WordPress Redux Plugin Vulnerability Affects +1 Million Sites
source link: https://www.searchenginejournal.com/google-web-stories-plugin-for-wordpress-gets-first-big-update/387560/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
WordPress Redux Plugin Vulnerability Affects +1 Million Sites
Redux Gutenberg Blocks Library & Framework, with over 1 million active users, patched a CSRF vulnerability
- SHARES
- READS

Redux, a popular WordPress plugin with more than 1 million active installations recently patched a vulnerability. The vulnerability allowed an attacker to bypass security measures in a Cross-Site Request Forgery (CSRF) attack.
Cross-Site Request Forgery
A Cross-Site Request Forgery (CSRF) attack is a method where an attacker exploits a vulnerability in the code that allows them to perform actions on a website. This kind of attack exploits the credentials of an authenticated user.
The U.S. Department of Commerce defines CSRF like this:
“A type of Web exploit where an unauthorized party causes commands to be transmitted by a trusted user of a Web site without that user’s knowledge.”
This particular attack bypassed security checks by exploiting a coding bug that caused a site to improperly validate security tokens called nonces. Nonces are supposed to protect forms and URLs from attacks.
The WordPress developer page describes nonces:
“WordPress nonces are one-time use security tokens generated by WordPress to help protect URLs and forms from misuse.
If your theme allows users to submit data; be it in the Admin or the front-end; nonces can be used to verify a user intends to perform an action, and is instrumental in protecting against Cross-Site Request Forgery(CSRF).
The one-time use hash generated by a nonce, prevents this type of forged attacks from being successful by validating the upload request is done by the current logged in user. Nonces are unique only to the current user’s session, so if an attempt is made to log in or out any nonces on the page become invalid.”
The flaw was in how the nonces were validated. This vulnerability was originally fixed in October 2020 but was reintroduced in a later update.
According to the WPScan security plugin site:
“The plugin did not properly validate some nonces, only checking them if their value was set. As a result, CSRF attacks could still be performed by not submitting the nonce in the request, bypassing the protection they are supposed to provide.”
WPScan and the WordPress Redux plugin both reported that the CSRF vulnerability has been fixed.
WPScan described the current issue:
“The plugin re-introduced a CSRF bypass issue in v4.1.22, as the nonce is only checked if present in the request.”
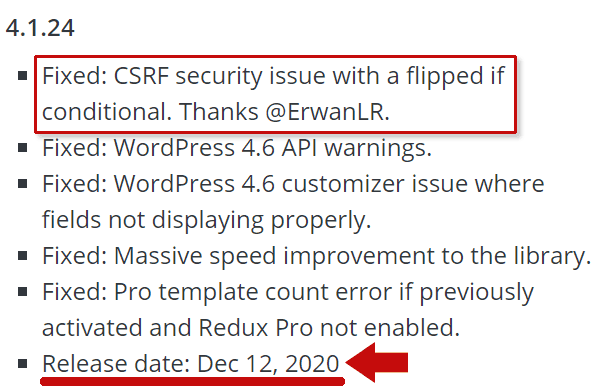
The Redux Plugin changelog states:
“Fixed: CSRF security issue with a flipped if conditional.”
Update Redux Gutenberg Blocks Library & Framework
Redux is a plugin that allows publishers to browse and choose from thousands of Gutenberg blocks and templates. Blocks are sections of a web page and templates are entire web page designs.
Take the frustration out of finishing projects.
Hand your deadlines over to expert freelancers who can get every task finished before every deadline - and keep your business up to top speed.
With over a million active users, Redux plugin is one of the most used WordPress plugins.
It is highly recommended that publishers using the Redux WordPress plugin immediately update to the latest version, 4.1.24.
Subscribe to SEJ
Get our daily newsletter from SEJ's Founder Loren Baker about the latest news in the industry!
Roger Montti
Roger Montti is a search marketer with 20 years experience. He provides site audits, phone consultations and content and link ... [Read full bio]
- Suggested Articles
-
SHARES
-
READS

WordPress 5.6 has been released with dozens of improvements and new features. Code named Simone (honoring singer Nina Simone), WordPress 5.6 has been met with a positive response, possibly because it didn’t break anything.
The substance of what’s new in WordPress 5.6 can be described as mostly good, some meh and one issue that’s ugly.
The Good
Enable jQuery Migrate Plugin Updated
The last two updates were somewhat rocky due to millions of websites breaking or accidentally updating with a beta version of WordPress.
The biggest potential issue was with the jQuery Migrate deprecations and updates.
WordPress 5.6 managed to avoid the legacy jQuery plugin issues experienced with the WordPress 5.5 update in August 2020. That was the update that caused websites to stop functioning in myriad and unexpected ways.
The reason those issues were avoided this time around is because WordPress 5.6 updated the Enable jQuery Migrate plugin in order to avoid a repeat of websites crashing.
When the plugin is active and the publisher is logged in, the plugin will detect outdated jQuery and log it, presenting a display at the top of page to signal the problem.
The plugin detects jQuery issues from page to page as the pages are served to the publisher as they browse the site.
There is an option to perform similar logging using pages served to users are browsing the site, but WordPress warns that this could create significant server load and recommends not turning it on.
There is a deprecation log page that shows the plugins responsible for the warnings. After updating a plugin the publisher can clear the old log and resume browsing again to see if the Enable jQuery Migrate plugin detect additional issues.
“With the above in mind, the Enable jQuery Migrate Helper plugin was updated for the release of WordPress 5.6, this provides a temporary downgrade path to run legacy jQuery on a site when needed.
The reason this is considered a temporary solution, is that the older version of jQuery no longer receives security updates, and the legacy version will not be patched manually if anything should occur that warrants updates to it.”
The Meh
WordPress 5.6 is shipping with their first version of WordPress that is (somewhat) PHP 8 compatible, the newest version of PHP that was released in November. However, this compatibility is meant to be regarded as beta compatible.
Because the WordPress PHP 8 compatibility news manages to be both good and less than good news it ends up being… meh.
As noted in the official guidance of WordPress 5.6 and PHP 8 Compatibility:
“WordPress Core aims to be compatible with PHP 8.0 in the 5.6 release (currently scheduled for December 8, 2020).
…Significant effort has been put towards making WordPress 5.6 compatible with PHP 8 on its own, but it is very likely that there are still undiscovered issues remaining.”
Publishers should test first before upgrading their version of PHP because themes and plugins at this point in time will very likely not be ready for PHP 8.
That’s why WordPress’ announcement framed PHP 8 compatibility as one of the first steps, because of potential compatibility bugs and because themes and plugins may not be compatible yet.
According to WordPress:
“5.6 marks the first steps toward WordPress Core support for PHP 8.”
The Ugly
One of the new features in version 5.6 that the WordPress team are rightfully proud of also contains a potential downside to it that if fully exploited could lead to a full site takeover.
WP 5.6 introduces the REST API authentication with Application Passwords Feature
The App Passwords Feature allows third party apps to connect to your website and add functionality.
“Thanks to the API’s new Application Passwords authorization feature, third-party apps can connect to your site seamlessly and securely. This new REST API feature lets you see what apps are connecting to your site and control what they do. “
However, according to WordPress security plugin publisher Wordfence, a social engineering attack could be used against a site administrator to obtain administrator credentials.
Social engineering is a hacking method that relies on tricking into providing information or access.
For example, Phishing is a form of social engineering where an attacker may email a victim posing as their bank, requesting that they reset their login credentials.
A link in the email leads to a copycat site that resembles a bank website where the victim enters their user name and password which is then harvested to obtain access to their banking account.
Wordfence describes a social engineering attack where a criminal could create an app that impersonates a trusted App, leading the site publisher to issue a password and allow a secure connection to their website. Wordfence describes the complexity of this attack as “trivial.”
According to Wordfence:
“An attacker could trick a site owner into clicking a link requesting an application password, naming their malicious application whatever they wanted…
Since application passwords function with the permissions of the user that generated them, an attacker could use this to gain control of a website.”
Wordfence produced a video describing and demonstrating the potential for a social engineering attack compromising the new Application Passwords Feature:
Wordfence Description of WordPress Application Passwords Feature Vulnerability to Social Engineering
WordPress 5.6 Overview
WordPress 5.6 is largely a success. There’s much that is so right with it. While it’s not a major advance it does have incremental improvements into site design functionality and improvements to functionality.
That this release manages to avoid the drama of the last two release makes this update a win considering there’s still a few weeks left in 2020.
Citation
WordPress 5.6 Warnings, Announcements and Documentation
Wordfence article:
WordPress 5.6 Introduces a New Risk to Your Site: What to Do
Official Announcement: WordPress 5.6 “Simone”
- Facebok
- SMS SMS
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK