

Granular controls - Power Platform | Microsoft Docs
source link: https://docs.microsoft.com/en-us/power-platform/admin/dlp-granular-controls
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Advanced DLP granular connector controls
- Article
- 04/11/2022
- 6 minutes to read
In this article
Although the connector classification capability is very helpful in governing Microsoft Power Platform connectors, fine-grained controls—such as the ability to block specific connector actions or connection endpoints—help you strike a balance between productivity and protection.
Some apps need to be re-published for your connector action rules and connector endpoint filtering rules to be enforced. See Known limitations below.
Connector action control
- Connector action control is generally available.
- Configuring a connector's actions is available for all blockable connectors, but not for unblockable connectors and custom connectors.
You can use connector action control to allow or block individual actions within a given connector. On the Connectors page, right-click the connector, and then select Configure connector > Connector actions.

This opens a side panel where you can allow or deny specific actions. You can also set the default value (Allow or Deny) for any new connector actions that will be added to the connector in the future.

PowerShell support for Connector action control
Retrieve a list of available actions for a connector
Get-AdminPowerAppConnectorAction
Example
Get-AdminPowerAppConnectorAction -ConnectorName shared_msnweather
| Id | Type | Properties |
|---|---|---|
| TodaysForecast | Microsoft.ProcessSimple/apis/apiOperations | @{summary=Get forecast for today; description=Get the forecast for the current day in the specified location.; visib... |
| OnCurrentWeatherChange | Microsoft.ProcessSimple/apis/apiOperations | @{summary=When the current weather changes; description=Triggers a new flow when the specified weather measure chang... |
| CurrentWeather | Microsoft.ProcessSimple/apis/apiOperations | @{summary=Get current weather; description=Get the current weather for a location.; visibility=advanced; pageable=Fa... |
| TomorrowsForecast | Microsoft.ProcessSimple/apis/apiOperations | @{summary=Get the forecast for tomorrow; description=Get the forecast for tomorrow in the specified location.; visib... |
| OnCurrentConditionsChange | Microsoft.ProcessSimple/apis/apiOperations | @{summary=When the current conditions change; description=Triggers a new flow when the conditions change for a locat... |
Configure connector action rules for a policy
The object that contains connector action rules for a policy is referred to below as the connector configurations. The connector configurations object has the following structure:
$ConnectorConfigurations = @{
connectorActionConfigurations = @( # array – one entry per connector
@{
connectorId # string
actionRules = @( # array – one entry per rule
@{
actionId # string
behavior # supported values: Allow/Block
}
)
defaultConnectorActionRuleBehavior # supported values: Allow/Block
}
)
}
Retrieve existing connector configurations for a DLP policy
Get-PowerAppDlpPolicyConnectorConfigurations
Create connector configurations for a DLP policy
New-PowerAppDlpPolicyConnectorConfigurations
Update connector configurations for a DLP policy
Set-PowerAppDlpPolicyConnectorConfigurations
Example
Goal:
- Block actions TodaysForecast and CurrentWeather of connector MSN Weather; allow all other actions.
- Allow action GetRepositoryById of connector GitHub; block all other actions.
In the following cmdlet, PolicyName refers to the unique GUID. You can retrieve the DLP GUID by running the Get-DlpPolicy cmdlet.
$ConnectorConfigurations = @{
connectorActionConfigurations = @(
@{
connectorId = "/providers/Microsoft.PowerApps/apis/shared_msnweather"
actionRules = @(
@{
actionId = "TodaysForecast"
behavior = "Block"
},
@{
actionId = "CurrentWeather"
behavior = "Block"
}
)
defaultConnectorActionRuleBehavior = "Allow"
},
@{
connectorId = "/providers/Microsoft.PowerApps/apis/shared_github"
actionRules = @(
@{
actionId = "GetRepositoryById"
behavior = "Allow"
}
)
defaultConnectorActionRuleBehavior = "Block"
}
)
}
New-PowerAppDlpPolicyConnectorConfigurations -TenantId $TenantId -PolicyName $PolicyName -NewDlpPolicyConnectorConfigurations $ConnectorConfigurations
Connector endpoint filtering
Connector endpoint filtering is in public preview.
Endpoint filtering allows admins to govern at a fine grain which specific endpoints will be allowed versus blocked at a tenant or environment level. This facility is available for HTTP, HTTP with Azure AD, HTTP Webhook, SQL Server, Azure Blob Storage, and SMTP connection endpoints. For more information, see Endpoint input formats and examples.
The Endpoint configurable column on the Prebuilt Connectors page in Data Policies indicates whether the endpoint filtering capability is supported for the connector
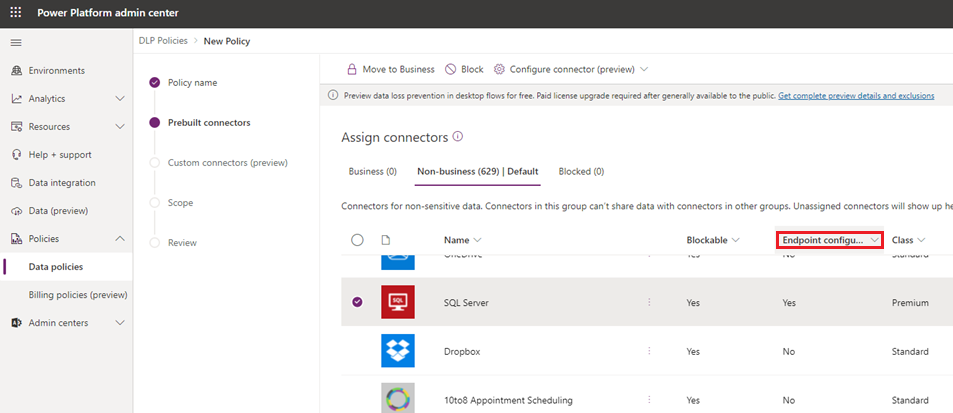
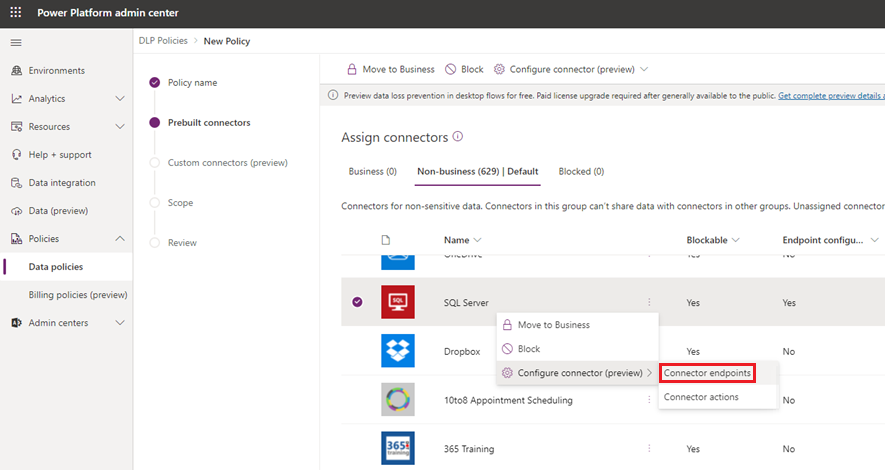
If the value of the Endpoint configurable column is Yes, you can use this capability by right-clicking and then selecting Configure connector > Connector endpoints.
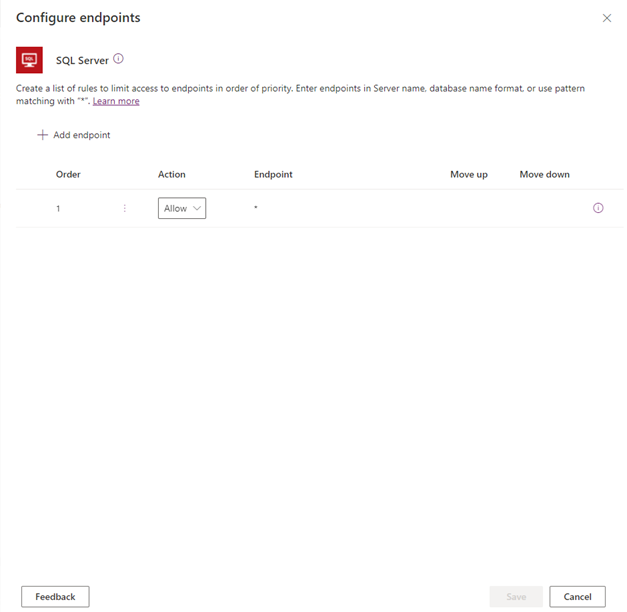
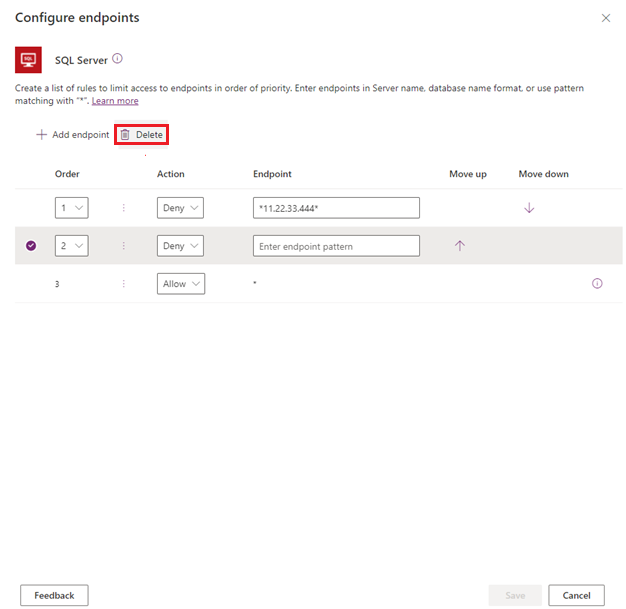
This opens a side panel where you can specify an ordered list of Allow or Deny URL patterns. The last row in the list will always be a rule for the wildcard character *, which applies to all endpoints in that connector. By default, the * pattern is set up as Allow for new DLP policies, but you can tag this as Allow or Deny.
You can add new rules by selecting Add endpoint. New rules are added to the end of the pattern list (as the second-to-the-last rule, because * will always be the last entry in the list). However, you can update the order of the patterns by using the Order dropdown list or selecting Move up or Move down.
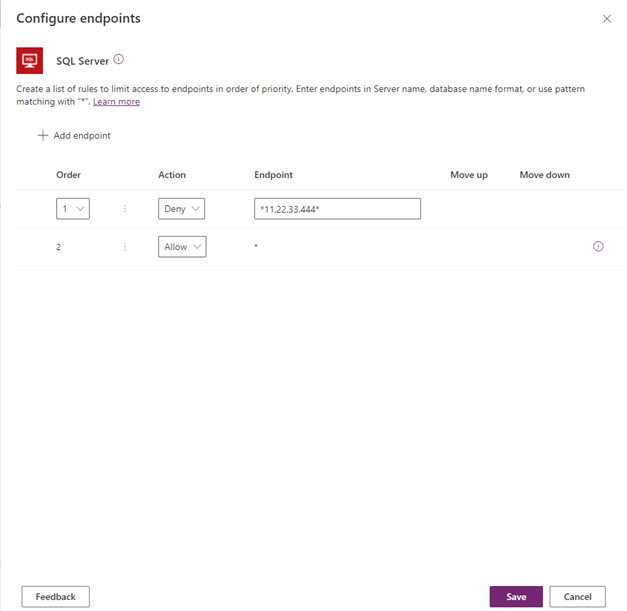
After a pattern has been added, you can edit or delete these patterns by selecting a specific row and then selecting Delete.
PowerShell support for endpoint filtering
Configure endpoint filtering rules for a policy
The object that contains endpoint filtering rules for a policy is referred to below as the connector configurations. The connector configurations object has the following structure:
$ConnectorConfigurations = @{
connectorActionConfigurations = @() # used for connector action rules
endpointConfigurations = @( # array – one entry per
@{
connectorId # string
endpointRules = @( # array – one entry per rule
@{
order # number
endpoint # string
behavior # supported values: Allow/Deny
}
)
}
)
}
Notes
- The last rule for each connector should always be applied to URL “*”, to ensure that all URLs are covered by the rules
- The order property of the rules for each connector should be populated with numbers 1 to N, where N is the number of rules for that connector
Retrieve existing connector configurations for a DLP policy
Get-PowerAppDlpPolicyConnectorConfigurations
Create connector configurations for a DLP policy
New-PowerAppDlpPolicyConnectorConfigurations
Update connector configurations for a DLP policy
Set-PowerAppDlpPolicyConnectorConfigurations
Example
Goal:
For the SQL Server connector:
- Deny database “testdatabase” of server “myservername.database.windows.net”
- Allow all other databases of server “myservername.database.windows.net”
- Deny all other servers
For the SMTP connector:
- Allow Gmail (server address: smtp.gmail.com, port: 587)
- Deny all other addresses
For the HTTP connector:
In the following cmdlet, PolicyName refers to the unique GUID. You can retrieve the DLP GUID by running the Get-DlpPolicy cmdlet.
$ConnectorConfigurations = @{
endpointConfigurations = @(
@{
connectorId = "/providers/Microsoft.PowerApps/apis/shared_sql"
endpointRules = @(
@{
order = 1
endpoint = "myservername.database.windows.net,testdatabase"
behavior = "Deny"
},
@{
order = 2
endpoint = "myservername.database.windows.net,*"
behavior = "Allow"
},
@{
order = 3
endpoint = "*"
behavior = "Deny"
}
)
},
@{
connectorId = "/providers/Microsoft.PowerApps/apis/shared_smtp"
endpointRules = @(
@{
order = 1
endpoint = "smtp.gmail.com,587"
behavior = "Allow"
},
@{
order = 2
endpoint = "*"
behavior = "Deny"
}
)
},
@{
connectorId = "http"
endpointRules = @(
@{
order = 1
endpoint = "https://mywebsite.com/allowedPath1"
behavior = "Allow"
},
@{
order = 2
endpoint = "https://mywebsite.com/allowedPath2"
behavior = "Allow"
},
@{
order = 3
endpoint = "*"
behavior = "Deny"
}
)
}
)
}
New-PowerAppDlpPolicyConnectorConfigurations -TenantId $TenantId -PolicyName $PolicyName -NewDlpPolicyConnectorConfigurations $ConnectorConfigurations
Known limitations
- Endpoint filtering rules are not enforced on environment variables, custom inputs and dynamically bound endpoints during runtime. Only static endpoints known and selected when building an app, flow, or chatbot during design time are enforced.
- Endpoint filtering rules for SQL Server and Azure Blob Storage are not enforced if the connections are authenticated with Azure Active Directory.
- Some Power Apps last published before October 1st 2020 need to be re-published for DLP connector action rules and DLP connector endpoint rules to be enforced. The following script enables admins and makers to identify apps that must be re-published to respect these new DLP granular control rules:
Add-PowerAppsAccount
$GranularDLPDate = Get-Date -Date "2020-10-01 00:00:00Z"
ForEach ($app in Get-AdminPowerApp){
$versionAsDate = [datetime]::Parse($app.LastModifiedTime)
$olderApp = $versionAsDate -lt $GranularDLPDate
$wasBackfilled = $app.Internal.properties.executionRestrictions -ne $null -and $app.Internal.properties.executionRestrictions.dataLossPreventionEvaluationResult -ne $null -and ![string]::IsNullOrEmpty($app.Internal.properties.executionRestrictions.dataLossPreventionEvaluationResult.lastAdvancedBackfillDate)
If($($olderApp -and !$wasBackfilled)){
Write-Host "App must be republished to be Granular DLP compliant: " $app.AppName " " $app.Internal.properties.displayName " " $app.Internal.properties.owner.email
}
Else{
Write-Host "App is already Granular DLP compliant: " $app.AppName
}
}
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK