

New MTE User Guide for Android OS developers - Operating Systems blog - Arm Comm...
source link: https://community.arm.com/arm-community-blogs/b/operating-systems-blog/posts/new-mte-user-guide
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
New Memory Tagging Extension User Guide for Android OS Developers

A few years have passed since the release in 2019 of Arm’s white paper Armv8.5-A Memory Tagging Extension (MTE) that introduced MTE to tackle the challenge of memory safety for security. Shortly after, in August 2019, Google announced they were partnering with Arm to design MTE as part of the commitment to improve the security of the Android ecosystem. Since then, different teams from Arm, Google, and their partners have been working on making MTE a reality. In 2022, we tested MTE on a development board for the first time with the Mediatek 9000, and more recently on a Vivo production device. So, the moment has come to provide developers with detailed documentation to make the most of MTE when new production devices come to market.
We are very happy to share the release of the MTE User Guide for Android OS that provides all the necessary information about MTE for developers.
Why MTE?
The MTE User Guide provides relevant data that explain why MTE was introduced to deal with memory safety bugs and the potential hacks that they can enable. Memory safety bugs are errors in handling memory by software, written in memory-unsafe languages like C, C++, and assembly. According to Google’s Memory Safety Report, memory safety bugs are the most common issue in the Android codebases. They account for over 70% of high severity security vulnerabilities and for millions of user-visible crashes - negatively impacting security and robustness of applications. A high density of memory safety bugs also directly correlates with poor user experience.
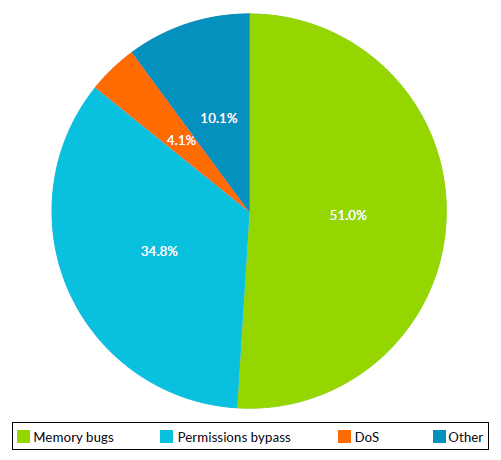
Figure 1. Memory safety bugs contribution to Android vulnerabilities.
The negative impact of memory safety bugs does not stop there. Developers know very well how difficult it is to diagnose a memory bug. Most of the time memory bugs manifest randomly, with sporadic crashes or silent data corruption, making them very difficult to reproduce. This increases both bug-fix and test costs in software development. Research shows that detecting these bugs earlier can reduce the cost by up to 6 times.
MTE’s Working Principle
The MTE User Guide explains to developers how MTE works. The Arm Memory Tagging Extension uses an underlying lock and key model for accessing memory. At runtime, when memory is allocated or freed, that region of memory is assigned a 4-bit memory tag (a.k.a. the lock) as part of the memory address. Memory accesses using pointers to that address need to use the same tag (a.k.a. the key) as part of the requested address.
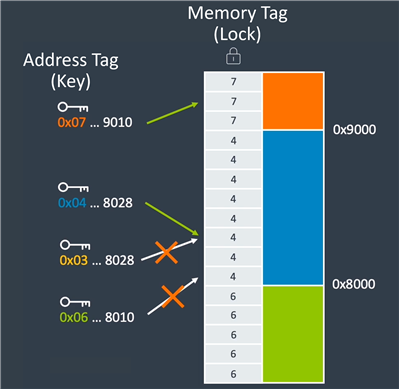
Figure 2. MTE key-lock model.
If the lock and key match, then memory access is granted. If the lock and key do not match, then a memory access violation has occurred. A mismatch between the lock tag in memory and the key tag in the address results in a tag check fault.
The memory accesses shown in Fig. 2 proceed as follows:
- 0x07…9010 - The key 0x07 matches the lock 0x07. Memory access succeeds.
- 0x04…8028 - The key 0x04 matches the lock 0x04. Memory access succeeds.
- 0x03…8028 - The key 0x03 does not matches the lock 0x04. Tag check fault.
- 0x06…8010 - The key 0x06 does not matches the lock 0x04. Tag check fault.
MTE necessarily causes some overhead, as tags must be fetched from and stored to the memory system. This overhead is related to the size and lifetime of memory allocations and whether tags and data are manipulated together or separately. The guide provides some tips to minimize this overhead.
How to use MTE
The guide provides a detailed explanation of the different modes MTE can be used.
Synchronous mode (SYNC)
| In synchronous mode, a mismatch between the tag in the address and the tag in memory causes a synchronous exception. This identifies the precise instruction and address that caused the failure, at the cost of a slight performance impact. |
Asynchronous mode (ASYNC)
| In asynchronous mode, when a tag mismatch occurs the processor continues execution until the next kernel entry, such as a syscall or timer interrupt. At this point, it terminates the process with SIGSEGV using code SEGV_MTEAERR. The processor does not record the faulting address or memory access. ASYNC mode has a smaller impact on performance than SYNC mode. |
As synchronous mode prioritizes accuracy of bug detection over performance, it is most useful during development or as part of a continuous integration system. In these situations, the precise bug detection capability is more important than the performance overhead.
On other hand, ASYNC mode is optimized for performance over accuracy of bug reports. The information about where the bug occurred is less precise, but ASYNC mode provides a low overhead detection mechanism for memory safety bugs. It is useful for production systems when performance is more important than detailed bug information.
The guide also lists a third mode called Asymmetric mode (ASYMM) that combines the benefits of SYNC and ASYNC modes. In asymmetric mode, read memory accesses are processed as SYNC, while write memory accesses are processed as ASYNC.
The guide explains the different ways MTE can be enabled in your project:
- Using the Android build system
- Using system properties
- Using an environment variable
- Using Android Manifest
Capturing and Interpreting a Bug Report
Once MTE has been enabled for use in your project, there are a few ways to capture the bug report. The bug report gives detailed information about the memory bug and identifies where it originated. The guide explains how the bug report can be captured:
- Using Developer Options in the Android device
- Using “adb bugreport“
Additionally, the guide showcases how to debug an application in Android Studio where MTE has been enabled from the Android Manifest. Android developers will find this method remarkably simple and straightforward, as when a memory safety bug causes a crash, the debugger takes you directly to the line immediately before the one responsible for the problem.
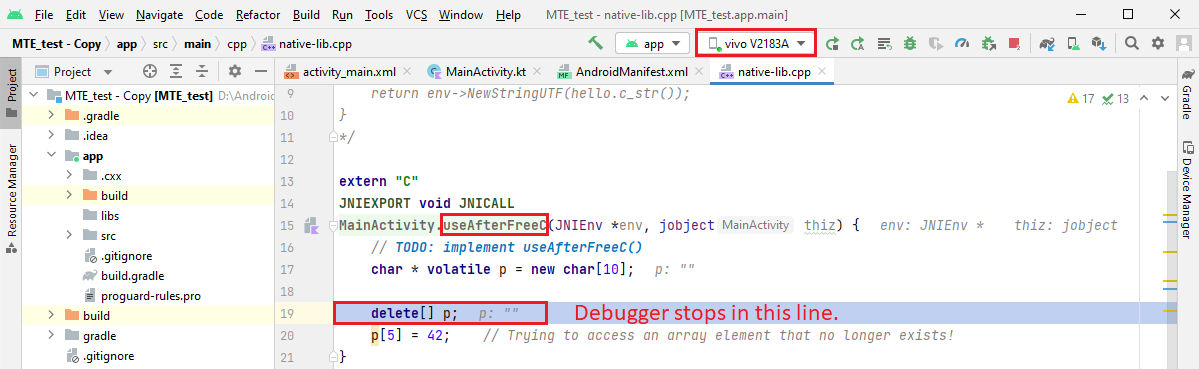
Figure 3. Debugging with MTE enabled in Android Studio.
Advanced Users
The guide has a section targeting advanced users. Complex software products can implement their own memory management system to optimize memory usage and improve the performance of memory handling. In this case changes will need to be implemented in the memory management to guarantee that the memory used by MTE to store metadata on each memory allocation or deallocation is not used, and it is left exclusively for MTE purposes. This section covers Unity’s experience when implementing MTE in their own memory allocators.
Conclusions
2023 is the culmination of several years of work to introduce MTE into the Android Ecosystem. Several partners have joined the initial effort from Arm and Google in testing and validating MTE in their software development. We expect to see this year new production devices supporting MTE. The MTE User Guide for Android OS will allow developers to make the most of this new technology and improve the robustness and security of Android applications. This will also positively impact on the quality of user experience.
We expect MTE to initially become part of the software development process, improving the quality of released products. As this new technology spreads and the usage becomes wider, we also expect the use of MTE in production devices. Then final users will be able to enjoy the added security and stability of software developed with MTE, and to provide their feedback and contribute to detecting memory safety bugs when using Android applications.
Finally, as this new technology is increasingly used in software development, we will update this MTE User Guide with the feedback and experience of developers.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK