

Varonis Delivers Market-leading Salesforce Security
source link: https://www.varonis.com/blog/varonis-delivers-market-leading-salesforce-security-varonis
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Inside Out Security Blog / Varonis Products
Varonis Delivers Market-leading Salesforce Security

As the market’s leading CRM, Salesforce houses some of your organization’s most valuable data — whether that’s customer and prospect information, contracts, or support cases. Many security teams don’t realize the depth and breadth at which Salesforce acquires and houses information — and how complicated it is to protect it.
For example, if a bank were to build an app using Salesforce, guess what would happen when you upload your financial documents with your mortgage application? All that information ends up in Salesforce as records, files, and attachments. Salesforce can classify the structured fields, but there’s no way to find, classify, or protect files and attachments natively in Salesforce.
Enter Varonis for Salesforce — agentless, cloud-native data security that deploys in 15 minutes.
Varonis for Salesforce gives you the ability to locate and control hard-to-find regulated data across all your Salesforce instances. Whether it’s stored in records and fields, or files and attachments, we’ll find, surface, and protect it:
- Classify sensitive data in records and fields
Varonis scans Salesforce to accurately discover and classify sensitive data stored within records and fields. - Classify sensitive files and attachments
Varonis is the only product on the market that can look inside files attached to objects in Salesforce and auto-tag sensitive items. - Understand exposure in Salesforce
Calculate net-effective permissions with a simple bi-directional view to quickly answer, "Who has access to sensitive data?"- Right-size permissions
Reduce exposure and fix compliance gaps, such as ex-contractors and guest users who still have unnecessary access.
- Detect anomalous activity
Monitor user behavior and alert on data exfiltration attempts by insiders and malicious actors. - Pinpoint misconfigurations
Detect org-wide settings problems, discover shadow instances, and spot vulnerabilities.
- Right-size permissions
- Classify sensitive data in records and fields
Read on for an in-depth look at how each of these features help identify and remove your most critical Salesforce risks.
Discover and classify sensitive data across Salesforce — no matter where it lives
Sensitive and regulated data can sprawl across Salesforce, hiding in many places — some in places you’d expect and others where you may not think to check.
Varonis discovers and classifies sensitive and regulated data across your Salesforce environment with pinpoint accuracy. We identify where sensitive data lives in each object’s records and fields — including your notes field!
It’s easy to assume you know where PII lives within your Salesforce records and fields. Phone numbers are in the phone field, addresses are in the address field, email addresses are in the email field, and so on, but that’s not always the case. Often, sales and marketing reps may enter sensitive or even regulated data into the notes field, which you may not immediately think to check. But not to worry — if sensitive data is stored in Salesforce, Varonis will surface and protect it.
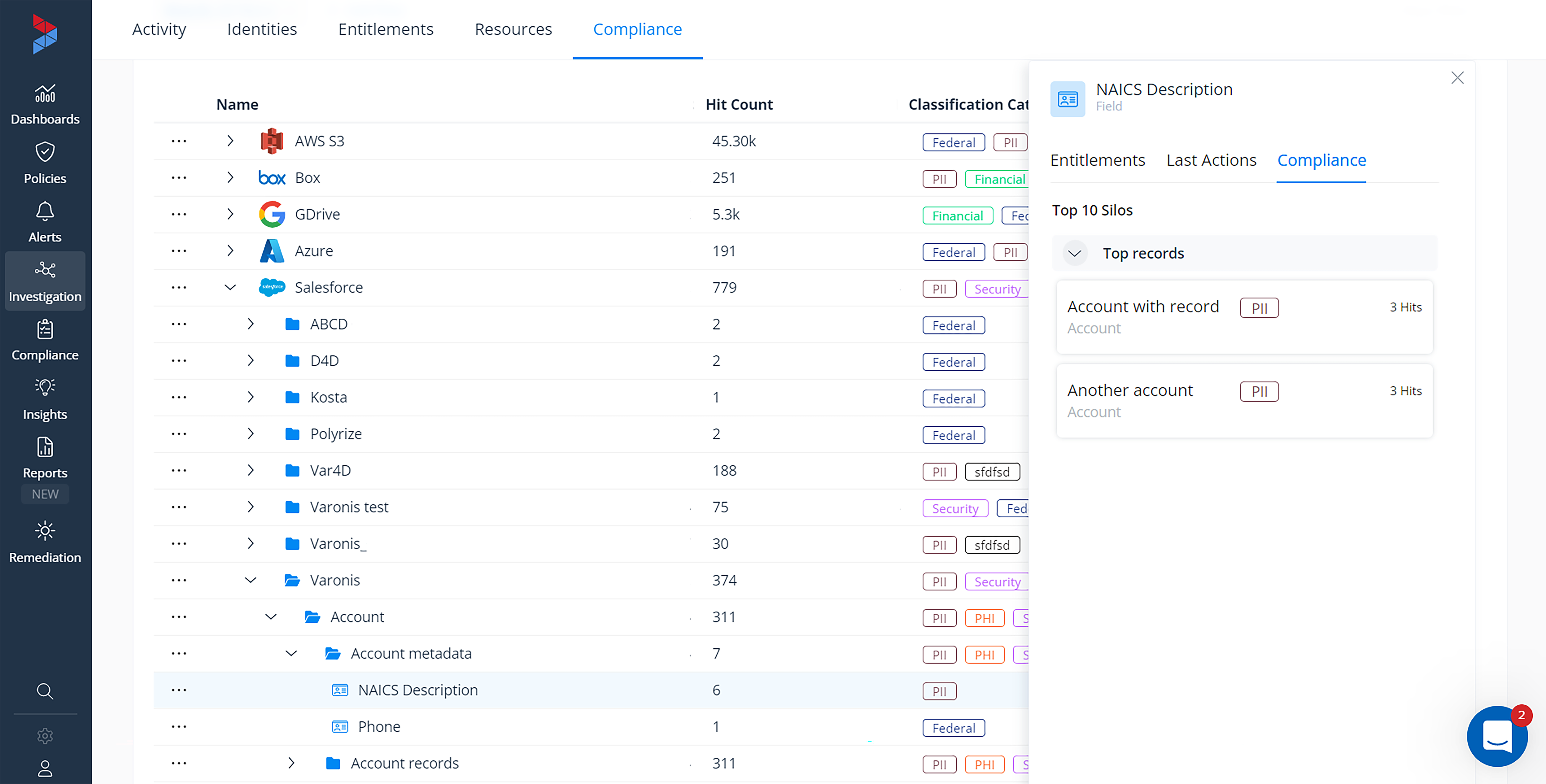
Discover sensitive data stored in records and fields.
In addition to helping you classify certain fields as sensitive, Varonis can find sensitive data attached to different records. The Salesforce security market has been missing this capability — until now.
Only Varonis can scan the contents of all your files and attachments, find sensitive data using our vast classification library, and then pair those classification results with permissions so that you can see exactly where data is exposed.
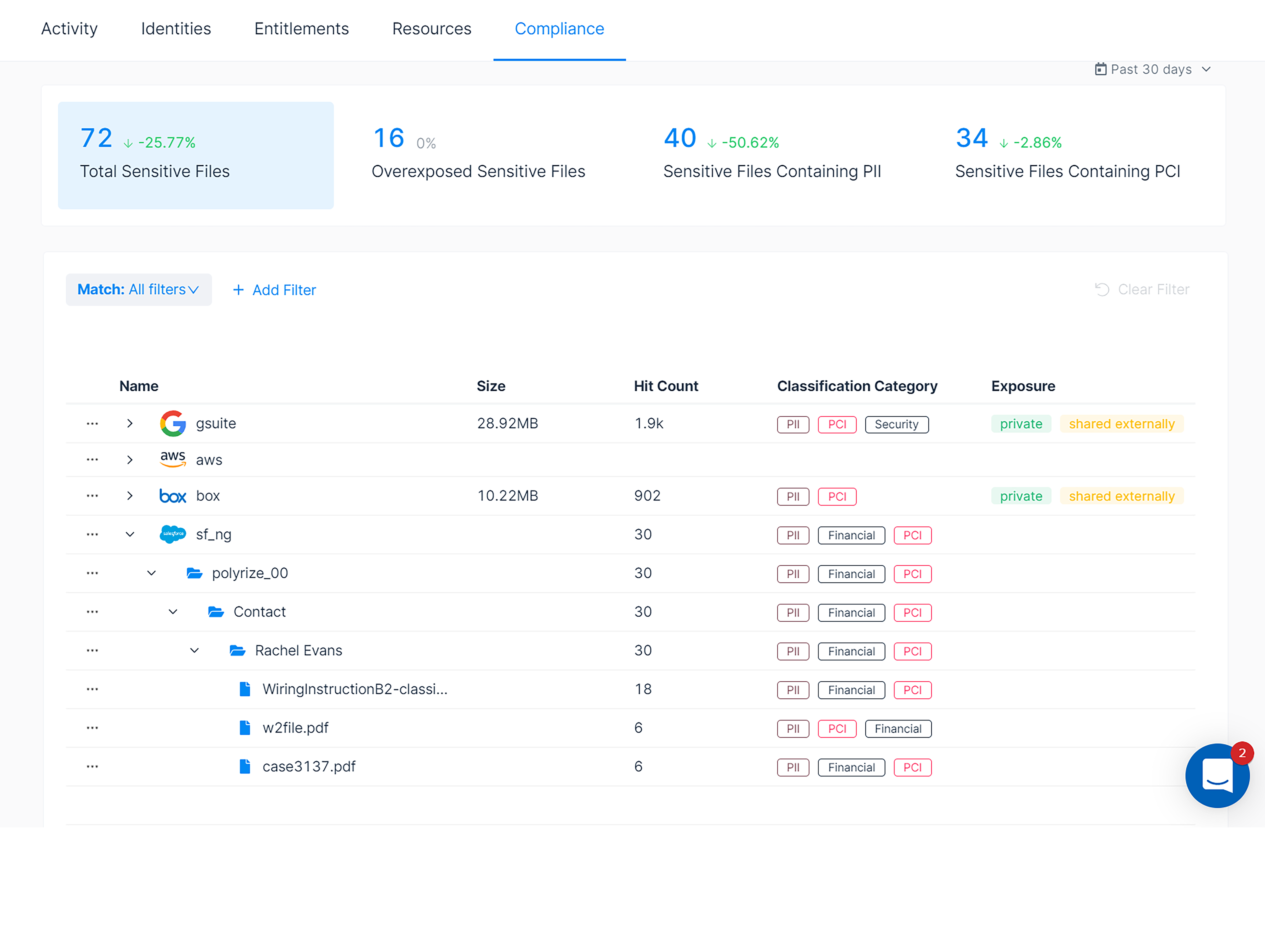
Quickly see where sensitive data is concentrated and exposed.
Varonis’ classification goes beyond regular expressions and includes pre-built databases of known valid values, proximity-matching, negative keywords, and an algorithmic verification to generate highly accurate results. The same classification engine that has made Varonis a leader in data classification for more than a decade now extends to the hardest-to-find files in Salesforce. With this new release, you can analyze classification results quickly and easily.
We show you exactly where sensitive data exists in the documents and color code results. Now you can easily “trust, but verify” all classification results.
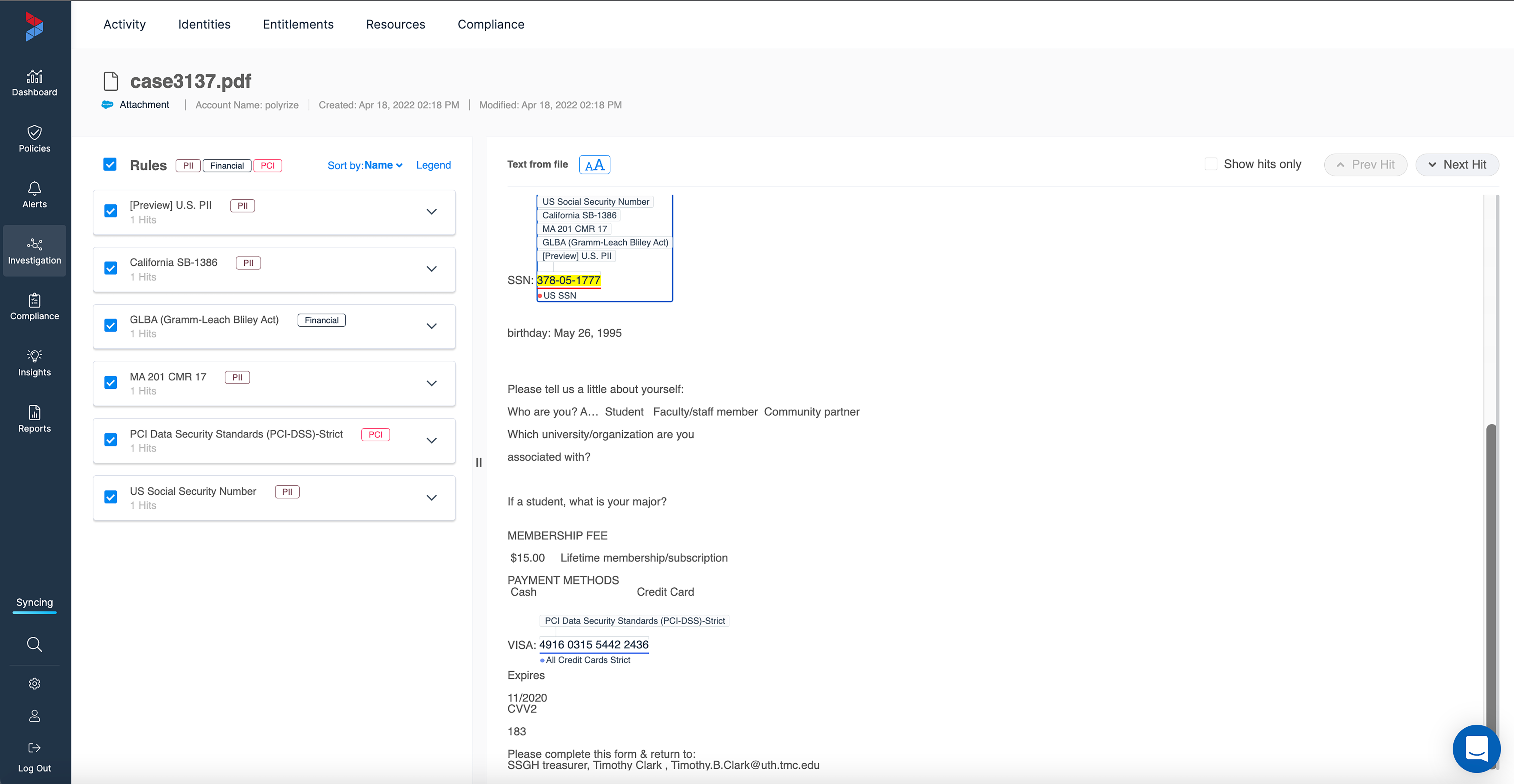
File analysis shows exactly where classification results are found within documents, records, and fields.
Effective permissions
Varonis radically simplifies permissions analysis, showing you not only what someone’s net effective permissions are but also how they got them.
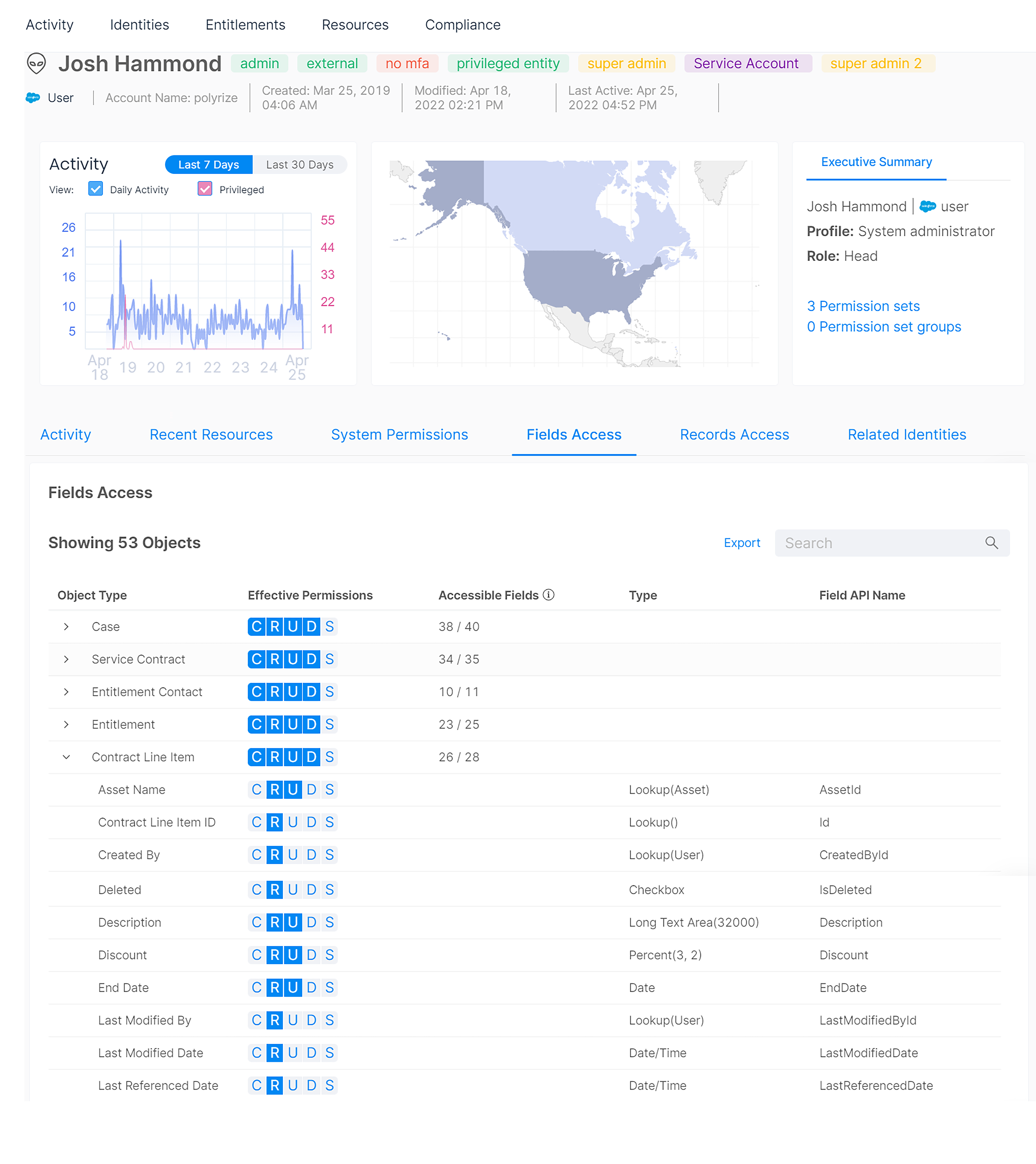
The permissions view shows aggregated, effective permissions on one screen.
Now, instead of clicking into every user’s profile, then clicking into every single one of their Permission Sets, you can see all their effective permissions from one screen. Hovering over a checkmark shows you how that user gained access, or you can add permission sets to the column view to see everything side-by-side. This permissions view gives security teams unprecedented visibility into risks and overexposure in their environment.
Single permissions tracking
On top of seeing what permissions a single user has, you can also see which group of users have a certain permission, such as, “Who has export access?”
Varonis’ bidirectional view of permissions in Salesforce enables you to click on a single system permission, such as “export reports,” to easily review the profiles and users that have this specific permission. With single permissions tracking, you’ll be able to better understand your blast radius and quickly identify any accounts with risky or toxic combinations of permissions.
![]()
View each user and Profile with the ”export reports” permission.
Record and field-level permissions
In a sales organization with frequently changing territories and roles, it’s easy to see how permission sets can get out of hand. Varonis empowers security teams to take back control of sprawling permissions and dramatically reduce their risk.
On top of system-level permissions, Varonis extends visibility to the object and field level. We simplify access into a simple CRUDS model (create, read, update, delete, share) and show you exactly what level of access someone has to every object and field in your environment and how they gained that access.

Varonis analyzes permissions down to the object and field level.
In addition to seeing everything an individual user can access, you can also go the other route and take specific records and determine all the users who can access them. If you know certain records are sensitive, you’d want to make sure that only the right people could access them.
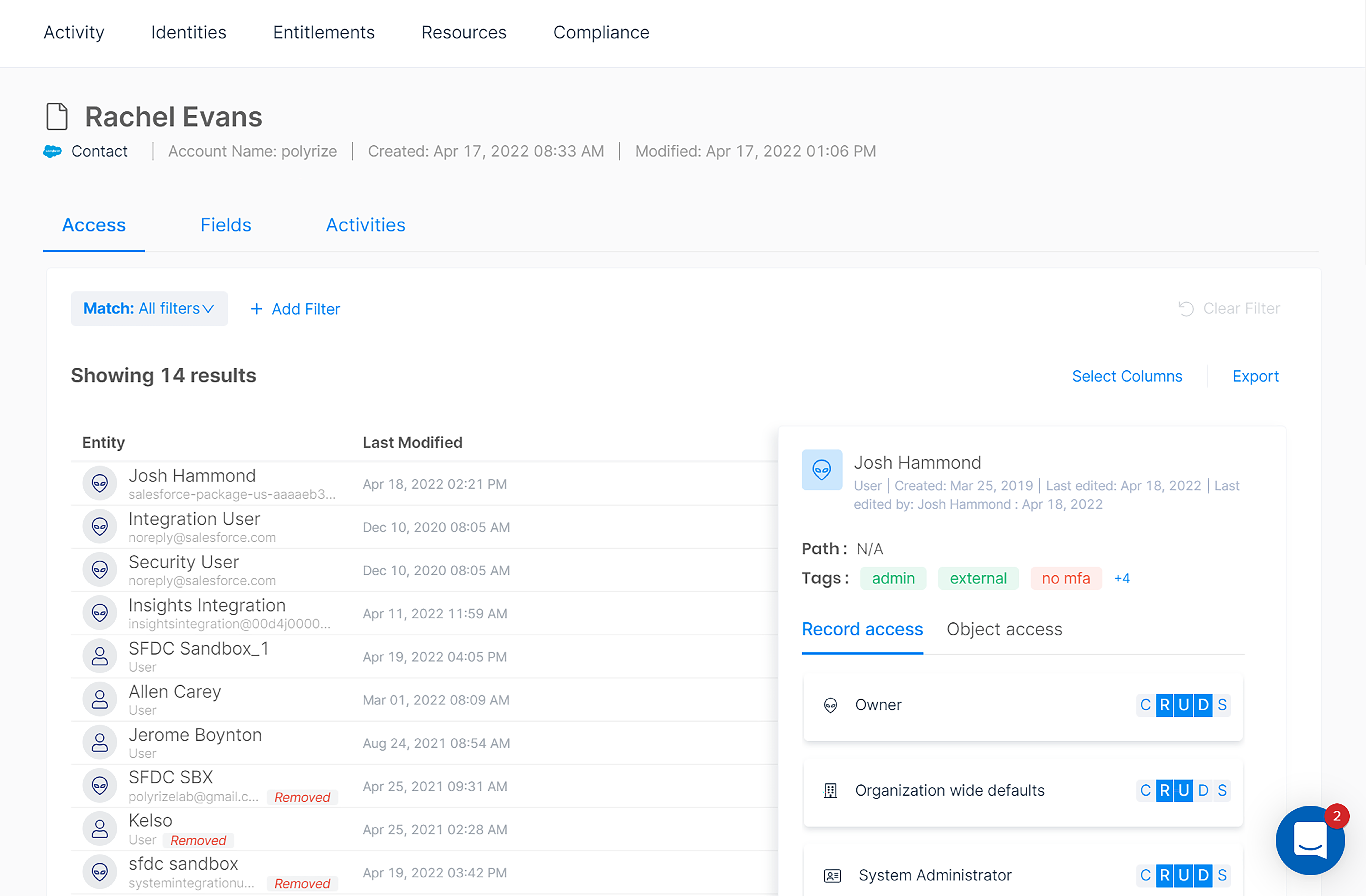
Easily see exactly who can access a specific record.
Within a specific record, you can drill down into the specific fields. You can quickly see the simplified CRUDS view of access and a more detailed view to see which permission sets give that access.
When someone leaves the company, you want to make sure they can’t access your corporate data anymore. Shockingly, three out of four ex-contractors can still access sensitive data after they’ve left the company. Varonis ties identities together across platforms to help you easily spot offboarding gaps, unsanctioned personal account use, or other compliance violations.
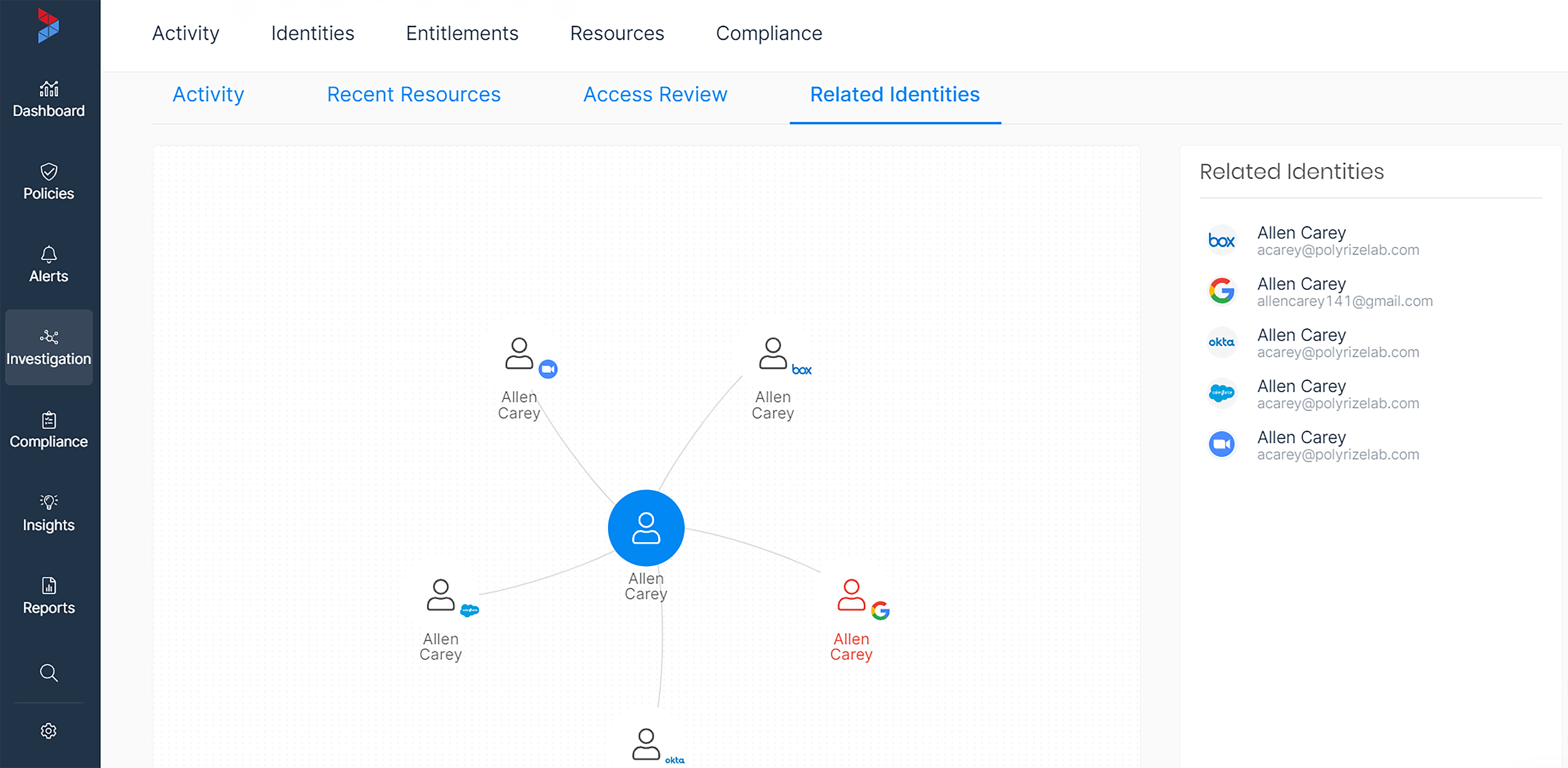
Detect anomalous activity
Varonis monitors Salesforce — and your broader SaaS environment — for suspicious activity. Our out-of-the-box alerts can detect internal and external threats, such as a user accessing an unusual number of Salesforce objects, deactivating a critical update, or escalating privileges. On top of built-in alerts, you can easily configure your own alerts without writing any Apex code. All of our alerts are mapped to MITRE ATT&CK for quick investigations.
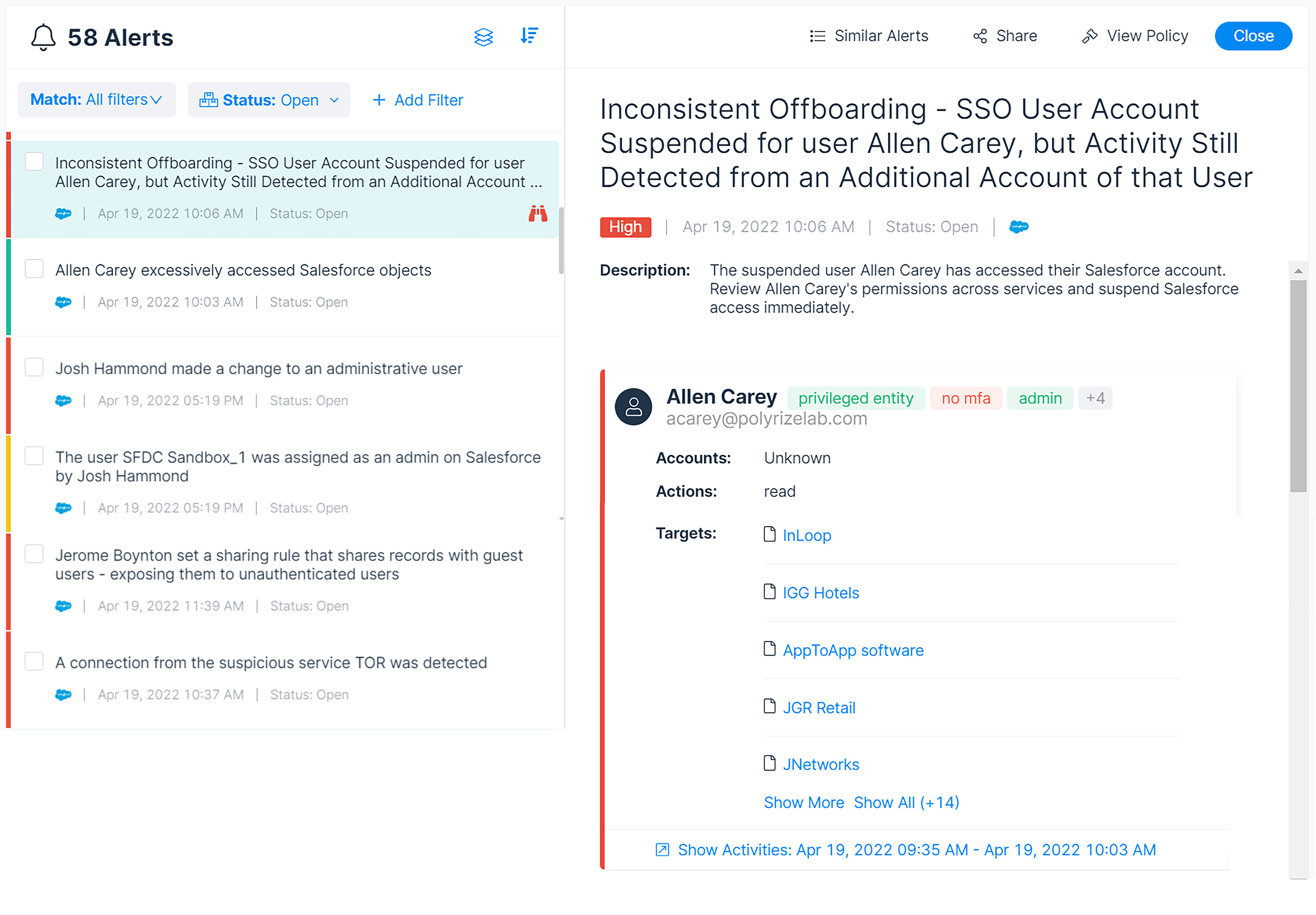
The Alerts Dashboard shows risky activity happening across your SaaS ecosystem.
Because we’re monitoring multiple SaaS apps in one platform, it’s easy to investigate incidents across your environment. We enrich events and correlate identities across cloud apps, making it easy to see something like a user logging in through Okta, accessing records in Salesforce, and then using their personal Gmail account to email themselves data.
Find misconfigurations
Excessive permissions are a major way sensitive data can end up exposed, but misconfigurations are another way data can be at risk. Given how configurable Salesforce is, it’s easy to miss a checkbox somewhere along the line — and these misconfigurations can create big gaps in your security posture. Varonis highlights these misconfigurations in our SaaS Security Posture Management (SSPM) Insights Dashboard.
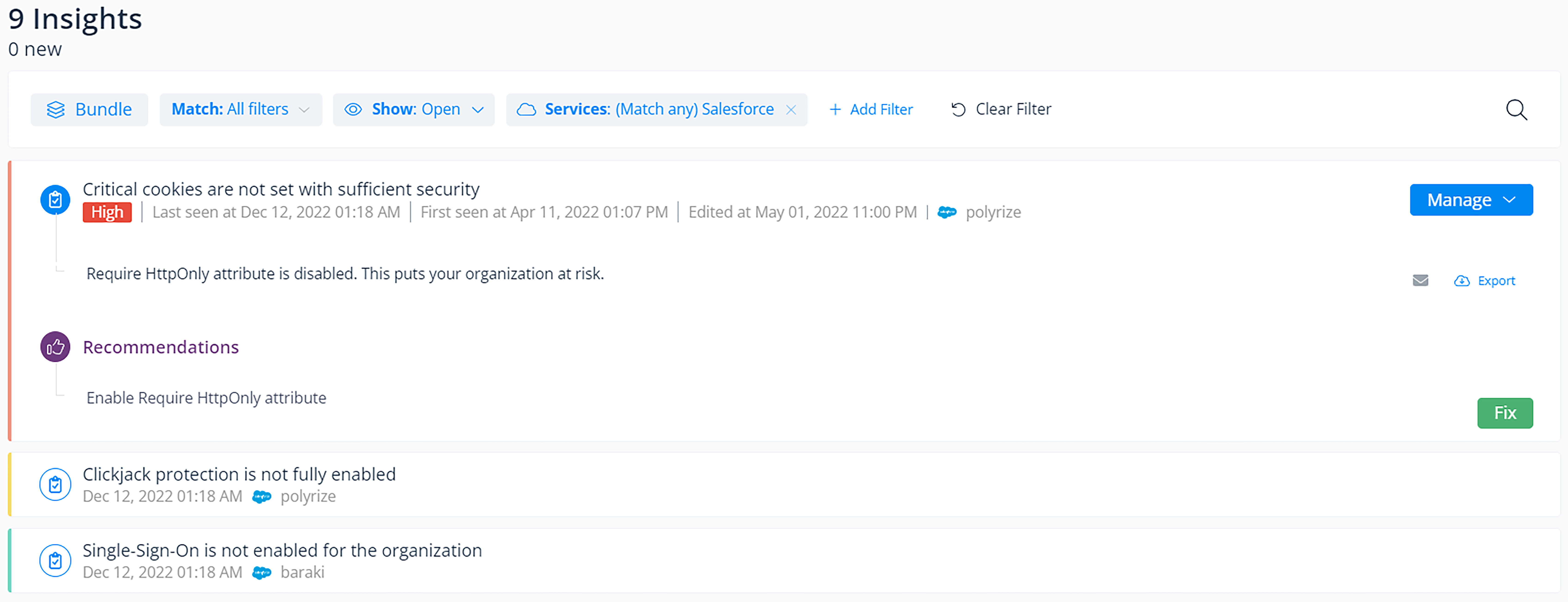
The Insights Dashboard highlights misconfigurations that can expose Salesforce data.
The Insights Dashboard includes findings from our elite cybersecurity research team. Such findings include Einstein’s Wormhole — a misconfiguration that exposed admins’ calendars through a Salesforce Community bug. Any time the team finds a potential SaaS configuration risk, Varonis can scan your environment and alert you if we think you’re exposed.
Try Varonis for Salesforce
Varonis is blazing a new trail in Salesforce security, with never-before-seen permissions analysis capabilities and unmatched data classification capabilities that add to our already robust SaaS security platform. When it comes to protecting your sensitive data, knowing where it exists, who can access it, and what they’re doing with it are all critical questions to answer. Only Varonis is integrating all these critical data security capabilities into one platform.
Varonis not only protects Salesforce, but also other SaaS apps like Google Drive, Box, AWS, Zoom, Okta, GitHub, Jira, and Slack.
If you’re curious to see what risks may exist in your SaaS environment, reach out to start a trial. In minutes, we can have you up and running.

Avia Navickas
Avia is a product marketing leader with over 10 years of experience at software companies big and small.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK