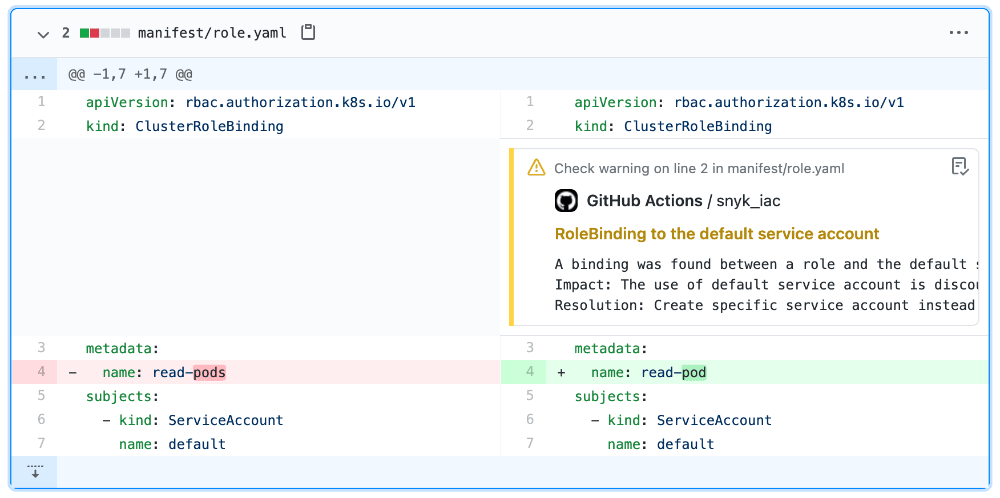
Now, all our developers are free to make RBAC changes without pausing to get AppSec involved and in AppSec can rest easier, knowing that Snyk is watching our back.
Want to have something similar for your team? Checkout the example repo here, and make sure you have a Snyk account—you can get started with IaC for free!
Recommend
-
 37
37
-
 38
38
RBAC RBAC(Role Based Access Control 基于角色的访问控制) 是安全领域一种授权(Authorization)机制。权限被授予给角色,角色又被赋予给主体。
-
 12
12
Kubernetes RBAC 详解 深入理解 Kubernetes RBAC 的用法 发表于 June 22, 2018 China 前面两节课我们学习了Kubernetes中的两个用于配置信息的重要...
-
 21
21
Permission manager : RBAC management for KubernetesPermission manager : RBAC management for Kubernetes
-
 15
15
为什么 RBAC 不足以保障 Kubernetes 的安全? 所有旧有的安全和合规规则和法规都需要以某种方式加装到 Kubernetes 上。不幸的是,像 RBAC 这样的旧的访问控制工具根本无法应对挑战。
-
 11
11
How To Access Kubernetes Dashboard On RBAC Enabled Azure Kubernetes June 9,2020 // Kubernetes...
-
 7
7
Azure Kubernetes Service – Azure RBAC for Kubernetes authorization At this year’s Ignite conference Microsoft announced the next major step of integrating Azure functionality into AKS: Azure RBAC for Kubernetes authorization.-...
-
 5
5
Kubernetes v1.12 二进制部署集群(HTTPS+RBAC) 作者: wencst 分类: docker,...
-
 4
4
在 Kubernetes RBAC Role/ClusterRole 规则中使用通配符 *在编写 Kubernetes RBAC Role/ClusterRole 中 rules 字段中定义的规则时,我们可以通过通配符 * 来实现规则中匹配任意字符的需求。 不过通配符 * 也不是可以任意使用的,下面是 rules 字段使用的...
-
 8
8
Kubernetes权限RBAC的基础和高级模式 - loftKubernetes 使组织构建、测试和部署其软件的方式现代化。由于其模块化、开源框架和基于角色的访问控制 (RBAC),公司可以创建高度可扩展且可靠的企业级集群,同时满足严格的安全和治理要求。RBAC 框架对不同成...
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK