Verified commits: sign your Git commits and avoid impersonation risk | Paul Dowm...
source link: https://www.pauldowman.com/posts/signing-git-commits-with-gpg/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Verified commits: sign your Git commits and avoid impersonation risk
A Git commit’s author might not be who you think it is.
I’m old enough to remember when it was easy to spoof the email sender (send fake email that appears to come from someone else). In the early days of the Internet most people didn’t even realize it was possible, so they were easy victims.
Email is delivered by SMTP, an open protocol, which is what has allowed it to flourish as a global, distributed system. But it was also designed without built-in cryptographic verification of the sender (in fact it was illegal to export cryptography from the US until 1992!). Now we have protection against this, such as SPF and DKIM, and most email services will warn you if the sender isn’t verified (or at least that it doesn’t come from the domain that it claims to).
But today a Git commit author is just as easily spoofed as email was in the 90s. Like email, Git is a global, distributed system, and by default it also doesn’t have built-in cryptographic verification of the author’s identity.
So how can you be sure that all commits are really from the author that you think they’re from? GitHub accounts can be compromised and malicious code can be hidden in pull requests (e.g. malicious packages added in hidden lockfile diffs, homoglyph changes to package names or domain names, changes in binaries if you have any in your repo, or maybe just a malicious change that you didn’t notice).
The solution
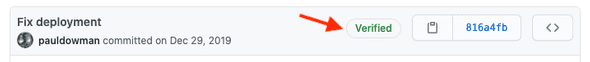
Git supports signing tags and individual commits, and the GitHub UI shows a “verified” label on signed commits:
Being sure of commit authors lets you focus more attention on less trusted contributions and it makes incident response a lot easier.
Git also supports rejecting unsigned commits.
How to
Here are a few options for setup guides:
- I would generally follow this guide from GitHub.
- If you’re using OS X this guide covers installing GPG and includes setting up
pinentry-macfor a passphrase entry dialog. - There’s also the Git docs.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK