

Building a Cybersecurity Culture
source link: https://medium.com/slalom-technology/building-a-cybersecurity-culture-9d58534abb2e
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Building a Cybersecurity Culture
Learn how to create a human firewall for your business

By David Roggen and Tara McCafferty
In 2020, the estimated global cost of cybercrime was $945 billion and the cost to implement cybersecurity was $145 billion. While there are multiple attack vectors, 94% of all attacks are initiated via compromised credentials. Most credential compromises can be traced back to human error, specifically those who are not well-versed in information security. Regular people. People like you and me (i.e. business users, technology people that are not specialized in security). Security is no longer solely the domain of IT, security, or legal departments, it is the responsibility of every individual across your entire organization.
A new enterprise imperative
It is essential that today’s organizations develop a strong cybersecurity culture. But, building a strong cybersecurity culture isn’t just about education. It requires that enterprises acknowledge firmly, and explicitly, that cybersecurity and data security protect the essence of organizations, businesses, and governments — in a very real way.
Creating a cybersecurity culture within an organization is one of many challenges leaders face today. Despite difficulties many enterprises face, it is neither unprecedented nor impossible to achieve. In fact, most organizations already have analogous policies in place. For example, employees are expected to uphold fiduciary responsibilities when it comes to managing budgets, resources and spend. As such, they are protecting the organization financially. Protecting the organization’s data and security can be embedded into the day-to-day habits of all employees. Because most compromises are errors made by non-security professionals, the imperative for incorporating security into your culture is crucial to protecting your organization, its information, intellectual property, as well as employee and customer privacy.
It’s more than just training
One of the cornerstones of cybersecurity is applying a defense-in-depth approach. Defense-in-depth is an “information security strategy integrating people, technology, and operations capabilities to establish variable barriers across multiple layers and missions of the organization”. This strategy involves leveraging a variety of tools and approaches to security, ensuring that no single vulnerability can be the cause of a major breach.
Given the rate of human error in compromised credentials, it comes as no surprise that defense-in-depth strategies involve people. A critical component of protecting your business is building a “Human Firewall” as part of your cybersecurity culture. By combining technology, process, and culture, your organization can take a holistic approach to cybersecurity.
Employee adherence to the cybersecurity principles set by the enterprise requires the organization to foster a culture that educates all team members about the threat of cybersecurity, while giving them tools and training needed to make possible, and encourage, cybersecurity informed actions. Doing so is more than cybersecurity awareness training and intermittent phishing exercises, rather it is a set of principles and actions which together ensure the security of critical data.
Forrester Research defines cybersecurity culture as “ a work environment where every person is excited by cybersecurity and motivated to make it better; people understand why cybersecurity is important and they see themselves as part of the solution.”
ISACA, one of the most respected cybersecurity organizations, explains that a cybersecurity culture must:
Require the workforce to know the security risk and the processes for avoiding that risk.
Build and enforce an operating process of tasks that keeps the enterprise safe.
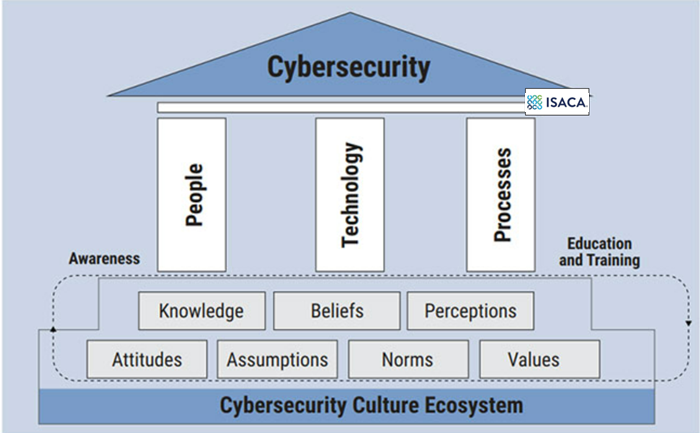
A cybersecurity culture framework
A review of the literature on cybersecurity culture uncovers multiple frameworks and approaches to achieving this outcome. The ISACA cybersecurity culture framework emphasizes the virtuous cycle of education and training, goes beyond the annual required training, and endeavors to create true cybersecurity awareness among teams.
It’s important to note that a cybersecurity culture is only as strong as the organization provides opportunities to realize cybersecurity behaviors day-to-day. This includes executive leaders actively promoting and demonstrating cybersecurity themselves — on a consistent basis. In addition, simple technology and processes that help realize these cultural goals include core policies like regular password updates.
Measure your impact
Build metrics to measure the impact of your cybersecurity culture efforts. In a recent Harvard Business Review article, the authors reviewed how Yahoo built a cybersecurity culture. Yahoo’s goal was to reduce the number of employees who click on a link on a phishing email test.
In preparation for a plan to decrease the vulnerability they established three metrics to measure the success of their program:
- Susceptibility Rate - the number of employees who entered credentials and did not report phishing emails, divided by the total number of phishing simulation emails sent;
- Credential Capture Rate - the number of employees who entered credentials (and did not report the link to our defense team), divided by the number of employees who opened the phishing simulation and landed on the fake login page; and
- Reporting Rate - the number of employees who reported the phishing simulation, divided by the number of total simulation emails sent.
Make it stick
In a recent article, Denise Lee Yohn (a leading authority on building exceptional organizations) wrote
A company’s culture needs to be adaptable. There are many external factors exerting pressure on any business as well as internal changes, such as leadership transitions and expansions. The culture needs to change to keep up with these changes.
The challenges faced incorporating cybersecurity into an organization’s culture is one example of the adaptability to which she refers. Creating a cybersecurity culture and mindset generally does not require an overhaul of an organization’s primary culture. In many cases, augmenting the existing culture with mindsets and habits that promote security will drive the desired results — fewer breaches, less exposure, and overall increase in data security.
So what does it take to augment the existing culture and reinforce security practices at all levels of the organization?
There are two foundational steps:
1. Connect the changes and expectations to the existing culture and values.
First, define which components of your existing culture and values connect with and promote a strong security mindset and practice. Most organizations don’t have to look too far to find a connection to security in their current culture. You probably won’t need to either.
- Is one of your core values is related to trust or responsibility?
- Are integrity, honesty, or commitment to customers pillars of your culture?
These simple examples are easy entry points through which security practices can be socialized and promoted. For example, a commitment to customers will be hard to realize if employees do not realize that protecting customer information is part of that commitment or are unclear what they can do to secure customer information.
By finding these entry point connections to security, you are embracing the adaptability Lee Yohn described in her article. It is not a change to your culture, it is an evolution of how your culture comes to life. Integration with existing culture and values also helps alleviate potential feelings of ‘change fatigue’ or ‘yet another new thing to adopt’ because you’re building from a foundation that already exists. There’s no need to create something entirely new —rather, treat cybersecurity behaviors as an expression of how your culture is evolving in real-time to meet the changing demands of the market.
2. Embrace, and partner with, influential stakeholders.
Second, tap into stakeholders that have the most direct accountability on security overall as well as those who have the greatest influence on day-to-day habits.
To enable every employee to take responsibility for safe and secure practices, we can look to two key demographics Lee Yohn addresses in her article — your boards of directors (or equivalents) and your middle managers. Although these two groups may never meet, they both have highly influential roles in building the habits that will drive overall success.
The board of directors is often charged the longevity of the organization, its success, and its brand reputation. Security breaches pose a threat to each of those concerns. Consider leveraging the board’s influence to direct the need for measuring your organization’s security and monitoring progress over time. Board members can help hold leadership teams accountable for ensuring that the company culture promotes an environment that enables, and expects, all employees to embrace security practices and feel safe raising security risks and concerns.
It’s also important to remember that day-to-day habits are built at the team level. Middle managers play a critical role in creating environments where teams feel empowered to act securely and safe to expose risks. Let’s consider a specific example:
An employee is traveling for work and receives an urgent request from a client or manager to share a document. The employee can access the airport Wi-Fi or their mobile device, but does not have access to a secure network. The employee feels as if they have no choice but to access the network from their mobile device, use their corporate credentials, and send the document.
While it is possible that the to the network can be compromised via the mobile device is minimal (i.e.. the mobile device is managed by the organization and has security protocols that mitigate these risks) but this is not always the case. Is it worth the risk?
Managers are instrumental in creating an environment in which that employee feels safe negotiating the urgency, or ask for help. Solutions as simple as asking the client or manager if the document can be shared in the morning, from a secure network, or suggesting another colleague send the document instead, can alleviate these everyday risks. However, if the current environment makes it unsafe or unclear to the employee that these options are available, the exposure and subsequent risk of security breach is significant.
Conclusion
The discourse on culture has increased greatly over the last decade. Leaders use culture to attract talent and keep employees engaged. Talented professionals seek work cultures that help them find satisfying and fulfilling careers. A robust culture that demonstrates it’s core values day-to-day can help enable employees to shift their behaviors organically, to meet the changing demands of technology and the market — including the ever-evolving needs of cybersecurity.
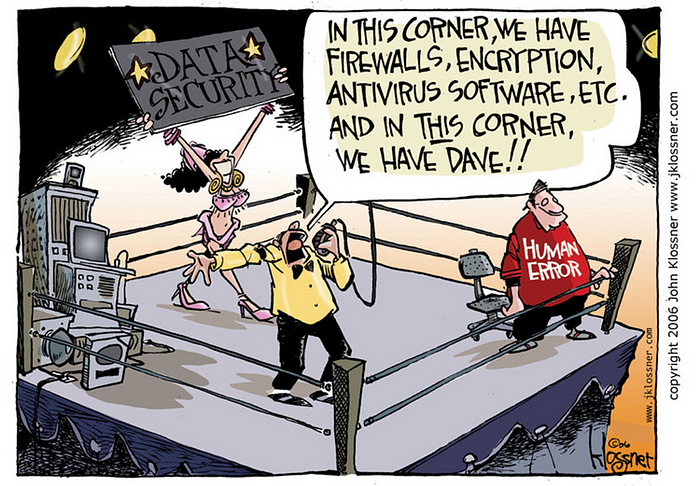
Building a cybersecurity culture that encourages organic growth towards a security mindset is critical for the modern enterprise. As society and business continue to digitize, our most important personal and business assets become digital assets. Failure to build a culture that is aware of this and moves towards a secure environment perpetuates the most critical vulnerability in the cybersecurity environment - the human being.
Slalom is a global consulting firm that helps people and organizations dream bigger, move faster, and build better tomorrows for all. Learn more and reach out today.
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK